Block traffic/No routing between LANs on pfSense
-
Hi,
Could you help me to create the other method that you mention please ?
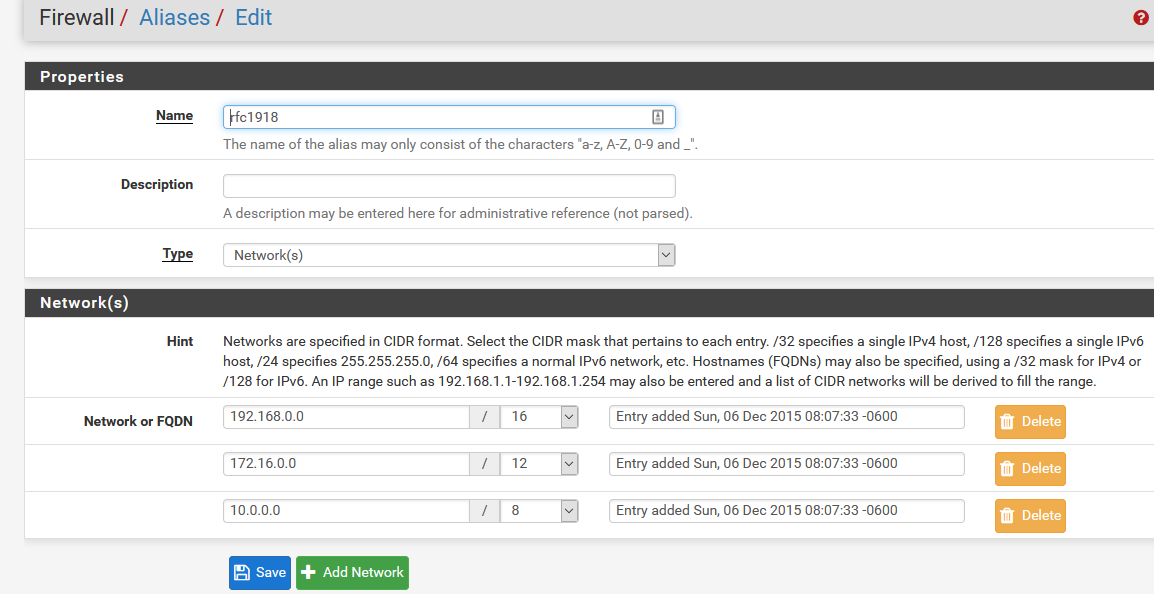
What are the parameters to use to create rfc1918 alias ? could you give me an screenshot of this alias to create it as well please ?After alias creation, does i need to create one or multiple rules ? in which section ? (Floating, WAN, VLAN_MY_LAN, VLAN_DMZ, VLAN_WIFI)
Could you give me screenshot copy of the rule(s) in this case please ?About NTP, some devices from different subnet use it but NTP target address is pointing on internet.
I do not have a ntp server on my lan's, so it doesn't block anything normally !?To have all parameters, you'll see below what rules/alias are present:
-
Interface list
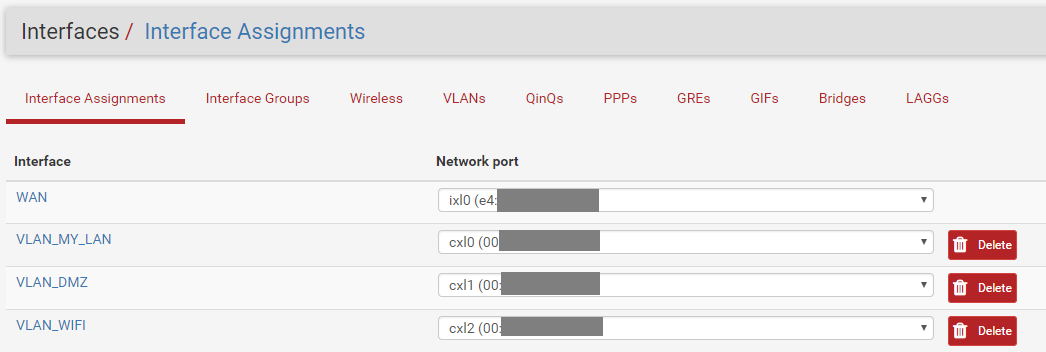
-
I block two LANs on three that i have to have access to pfsense webgui for security reason.
Alias
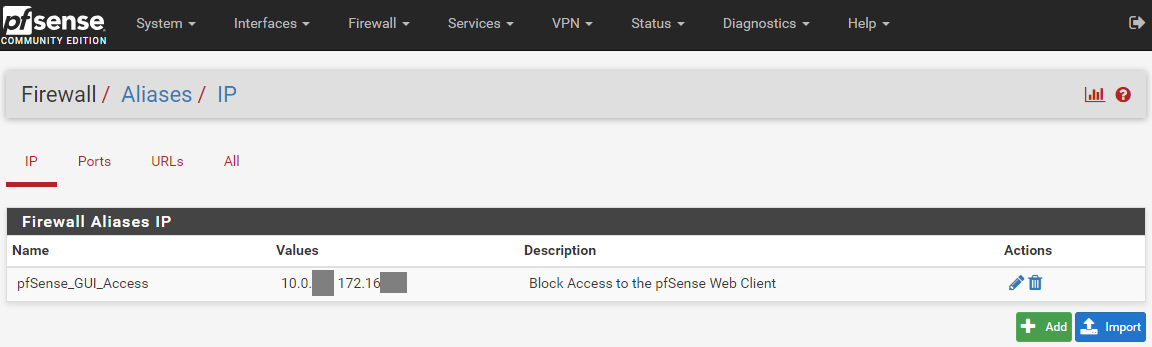
Floating rules associated:
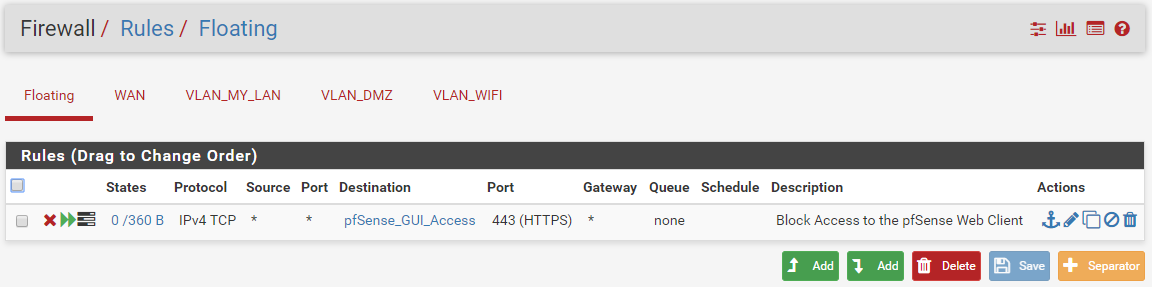
-
Port forward for Torrent
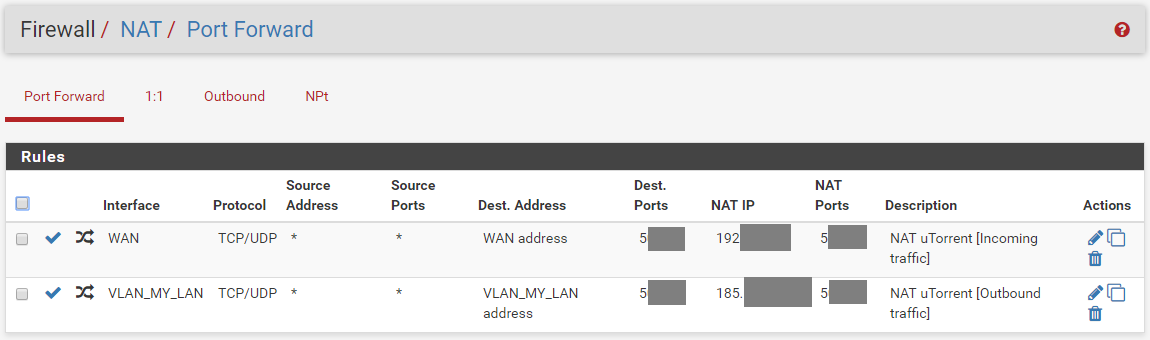
-
Current WAN Rules
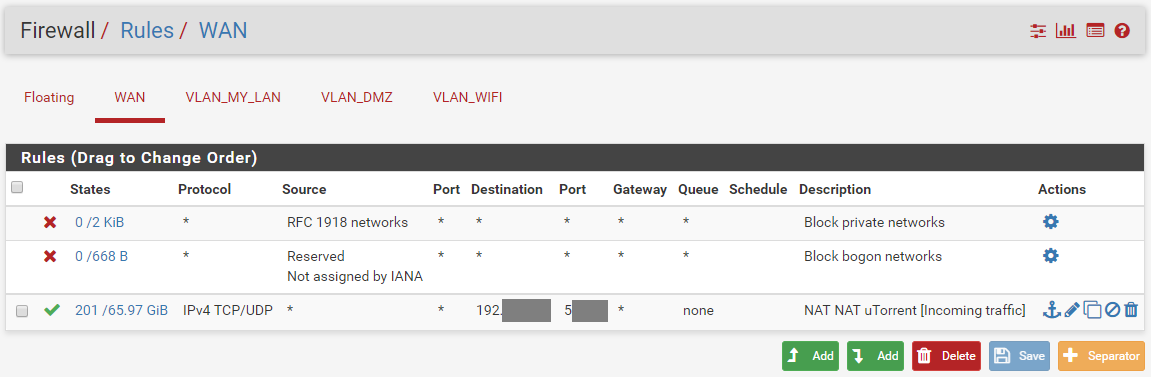
-
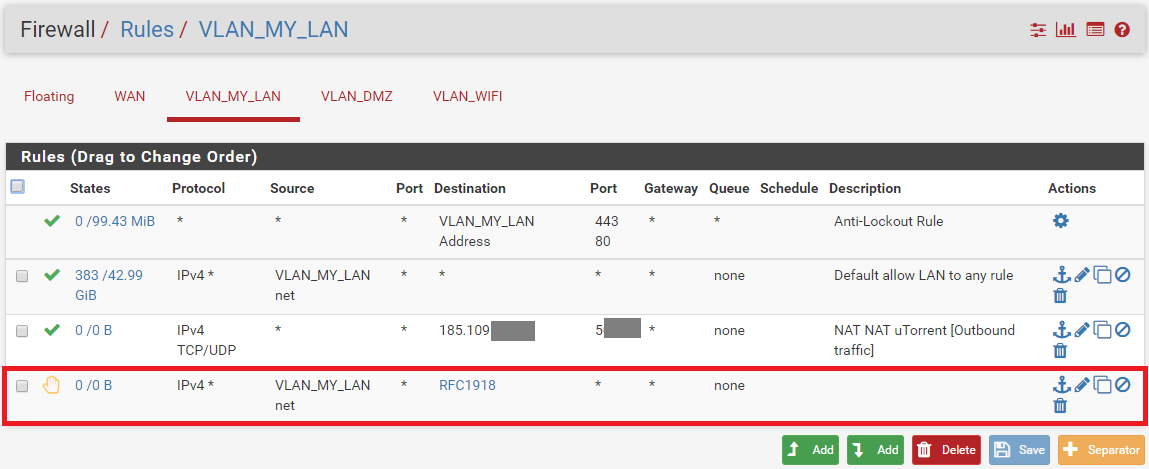
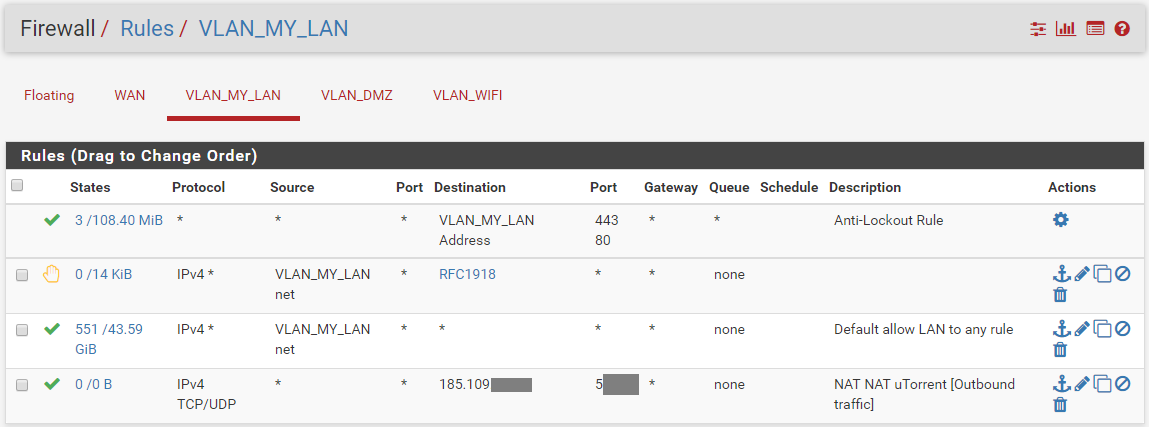
Current VLAN_My_LAN Rules (= LAN)
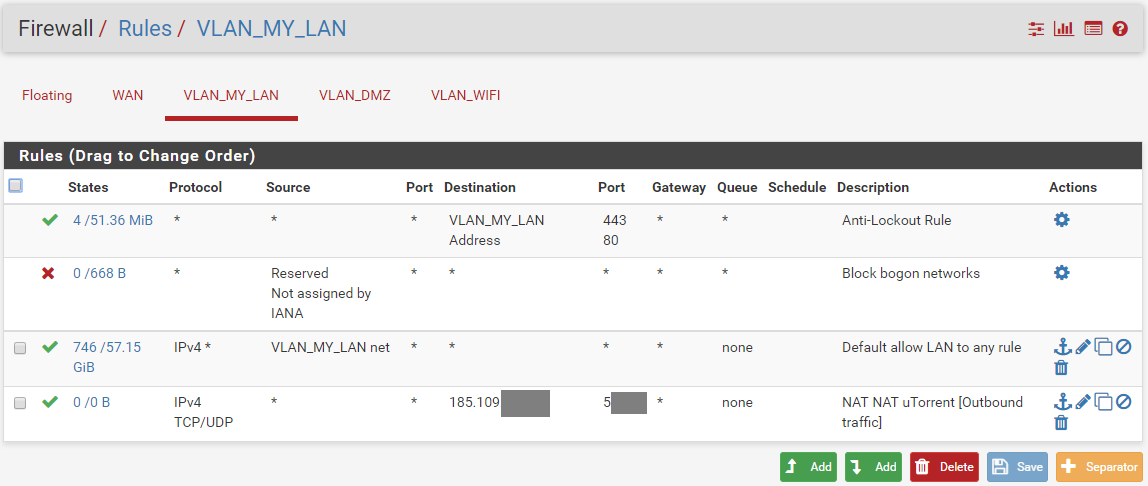
-
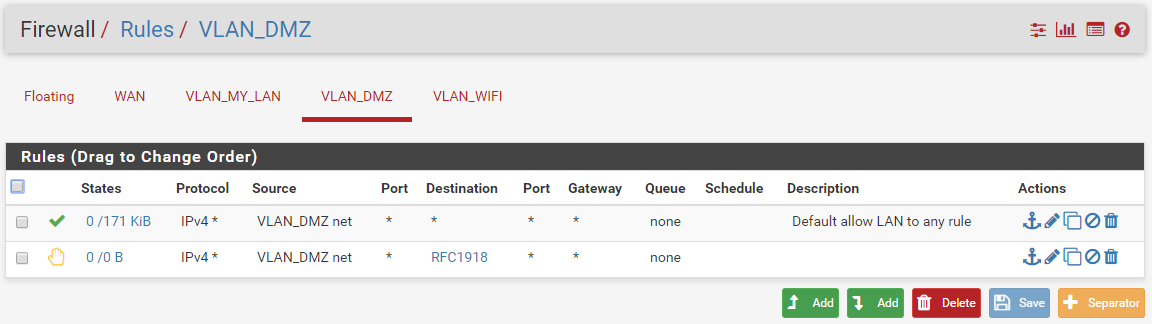
Current VLAN_DMZ (= OPT1)
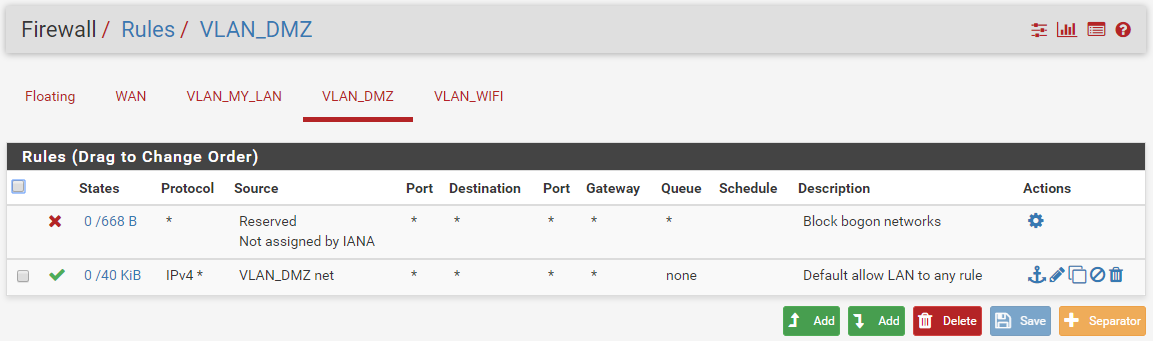
-
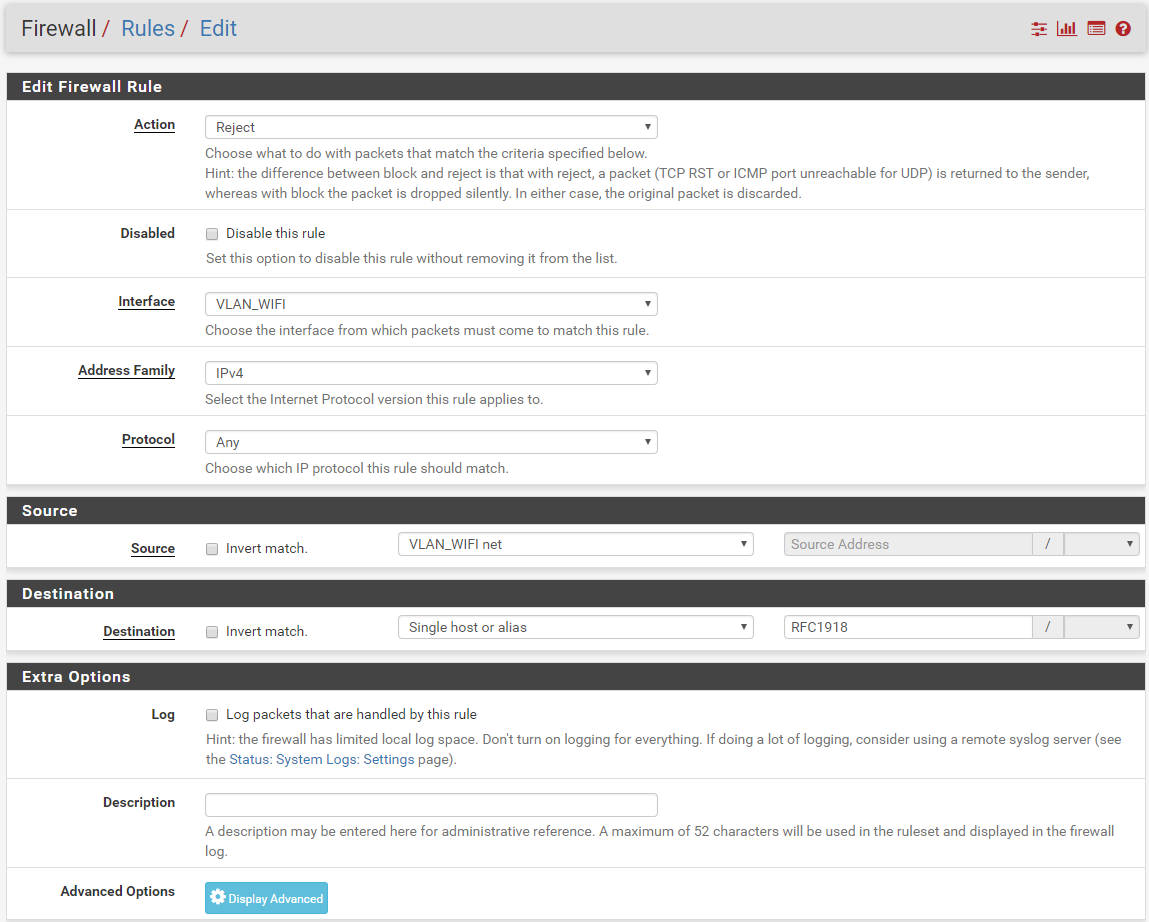
Current VLAN_WIFI (= OPT2)
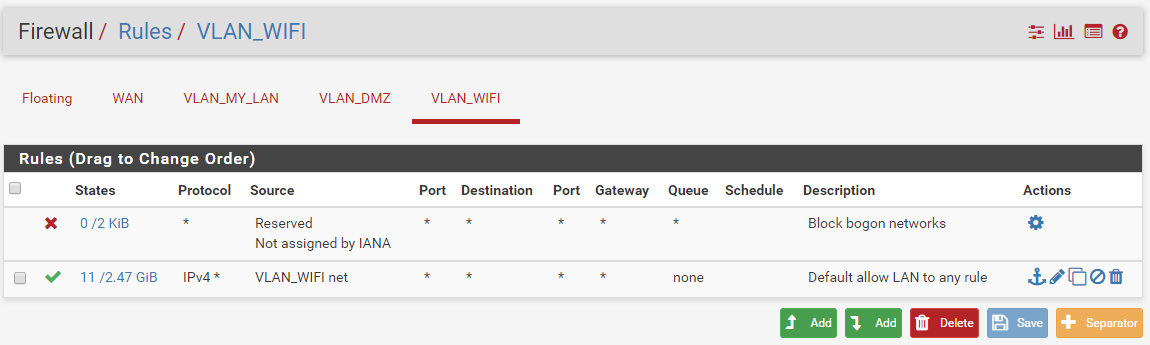
I figure that your answer help me and many other person who need to do the same things.
Many thanks in advance for your precious help :) -
-
Here..
BTW - blocking bogon on your local networks is going to cause you nothing but grief... there is ZERO reason to block bogon on your local network.. What you think someone is going to connect to your network and start using bogon addresses?
-
Thanks, aliases is created :)
I disable bogon, sorry i was not aware about this, don't hesitate to advise if you find something strange into my setup.So i need to create just one Rules after with rfc1918 after ?
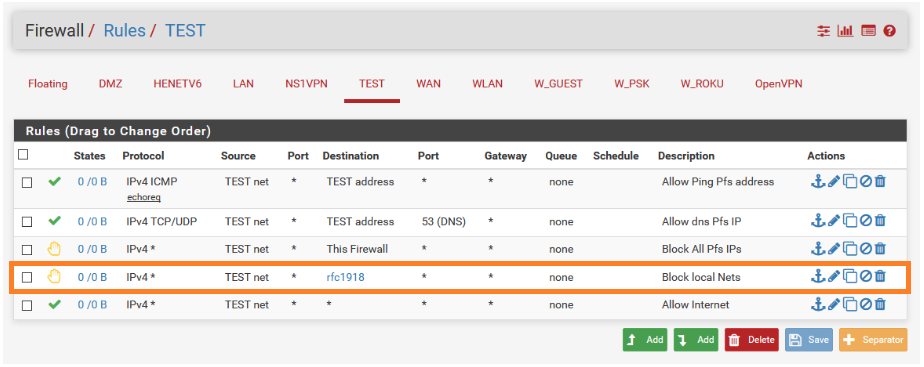
Could you tell me in which tab does it be created ? in Floating tab, WAN, VLAN_MY_LAN, VLAN_DMZ or VLAN_WIFI?Coud you edit your rules to be sure to have all good parameters set properly ?
Many Thanks.
-
You create the rules on the interfaces you want.. Just making your setup look like a picture isn't the correct way.. The correct way is understanding what the rules are doing so you can determine what rules you need per your setup..
You place the rules on the interface where the traffic would first enter pfsense.. If you don't want your 3 vlans to talk to each other than the block would need to be on all 3 of them..
You could put rules on floating tab - but I highly suggest against that since you don't seem to understand basic concepts as of yet and rules placed there are for more complex uses.
Rules are evaluated as traffic enters pfsense from that network, top down, first rule to trigger wins, no other rules are evaluated..
So if you want to block opt1 from talking to lan, where do you think the "rules" would go..
Also there is nothing in the rules I showed other than that info, if any special things had been set you would see the little gear symbol next to them.
Pretty much the rules as I posted them would go on EVERY interface.. Where you would just change out the test address, and test net for the interface you are putting them on. The rules are labeled as to what they specifically do.
-
Hello,
I create one rule on VLAN_MY_LAN interface, but it doesn't seems good.
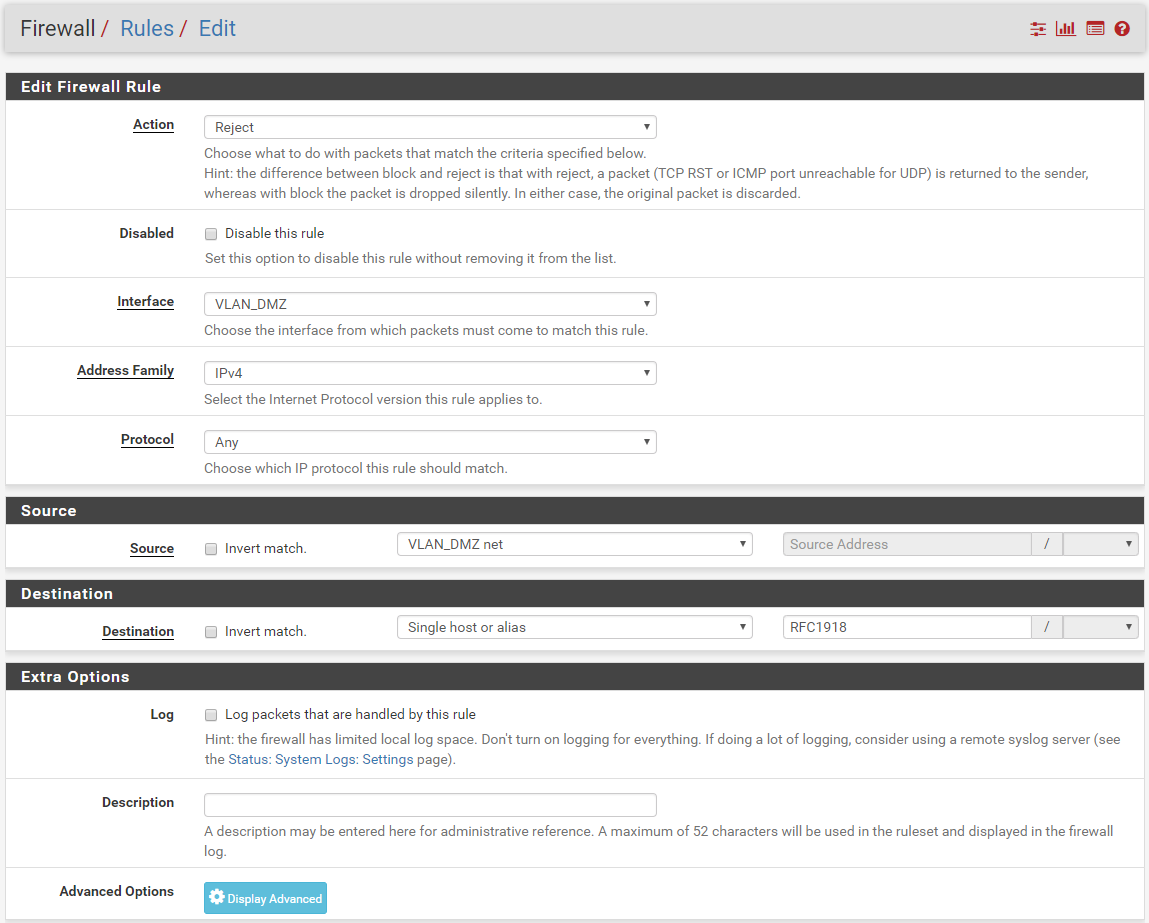
I'm still able to ping VLAN_DMZ from VLAN_MY_LAN :(i try to add one rule on VLAN_DMZ and VLAN_WIFI, but it's remain the same.
My setup is like this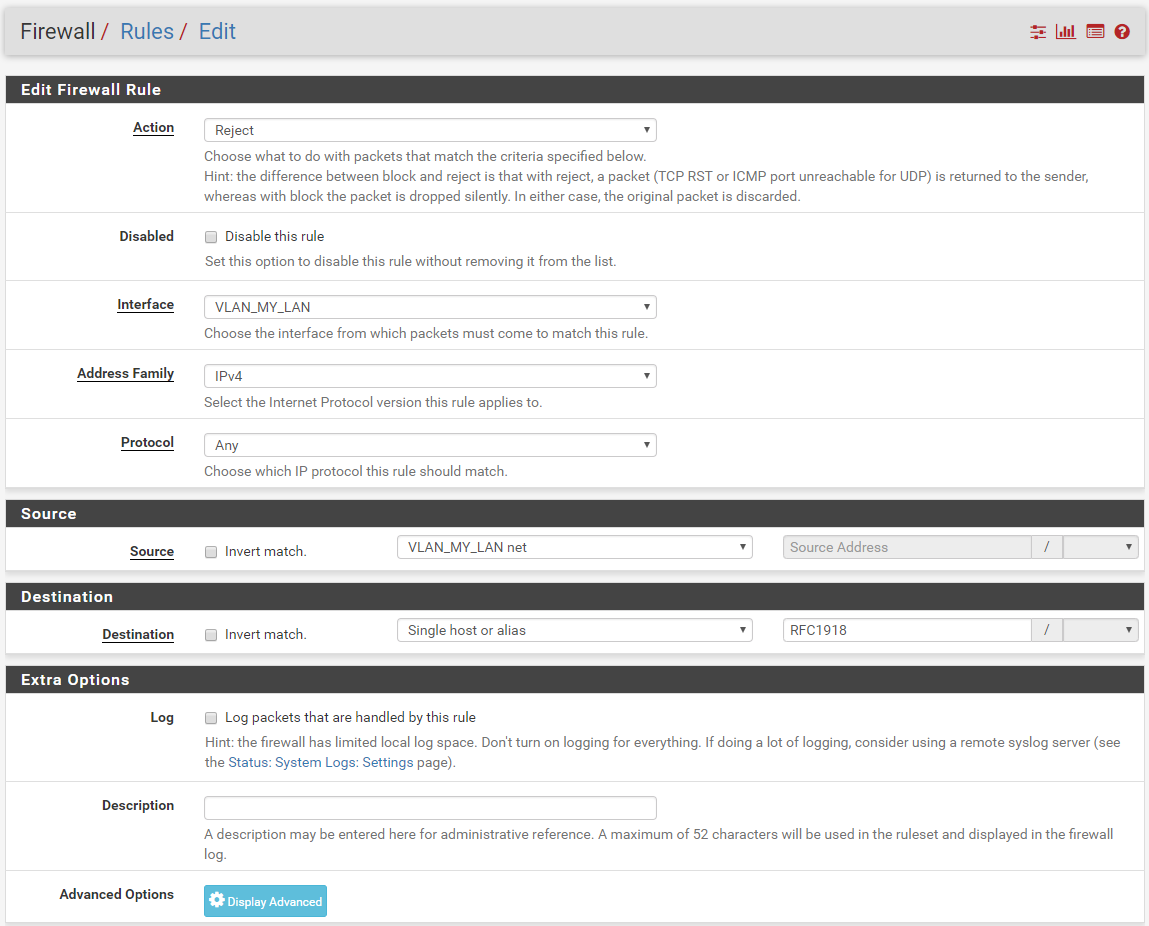
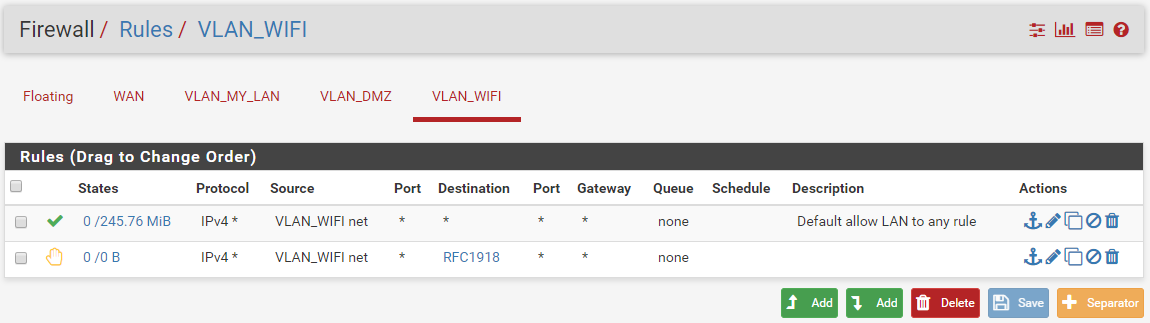
What's wrong please ?
-
That is because your block rule is UNDER an allow rule... Again rules are evaluated TOP DOWN, first rule to trigger wins.. So no your block rule would never trigger.
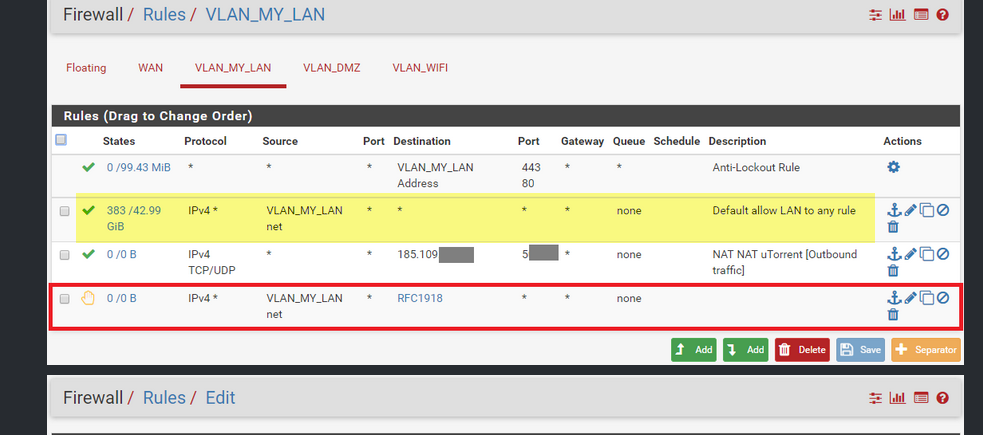
And not sure what you think that nat nat rule is suppose to do?
And if you move the block to above your allow, then how would you talk to pfsense for dns..
When designing your rules - just think about your destination and then look at it rule from the TOP down, which rule matches first? This is the rule that will be used, any rules below a rule that matches will not be evaluated.
So I want to ping IP in dmz.. Lets walk down you rules.
1st anti lock, nope dest is NOT your my lan address, nor is it to port 443 or 80, so skipped
2nd rule anything from my lan net to anywhere - well dmz fall into any (*) and its ipv4, and dest is also any.. So up allowed and rule matches.no other rules looked at.. So yeah you can ping something in your dmz.
-
After change rule order, it works better.
The most restricitive rules need to be on top, the other after, integrate for next time.My setup is like this:
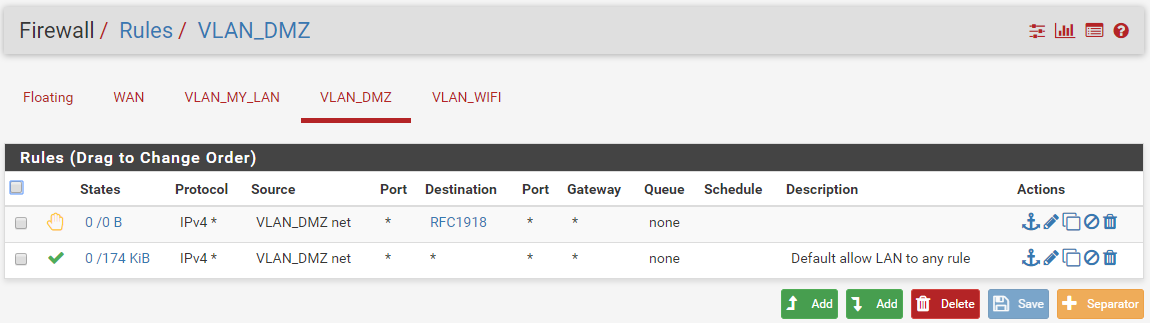
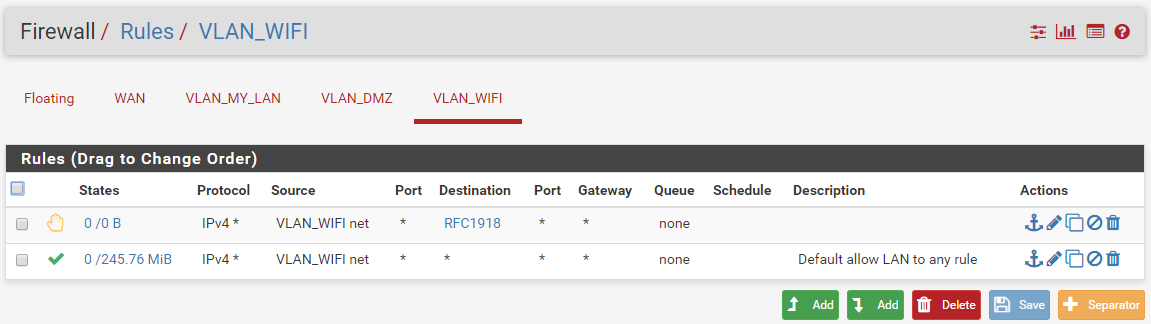
About DNS, i'm still able to ping google from workstation in VLAN MY LAN or ping server in VLAN MY LAN from workstation in VLAN MY LAN.
From my understanding, all gateway use DNS resolver to make it possible? that's why it's still working?I already created one rule in floating section, how these rules will be applied versus other rules in other LAN section ? does floating rule are upper than all other LAN section?
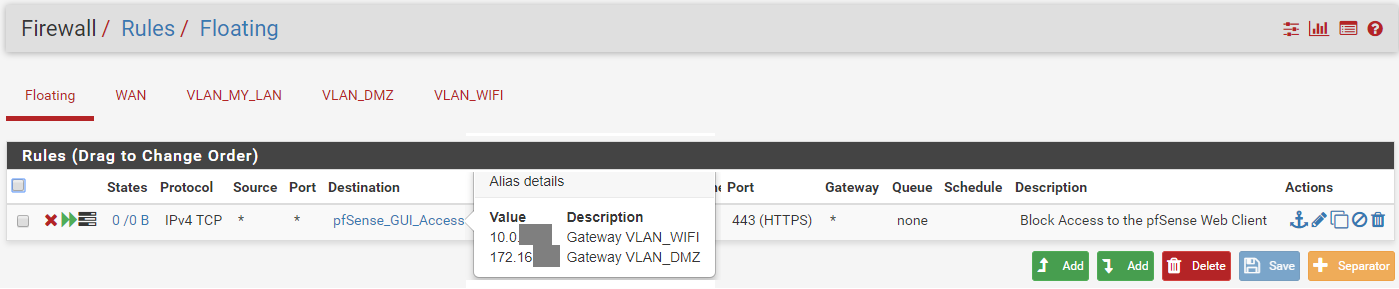
About Anti-Lockout Rule, it was present by default, i don't understand what does it do...
It seems to allow all traffic to VLAN MY LAN on http/https, but i dunno why.
Does it make sens to keep it?Many thanks for your help
-
The antilock out rule makes sure you do not lock yourself out of the web gui.. or ssh so you can admin the firewall.
From my understanding, all gateway use DNS resolver to make it possible? that's why it's still working?
No that is not why is still working.. Look at your rules.. Your blocking all access to any rfc1918 address, if you correctly make the alias.. What is the IP your using for dns? If its pfsense IP say 192.168.1.1, then that rule wold block it.. So how would you ask pfsense for dns..
Now maybe your client has the IP cached for google, so it didn't have to ask dns to know what IP to ping.. That would be my guess.
And no you don't always put most restrictive on top.. It DEPENDS on what your wanting to do.. Again follow the order of the rules to figure out how they need to be ordered to do or block what your wanting to block or allow.
As to floating those rules are evaluated before rules on your interface, but they may or may not be "quick" it is all documented. I suggest you read over how rules are evaluated.
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-processing-order.html
-
You are right...
With this rules, i'm not able to ping my own gateway when i am in VLAN_MY_LAN.
Even if all LANs was isolated, i was figuring that i would be able to ping each gateway when i was into this LAN...
Does i need to modify the reject rules related to be able to ping it ? or i need to create one more rules for it ?For DNS, i have registered it in workstation IP setup, i add DNS IP manually, i think that why i was able to have DNS resolution without issue.
So i understand the rules that you added.
In Green, this rules allow you to ping the default gateway when you device is on the same lan, right ?
In Blue, this is to allow DNS request if a workstation is using the gateway as DNS in his IP setup, right ?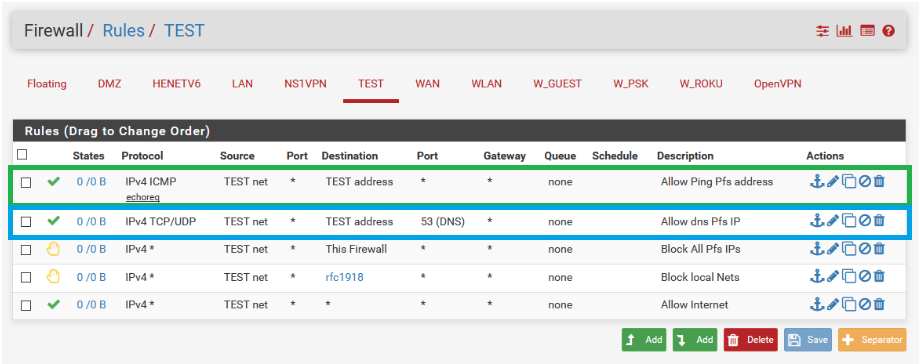
You put these rules before the rejected rules rfc1918 to be sure that they keep in count.
Could you tell me what is TEST address as Destination on both ? it's another alias ?
Is it possible to edit each rules to be sure to replicate it please ?Best Regards.
-
Up, please advise :)
-
You are correct, and that is how they are labeled.
Green allows ping, which is labeled "Allow Ping Pfsense Address" even ;)
You put the rules above the rejected, because as I have stated multiple times rules are evaluate top down.. So yes if you want to ping it needs to be evaluated be a rule that says reject anything to any rfc1918 address ;)
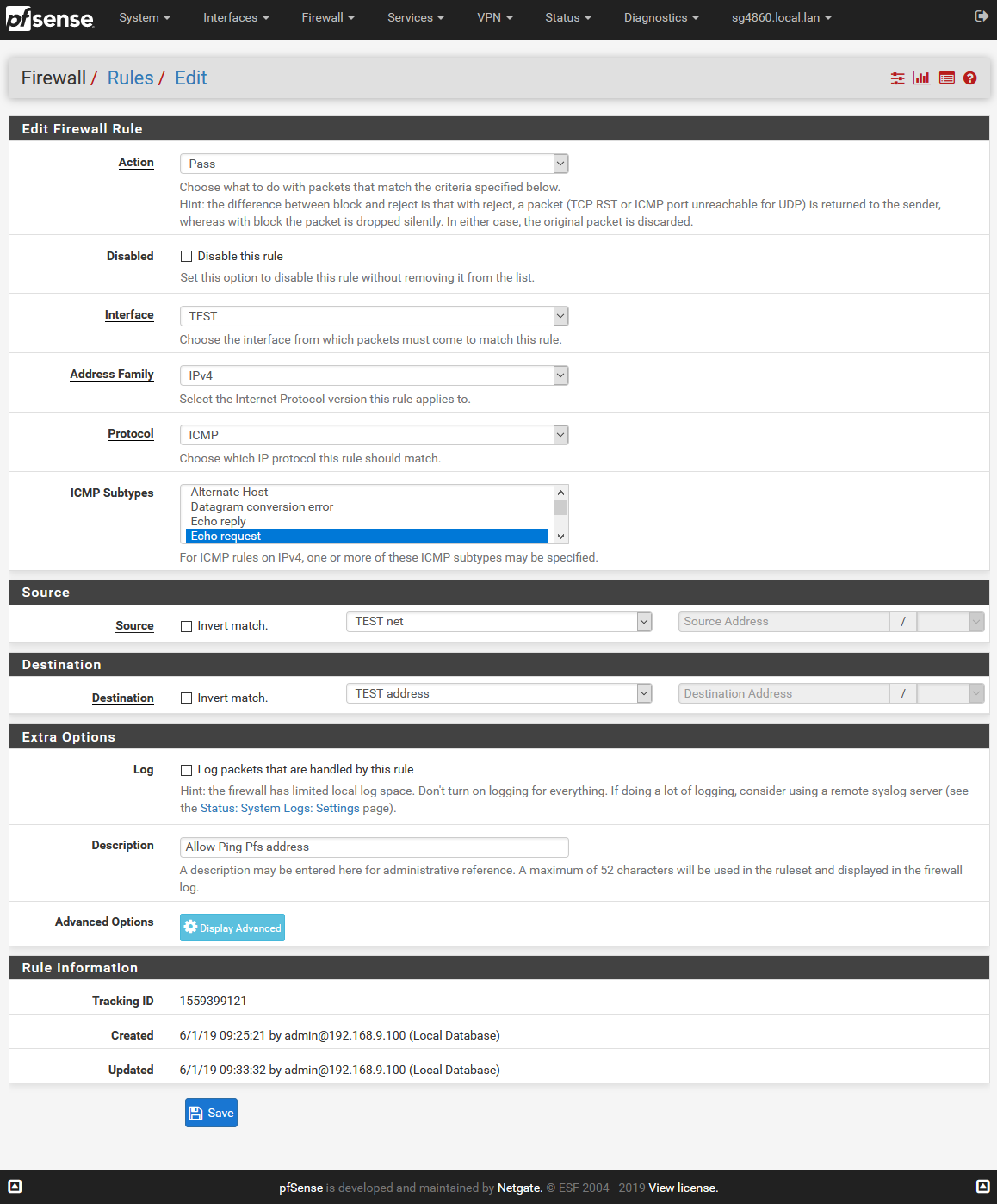
There is nothing to replicate.. The info shown is exactly what you would need to set in the rule.. Don't touch anything else in the rule ;)
The Test address, is pfsense IP on the interface called Test.. in this case its 192.168.100.1 As to what test address or net are, those are the built in aliases for any interface you have on your pfsense. like lan net or lan address. So in my case address would be 192.168.100.1 and net would be 192.168.100.0/24
here
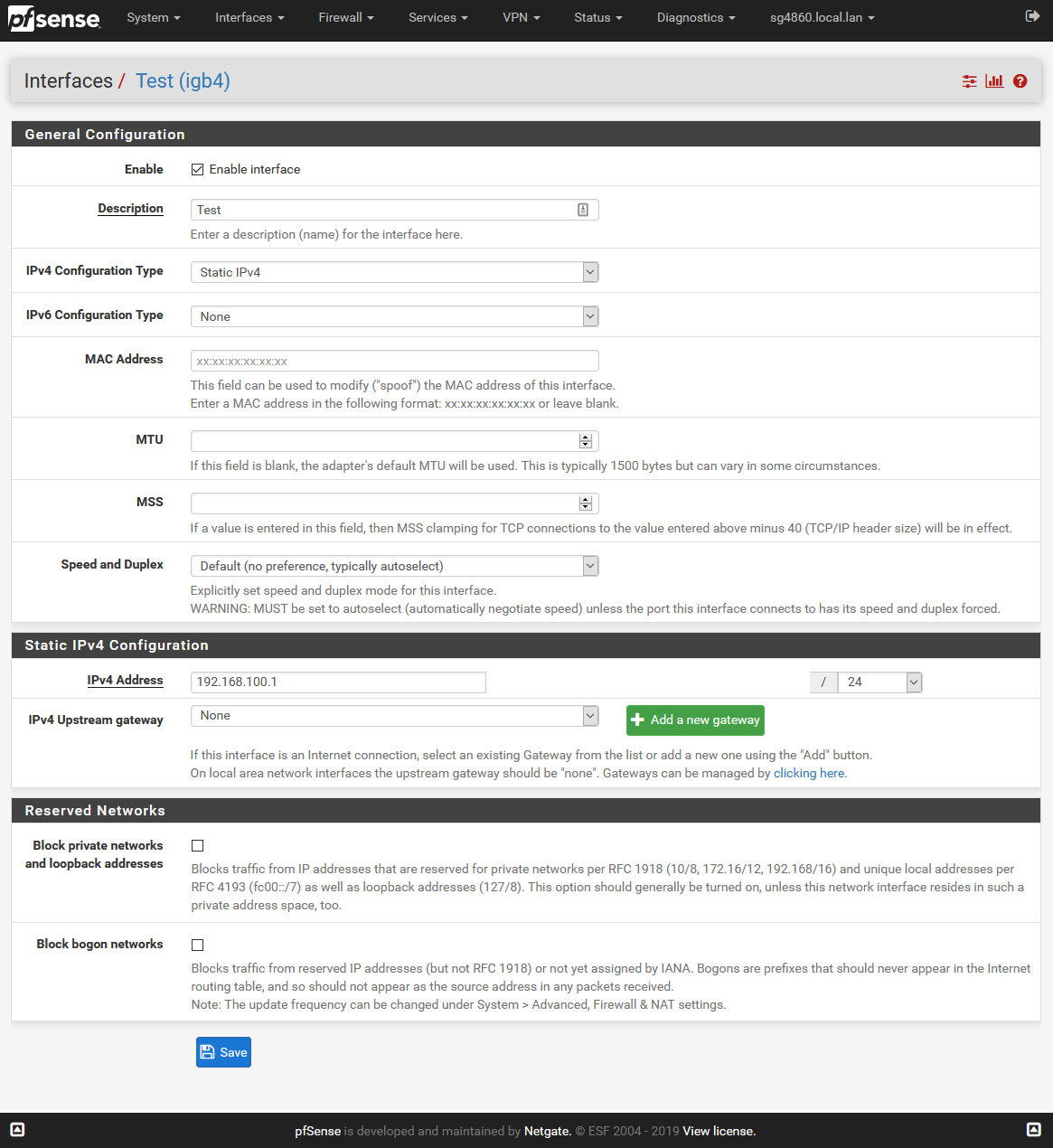
-
Many thanks for your help, it works fine.
You help me a lots.