Can access web server externally, but not from LANs.
-
https://www.netgate.com/docs/pfsense/nat/accessing-port-forwards-from-local-networks.html
-
@PITS_King said in Can access web server externally, but not from LANs.:
but I believe services like the Virtualmin UI has to be accessed via a port number (10000).
Yeah but external that could be 443.. And that is just what webmin defaults too it could be changed to standard 443.
No its not anywhere close to what I would consider a typical setup ;) Its just a bit much all in 1 post/question that is all over the board about multiple things at once.
Why do you have 53 open to the public internet? Are you running an authoritative NS for some public domain, or provide dns filtering services to the public?
25 - your running mail server to the public internet? So your IP is non residential? Is not on the dynamic IP list, you have configured the PTR for it?
I think maybe you have stuff open to the public that doesn't need to be..
If you did not setup tagging then they are just native lans, but lan/vlan/network/segment all pretty interchangeable terminology.
I was unable to put it in AP mode, so it is handling DHCP on a different subnet. WiFi
Well that is going to cause its own grief for sure.. If you want wifi, then get an AP, or use something that can be used as one.. Any wifi router can be used as just an AP.. doesn't matter what "settings" they allow for.. You connect one of its lan ports to your network, turn off its dhcp server and give it an IP on the network your connecting it too.And no its not a "gateway" to be honest, if did your modem and your nat then gateway... Right now you just have it in nat router mode.
So you have 4 networks setup on pfsense.. with just any any rules.. So what is the point of segmentation?
-
This post is deleted! -
So are you running an authoritative NS? The only reason that 53 needs to be open to the public would be that or say running pfblocker something like pihole for outside your network users.
The optimal setup for wanting to use a public fqdn that resolves to say public 1.2.3.4 IP, would be to just use a host override so your internal dns resolves it to the rfc1918 address - say this 10.0.1.4 IP.
-
@johnpoz said in Can access web server externally, but not from LANs.:
So are you running an authoritative NS?
963 bytes of traffic while other NAT rules already handled several GB -> so no way. Not a name server on a local LAN.
Most ISP will block the access to port '53' - mine does. Normally, these do not have their place at an @home or 'work' network.Note : I guess it's a SOHO network because of the presence of a "WLAN "network.
My first reaction was, seeing all the WAN interfaces (NAT) rules : the mstsc or RDP is missing !
Very nice : ESXi and MySQL are listed !No advise from my side, but I will light a a candle for @PITS_King when I come home.
-
Yeah there are lot of ports open there that shouldn't be most likely, and prob not even needed at all.
Openvpn to server behind is going to be pain the ass to access other boxes on his network with.. He made no mention creating the routes that would be needed to do that, etc.
Looks like he has openvpn open to pfsense, so why would you want/need to server behind?
-
This post is deleted! -
@PITS_King said in Can access web server externally, but not from LANs.:
I found my ISP is illegally blocking inbound SMTP on 2
Don't feel mistreated. That happened to all of use on planet earth since ... 2005.
Basic ISP's do not accept incoming (to you) connections to your own mail servers - and also : you can only use port "25" outgoing connections to a mail server handled by your ISP (and no other 25 mail servers).
They finally understood that "port 25 connections" should be reserved for communication between real mail servers.
Mail clients on your LAN(s) should use port 587 or (better) port 465 to deposit mail for transport.Also : the IP's used by ISP's are all listed in databases, and no serious mail server will accepts mails from these IP's because they are listed. This means : mail servers like Microsoft (MSN, Oulook, Hotmail, etc etc), gmail, Yahoo, etc etc will accept mail from your mail server.
Do you really have a mail server running on your LAN's ? You https://www.mail-tester.com/ to send that site a test mail from your server, and checkout the results ... ^^ (did you get the 10/10 ??)
If you really want your own mail server (and name server for your domain(s)), I advise you to rent a small VPS on the Internet.
Then you can amuse** yourself with 'postfix' and 'bind' -
This post is deleted! -
This post is deleted! -
I guess you can remove (== red) these :
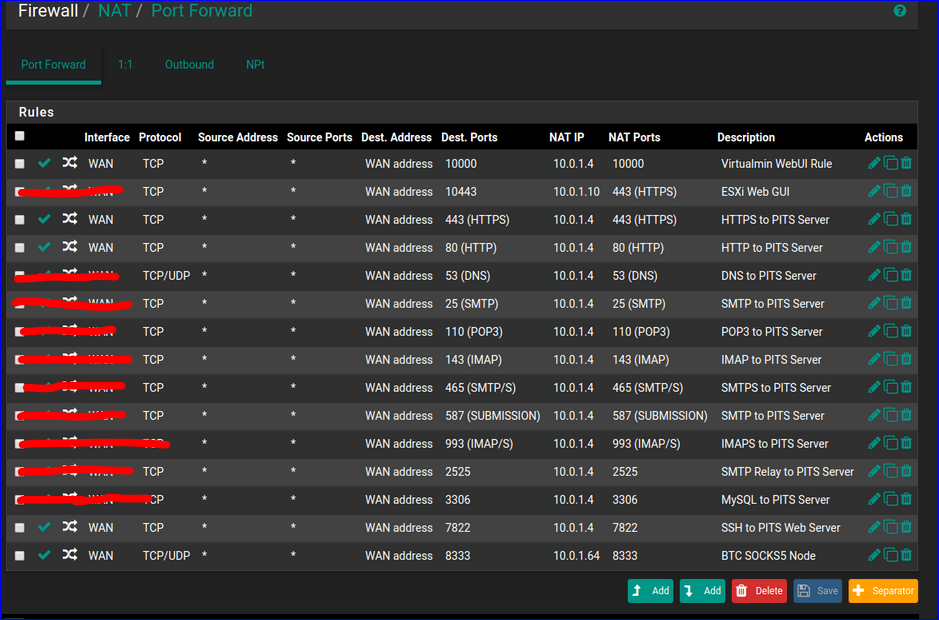
As you already have a - or 2 - incoming VPN connections, I advise you to remove blow up every NAT rule.
If needed, you have access to everything from the outside, using VPN. -
@PITS_King said in Can access web server externally, but not from LANs.:
is illegally blocking inbound SMTP on 25,
No I don't think it can be considered illegal, as Gertjan stated pretty much all residential connections block this and even if they didn't as Gertjan also correctly goes over wouldn't do you any good, other then sending to maybe some smaller domains. All the major player will not accept mail from you anyway.
Many home isp connections clearly state in their TOS that you are not to run servers.. So they can just not allow those ports since its in their TOS that your not suppose to do it, which you agreed to when you signed up be it you read them or not.
Even open - your isp not going to allow you edit your PTR for your IP, and when that doesn't match the name your mail server gives when trying to send mail, would also be denied - your just some want a be spammer in their minds.. Since any real mail server would follow all the RFCs in running a mail server, etc.
The software your running is designed to be run on a public connection... And then sure if you were running those services they would have to be open on your firewall.. But you would want or really need those open on a HOME connection..
If I get a few minutes here today, will draw up a basic connection drawing and we can work from there on getting your services working locally. And then how to get the services you do want/need to provide to the internet that make sense and can be done realistically..
But also as @Gertjan correctly mentions - if you want to play with some of this stuff and serving up to the public you prob better off doing that on VPS somewhere then off your local "home" connection be it mail or other services.
Lets start with your local stuff working and accessing your local resources be a fqdn you want to use.. So if that is the case you could remove ALL of those port forwards.. Port forwards are only required for access externally not for lan to other lan access.
-
This post is deleted! -
What is the source address of the client you are testing from?
What is real IP address on the server you are trying to connect to?
What port are you trying to connect to?
How are you testing?
What is the result?
How many FQDNs to the WAN address are we talking about?
Please limit your answer to one port on one server only. Fix that and you'll probably know how to fix them all.
-
This post is deleted! -
What did you do with the Redirect IPv4 Gateway - Force all client-generated IPv4 traffic through the tunnel checkbox in the server configuration?
If unchecked (or if you have set the equivalent of Don't pull routes in the client configuration) what are the Local Networks defined in your OpenVPN server.
One issue at a time please. Please provide as much detail as possible. You have the benefit of being able to choose the first one / prioritize.
-
This post is deleted! -
This post is deleted! -
If you have Redirect IPv4 Gateway checked AND you are not telling the client not to pull routes, you do not need any custom options to push any routes. You will get two routes on the client into the tunnel 0.0.0.0/1 and 128.0.0.0/1. That covers all IPv4 addresses without clobbering the client's default route. The netmask is longer (/1 is longer than /0) so those routes are preferred in the routing table over 0.0.0.0/0.
With that in place, connect to the VPN and attempt a connection (a single connection like to http://10.0.1.4:10000/ (or https or whatever it is supposed to be).
What, exactly, happens.
Then go to Diagnostics > Packet Capture and set the following:
Interface: The interface the server is on. The 10.0.1.0/24 interface
Host: 10.0.10.0/24
Port: 10000
Count: 100000Start
Test connecting to 10.0.1.4:10000 and let it fail
Stop the capture. What do you see?
If you see nothing, move the packet capture to the OpenVPN interface and do the same thing. What do you see?
-
An aside: you should not be using Custom Options to push routes. You would use the Local Networks form field that would become visible if you unchecked Redirect IPv4 Gateway