IPSec Site to Site with peer behind CGNAT
-
It is a bit of a weird setup but i am kinda stuck with it:
Site 1:
- pfSense being our internal router, this is the target IPSec host. However, it is setting behind Unifi USG 4 Pro (with Public static IP address).
Unifi config:
*port forwarded 500, 4500 towards WAN interface if pfSense.
*Firewall WAN IN EH & ESP accepted
Site 2:
- Huawei AR502 4G Modem on a remote workshop, this device is CGNATed.
I was wondering if a Site-Site IPSec would be possible ? would the pfSense being HQ would accept a remote gateway of 0.0.0.0 (Responder Only checked)?
Or do i need to enable Mobile Remote Access VPN for this to work?
P.S1: Huawei VPN Wizard shows the following usage scenario, i was wondering if it is expecting the Site-Site to have both ends with public IP addresses? and Branch Site is more like the Mobile Remote Access option in pfSense?
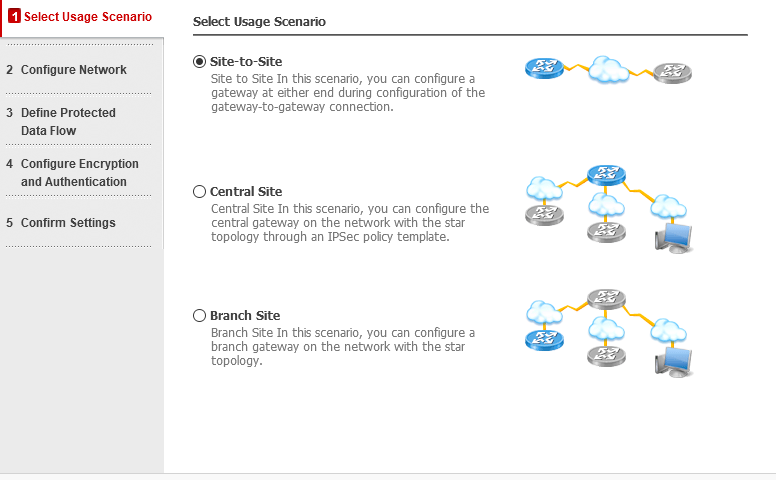
- pfSense being our internal router, this is the target IPSec host. However, it is setting behind Unifi USG 4 Pro (with Public static IP address).
-
@mohsh86
Hey
Yes , it is possible to do
There are two options- to try to use Dyndns (I'm not sure if this will work correctly if the client's ip address changes)
- make manual changes to the PFSense configuration file so that you can establish a connection ( site-to-site) from any ip address ( non-fixed ip), as is done for the mobile clients (This option works fine , but every time you update PFSense, you need to make changes to the file again)
-
For anyone who is interested (n00b here), i got it to work (branch to pfsense only):
Phase 1 remote subnet on pfsense has to be 0.0.0.0 with responder only option checked.
on Huawei Side, the following command had to be configured:
ipsec authentication sha2 compatible enablethe result is:
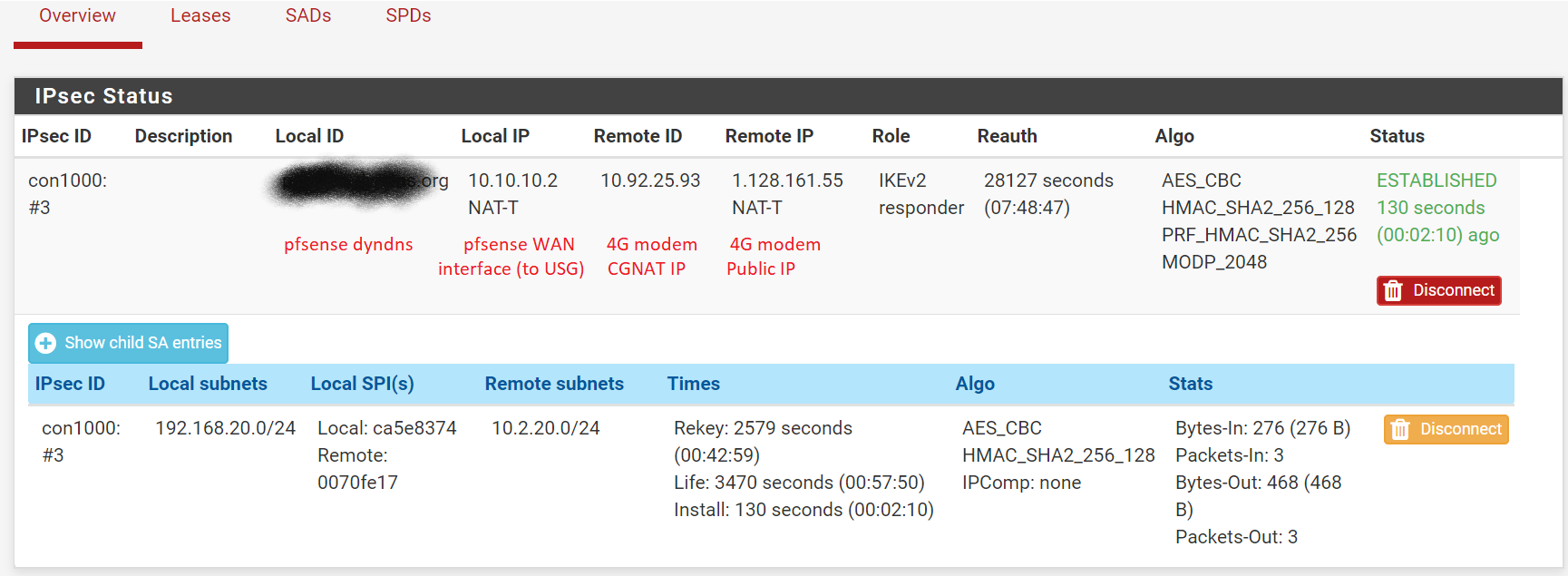
The problem now is that pfsense does not direct traffic with destination to remote subnet (i.e. 10.2.20.0) through IPSec, it uses WAN0 for that. any ideas?[update] working now, was pinging from the wrong device.