NAT 1:1 Polycom VSX 7000
-
You need to look into the SIP protocol and see what it's doing.
-
Yes, you would need to filer additionally by port 5060 and then download and check the actual SIP packets to see what is being sent. You probably don't want to post that publicly though.
Steve
-
What would the tcpdump command syntax look like, just to filter everything to my wan-ip port 189.20.108.XX port 5060?
-
I would do it from the GUI but: https://docs.netgate.com/pfsense/en/latest/monitoring/performing-a-packet-capture.html
Steve
-
Hi Steve, how are you?
I monitored a connection made by my videoconferencing system, using "pftop" CLI my polycom connects with the target, but "NO_TRAFFIC: SINGLE" communication errors occur.PR DIR SRC DEST STATE AGE EXP PKTS BYTES rsvp In 192.168.40.251:0 140.242.250.200:0 NO_TRAFFIC:SINGLE 00:15:15 00:00:19 0 0 tcp In 192.168.40.251:3233 140.242.250.200:1720 ESTABLISHED:ESTABLISHED 00:07:57 23:58:04 15 1096 tcp Out 189.20.108.XX:3233 140.242.250.200:1720 ESTABLISHED:ESTABLISHED 00:07:57 23:58:04 15 1096 tcp In 192.168.40.251:3234 140.242.250.200:3242 ESTABLISHED:ESTABLISHED 00:07:57 23:59:35 181 10480 tcp Out 189.20.108.XX:3234 140.242.250.200:3242 ESTABLISHED:ESTABLISHED 00:07:57 23:59:35 181 10480 udp In 192.168.40.251:3232 140.242.250.200:3262 NO_TRAFFIC:SINGLE 00:07:56 00:00:30 19850 13004860 udp Out 189.20.108.XX:3232 140.242.250.200:3262 SINGLE:NO_TRAFFIC 00:07:56 00:00:30 19850 13004860 udp In 192.168.40.251:3231 140.242.250.200:3261 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 7220 udp Out 189.20.108.XX:3231 140.242.250.200:3261 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 7220 udp In 192.168.40.251:3233 140.242.250.200:3263 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 9120 udp Out 189.20.108.XX:3233 140.242.250.200:3263 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 9120 udp In 192.168.40.251:3235 140.242.250.200:3265 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 7220 udp Out 189.20.108.XX:3235 140.242.250.200:3265 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 7220 udp In 192.168.40.251:3237 140.242.250.200:3267 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 7240 udp Out 189.20.108.XX:3237 140.242.250.200:3267 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 7240Best regards,
Wesley Santos -
That's not necessarily an error but you would expect more traffic when it connects correctly.
I would bet it's sending it's internal private IP still we've seen that many many times. Including numerous times when a VoIP provider told us it definitely wasn't and we had to prove it was using packet captures.
We would need to see the SIP packets to be sure.
PM them to me if you prefer. I'll take a look when I have time.
Steve
-
can i send you a .pcap packet capture for you to help analyze?
-
Yes, start a chat and attach it there.
-
not allowed, your chat is restricted to people you follow only
-
Post whatever it is you think is telling you that. If that is the case it should not be. People chat me all the time without following.
-
ERROR
This user has restricted their chat messages. They must follow you before you can talk to them -
Hmm, must have changed the default at a forum update or something. I've changed that setting now, try again.
Steve
-
Your chat is now released.
-
Dear, I made the capture available on Google Drive
-
Great I have that.
There are no SIP packets in there so I can't check that directly but it looks like it's still sending it's internal IP as the address to connect back to which can never work. For example:
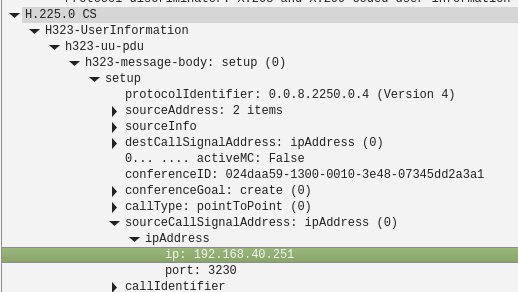
And:
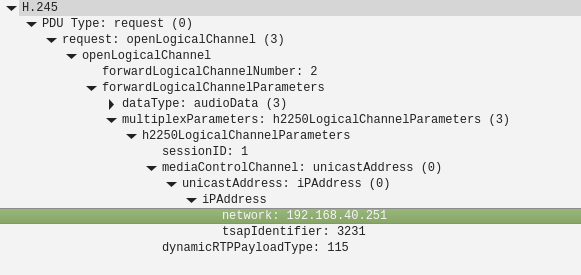
I won't to be any sort of expert in those protocols but from your description of the behaviour and the fact we see only outgoing RTP traffic in the pcap I think it is not configured to send the external IP.
You need to set that correctly in the Polycom device before it can work behind NAT.
Steve
-
Hi, thanks for your effort to help solve my case.
Please can you explain if I used the filter correctly, I intended to monitor only LAN-ip traffic, using a filter for polycom IP address "192.168.40.251", when NAT requests occur, they should be caught in tcpdump using the command filter below?tcpdump -nvxi re0 -w capture.pcap host 192.168.40.251I captured packets from the WAN-ip interface, using a filter for WAN-ip and LAN-ip addresses, but when analyzing wireshark did not find NAT requests, I will forward the link of this packet in your chat.
I used the command below.tcpdump -nvxi sk1 -w new.pcap "(host 189.20.108.XX or host 192.168.40.251)"Best regards,
Wesley Santos -
It has nothing to do with the filter.
The PBX is telling the far side to connect back to 192.168.40.251 on port 3230 for RTP.
Obviously the far side cannot do that because that is your inside, non-routable, RFC1918 address.
You need to tell the PBX to send your outside WAN address there instead.
It is embedded in the SIP protocol. NAT can't translate it and there is no SIP ALG in pfSense to do it for you either.
-
Hey man, how you doing?
I reviewed all NAT settings applied to "Polycom VSX 7000", also restored the applied settings and configured them again. I can not understand what I am configuring wrong with NAT inside the pfsense firewall, the polycom NAT settings are very simple, below are some pictures of the polycom NAT settings.LAN properties.
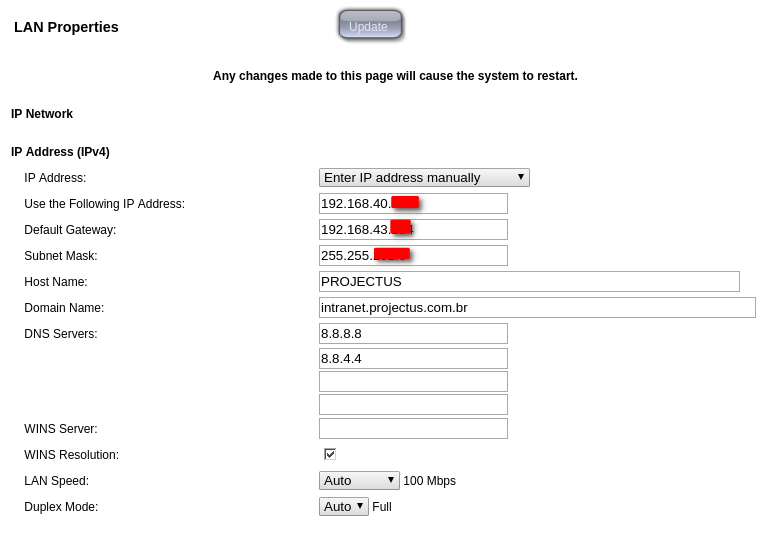
Polycom NAT Settings.
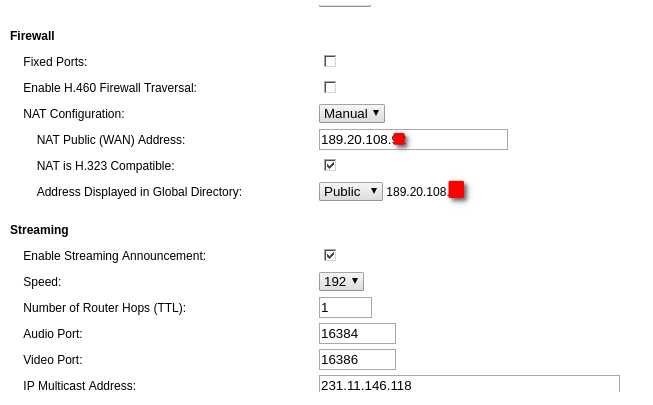
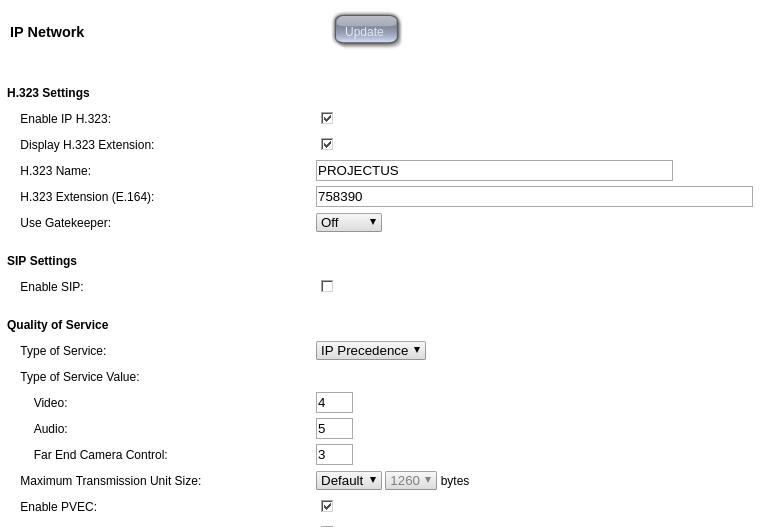
Best regards,
Wesley Santos -
Sorry. I don't read Portuguese.
-
https://community.polycom.com/t5/Video-Endpoints/VSX-7000-Connection-Issue/td-p/36896