New xg-7100 owner stuck
-
So I have been a fan of pfSense for years, and finally upgraded my gateway device from a 4-port microcomputer to the xg-7100. I knew it would be a challenge using switchports over nic's. I have 6 subnets, 6 VLANs, and I ran them as a ROAS between the microcomputer and a cisco 3560G. The ROAS was also a port-channel containing 2 etherchannels. Im stuck trying to duplicate this in the xg-7100.
The BLUF is that I am seeing plenty of traffic through the cisco switch without errors, but none of my devices are able to get an IP address from the xg-7100 (all self-assigned 169.254.226.160) or ping/reach any of the xg-7100 interfaces.
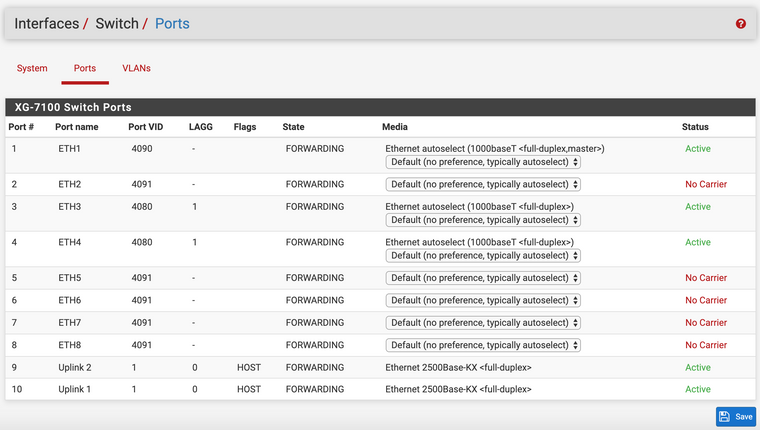
FYI, I connect to ETH2 (direct access for troubleshooting), DHCP works and I can access internet.
The screenshots below are from my last attempt when I simplified it and removed the port-channel, just using 1 trunk between the xg-7100 and 3560 (ETH4). I followed a similar issue here, but am not having any luck.
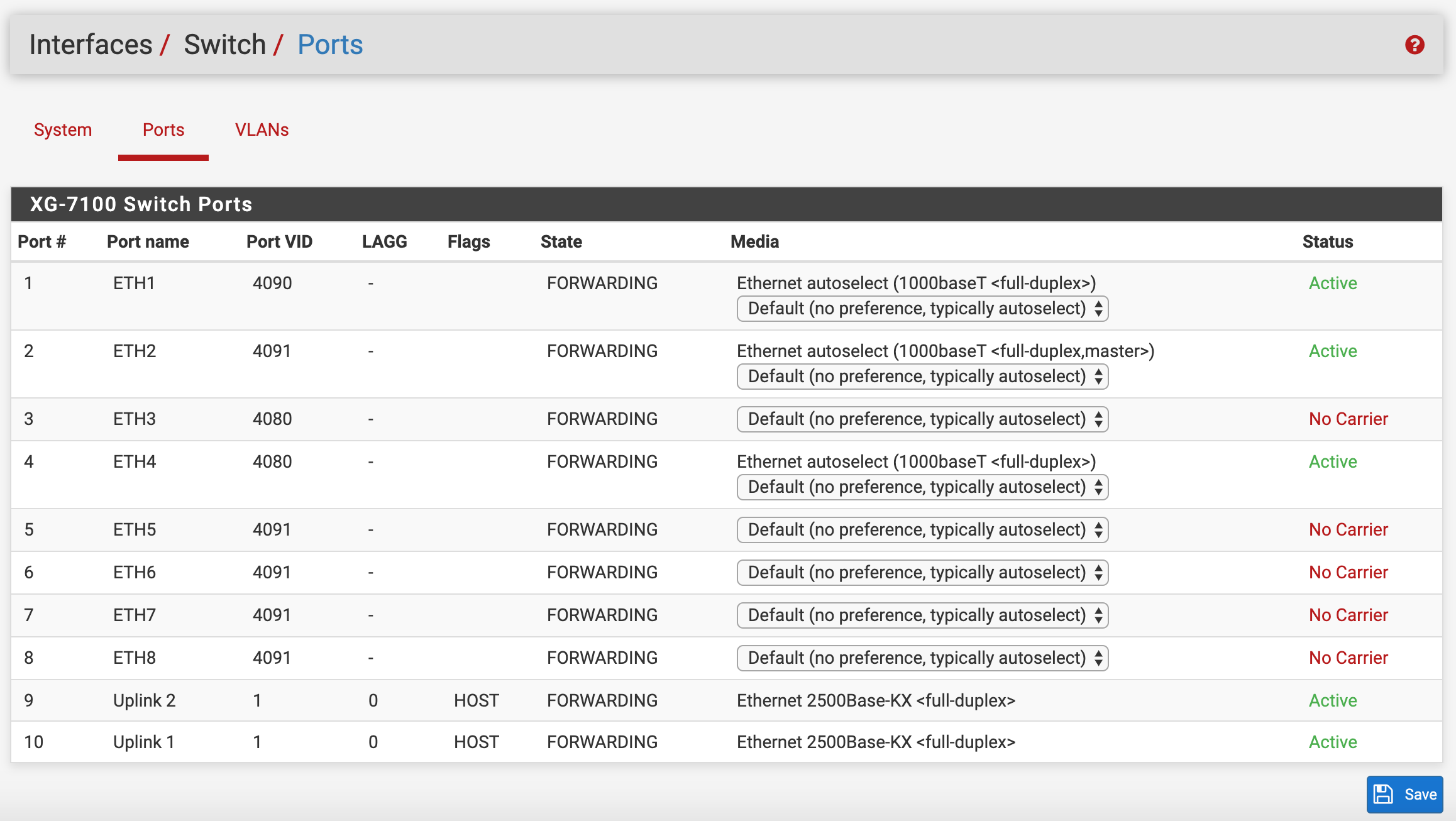
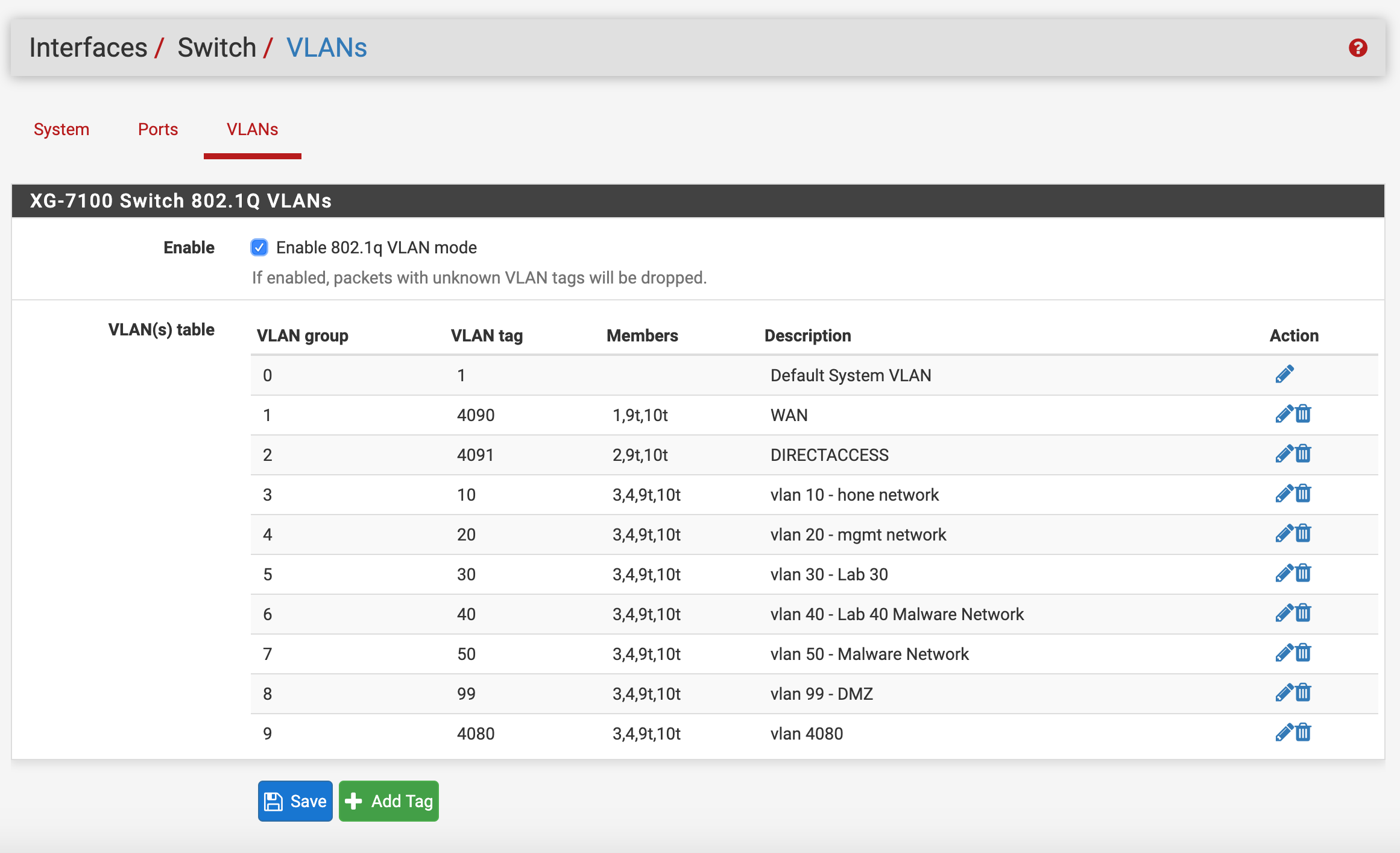
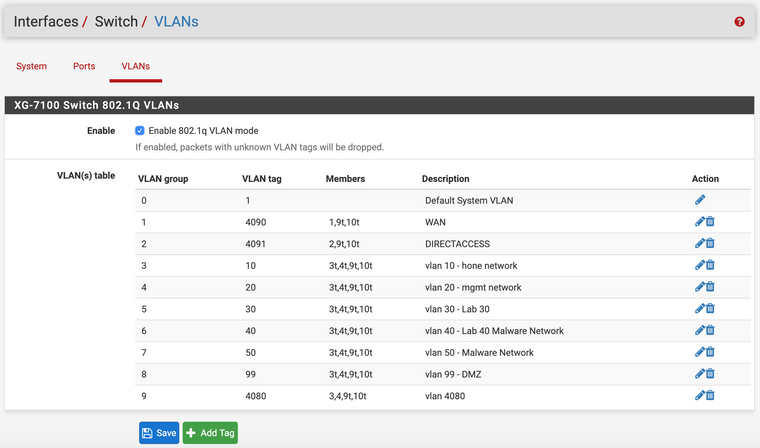
I started by creating the switch vlans
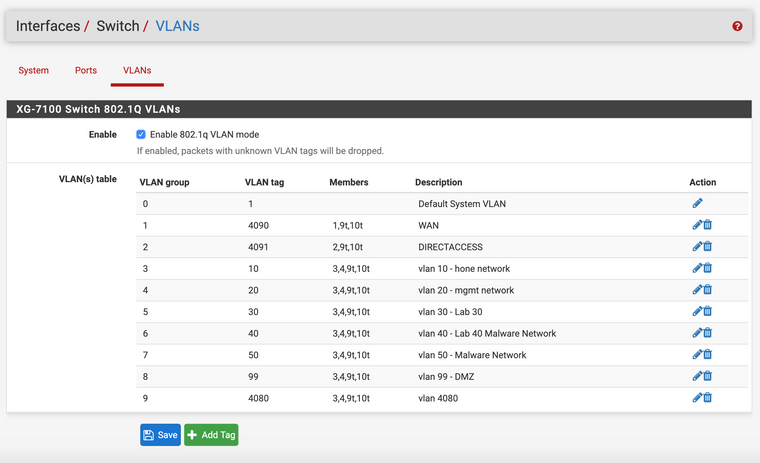
I have tried this configuration without switch VLAN 4080, but just recently added that on my last try.
I made the PVID 4080 on switchport 3 and 4, but my last attempt was with only 1 trunk and no port-channel (on the 3560). I also tried it with LAGG 1 on both switchports 3 and 4.
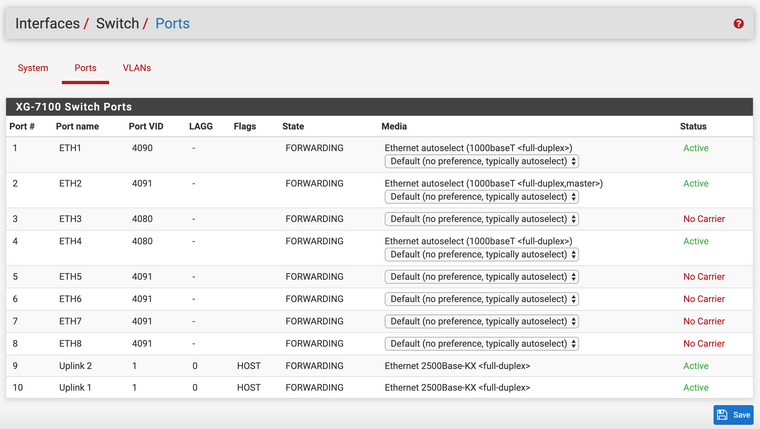
Attempted with a single trunk on G0/15 as well as a port-channel with G0/15-16 in it.
# Global port-channel load-balance src-dst-ip spanning-tree mode pvst spanning-tree extend system-id interface GigabitEthernet0/15 description trunk to xg-7100 switchport trunk encapsulation dot1q switchport trunk allowed vlan 10,20,30,40,50,99 switchport mode trunk switchport nonegotiate duplex full spanning-tree portfast trunkWhen I tried it with the port-channel:
interface range GigabitEthernet0/15 - 16 description interfaces in port-channel group 3 xg-7100 ROAS switchport mode trunk switchport trunk encapsulation dot1q switchport trunk allowed vlan 10,20,30,40,50,99 channel-group 3 mode on spanning-tree portfast trunk interface port-channel 3 description port-channel to xg-7100 switchport trunk encapsulation dot1q switchport trunk allowed vlan 10,20,30,40,50,99 switchport mode trunk spanning-tree portfast trunkNote: cisco's output showed 0 errors on the cisco interfaces 15 and 16 and the po3 showed no errors either.
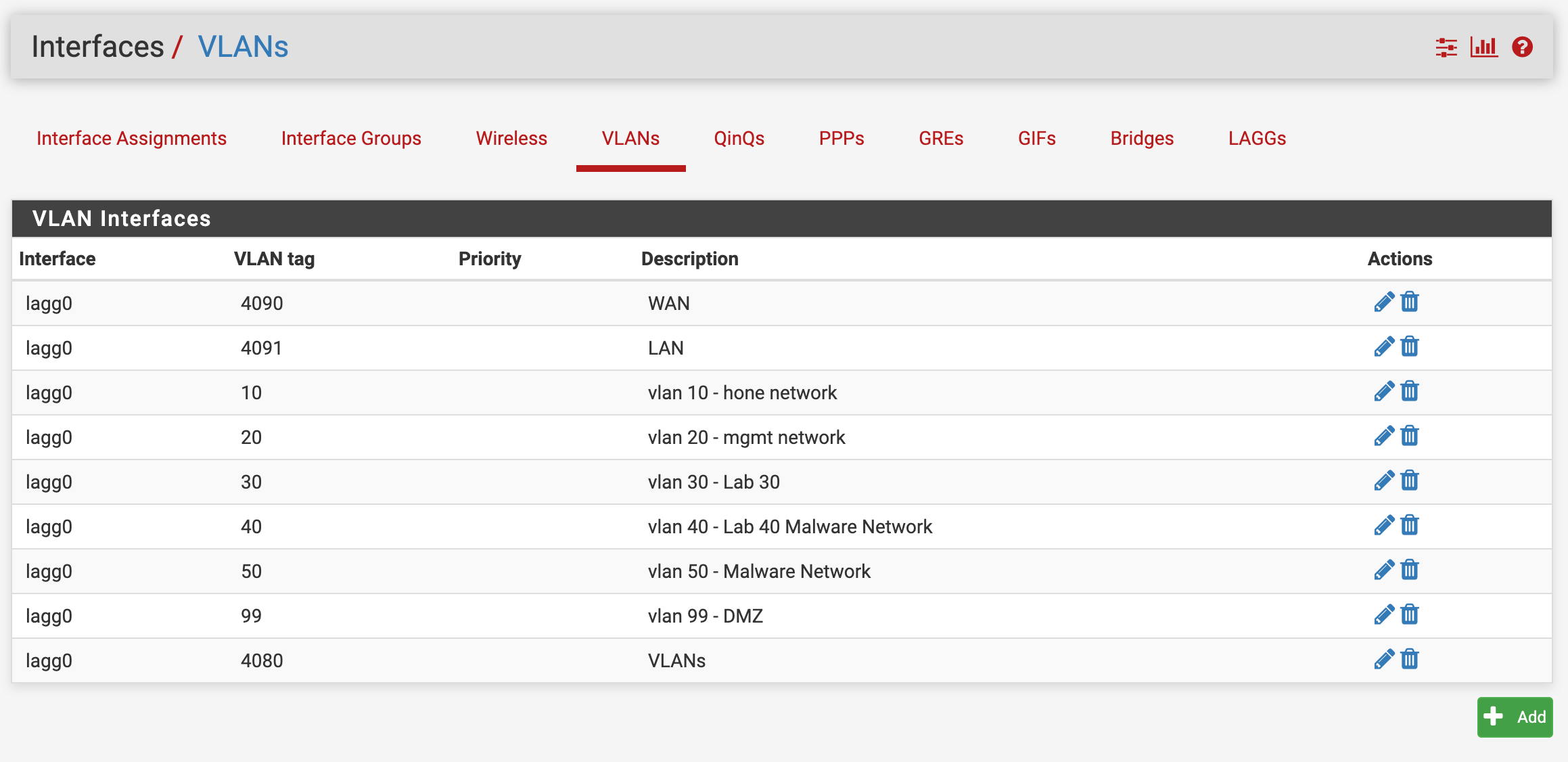
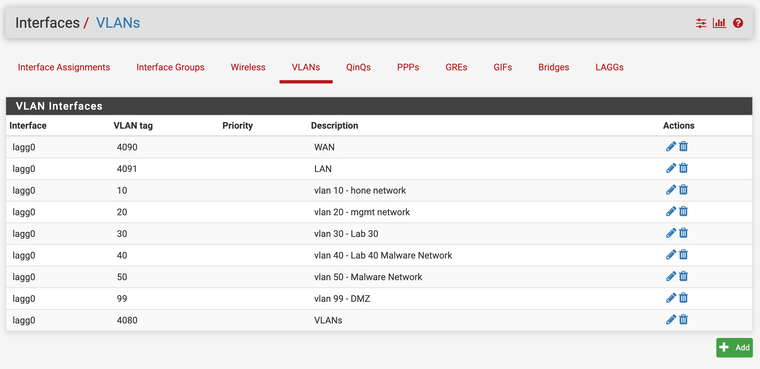
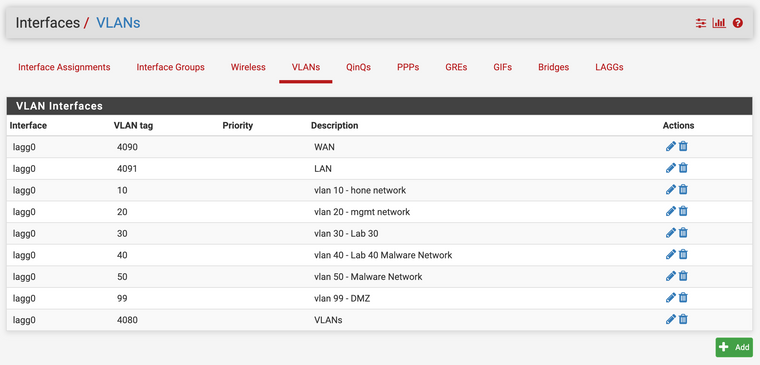
show interface counters errors Port Align-Err FCS-Err Xmit-Err Rcv-Err UnderSize OutDiscards Gi0/15 0 0 0 0 0 0 Gi0/16 0 0 0 0 0 0 Port Single-Col Multi-Col Late-Col Excess-Col Carri-Sen Runts Giants Gi0/15 0 0 0 0 0 0 0 Gi0/16 0 0 0 0 0 0 0I created the interface vlans
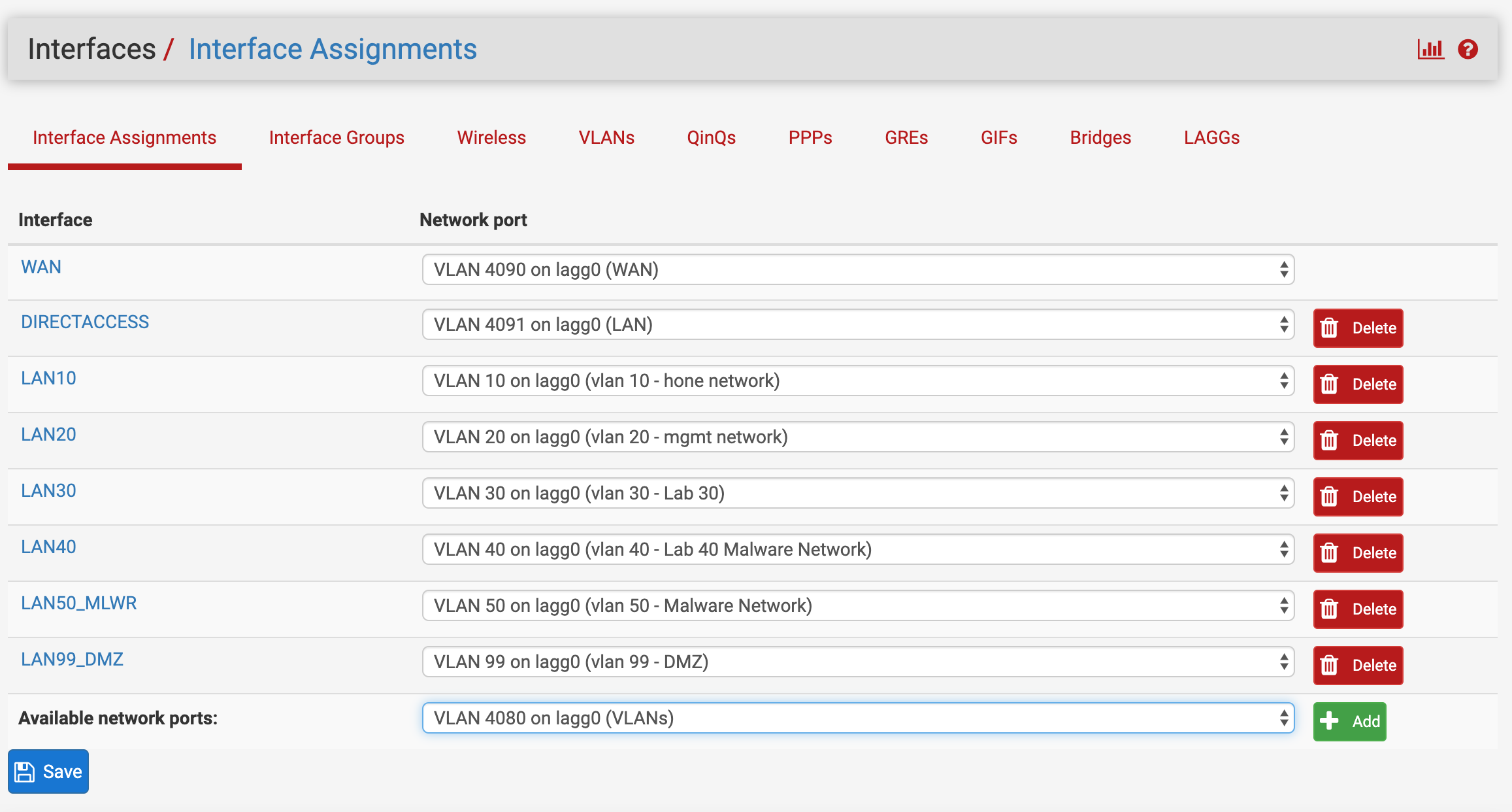
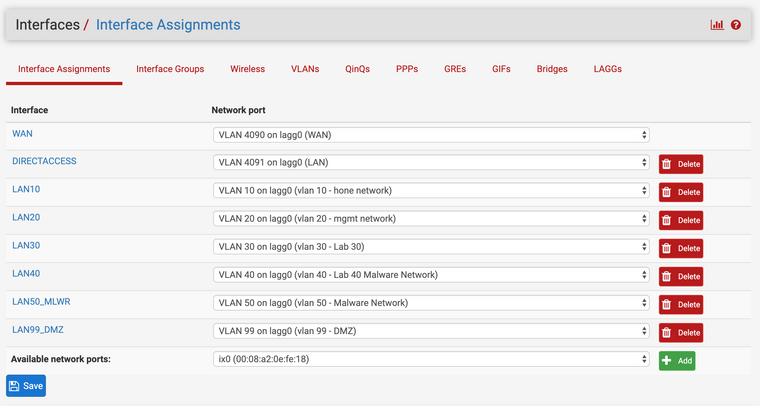
Then I assigned the interfaces
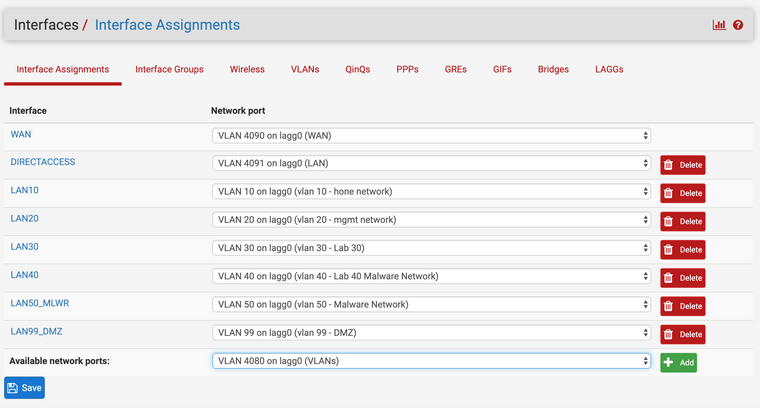
Any input as to what I am missing is appreciated. Do I need to enforce tagging on switch VLANs 10,20,30,40,50,99 (ie 3t,4t,9t,10t)? Do I need to assign and enable an interface for the 4080 VLAN or the lagg0(uplink)?
Forgot to post this info:
I can see the DHCP requests and offers in the pfsense dhcp logs, but the clients end up with the self-assigned IP, and the DHCP Leases dashboard will show a few clients as offline. After leaving it run for a while, the DHCP dashboard was empty. -
Solved it. When adding the switch VLANs, making members 3, 4 tagged enabled the hosts to communicate. See below for screenshots of working trunks.
port-channel load-balance src-dst-ip interface GigabitEthernet0/15 - 16 description etherchannels in port-channel group 3 xg-7100 switchport trunk encapsulation dot1q switchport trunk allowed vlan 10,20,30,40,50,99 switchport mode trunk switchport nonegotiate duplex full channel-group 3 mode on spanning-tree portfast trunk interface Port-channel3 description port-channel to xg-7100 switchport trunk encapsulation dot1q switchport trunk allowed vlan 10,20,30,40,50,99 switchport mode trunk switchport nonegotiate spanning-tree portfast trunk -
Yes, you can assign only one not-tagged vlan on switch port. I suggest you need one non-tagged - default vlan, and all other vlans can be only tagged on same interface.