DNS Forwarder - how to use non-default route.
-
I have multiple LAN segment. One of which is specially for VOIP
I use DNS Resolver for the segments that use a VPNI use DNS Forwarder for the VOIP segmant - so it should continue to function whether VPN is up or down.
This works great when the default route is WAN
Problem is, i am using squid, and squid passes out of the default route, which defeats the point of the VPN.
If i change the default route to VPN, DNS Forwarder is not working and the VOIP box can't register with providers.
Adding this segment to DNS Resolver fixes the problem, but only when the VPN is up.Question
Can i force DNS Forwarder to use the WAN instead of the Default Route? How? -
@gwaitsi I don't know if this is the best solution, but would welcome any feedback.
VOIP_LAN
- disabled DNS Forwarder
- set VOIP DHCP to use external DNS address
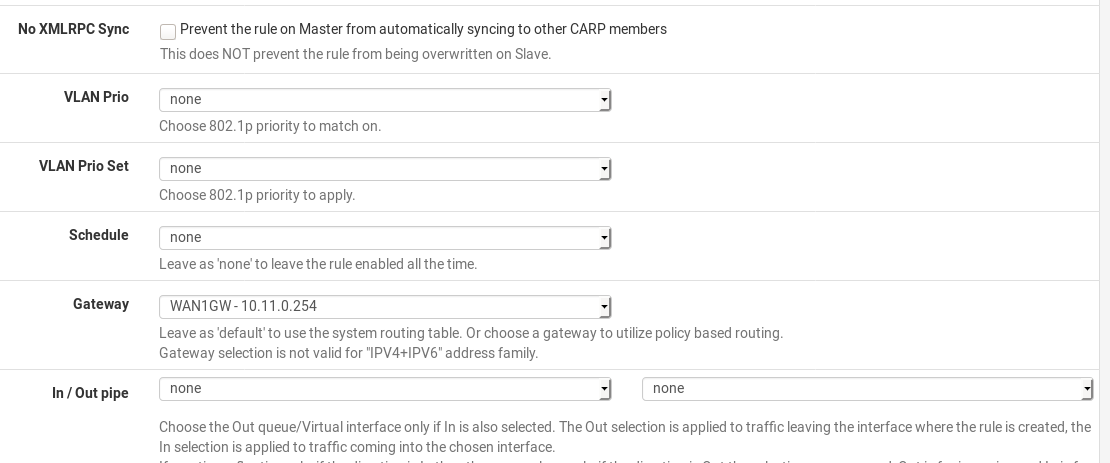
- set rule to pass DNS via WAN
- set rule to pass DHCP in VOIP LAN
- set rule to forward NTP to PFSENSE
- set rule to pass HTTP from device to VOIP providers via WAN
- set rule to pass voip_device to VOIP_addresses via WAN
- set rule to block * to *
LAN
- enabled DNS resolver
- set interface to LAN (excluding VOIP)
- set outgoing to VPN
- set relevant rules via VPN_Pool
- set rule to block * to *
- block HTTP and HTTPs from WAN
- set default gateway to VPN pool
- set squid+squard to use LAN (exclude VOIP)
- set squid to out going VPN
All seems to work as intended. i.e.
VOIP is up irrespective of VPN state
HTTP/HTTPS only works if VPN is up and goes via VPNIn terms of hardening or threats, i'd be interested to hear if i can tighten this any further or if what i have done is sufficient
-
@gwaitsi said in DNS Forwarder - how to use non-default route.:
Question
Can i force DNS Forwarder to use the WAN instead of the Default Route? How?Which DNS servers DNS Forwarder uses?
You can set gateway for each DNS server under System / General Setup
For example: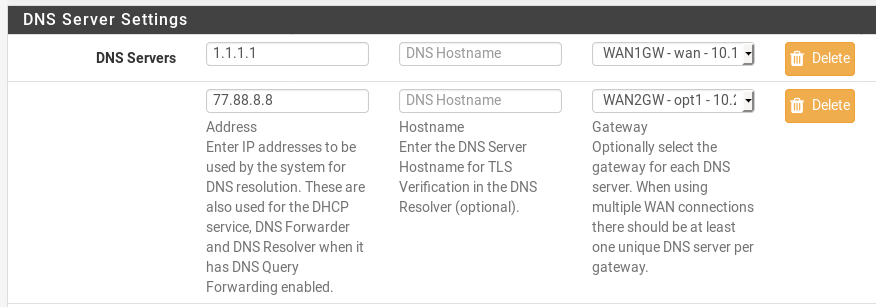
-
@viktor_g i have my dns servers configured like that, but seems DNS Forwarder only used the default gateway. I guess the WAN could be specified by the dnsmasq custom options fields, but not sure if it would accept alias.
-
@gwaitsi
You want to use ISPs DNSes by DNS Forwarder or some kind of public DNS?
Please explain.
Maybe you can use just static routes to needed DNS.And show Diagnostics / Routes
-
@viktor_g i thought i explained, but might not have been clear.
Environment
VOIP_LAN
LAN1
LAN2VOIP_LAN should go directly over WAN so as not to be interrupted by VPN outages.
LAN1and2 should go directly over the VPN (including DNS queries)original setup
LAN1&2 use DNS Resolver (where the outgoing interface is specified as VPN interfaces)
VOIP_LAN use DNS Forwarder with port forward from 53->5353 (no option to set outgoing interface)
Default Gateway was WANEverything worked as intended.
Then i introduce squid caching and discover outgoing from squid is over default gateway i.e. WAN
definitely not desired. So i have to set Default Gateway to VPN_PoolFrom general settings i have DNS configured for each interface i.e. WAN, VPN1 and VPN2
But the DNS Forwarder is actually forwarding over VPN instead of WAN (this means VOIP doesn't work when no VPN)
-
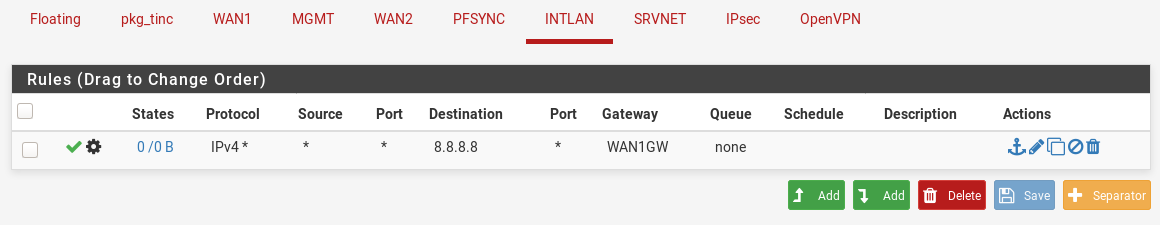
@gwaitsi you can configure policy based routing, by selecting gateway for appropriate network segment
see https://www.netgate.com/resources/videos/multi-wan-on-pfsense-23.htmlin such way you can configure to route through WAN_GW for destination 8.8.8.8 (needed DNS) on VOIP_LAN interface