Insert SG-1100 between existing cable modem and router
-
By default, WAN is configured for DHCP so it should get an address from your ISP (if your modem is in bridge mode) or from the modem itself (if it's acting as a router). You shouldn't have to anything other than plug it in and then configure the LAN interface.
-
Thank you.
Yes my router gets an IP from the service provider so understood that now the Firewall will get it.
So I set up my SG-1100 to essentially bridge out to the WAN input on my router, and the router continues doing what it is doing today, correct?
-
Essentially yes. In bridge mode, your cable-modem simply acts as a dumb conduit to your ISPs network.
-
@KOM Thanks. Is there a particular "mode" I need to configure in the SG-1100 so that all it does is pass data between the modem and my router (other than with the added functionality of the Firewall)?
Perhaps I'm making more of this than I need to.
-
The SG is already configured to route your traffic from WAN to LAN, if that's what you mean. There is no 'mode' to worry about.
-
Having problems making this work.
I followed the instructions to start up the SG-1100. I then went into the setup wizard and walked through it.
With a laptop plugged into the SG's LAN port, I can browse the internet so that tells me that the LAN port is getting out. The SG has a LAN IP of 192.168.1.1.
When I unhook the cable from the laptop and plug in the cable going to my wifi router (Ubiquity AirRouter), I get no connectivity downstream (even after restarting the router numerous times).
If I open a browser (on a PC on the LAN) and browse to 192.168.1.1, I get the AirRouter's configuration screen rather than the SG's setup screen. So there is an address conflict. And of course I can ping that address from the LAN.
I went back into the SG and set it's address to 192.168.1.2, thinking that would solve the problem, but no luck. From a LAN pc, I cannot browse to 192.168.1.2. If I ping it, I get a reply from 192.168.1.200 that the destination is unreachable. Not sure where that is coming from.
I did add 2 firewall rules to pass all TCP and UDP traffic; those rules sit below the built-in rules.
I am not sure exactly what to try next. Appreciate any help! Thanks.
-
There are several ways you could address this. For instance, you could give your laptop a static IP address of 192.168.1.2, 255.255.255.0 mask, no gateway and then connect your LAN port directly to the AP and then try to hit its web interface at 192.168.1.1.
Or you could unplug the AP and then get to pfSense WebGUI and change its LAN IP address and mask to 192.168.2.1, /16 mask. Also change your mask to 255.255.0.0. Then plug in the AP and hit its web interface.
Once you get to its interface, see if you can change its mode from the static 192.168.1.1 to DHCP. If not, then change it to 192.168.1.2. Turn off its DHCP server if one is enabled. You just want it to act as a bridge to LAN, and let pfSense handle giving out addreses. Make sure you have the DHCP server running on LAN and configured or your wifi devices won't get an address.
Once you have changed it, go back and restore your pfSense LAN settings to their original 192.168.1.1/24.
-
Good progress but not quite there.
I have my AP set up as a Bridge. SG gives each device (both wired and wireless) IP addresses via DHCP. I can ping any other device from any device, on the LAN. But nothing gets out to the internet (or back).
In the SG my Dashboard shows all green up arrows for everything, except OPT which I haven't done anything with.
In the Firewall, I added 4 rules: tcp and udp "pass" for both ip4 and ip6. They are green-checked. They are below the built-in rfc 1918 and reserved rules.
I suspect I have a something blocking traffic but not sure what.
-
Success! I realized I needed to create Firewall rules to allow tcp and udp on the LAN side.
Appreciate all your help #KOM! Very grateful.
-
@NGUSER6947 said in Insert SG-1100 between existing cable modem and router:
I needed to create Firewall rules to allow tcp and udp on the LAN side.
No if its the default lan it would be any any rule out of the box.. You only need to create rules on new interfaces/vlans OPTX, the out of the box lan defaults to any any rule.
In the Firewall, I added 4 rules: tcp and udp "pass" for both ip4 and ip6.
You didn't create rules on your WAN did you?
-
Please post screens of your WAN, LAN and OPT1 rules so we can check them out for you.
-
Ok.
Wan:
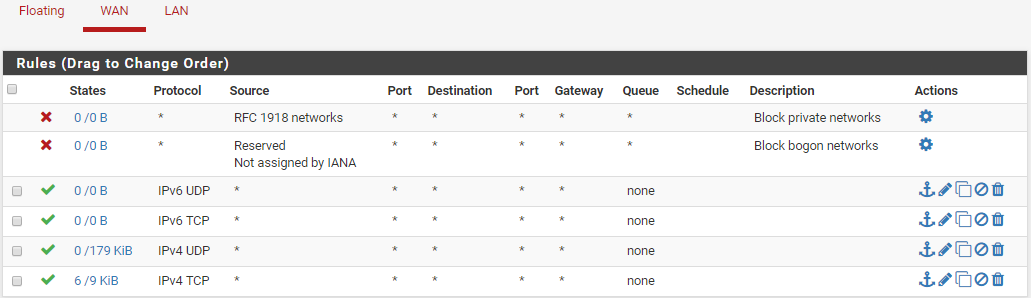
Lan:
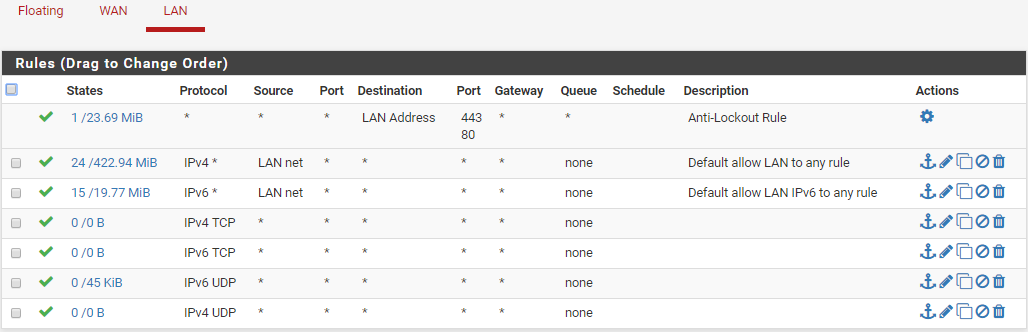
I realize this probably isn't "firewalling" much of anything right now. My plan was to get everything on my network operating then research how to set up the best rules and lock the device down.
-
Rules are evaluated top-down, first match wins. No other rules are processed after a hit.
On your WAN, get rid of those last four allow rules.
On your LAN, also get rid of those last 4 rules. The second rule is already passing all IP4 traffic. Those other rules you added aren't really doing anything. If you're not using IP6 then go to System - Advanced - Networking and disable IP6 there.
-
Ok done. And, everything still works. Thanks folks for the help.
-
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.html
-
If you do disable IP6, don't forget to go back to your LAN rules and delete the IP6 ones you manually added.
-
There you go - much better ;)
See no need to have created any rules..
-
Thank you both.
So with the "factory" rules (only) in place, am I better protected than without the SG, or not really until I start creating more specific rules?
-
Yes. Default rules allow all traffic out from LAN, and block all unsolicited traffic in to WAN.
-
depends - with the default rules nothing has been forwarded from wan/internet to your behind pfsense router that is for sure.
Not sure why you want or think you need another router behind pfsense.. If you want wireless - then just use an AP.
edit
What is this exactly "Ubiquiti wife router." Do you mean an AP like an AC-Pro or -Lite? What is the model number of this device? you have from unifi?