Route WAN network to OVPN
-
If Proxmox has an IP in the 10.23.1.0/24 tunnel subnet when you ping anything in the tunnel subnet from it I suspect you are seeing an icmp redirect at some point so the traffic in at least one direction goes directly rather than via pfSense.
You have a high probability of asymmetric routing there.Do you see blocked traffic in the firewall log when it fails?
Steve
-
Thanks for reply.
No there is anything blocked, I allow everything into the firewall rules.
Proxmox don't have an IP in the 10.23.1.0/24 tunnel.I just added a rule to tell proxmox to communicate to the 10.23.1.0/24 tunnel via 10.1.1.2(pfSense)
ip route add 10.23.1.0/24 via 10.1.1.2So my proxmox server know where to go to communicate with 10.23.1.0/24 network.
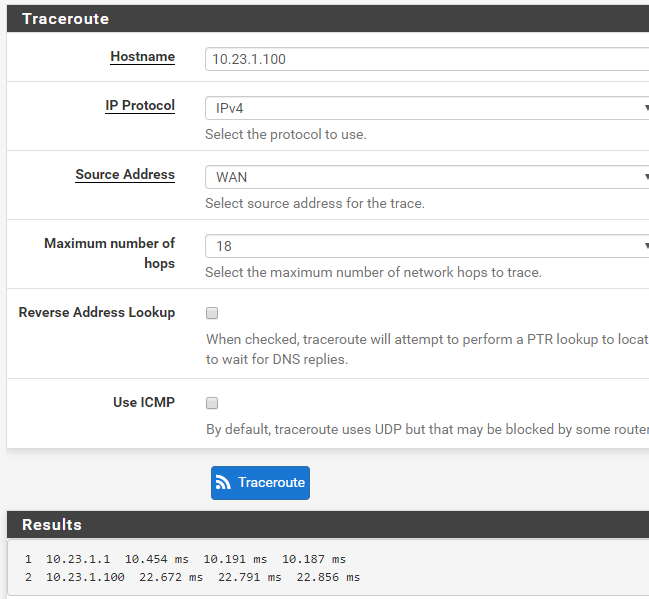
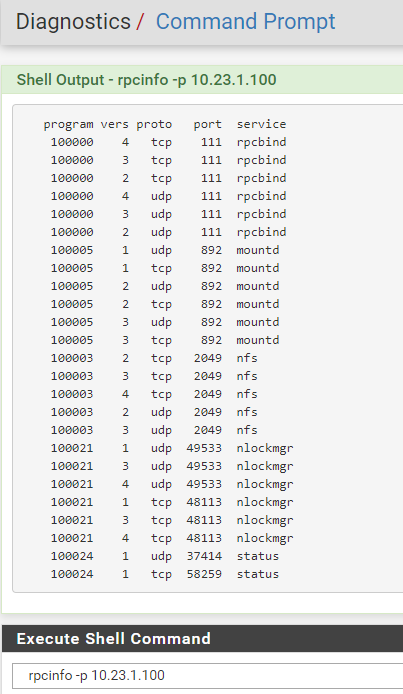
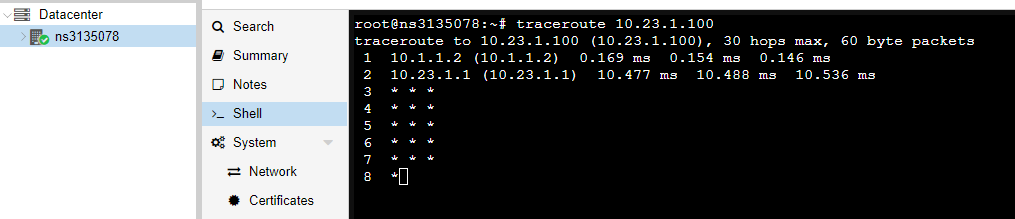
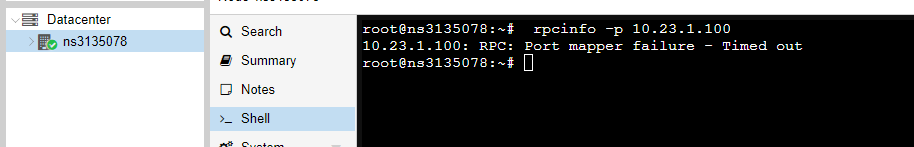
The thing I don't understand is why ping is working, but not traceroute or rpcinfo, if I do a traceroute -I it work.
But well, in final I need this rpc working to etablish a NFS storage. -
@DasK said in Route WAN network to OVPN:
The ip: 10.23.1.200 is the IP of the proxmox on the vpn network
Then what did you mean by that? A different Proxmox server?
Steve
-
Ok I'm sorry, I was meaning the IP of the pfSense, my bad
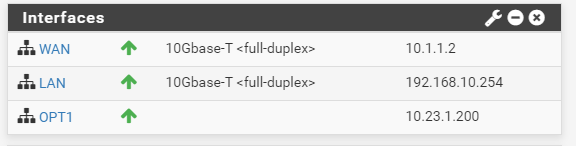
Proxmox IP: 10.1.1.1
PfSense WAN IP: 10.1.1.2
PfSense LAN IP: 192.168.10.254
PfSense VPN IP: 10.23.1.200
VPN NETWORK: 10.23.1.0/24And the server I try to communicate with on the VPN is : 10.23.1.100
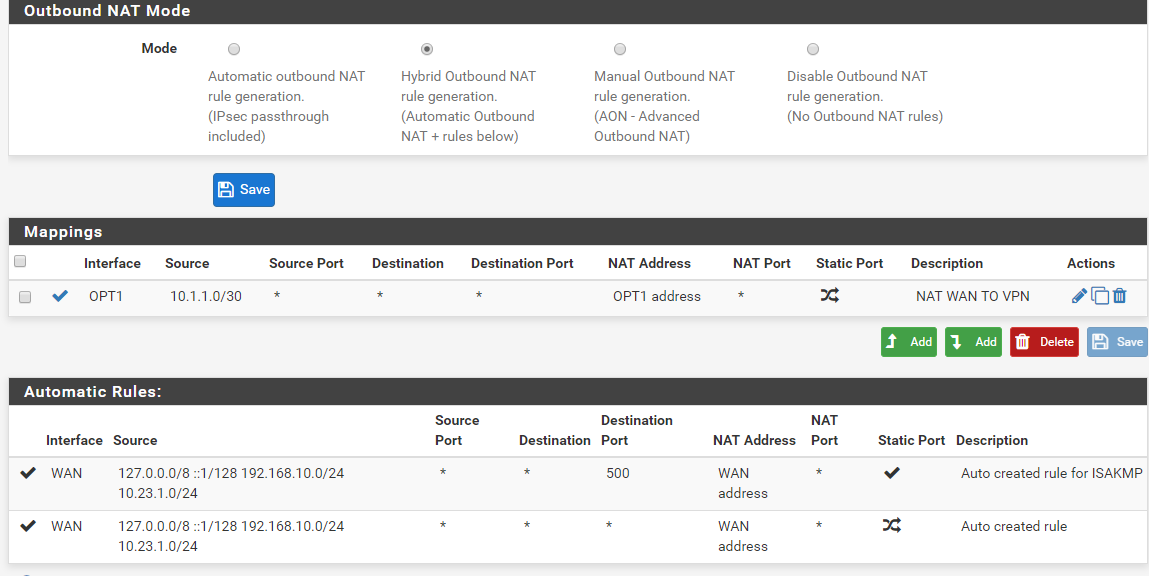
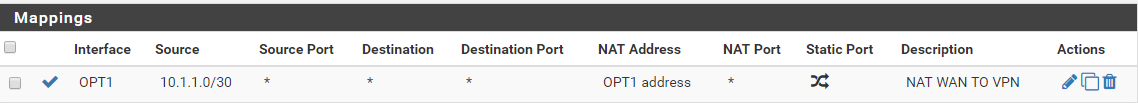
Outbound rules (without this, proxmox can't ping 10.23.1.100 anymore)
Interfaces
Wan rules
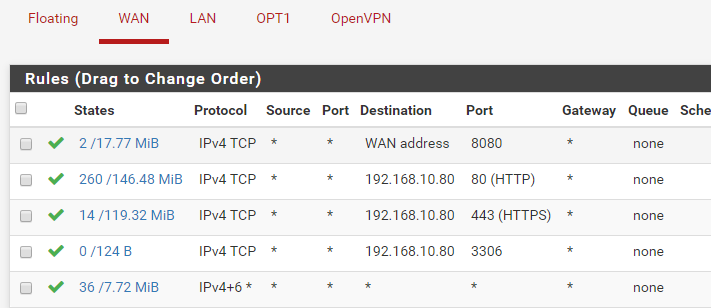
Lan rules
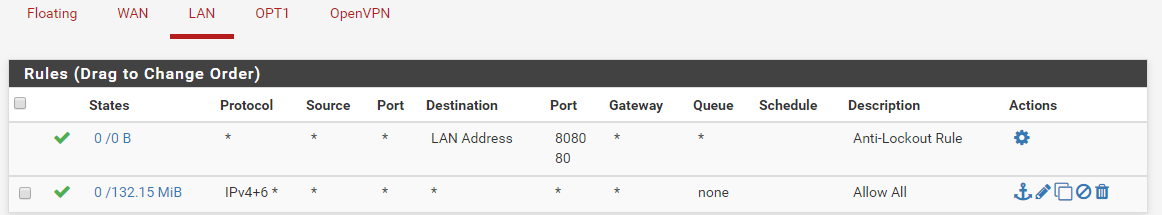
OPT1 rules
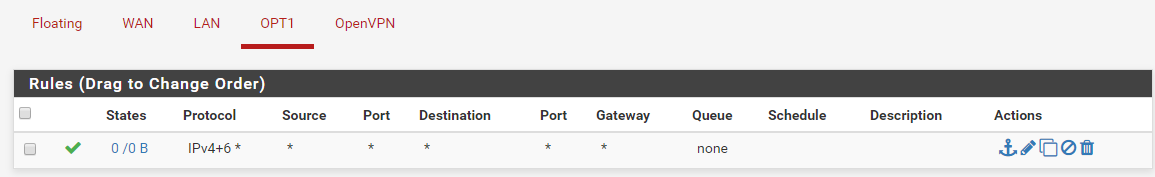
Routes
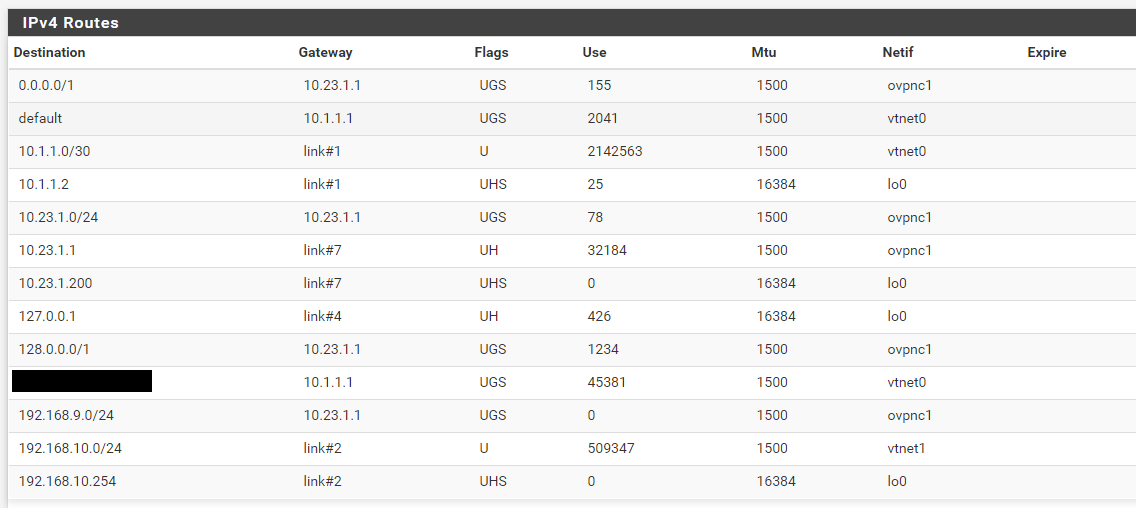
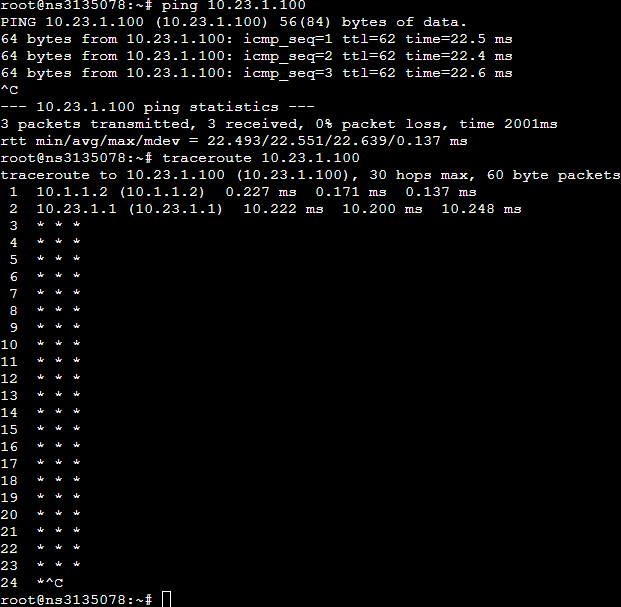
pfSense traceroute:
pfSense rpcinfo:
Proxmox traceroute:
Proxmox rpcinfo:
Proxmox ping:
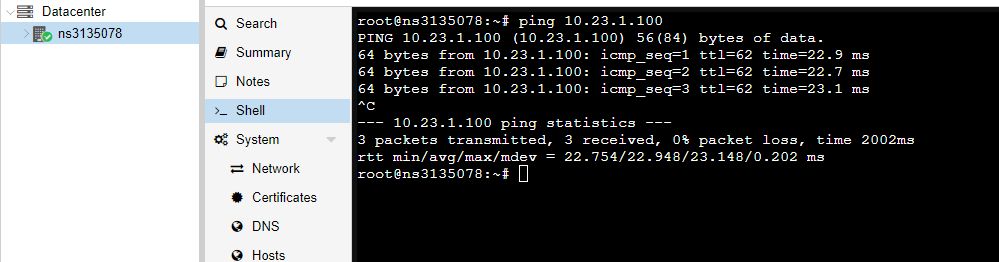
-
Hmm, you might have to check the OpenVPN server, it's able to reach that at 10.23.1.1 but no further. Something blocking or re-routing it there maybe?
Hard to imagine what the difference might be there though. It could only really be TTL....
You probably need that outbound NAT rule as those target devices otherwise have no route back.
Steve
-
All if good for the OpenVPN server.
Any example of how "outbound NAT rule as those target devices " ?
Best
-
The rule you already have for source NATing 10.1.1.0/30 to 10.23.1.200.
Devices at 10.23.1.100 (and .1) obviously know how to reach 10.23.1.200 but probably have no route to 10.1.1.0/30. That is the reason you need that rule.
Steve
-
I added the rule, but still the same problem
-
Well I think I'll give up and just also connect the proxmox server to the VPN, so there will be a direct connection to both server.. It just look weird to connect proxmox to VPN, when there is a VM pfSense already connected to this VPN
-
We haven't yet seen a packet capture of a TCP connection failing. That should be revealing. If there is no traffic coming back at all for example.
This still looks like some route asymmetry somewhere.
Does an icmp traceroute succeed?
Steve
-
Yes all ICMP traceroute work, like ping.
-
When you have ICMP works but TCP fails it's usually an asymmetric routing problem.
It can also be a packet size issue but that would not normally affect UDP traceroute.
Or it can be a hardware off loading problem if the a NIC/driver somewhere is not doing what it reports it can.
Steve
-
How does I can solve this asymetric routing problem ? Or detect where is located the routing problem.
-
Run a packet capture showing some TCP connection failing. If you see parts of the TCP setup missing they are either being blocked somewhere or routed some other way.
Steve
-
There is a little diagram, if that can help to understand how is setup
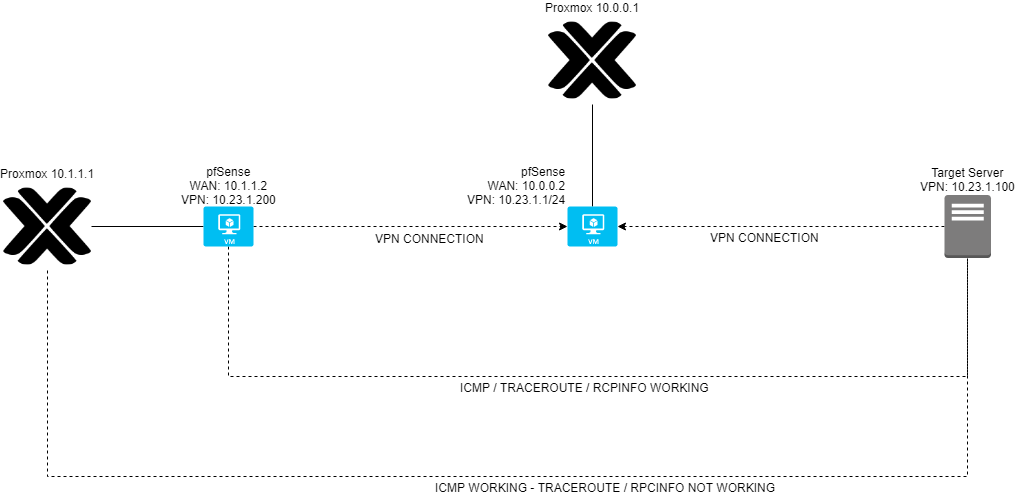
-
Yeah, there is some difference between what happens when you run, say, rpcinfo from pfSense directly and when it's run from Proxmox. So I would run a pcap on the OpenVPN interface and compare them.
rpcinfo will create quite a lot of output so you might want to use something simpler like just telneting to a port assuming that also fails from Proxmox.
Steve