Port forwarding problem
-
So devices on this "lan" network point to pfsense to get off whatever this lan network is?? 192.168.1/24 would be pfsense default.
You don't need to forward to get to any other network, since that rule right there on the top below the anti-lock lets you go wherever you want.
Pfsense out of the box will nat this traffic to what the WAN IP is..
-
@johnpoz said in Port forwarding problem:
ill consider an interface with a gateway on it wan.
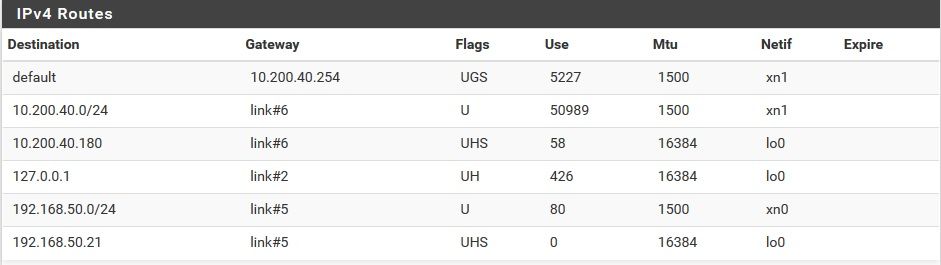
pfsense LAN ip 10.200.40.180
pfsense WAN ip 192.168.50.21Want to reach 192.168.50.4 port 999
I go to the console in pfsense and do telnet 192.168.50.4 999 comes ok..
I want to hit the 10.200.40.180:999 and go to the 192.168.50.4:999
Nothing more.. -
@johnpoz said in Port forwarding problem:
an call it whatever he wants or label them whatever he wants..
-
Your wan is that 10.200.40/24
Where is your 192.168.50/24 network connected??
Says its connected to xn0, that just some opt off pfsense, you don't need a port forward to get there, your lan rules allow it... But if devicese on 192.168.50 don't point back to pfsense as there gateway they wouldn't get back unless you source nat or host route on the dest device in the 192.168.50 network
This is part of the reason you should DRAW your network.
-
@johnpoz said in Port forwarding problem:
since that rule right there on the top below the anti-lock lets you go wherever you want.
No wan its 192.168.50.21 and its internal, reach fine the other host on the network.. ping 192.168.50.4 (the gateway are fine)
From console:PING 192.168.50.4 (192.168.50.4): 56 data bytes 64 bytes from 192.168.50.4: icmp_seq=0 ttl=63 time=5.185 mstelnet 192.168.50.4 999 Trying 192.168.50.4... Connected to 192.168.50.4. Escape character is '^]'.Now want to access from 10.200.40.132 (other host in the LAN network to the ip of the Pfsense 10.200.40.180 and redirect the port 999 to the WAN ip 192.168.50.4:999.
-
Dude if you want Help then draw up this network and show all your routes...
You have a 192.168.50 connected to xn0 -- what you want to call it doesn't mean anything... Its not wan to pfsense, pfsense wan as you showed the routes is is the 10.200.40 network - since there is where the default route is pointing to.
10.200 is not LAN to pfsense, pfsense default route is to 10.200.40.254.. That is where pfsense will send traffic to if not directly attached..
So again DRAW up your network..
we know that 10.200.40 is attached to xn1, and 192.168.50 is attached to xn0
Pfsense default route is to 10.200.40.254... So that is pfsense WAN..
-
@johnpoz said in Port forwarding problem:
what you want to call it doesn't mean anything...
@johnpoz I haved posted all the routes.. You mean I need one default gw on the wan to do this?
-
@johnpoz You mean I need to change WAN for Lan and LAN for wan?
-
pfsense WAN is the network that allows you to get to other networks, this is normally the internet, but it could also be another internal network... Your default gateway on pfsense is pointing to 10.200.40.254... This is the WAN network to pfsense.
This other network attached to xn0 192.168.50.0/24 is pfsense LAN..
If you want devices that reside on this wan network to get to 192.168.50, then you would port forward on wan and point to the lan devices. Devices on wan would have to hit pfsense WAN IP...
If you want devices on lan to get to wan IPs then the default lan rules allows this.. And outbound nat would nat to this 10.200.40 address pfsense.
Your problem could be if you port forward from wan to lan, is if clients on lan 192.168.50 are not using pfsense for their gateway, they would not know how to get back to this 10.200.40 network.
Your problem with lan talking to wan 10.200.40, could be if you turned off natting, and those devices would not know how to get back to 192.168.50
This is your network right?
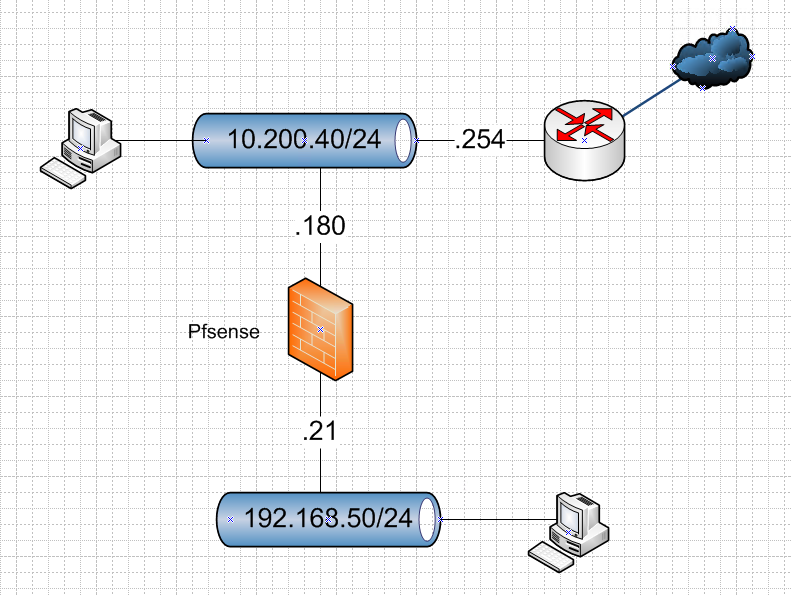
Other devices on 10.200.40 use .254 as their gateway right..
And devices on 192.168.50 use pfsense as their gateway .21 right.. This is pfsense LAN!!10.200.40 is pfsense WAN!!
If you have it pfsense the other way around, then its BORKED!!! Setup pfsense wan interface to be your 10.200.40.180 (gateway set to 10.200.40.254) and LAN to be 192.168.50.21 (no gateway set)
-
So in the 192.168.50.4 i have:
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.50.0 192.168.50.1 255.255.255.0 UG 0 0 0 eth0
192.168.50.0 * 255.255.255.0 U 0 0 0 eth0
10.200.40.0 * 255.255.255.0 U 0 0 0 eth1
default 10.200.40.254 0.0.0.0 UG 0 0 0 eth1 -
Huh??
So you have a multi homed device in 192.168.50???
What device is this
192.168.50.1Dude DRAW your MESS!!!
-
Yes it can be reached directly by the 10.200.40 network.. maybe I need to add the route of the pfsense ip in the eth0 even If I have all the net 192.168.50.0 on this interface?
-
What.... OMG dude sounds like you have a real freaking cluster F.... Why do you have a multi homed device... And it has a interface in the 192.168.50 network, its sure and the F does not need a gateway to get to the 192.168.50 - which is what your showing at 192.168.50.1
I would love to help you straighten your mess out... But can not help you without understand the full scope of your mess and what your trying to accomplish.
-
@johnpoz said in Port forwarding problem:
nd it has a interface in the 192.168.50 network, its sure and the F does not need a gateway to get to the 192.168.50 - which is what your showing at 192.168.50.1
The 192.168.50.1 it´s another host in the 50 network as a gw.
This doesn´t matter even when I have the 192.168.50.0 pointing to the interface.. all the related and established by directly connected network doesnt need the GW.. -
@johnpoz TheScope of forward wanted IS
10.200.40.132 (outgoing port) > 10.200.40.180(pfsense) port 999 (xn1) > forward(nat) 192.168.50.4:999 xn0
As can you see in the tcpdump the packages are not nated are come to the 192.168.50.4 as 10.200.40.132 and back by the default gw in the eth1 as you can see in the route table of the 192.168.50.4 host. -
@fakauy said in Port forwarding problem:
10.200.40.132 (outgoing port) > 10.200.40.180(pfsense) port 999 (xn1) > forward(nat) 192.168.50.4:999 xn0
Here is where you going to have a problem... Your .4 host has an interface in 10.200.40 so he will answer back via his other connection.
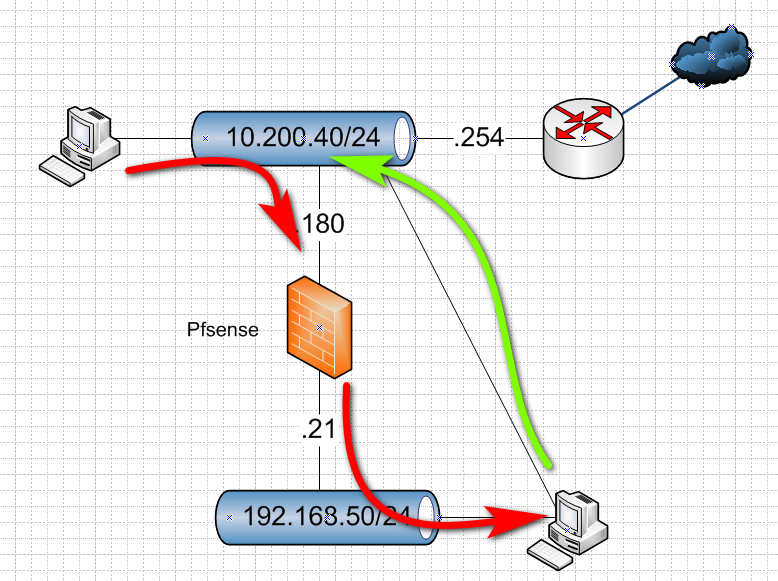
You would have to source nat it to the 192.168.50.21 address if you want .4 to send it back to pfsense...
Pfsense doesn't nat port forwards, only outbound nats..
Why would you want to hit 192.168.50.4 when you can just hit on its 10.200.40 address?
Your clients going not going to accept such an answer... because they sent it to 10.200.40.180, why would 10.200.40.x be sending me an answer, etc. etc.
-
@johnpoz said in Port forwarding problem:
Why would you want to hit 192.168.50.4 when you can just hit on its 10.200.40 address?
The 10.200.40 address its from one interface that´s need to be clear of traffic in this host (192.168.50.4)
-
@johnpoz I haved tested of remove this interface in 192.168.50.4 and didnt work.
-
Then you have to source nat..
The network makes ZERO sense.. .What exactly are you wanting to accomplish, once you multihome a device and put interfaces in networks on each side of a firewall - you basically make that firewall pointless.
-
What??? Removed what interface? The 200, then trouble shoot your port forward.. You did on pfsense WAN?
Did you change the .4 box to point to .21 as its default gateway? If not it wouldn't know how to get back to the 10.200