Reach mobile client from LAN via IPsec tunnel
-
Please see attached pictures with the IPsec config:
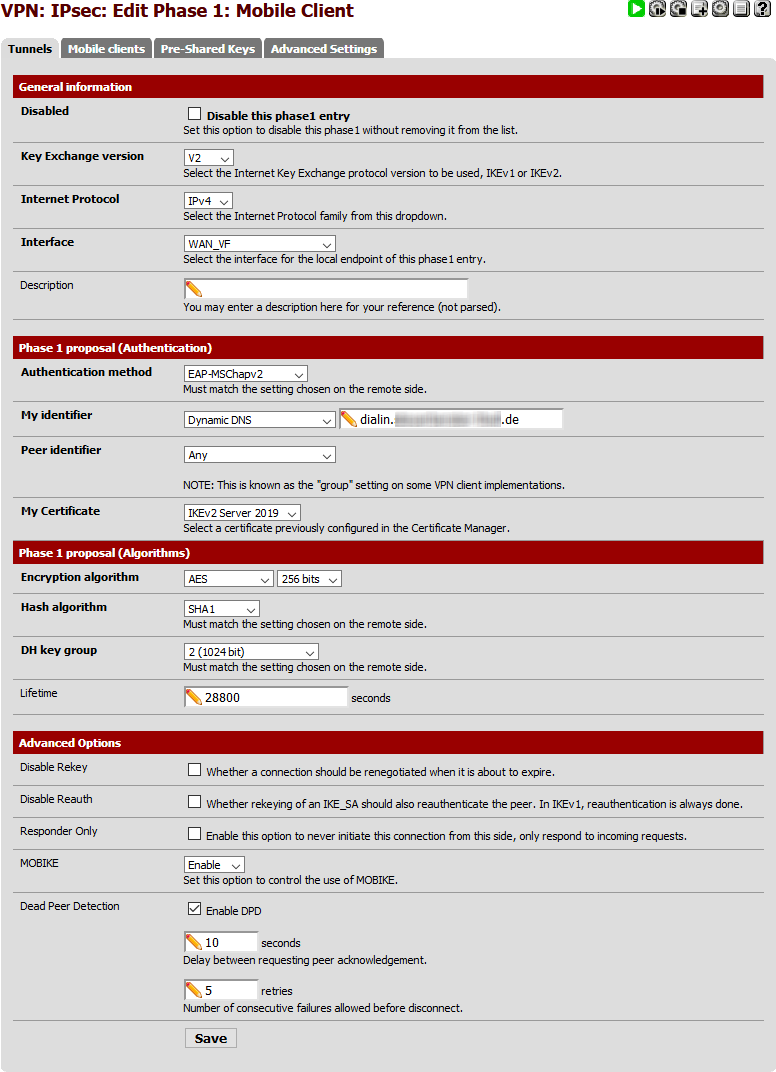
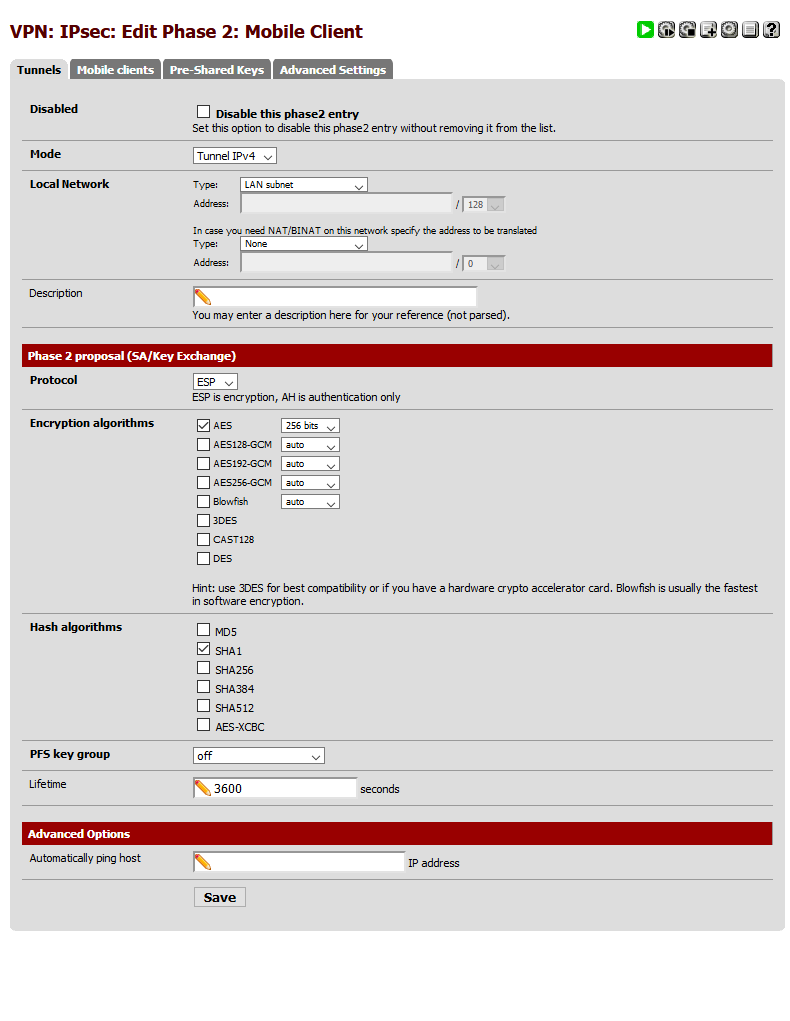
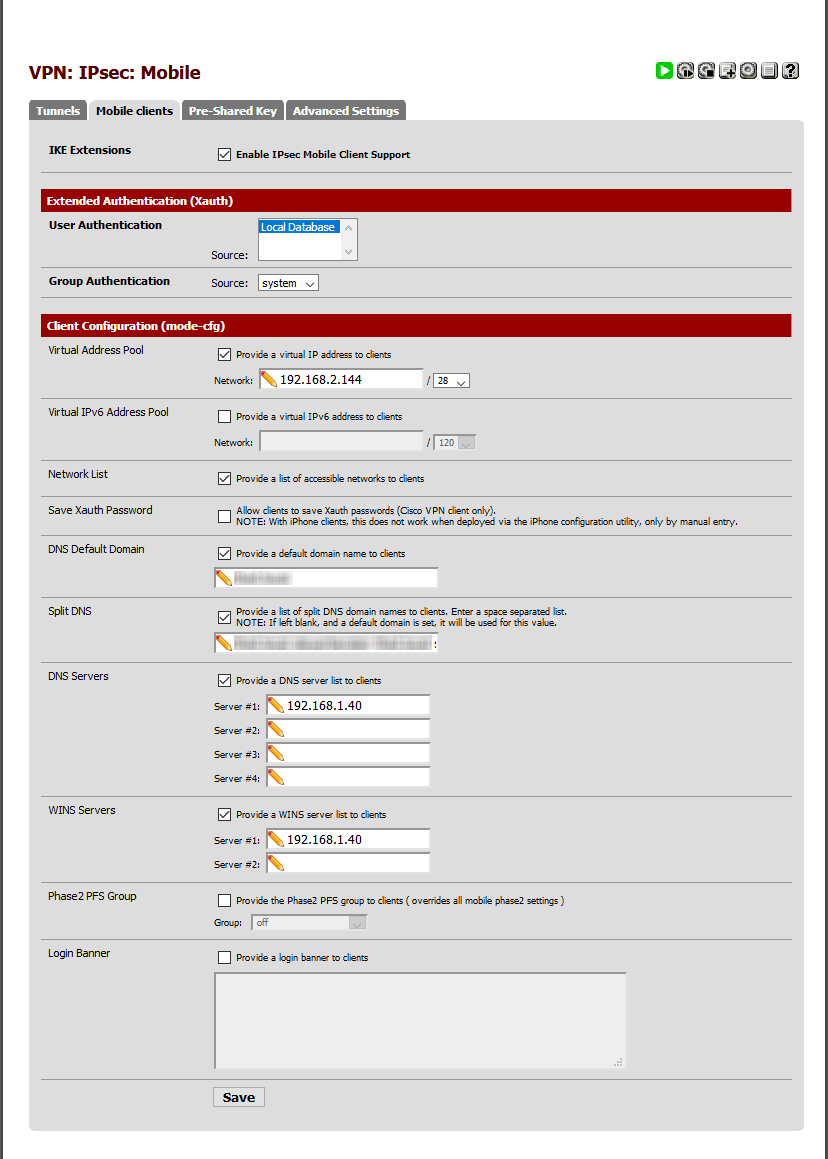
-
You use very outdated version of pfSense
Please update to latest 2.4.4-p3 -
I still need PPTP VPN for one client, therefore update is not possible right now.
Any hint how to solve the IPsec routing to the roadwarrier?
-
Checked it on last 2.4.4-p3 - no problem
traffic routed into IPsecpfSense is single gateway in 192.168.1.0/24 network?
What is default gw on ServerA? -
Default GW on ServerA is the pfSense LAN address 192.168.1.10. No route configured on ServerA for the 192.168.2.x network.
If I do capture packages on the LAN interface, I can see the ICMP packet on the LAN interface (IP 192.168.1.20 > 192.168.2.149) and on the WAN interface (IP 192.168.50.2 > 192.168.2.149), but nothing on the IPsec interface.
192.168.50.2 is the IP of the one of the pfSense WAN Interfaces (it has two in a gateway group).I've tried with a "NO NAT" outbound rule on every interface for destination 192.168.2.0/24 with no success.
In parallel, I've also set up an lan-to-lan IPsec tunnel. This works in both directions out of the box. -
Can I list the fw tables with ipfw?
The command 'ipfw table all list' throws the following error: 'ipfw: Context is mandatory: No such file or directory' -
@lemonfan is more better to show routes:
netstat -rn4
-
@lemonfan did you try OpenVPN for mobile clients? check the same.
-
The output of netstat -rn4 (while IPsec connection is established):
Routing tables Internet: Destination Gateway Flags Netif Expire default 192.168.50.1 UGS sk0 1.1.1.1 192.168.50.1 UGHS sk0 8.8.8.8 192.168.51.1 UGHS sk2 127.0.0.1 link#8 UH lo0 192.168.50.0/24 link#1 U sk0 192.168.50.2 link#1 UHS lo0 192.168.51.0/24 link#3 U sk2 192.168.51.2 link#3 UHS lo0 192.168.1.0/24 link#2 U sk1 192.168.1.10 link#2 UHS lo0 -
Some more debugging on the fw:
-
ping 192.168.2.145
Generates ICMP echo request packages on the gw interface (sk0/sk2), no ICMP echo reply is received (obviously).
Result: ping command gets no answer. -
ping -S 192.168.1.10 192.168.2.145
Generates ICMP echo request packages on the ipsec interface (enc0) and the clients answers back with ICMP echo reply packages.
Result: ping command is ok. -
route add 192.168.2.144/28 192.168.1.10
ping 192.168.2.145
Generates ICMP echo request packages on the ipsec interface (enc0) and the clients answers back with ICMP echo reply packages.
Result: ping command is ok.
BUT:
Even with the above route, i can ping the client only from the fw itself, but not from the network. I`ve also tried playing with NAT rules to force the fw source address, but no lock so far.Any further idea to solve the problem?
-