Strange DNS queries from pfSense
-
@gchialli said in Strange DNS queries from pfSense:
We normally have it disabled
Why would you do that? Do you have another NS that your network uses for local resolution?
-
@johnpoz said in Strange DNS queries from pfSense:
Why would you do that? Do you have another NS that your network uses for local resolution?
Correct, we use a separate DNS server.
-
@johnpoz The issue I'm chasing is some logs in our internal DNS server, for queries to the garbage DNS names I mentioned in the OP. Those come from the LAN IP address of pfSense.
pfSense is configured to use this internal DNS server, as well as the rest of the hosts in the environment.
DNS Resolver has "Forwarding Mode" disabled, so recursive queries are being sent to the Internet.
With all this in mind, it looks to me the suspicious queries are originating from pfSense as well.
Could you please help me think of an scenario where pfSense will be forwarding queries from a different host to the internal DNS server, with the setup I described?
Thank you -
If you have unbound running, and you are forwarding it to your internal NS, then that is where it would send queries too.. Pfsense would have zero reason to query shit like that.. So something is asking it, and its trying to find it... Or there is an IP in its logs and trying to resolve - but that would be a PTR query.
You have unbound running, and you set it domain override, etc. Post up your unbound configuration.
-
This is the unbound.conf:
########################## # Unbound Configuration ########################## ## # Server configuration ## server: chroot: /var/unbound username: "unbound" directory: "/var/unbound" pidfile: "/var/run/unbound.pid" use-syslog: yes port: 53 verbosity: 3 hide-identity: yes hide-version: yes harden-glue: yes do-ip4: yes do-ip6: yes do-udp: yes do-tcp: yes do-daemonize: yes module-config: "validator iterator" unwanted-reply-threshold: 0 num-queries-per-thread: 512 jostle-timeout: 200 infra-host-ttl: 900 infra-cache-numhosts: 10000 outgoing-num-tcp: 10 incoming-num-tcp: 10 edns-buffer-size: 4096 cache-max-ttl: 86400 cache-min-ttl: 0 harden-dnssec-stripped: yes msg-cache-size: 4m rrset-cache-size: 8m num-threads: 2 msg-cache-slabs: 2 rrset-cache-slabs: 2 infra-cache-slabs: 2 key-cache-slabs: 2 outgoing-range: 4096 #so-rcvbuf: 4m auto-trust-anchor-file: /var/unbound/root.key prefetch: no prefetch-key: no use-caps-for-id: no serve-expired: no # Statistics # Unbound Statistics statistics-interval: 0 extended-statistics: yes statistics-cumulative: yes # SSL Configuration # Interface IP(s) to bind to interface-automatic: yes interface: 0.0.0.0 interface: ::0 # DNS Rebinding # Access lists include: /var/unbound/access_lists.conf # Static host entries include: /var/unbound/host_entries.conf # dhcp lease entries include: /var/unbound/dhcpleases_entries.conf # Domain overrides include: /var/unbound/domainoverrides.conf ### # Remote Control Config ### include: /var/unbound/remotecontrol.conf/var/unbound/domainoverrides.conf is empty:
: ls -l /var/unbound/domainoverrides.conf -rw-r--r-- 1 root unbound 0 Sep 13 17:39 /var/unbound/domainoverrides.confIt's pretty much the default. We are really not using this package. I guess I can turn it off.
But I don't see anything in the config of unbound that will forward a query to the internal DNS server. -
Are you doing dns redirection, were if unbound ask for something it would get redirected to your internal NS... Pfsense has zero reason to look for those. What packages are you running? I can not see you using pfblocker if your not using unbound..
Where does pfsense itself point to for dns? Via static setting, via dhcp?
-
@johnpoz said in Strange DNS queries from pfSense:
Are you doing dns redirection, were if unbound ask for something it would get redirected to your internal NS...
Nope, nothing like that in place
Pfsense has zero reason to look for those.
Agreed, it's very odd to me as well.
What packages are you running? I can not see you using pfblocker if your not using unbound..
Pretty much what comes out of the box in the AWS Marketplace AMI. +NRPE and Snort. Could this be coming from Snort? Maybe Snort trying to verify something it saw in a packet? I checked Snort alerts and cannot really see anything though.
Where does pfsense itself point to for dns? Via static setting, via dhcp?
pfSense points to the internal NS that is showing these strange queries in the logs. It's statically configured in the General Settings.
-
Not sure why snort would look for those.. I am not aware of snort looking to what you have set pfsense to use NS xyz would use that anyway.
Turn off unbound, since you have zero use for it.. You do not have bind or dnsmasq setup either.. Nothing listening on 53 on the box.
I can not think of any reason pfsense would look for something like that other then something asked for it. So this is in aws, how are you sure its actually coming from pfsense?
Pfsense will look for updates. It could do a PTR query for IPs in its logs.. Are you running smtp on it? Do you have smtp notifications setup. Do you have any aliases setup? Where it wants to resolve a fqdn.. If you have an alias setup it could look for stuff you have in the aliases..
How often are you getting these odd queries?
Are you in Ireland? Are you running proxy on pfsense - that could do it I would think.
Those really look like what chrome does.. So if your running proxy, be it transparent or explicit then that could explain it I guess
Here I just fired up chrome on my pc, which is in the local.lan domain - and see it creates these nonsense queries
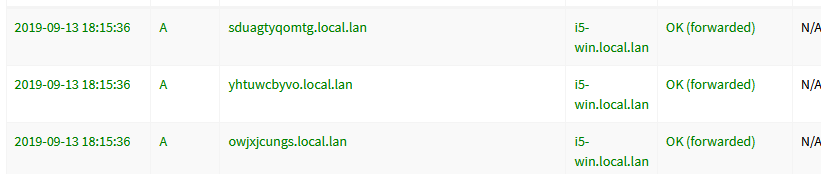
So its got to be chrome creating them, but so proxy would be my guess. Since you can not run chrome in pfsense. If your not running any dns services off of pfsense.
-
@gchialli said in Strange DNS queries from pfSense:
Pretty much what comes out of the box in the AWS Marketplace AMI. +NRPE and Snort. Could this be coming from Snort? Maybe Snort trying to verify something it saw in a packet? I checked Snort alerts and cannot really see anything though.
Snort performs zero DNS lookups while inspecting traffic. It has no reason to do that. So Snort is not performing those lookups.
The only part of the Snort package that does a DNS lookup is the periodic rules update cron task. That task will lookup the IP address for the web site of the rule vendor so that Snort can download the rules update tarball.
P.S. -- forgot to mention one other place. If you click on the magnifying glass icon beside a listed IP address on the ALERTS tab, that will trigger a reverse PTR DNS lookup by the Snort GUI code in an attempt to identify the domain associated with the IP. But that is a manual user action. Snort won't do that lookup on its own.
-
@bmeeks would know what snort can do and or should do - he is the snort guru around here that is for sure ;)
-
R rasputinthegreatest referenced this topic on