How to remove NAT through the VPN ?
-
@LLFT said in How to remove NAT through the VPN ?:
I want that when the server responds it does it on port 9000 and by on the port forwarding
You do understand that very often different port numbers are used for either direction. What is the source port on that packet? That's where the reply will be sent. Also, do you have NAT running anywhere? I don't see any point where it's likely to be used. NAT is normally used to get around the IPv4 address shortage, though it may also be used to avoid conflicts between sites that use RFC1918 addresses locally.
-
Re: How to remove NAT through the VPN ?
Yes, I reassure you I understand a minimum the mechanism of the network.
In TCP most of the time an application initiates a communication on an application port and then the server and the client go on to communicate over our port range.
The source port is 9000.
No current NAT in my opinion only routing, but a PAT well apparent.
My wish would be to get this:
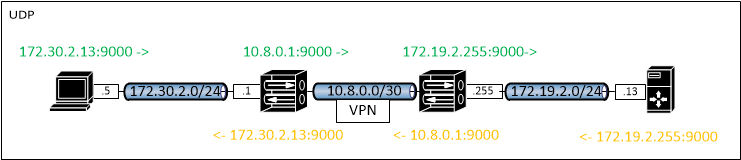
Easier to manage firewall rules.
-
That is not how it would work at all.. And why and the hell would you want it too.. You have a double nat in that picture..
If sent from 172.30.2.13:9000 then the answer would be to 172.30.2.13:9000
Why would you think it would ever get natted to your tunnel interface? If you want it to be source natted at your 172.19.2 network, then do it there.. You might do such a thing when the dest box doesn't have a gateway, or uses a different default gateway and has no route back to 172.30.2 via your vpn server..
-
The purpose of this montage is only when the client sends a frame. The server receives a frame having for source IP that of the client.
I would like the VPN part to be invisible in their exchange.
-
@LLFT said in How to remove NAT through the VPN ?:
I would like the VPN part to be invisible in their exchange.
Then you want the VPN in TAP mode, not TUN. That is essentially a bridge between the 2 networks. It also requires the networks to be in the same subnet.
-
@LLFT said in How to remove NAT through the VPN ?:
I would like the VPN part to be invisible in their exchange.
It would be from the client or servers perspective... The client has no idea its going over a tunnel, nor does the server have any idea about the tunnel network... It sees the source IP only..
-
It would be nice to know exactly what he's trying to do and what he thinks the issue is. I'm still stuck on the first part.
-
Yeah have no idea either, there is no nat in a vpn connection.. Unless he on purpose set it up to nat somewhere..
Maybe he is trying to do a L2? But if so he is showing different L3 on each end of his tunnel.. So yeah not really sure what his issue is or trying to accomplish.
Maybe something is getting lost in translation? He posted in French as well?
-
Hello,
Sorry for the response times, I was away.
I will try to answer your questions.
I did not take a VPN in TAP mode because the purpose of my VPN is to connect a remote site with multiple hosts to a central site through an LTE and ADSL network.
My problem is that everything works well. Only equipment located on the remote site can not communicate with its server.
One of the exchanges at the level of this equipment is done via FTP. (PASSIVE / ACTIVE, I do not know)I assumed that the port change between each routing hop was causing my problem. That's why I made a fixation on the NAT / PAT, I simply forgot the OSI level of my VPN.
And yes ! I am French :)
-
And does the firewall on the server allow traffic from this remote network IP range.
-
I intend to activate the firewall part in a second time. For now it's open door.