[solved] backend server nginx down HAProxy
-
@wesleylc1 You accessing nginx or haproxy now? Print nslookup domain.com output plz
-
@dragoangel This access is being made from my LAN subnet, below the nslookup output.
nslookup nextcloud.projectus.com.br Server: 192.168.45.11 Address: 192.168.45.11#53 Non-authoritative answer: Name: nextcloud.projectus.com.br Address: 189.20.108.xxbest regards,
Wesley Santos -
hm... you said that you access it locally, but domain resolving goes to public IP
-
The resolution is pointing to the public IP, because my DNS provider is external.
-
@dragoangel said in backend server nginx down HAProxy:
You accessing nginx or haproxy now
You accessing nginx or haproxy now??
-
I do not understand, can you explain again?
-
 facepalm.
facepalm.@wesleylc1 said in backend server nginx down HAProxy:
@dragoangel internally it is accessible to the web page through the https protocol.
You opened connection to NGINX or HAproxy?? Try change healthchecks to GET /
-
@dragoangel My problem may be that my front end already uses another default backend?
I had already made changes from OPTIONS to GET and HEAD, for example, using https there was no success, already using http went well.
-
you musn't use "default backend". This bad practice. All time use only ACLs to assign backend.
-
I use a default backend for https systems and assign to these sites through acls.
-
@dragoangel @PiBa Hi guys !!
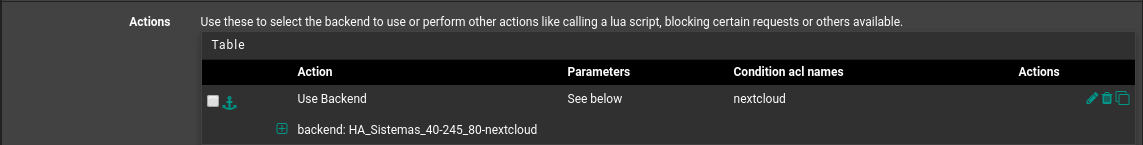
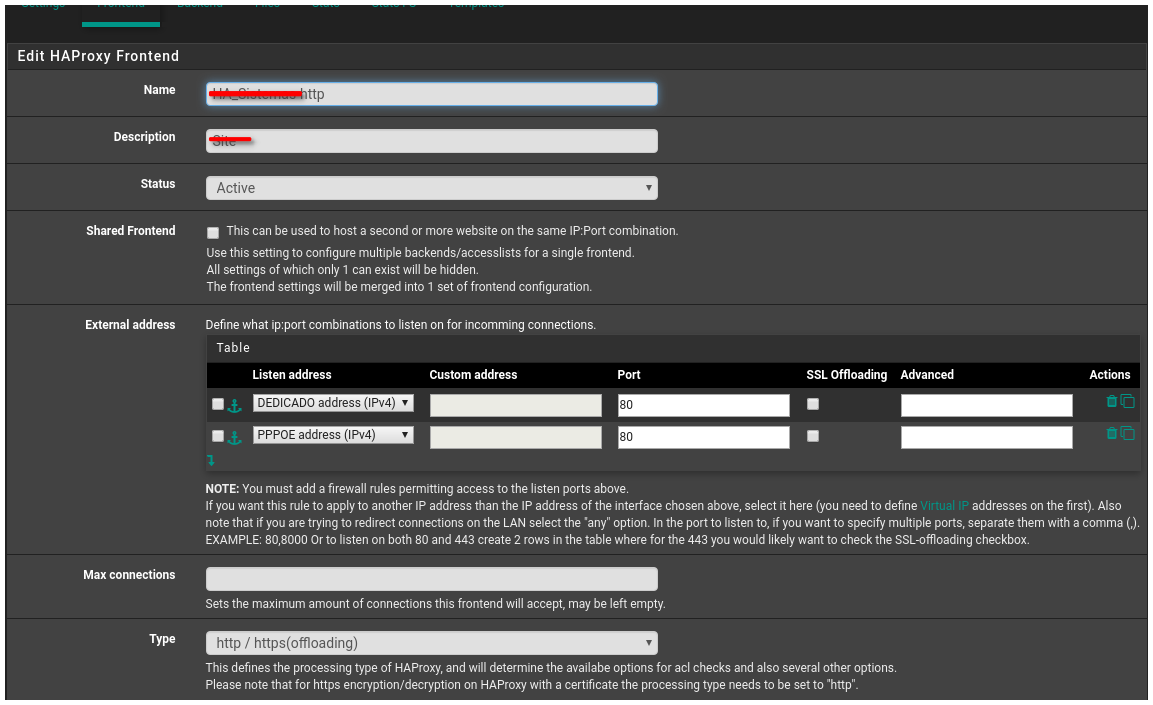
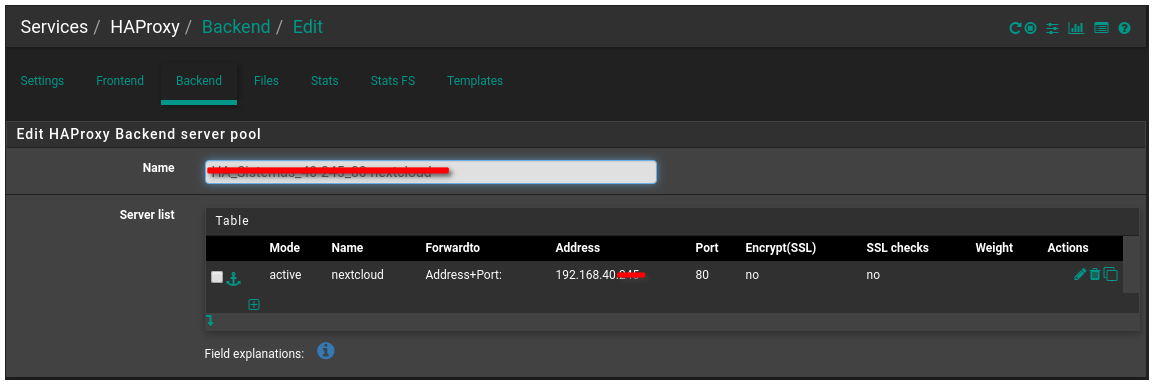
I deleted entries 443 from this backend and made new settings using 80, the image below the backend communicates successfully.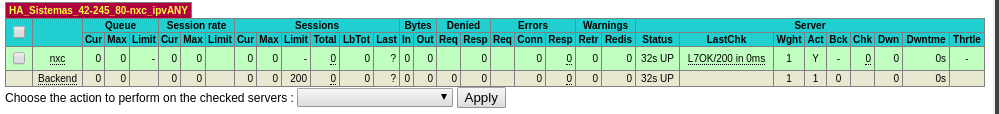
I really need to publish this site, I will be very grateful if you help me.
best regards,
Wesley Santos -
The supplemental information, after applying the changes below to the backend, is now in active status, but the ACL still does not point to the correct page.
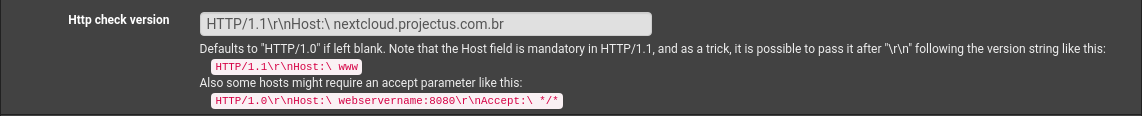
- backend status:

I am using this documentation as a reference.
https://serverfault.com/questions/664332/haproxy-returns-bad-request-invalid-host-for-seemingly-no-reason
- backend status:
-
@wesleylc1
Is this what your current config looks like?:use_backend HA_Sistemas-45-xx_80-www_ipvANY if !time-sheet !qsms !treinamento !proposta !chamado !pesquisa !pesquisa-ce use_backend HA_Sistemas_40-xx_443-nextcloud_ipvANY if !nextcloud default_backend HA_Sistemas_43-xx_8443_ipvANYIf so then the logic seems to be wrong. Keep in mind that the first matching 'use_backend' is used.
A client visiting nextcloud would match the first use_backend line that says it should not be timesheet/qsms/treinamento/.. which would evaluate to 'true'.. As such the client will be send to that 1st www backend.
You might want to have that one also exclude the !nextcloud.. and DO allow usage of the nextcloud backend when the nextcloud is requested.. so that should be without the ! sign.
-
Current configuration looks like this:
frontend HA_Sistemas-https bind 189.20.108.xx:443 name 189.20.108.xx:443 ssl crt-list /var/etc/haproxy/HA_Sistemas-https.crt_list bind 187.75.209.xxx:443 name 187.75.209.xxx:443 ssl crt-list /var/etc/haproxy/HA_Sistemas-https.crt_list mode http log global option log-separate-errors option httplog option http-keep-alive timeout client 300000 acl rootrequested var(txn.txnpath) -m str -i / acl time-sheet var(txn.txnhost) -m str -i time-sheet.projectus.com.br acl qsms var(txn.txnhost) -m str -i qsms.projectus.com.br acl treinamento var(txn.txnhost) -m str -i treinamento.projectus.com.br acl proposta var(txn.txnhost) -m str -i proposta.projectus.com.br acl chamado var(txn.txnhost) -m str -i chamado.projectus.com.br acl pesquisa var(txn.txnhost) -m str -i pesquisa.projectus.com.br acl pesquisa-ce var(txn.txnhost) -m str -i pesquisa-ce.projectus.com.br acl nxc var(txn.txnhost) -m str -i nextcloud.projectus.com.br http-request set-var(txn.txnpath) path http-request set-var(txn.txnhost) hdr(host) http-request redirect location /TimeSheet/faces/login.xhtml if rootrequested time-sheet http-request redirect location /SistemaQSMS/ if rootrequested qsms http-request redirect location /Treinamento/ if rootrequested treinamento http-request redirect location /Proposta/ if rootrequested proposta http-request redirect location /Chamado/ if rootrequested chamado http-request redirect location /PesquisaClima/ if rootrequested pesquisa http-request redirect location /PesquisaClimaCE/ if rootrequested pesquisa-ce http-response add-header Content-Security-Policy upgrade-insecure-requests if !time-sheet !qsms !treinamento !proposta !chamado !pesquisa !pesquisa-ce !nxc use_backend HA_Sistemas-45-14_80-www_ipvANY if !time-sheet !qsms !treinamento !proposta !chamado !pesquisa !pesquisa-ce use_backend HA_Sistemas_40-245_443-nxc_ipvANY if !nxc default_backend HA_Sistemas_43-235_8443_ipvANYI tried applying the settings as reported in your last message, but still have trouble redirecting to https://nextcloud.projectus.com
-
@wesleylc1
The settings in my message are exactly what you posted just to ask confirmation if that is what you currently had active. The settings are wrong indeed.Try making them like this:
use_backend HA_Sistemas-45-14_80-www_ipvANY if !time-sheet !qsms !treinamento !proposta !chamado !pesquisa !pesquisa-ce !nxc use_backend HA_Sistemas_40-245_443-nxc_ipvANY if nxc default_backend HA_Sistemas_43-235_8443_ipvANY -
@PiBa I set up according to your last message, but the problem persists, continuing to direct nextcloud.projectus.com.br to the main site of the company.
frontend HA_Sistemas-https bind 189.20.108.xx:443 name 189.20.108.xx:443 ssl crt-list /var/etc/haproxy/HA_Sistemas-https.crt_list bind 187.75.209.xxx:443 name 187.75.209.xxx:443 ssl crt-list /var/etc/haproxy/HA_Sistemas-https.crt_list mode http log global option log-separate-errors option httplog option http-keep-alive timeout client 300000 acl rootrequested var(txn.txnpath) -m str -i / acl time-sheet var(txn.txnhost) -m str -i time-sheet.projectus.com.br acl qsms var(txn.txnhost) -m str -i qsms.projectus.com.br acl treinamento var(txn.txnhost) -m str -i treinamento.projectus.com.br acl proposta var(txn.txnhost) -m str -i proposta.projectus.com.br acl chamado var(txn.txnhost) -m str -i chamado.projectus.com.br acl pesquisa var(txn.txnhost) -m str -i pesquisa.projectus.com.br acl pesquisa-ce var(txn.txnhost) -m str -i pesquisa-ce.projectus.com.br acl nxc var(txn.txnhost) -m str -i nextcloud.projectus.com.br http-request set-var(txn.txnpath) path http-request set-var(txn.txnhost) hdr(host) http-request redirect location /TimeSheet/faces/login.xhtml if rootrequested time-sheet http-request redirect location /SistemaQSMS/ if rootrequested qsms http-request redirect location /Treinamento/ if rootrequested treinamento http-request redirect location /Proposta/ if rootrequested proposta http-request redirect location /Chamado/ if rootrequested chamado http-request redirect location /PesquisaClima/ if rootrequested pesquisa http-request redirect location /PesquisaClimaCE/ if rootrequested pesquisa-ce http-request redirect location /login if rootrequested nxc http-response add-header Content-Security-Policy upgrade-insecure-requests if !time-sheet !qsms !treinamento !proposta !chamado !pesquisa !pesquisa-ce use_backend HA_Sistemas-45-14_80-www_ipvANY if !time-sheet !qsms !treinamento !proposta !chamado !pesquisa !pesquisa-ce !nxc use_backend HA_Sistemas_40-245_443-nxc_ipvANY if nxc default_backend HA_Sistemas_43-235_8443_ipvANYcompany website projectus.com.br
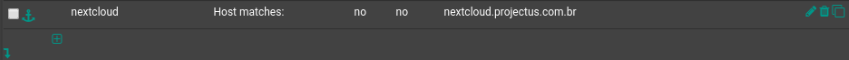
site "nextcloud" nextcloud.projectus.com.br

-
@wesleylc1
Seems to me that https://nextcloud.projectus.com.br/ is working just fine..? Can you confirm that?Perhaps you have another frontend that is listening on :80 that is sending a wrong redirect?
-
@PiBa redirection occurs, but leading to the wrong page, I have another frontend that responds to requests on port: 80.
Port Front End Settings: 80frontend HA_Sistemas-http bind 189.20.108.xx:80 name 189.20.108.xx:80 bind 187.75.209.xxx:80 name 187.75.209.xxx:80 mode http log global option log-separate-errors option httplog option http-keep-alive timeout client 30000 acl projectus var(txn.txnhost) -m str -i projectus.com.br acl projectus var(txn.txnhost) -m str -i www.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i time-sheet.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i treinamento-qsms.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i qsms.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i proposta.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i treinamento.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i chamado.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i pesquisa.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i pesquisa-ce.projectus.com.br acl cadcae var(txn.txnhost) -m str -i www.cadcae.projectus.com.br acl cadcae var(txn.txnhost) -m str -i cadcae.projectus.com.br acl rh var(txn.txnhost) -m str -i rh.projectus.com.br http-request set-var(txn.txnhost) hdr(host) http-request redirect scheme https if redirect-to-SSL http-request redirect location http://www.projectus.com.br if !projectus !cadcae !rh use_backend HA_Sistemas-45-14_80-www_ipvANY if projectus use_backend HA_Sistemas_43-70_80-ged_ipvANY if cadcae use_backend HA_Sistemas_42-226_80-rh_ipvANY if rh- It worked after creating the "nextcloud.projectus.com.br" ACL
acl projectus var(txn.txnhost) -m str -i projectus.com.br acl projectus var(txn.txnhost) -m str -i www.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i time-sheet.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i treinamento-qsms.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i qsms.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i proposta.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i treinamento.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i chamado.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i pesquisa.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i pesquisa-ce.projectus.com.br acl redirect-to-SSL var(txn.txnhost) -m str -i nextcloud.projectus.com.br acl cadcae var(txn.txnhost) -m str -i www.cadcae.projectus.com.br acl cadcae var(txn.txnhost) -m str -i cadcae.projectus.com.br acl rh var(txn.txnhost) -m str -i rh.projectus.com.br -
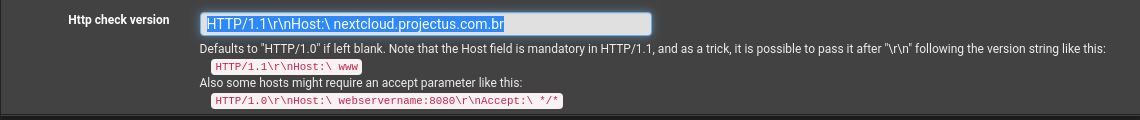
@PiBa can you explain to me, why the backen only focused up after using the setting "HTTP / 1.1 \ r \ nHost: \ nextcloud.projectus.com.br"?
-
@wesleylc1
Can you tell me why your nginx configuration requires the host header to be send in requests?