IPv6 manual PD
-
Does not need any cooperation or service from upstream.
Static ULA will work just fine locally.
-
@Derelict said in IPv6 manual PD:
Does not need any cooperation or service from upstream.
Static ULA will work just fine locally.
I was thinking he should have both ULA and GUA. If he doesn't have either, there's some other problem.
-
@Derelict said in IPv6 manual PD:
What do you get if you set the interface IPv6 address to a static fd50::1/64 and use unmanaged mode?
Setting the IPv6 address statically unmanaged mode created a SLAAC with the prefix defines on a machine.
Setting Assisted mode and disabling the DHCPv6 server doesn't make a lot of sense to me. If you only want SLAAC, use Unmanaged.
Our broadband is still down and I'm a bit concerned about static IPv6's once we're receiving the ISP's PD again. Will it route correctly over pfsense and the VLANs when pfsense's IPv6 interface is not tracking the WAN interface anymore ?
I'll just drop this here for the record since seeing fd50::/64 burns my eyes: https://tools.ietf.org/html/rfc4193#page-3
I can understand the emphasis on a globally unique prefix with LUA (Local Unicast Addresses or is it ULA Unique Local Addresses) IPv6 addresses for larger multi-nationals. However, as it's not supposed to ever be globally routable, what would it break in small setups ?
As such, is
fd00::10: /64 for vlan 10 fd00::20: /64 for vlan 20 fd00::30: /64 for vlan 30 fd00::40: /64 for vlan 40 fd00::50: /64 for vlan 50therefore a more acceptable approach ?
** Noted that the format above is seen as invalid in pfsense, though specifying fd00:0:0:50:: is acceptable **
-
@JKnott said in IPv6 manual PD:
Assuming you're connect to an ISP that provided IPv6, you should get a valid prefix. You'd normally use DHCPv6-PD to connect to the ISP and the local LAN can use SLAAC or DHCPv6 to assign addresses to the devices.
I am receiving a DHCPv6-PD from the ISP. The vLAN interfaces is then tracking the WAN interface and machines' interfaces is generally configured via SLAAC.
However, some machines (servers) have their IPv6 addresses statically assigned.
Once the broadband line went down, we cannot reach the machines unless using IPv4 due to the link-local addresses not being routeable over the VLANS.
I therefore need a ULA and GUA per interface, for when the PD isn't available for whatever reason. At present an interface is configured as follows:
# SLAAC iface eth0 inet6 auto or # DHCPv6 iface eth0 inet6 dhcp or # Static iface eth0 inet6 static address 2001:db8:3:4::8888 netmask 64How do I thus ensure an interface acquires both a GUA (via the ISP's PD) and a LUA (via pfsense) ... ?
-
No. You will want to delete everything if you are getting a DHCP6 PD and using tracking interfaces.
What, exactly, is your goal.
When you deal with NATting IPsec connections because both sides chose the same RFC1918 subnet and nobody wants to renumber you will see the value of doing a globally-unique local /48 at every site from the beginning.
-
@Derelict said in IPv6 manual PD:
No. You will want to delete everything if you are getting a DHCP6 PD and using tracking interfaces.
Delete everything ... Sorry, I totally lost you there.
What, exactly, is your goal.
Local IPv6 addresses registered in the DNS resolver to allow contacting machines from the internal LAN when the Global prefix isn't being delegated.
When you deal with NATting IPsec connections because both sides chose the same RFC1918 subnet and nobody wants to renumber you will see the value of doing a globally-unique local /48 at every site from the beginning.
The idea is to move away from anything IPv4 related. IPv4 is only used as a backup and in some scenarios where IPv6 isn't fully supported.
-
@JKnott said in IPv6 manual PD:
I was thinking he should have both ULA and GUA. If he doesn't have either, there's some other problem.
Which is what I believe as well.
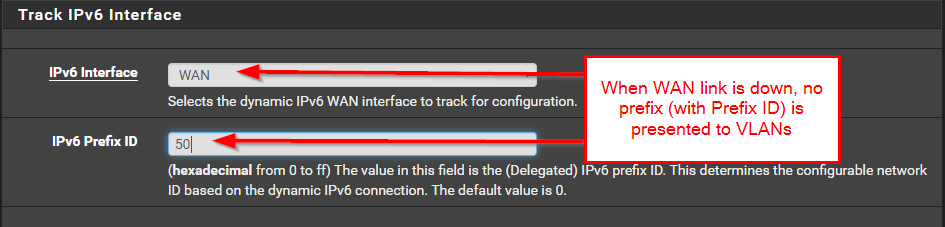
-
This post is deleted! -
There are problems with that.
https://redmine.pfsense.org/issues/5999
When I have to reboot I:
- Delete the ULA IP Alias VIPs from LAN and DMZ
- Edit/Save WAN to kick off DHCP6 and Track interface
- Put the ULA VIPs back on LAN and DMZ
After that I am good until I have to reboot the firewall again. That is the current state of things. If that is unacceptable for you then pfSense, as it exists right now, might not be a good fit for your requirements.
$ ifconfig vlan0 vlan0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> mtu 1500 options=3<RXCSUM,TXCSUM> ether a8:60:b6:19:15:fe inet6 fe80::18f3:9042:2cd0:8d8%vlan0 prefixlen 64 secured scopeid 0xd inet6 2600:face:0ff:9501:ca2:7504:b2dc:4842 prefixlen 64 autoconf secured inet6 2600:face:0ff:9501:b567:3b2f:300f:398c prefixlen 64 deprecated autoconf temporary inet6 fd8c:9857:66db:1:4c9:e132:ee:396a prefixlen 64 autoconf secured inet6 fd8c:9857:66db:1:10d2:3eb7:aefc:d655 prefixlen 64 deprecated autoconf temporary inet 192.168.223.6 netmask 0xffffff00 broadcast 192.168.223.255 inet6 2600:face:0ff:9501::145a prefixlen 64 dynamic inet6 2600:face:0ff:9501:1123:95df:fb97:3e4c prefixlen 64 deprecated autoconf temporary inet6 fd8c:9857:66db:1:1123:95df:fb97:3e4c prefixlen 64 deprecated autoconf temporary inet6 2600:face:0ff:9501:b529:c61f:f4f5:ba3a prefixlen 64 deprecated autoconf temporary inet6 fd8c:9857:66db:1:b529:c61f:f4f5:ba3a prefixlen 64 deprecated autoconf temporary inet6 2600:face:0ff:9501:1dd:5877:4758:d9d2 prefixlen 64 deprecated autoconf temporary inet6 fd8c:9857:66db:1:1dd:5877:4758:d9d2 prefixlen 64 deprecated autoconf temporary inet6 2600:face:0ff:9501:551d:4e96:bb81:e2f7 prefixlen 64 deprecated autoconf temporary inet6 fd8c:9857:66db:1:551d:4e96:bb81:e2f7 prefixlen 64 deprecated autoconf temporary inet6 2600:face:0ff:9501:ecb6:32ad:85b6:8a8e prefixlen 64 deprecated autoconf temporary inet6 fd8c:9857:66db:1:ecb6:32ad:85b6:8a8e prefixlen 64 deprecated autoconf temporary inet6 2600:face:0ff:9501:3c69:b7aa:a84:284 prefixlen 64 autoconf temporary inet6 fd8c:9857:66db:1:3c69:b7aa:a84:284 prefixlen 64 autoconf temporary nd6 options=201<PERFORMNUD,DAD> vlan: 223 parent interface: en0 media: autoselect (1000baseT <full-duplex>) status: active -
LAN:
And:

-
This post is deleted! -
This post is deleted! -
This post is deleted! -
@Derelict said in IPv6 manual PD:
Delete the ULA IP Alias VIPs from LAN and DMZ
Edit/Save WAN to kick off DHCP6 and Track interface
Put the ULA VIPs back on LAN and DMZ@Derelict, would you mind elaborating on deleting and putting back the ULA VIPs as referred to above ?
-
Firewall > Virtual IPs
-
@Derelict
 Would you believe it. That was the last place I never check. Doh ! Thanks.
Would you believe it. That was the last place I never check. Doh ! Thanks. 