Mail server connection from NAT to port-forward
-
Hello,
Since this is my first post i'd like to thank you all.
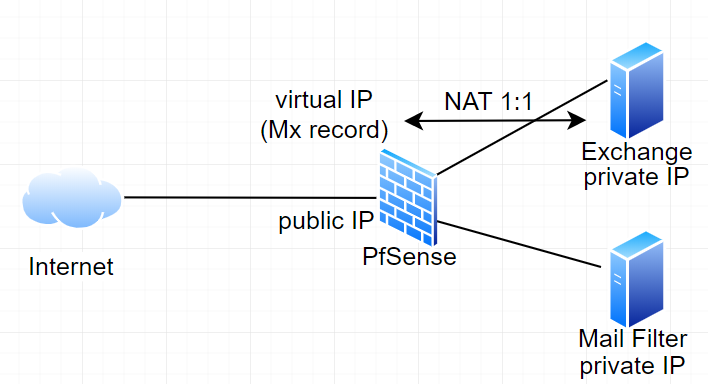
Currently at work there is a PfSence firewall between local network and internet, connected like in the image below (partial rough sketch)
-
Company has more that one public IP addresses
-
Exchange server has private IP
-
Exchange public IP is configured as Vitual IP on PfSence WAN interface
-
Currently there is a 1:1 NAT between public exchange IP (MX record IP) and Exchange private IP address. With a port filter in a different firewall rule.
Now i need to redirect all incoming emails to a new mail-filter VM, since i cannot do that in a NAT 1:1 (or can I ?) I was thinking of the following : -
set port-forward for exchange ports (OWA,IMAP,POP, etc.) to internal ip of exchange server
-
set port-forward for smtp ports to internal ip of mail filter
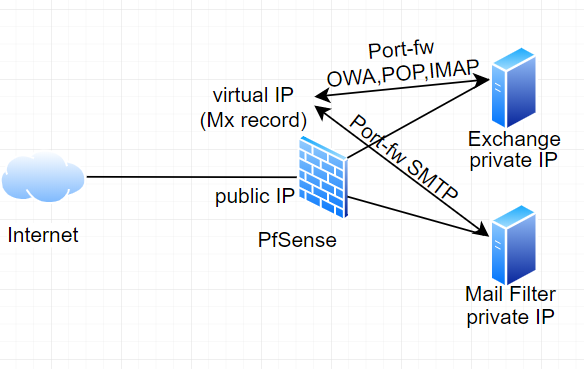
Key things that must be accessible :
- OWA from LAN and Internet
- Exchange connectivity from LAN and Internet
- All external incoming emails must be redirected trough mail-filter server
- All internal emails should not pass trough mail-filter server
- Is all this viable ?
- I understand that PfSense has a system to send packages on the interface that it arrived but is that available for Virtual IP's ?
- Can i make all this modification (disable nat 1:1 and create port-fw rules) in one go, in order to minimize downtime ?
THANKS, I know this was a long post but i'm new too PfSense and very insecure since i must do all this in a production environment being unable to test.
-
-
@MosfetWall said in Mail server connection from NAT to port-forward:
set port-forward for exchange ports (OWA,IMAP,POP, etc.) to internal ip of exchange server
You may put these ports into an alias and use this alias in the fording rule. So all is done with only one rule.
@MosfetWall said in Mail server connection from NAT to port-forward:
I understand that PfSense has a system to send packages on the interface that it arrived but is that available for Virtual IP's ?
?
Response packets on requests from outside which go to the virtual IP will get that virtual IP as source, when they go out on WAN.But if your upstream traffic from the Exchange should get a specific source IP you have to add an outbound NAT rule, after deleting the 1:1.
To do so, go Firewall > NAT > Outbound. If it is still working in automatic mode, switch into the hybrid mode. Then add a new rule:
interface: WAN
source: <Exchange IP>
destination: any
translation: interface addressIf you want, you may also restrict the protocol.
@MosfetWall said in Mail server connection from NAT to port-forward:
Can i make all this modification (disable nat 1:1 and create port-fw rules) in one go, in order to minimize downtime ?
Yes. However, in the past the outbound NAT needed a reboot to apply new rules.
-
Thanks for the answer.
I'v already created two aliases for ports, one with OWA, POP3, IMAP and the other with SMTP ports. I'v read about this in the documentation and it looks way better than one rule for each portCurrently Outbound is in Hybrid mode. It was in manual mode but i'v change it a few days ago -- it didn't make sense for me to use manual mode.
Thanks again.
-
If your exchange sends mails itself without any mail gateway in between and needs to send mails via your external IP that you 1:1 NATted before, I'd let the 1:1 NAT in place and just add port forwards on top. Otherwise if you only use port forwards, that works well, too, but you have to double check you create custom NAT outbound rules so your exchange uses its public NAT IP and the mail filter VM uses whatever you wish it to use :)
-
@JeGr said in Mail server connection from NAT to port-forward:
let the 1:1 NAT in place and just add port forwards on top.
And I do that just by adding a regular port forward ?
The way you suggested seems better since the number of modifications is limited to just one :)
THANKS!
-
You have two things: inbound connections and outbound connections.
A 1:1 NAT will translate both inbound and outbound connections between that inside address and that outside address.
You can override an inbound connection using a specific port forward for that connection profile.
You can override an outbound connection with a specific outbound NAT profile.
If neither a specific inbound port forward or a specific outbound NAT match applies, the 1:1 address translation will apply.
-
Therefore i can leave the NAT and just add a port forward just for SMTP to override the nat for specific ports, levaing me with :
Virutal public ip <--|------ NAT 1:1 (with firewall rule restricting ports) ------> Exchange server | |------- Port Forward rule (redirecting SMTP ports) ---------> Mail Filter serverThanks again , and sorry for asking so many questions and confirmations :D
-
Whether that will work for you based on all your requirements I can't say based on the information that has been provided but, yes, you can just port forward, say, inbound ports 25, 465, and 587 on a particular WAN address to something completely different than a 1:1 NAT on the same destination address.
-
@Derelict
Thanks, again !I'll try this configuration and get back with the result, just in case there is someone else has a similar question.
-
@viragomann @JeGr @Derelict thank you, the traffic redirect works like a charm :)
Thanks again for your time and patience !