Setup DNS over TLS on pfSense 2.4.4 p2 - Guide
-
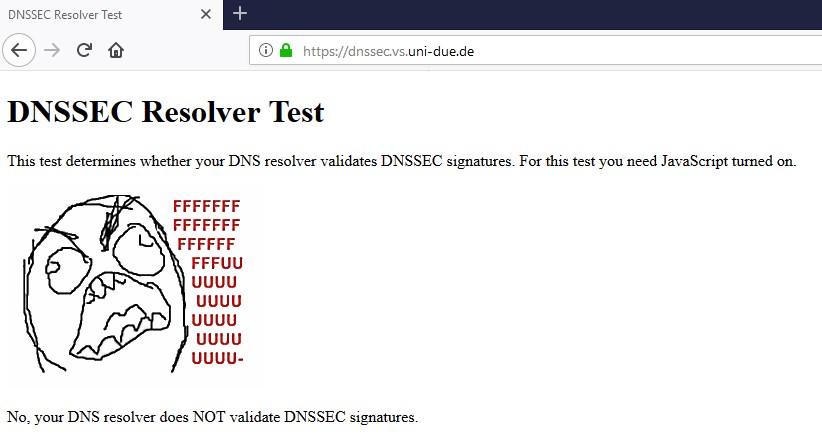
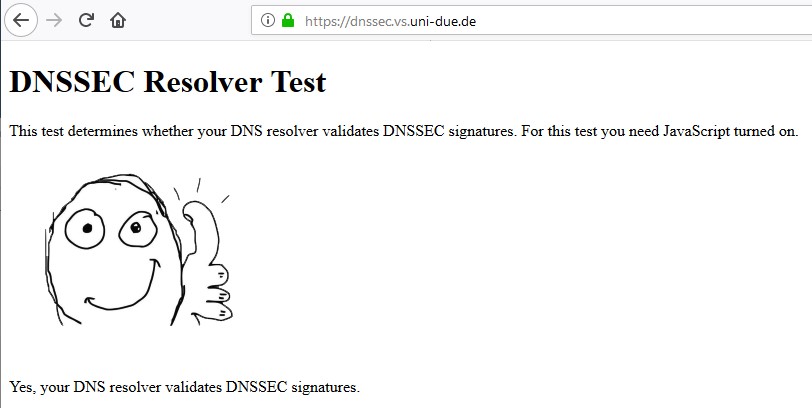
The resolver would of have already validated it if doing dnssec, if it didn't validate it wouldn't give you an answer..
It is pointless to have a forwarder do anything with dnssec.. Unless you want some eyecandy in say pihole or something on which records were validated via dnssec and which were not. But makes no difference - if the resolver is running dnssec, and something doesn't validate - you wouldn't get an answer.
-
Maybe in a perfect world if the upstream forwarder unilaterally did DNSSEC for everything. But in reality, if you don't request validation, it won't outright deny the query like that. At least with some forwarding services like Google public DNS, you have to send the AD/DO flag in the query or they won't drop responses that fail DNSSEC tests.
-
no that is not the way a dnssec resolver works.
here I asked quad 9 for a fqdn that fails validation
; <<>> DiG 9.14.4 <<>> @9.9.9.9 www.dnssec-failed.org ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 39214 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.dnssec-failed.org. IN A ;; Query time: 230 msec ;; SERVER: 9.9.9.9#53(9.9.9.9) ;; WHEN: Thu Sep 26 08:02:01 Central Daylight Time 2019 ;; MSG SIZE rcvd: 50I did not ASK for any dnssec - it just does it..
Now if I ask a non dnssec resolver - say 4.2.2.2, I get an answer
<<>> DiG 9.14.4 <<>> @4.2.2.2 www.dnssec-failed.org ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38029 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 8192 ;; QUESTION SECTION: ;www.dnssec-failed.org. IN A ;; ANSWER SECTION: www.dnssec-failed.org. 7200 IN A 69.252.193.191 www.dnssec-failed.org. 7200 IN A 68.87.109.242 ;; Query time: 38 msec ;; SERVER: 4.2.2.2#53(4.2.2.2) ;; WHEN: Thu Sep 26 08:03:45 Central Daylight Time 2019 ;; MSG SIZE rcvd: 82google does dnssec
; <<>> DiG 9.14.4 <<>> @8.8.8.8 www.dnssec-failed.org ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 25753 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;www.dnssec-failed.org. IN A ;; Query time: 80 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Thu Sep 26 08:04:33 Central Daylight Time 2019 ;; MSG SIZE rcvd: 50https://www.internetsociety.org/blog/2013/05/confirmed-googles-public-dns-now-performs-dnssec-validation-for-all-queries-by-default/
you do not have to ask - when you forward asking for dnssec is pointless!!! Other than maybe your tool providing some eyecandy on which ones pass and which ones don't have it.
-
I recall digging into it a while back and you had to have DNSSEC enabled to get that behavior (at least from Google public DNS servers). I didn't think it was that long ago, though. Maybe it was before 2013. I still wouldn't say it's pointless to ensure you are requesting it.
DNS over TLS still only covers privacy and first-hop validation (Assuming you are checking the hostname/cert), though.
-
no its pointless.. Your forwarding, how is your forwarding even going to validate the records it gets back.. Does it have the anchors? How is it actually going to do the validation?
So I ask 4.2.2.2 +dnssec - still get a freaking answer. I get back the rrsig
; <<>> DiG 9.14.4 <<>> @4.2.2.2 www.dnssec-failed.org +dnssec ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44796 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 8192 ;; QUESTION SECTION: ;www.dnssec-failed.org. IN A ;; ANSWER SECTION: www.dnssec-failed.org. 7200 IN A 69.252.193.191 www.dnssec-failed.org. 7200 IN A 68.87.109.242 www.dnssec-failed.org. 7200 IN RRSIG A 5 3 7200 20191002174442 20190925143942 44973 dnssec-failed.org. cJnvSoQfMtWHg4KWySkDAEaHaqtcw+BlHNC2+MuT1BSJDpn5fv3fIEyG HuPYJ4Pd9N38QgBDA4Bcdfc0O/P5qzvP6+ixCwLNJ9FppRrNVuPG6QCB pIApBzleHvfwKPZUQ1FKXjOaCEb/vQJhJ/QvwSSmz4LLF3sh0M3s8nvK hK8= ;; Query time: 96 msec ;; SERVER: 4.2.2.2#53(4.2.2.2) ;; WHEN: Thu Sep 26 08:10:46 Central Daylight Time 2019 ;; MSG SIZE rcvd: 259Means nothing.. How is it validated by the forwarder? If the forwarder did some sort of validation? You clearly trust this where you forwared, and you picked it to do dnssec for you.. What is the point in trying to doublecheck what it sends you.. It could send you anything it wanted to be honest..
If you want dnssec, run your own resolver (unbound) if you want to forward and have dnssec, then pick a NS you forward to that does dnssec for you. Its that simple - if you forward there is no reason for the forwarder to ask about dnssec. If you want to forward with dot or doh and dnssec - pick a NS to forward to that does what you want to use. Enabling dnssec on a forwarder, that is forwarding to something that doesn't do dnssec is pointless. Having dnssec enabled on your forwarder using forwarding to a resolver that does dnssec is pointless.
If you forward to something that is suppose to be doing dnssec, and you get back an answer for something that should be failing dnssec - then where you forwarding to is broken, so you asking for dnssec is not going to fix their broken setup even if you did get back rrsig for that record..
-
It's not about the client validating it locally but about telling the server "yes, I would like this validated" if the server does so conditionally. Sure, you can pick a forwarder that does what you want 100% of the time but that may not be in your control.
It's not an absolute situation. You can't say it's worthless 100% of the time because you do not know what the servers are doing. Sure, the ones you checked behave that way, but that doesn't mean everyone's always will. You can't make those assumptions.
-
Name one public ns you can ask for dns, that doesn't do dnssec unless you ask it... There is no such animal that I am aware of.. But ok - that is one scenario where could make sense - but wouldn't it just be better solution to just use a forwarder you "know" is doing dnssec.. Which pretty much all the major players are doing now.. Some even have specific IPs you can use that don't do it, etc.But their normal IPs do it out of the box.
If the ns your forwarding to doesn't do dnssec unless you ask it, how do you know its doing it even when you ask it or doing it correctly? You can not assume it would do such a thing.
If you want to turn it on, have it - it shouldn't break anything... I just do not see a point in doing such a thing, ie pointless ;)
If I hire a doorman (that I TRUST) to check ids to make sure they are valid.. And his duty is to validate them (he is doing dnssec).. What is the point in asking him to do it? Oh can you write down the info and send it to me as well, so I can double check your work (so you don' trust him?).. But since he is the one writing down the info on how he validated the ID, how are you to know that its not valid from looking at that info... He could send you anything he wants to send you..
If I hire a doorman, but he only validates the ids if I ask him - so I ask him every time there is an ID to check... He is a pretty shitty doorman, why wouldn't I just hire one that does that already - so I don't have to ask him..
If I hire a doorman that doesn't check IDs, but if I ask him he will pass on the info he has for me to check it, but I don't have a valid way to check it - what is the point?
-
You are assuming people always forward to public DNS servers, too. Too many assumptions about too many things. That's not the way the real world works for everyone all around the globe.
You can qualify your statement and still be correct: Yes, if you know your upstream forwarder is doing DNSSEC properly 100% of the time for all queries, then you most likely do not need to set DNSSEC locally.
But you cannot assume you know how everyone's upstream servers behave.
-
And you think these users do? Are they forwarding to their own resolving NS, then they should set it to do dnssec if that is they want.
So your scenario here is to turn it on - because you don't know it might do something? Is that what your saying?
You either understand how your upstream NS works - your forwarding to it! Or you don't... Turning dnssec on hoping it does something is again - pointless!!
-
I'm saying you can't always say it's pointless. The user has to make that determination based on the behavior of their chosen forwarding server. Is it typically unnecessary? Probably. But that's between the user and their DNS servers.
-
@jimp said in Setup DNS over TLS on pfSense 2.4.4 p2 - Guide:
But that's between the user and their DNS servers.
Valid point. But all I can do is base my recommendation on experience with dns.. And in all of that experience I have never seen a scenario where it makes sense to do dnssec if your forwarding... Is it possible there is some odd ball setup where it might do something. Sure ok..
Your assuming the users actually understand what they are doing... They don't or they wouldn't be here asking ;) And to be honest if they are doing some odd ball setup where forwarding and asking for dnssec actually does something worthwhile.. I would tell them they are doing it wrong ;) Why not just forward to NS that actually does dnssec without asking it to do it ;)
If a NS doesn't do dnssec unless you ask for it, how could it serve you up stuff from cache? Since if it didn't do dnssec that cache info is not validated... So It can not serve it up to anyone that asks for dnssec, It would have to do a fresh resolve. So its either doing dnssec all the time, so it only places stuff that validates in its cache, or does not have any dnssec set on it.. Or its not... So asking some NS to to do dnssec that isn't doing it all the time makes no sense really.. Because it would not be able to use its cache - which is really the point of forwarding. If your just to resolve anything you ask and do dnssec on it - might as well just run my own resolver and get the info directly, etc.
Lets just agree to disagree here I guess. I will give you the point that we can not know all possible scenarios that a user might be doing, and we are only assuming.. But I for the life of me can not fathom an actual real world scenario were it would make any sense to ask for dnssec of a NS I am forwarding too that doesn't already do it anyway. So no reason to ask in the first place.
-
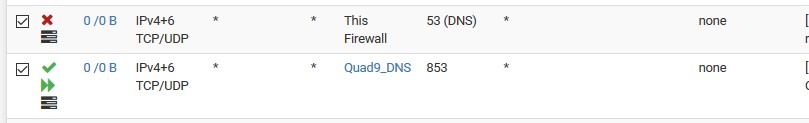
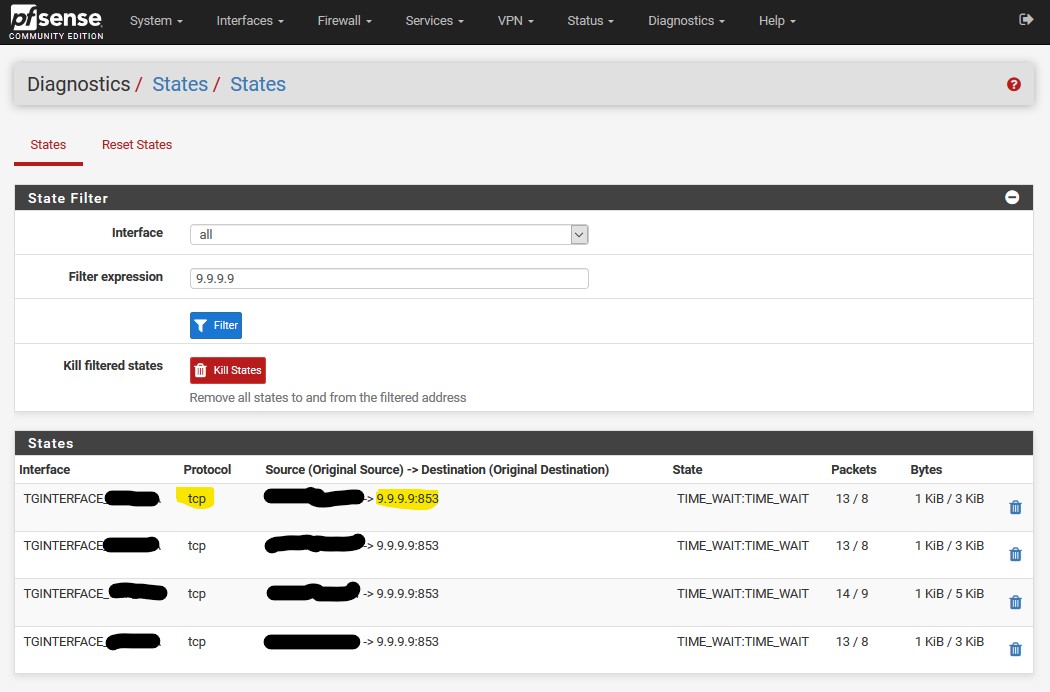
I did these same steps but used 1.1.1.1 and 1.0.0.1. My connection states show its TCP 853 traffic to 1.1.1.1.
But when I use cloudflare’s tester, it shows it failed. Ignore the 192.168.1.11, that’s a hard coded machine I have to fix.Settings: https://imgur.com/gallery/2gbd2Il
Fail: https://imgur.com/gallery/xeclJ0W
-
How would they know how you talked to 1.1.1.1 - the test is not valid unless your talking to their dns..
They can only test that your encrypted or not encrypted to dns if your actually talking to them for dns.. That test should say NA unless your talking to them.. Not that your unsecured - they have no clue what port or protocol or anything on how you talked to 1.1.1.1
This is what it should say
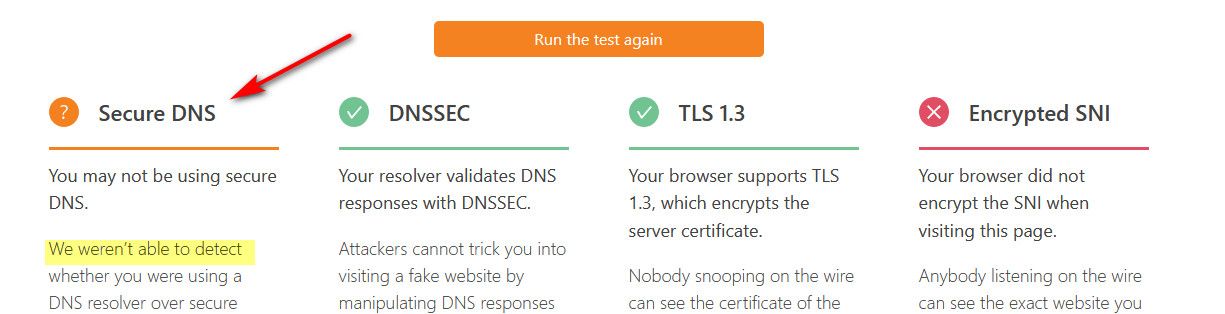
-
For some reason, now it shows Secure DNS. Not sure what changed to make it do it or why yours is showing a question mark....
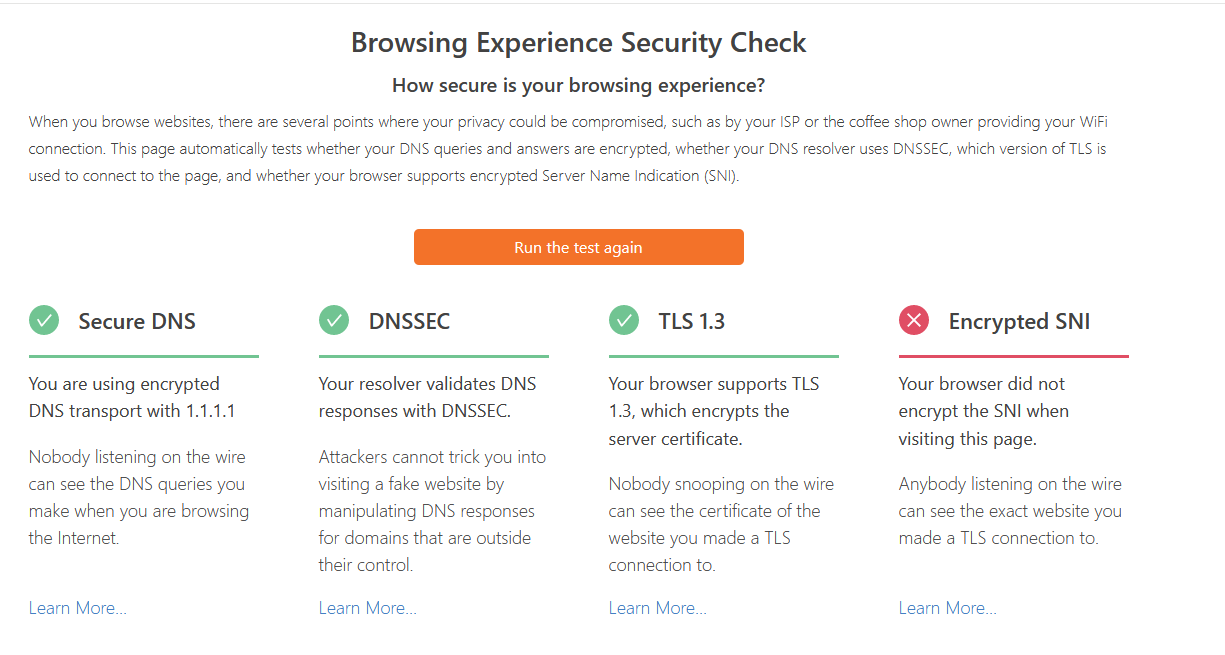
-
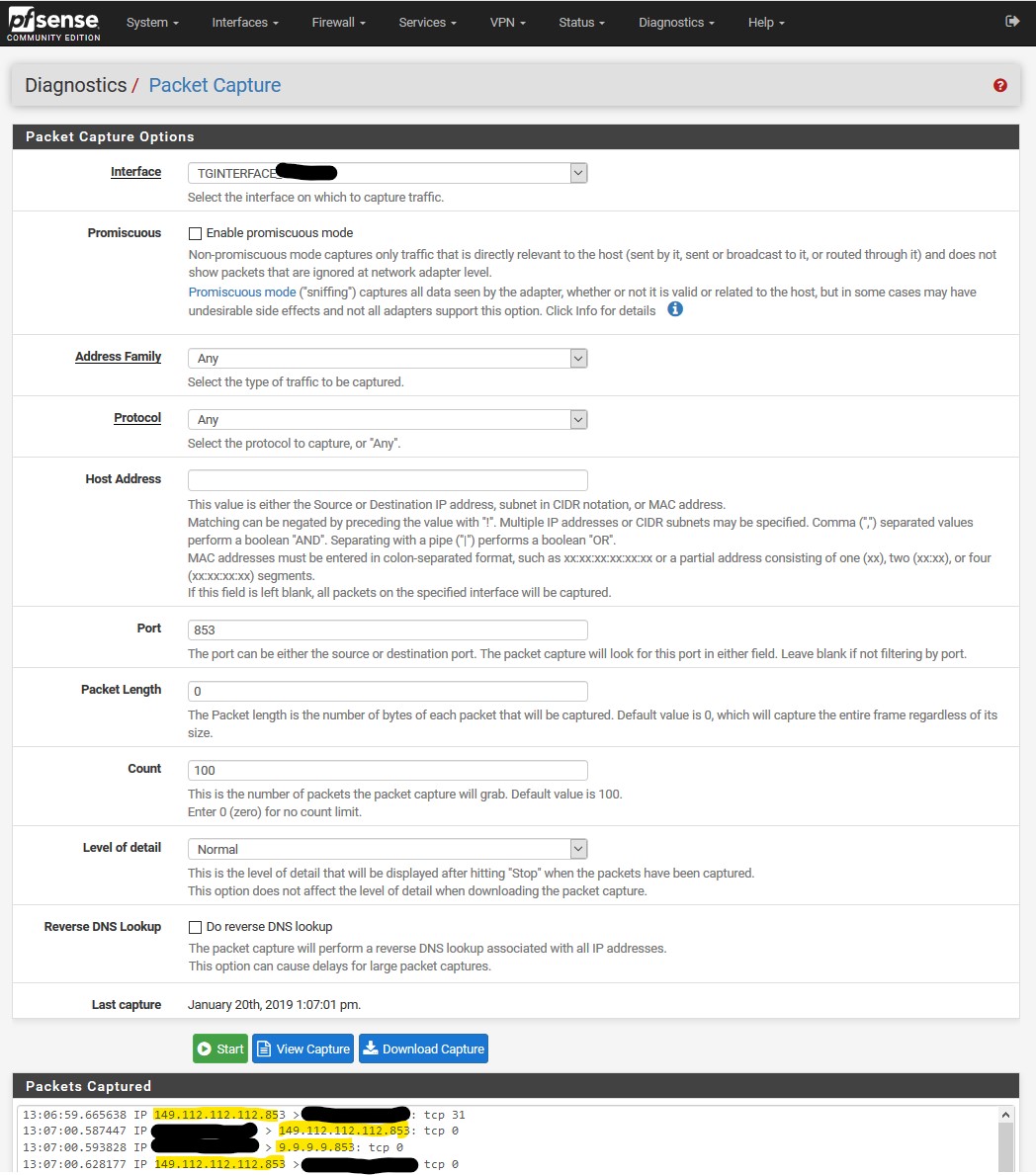
I can't tell by all of the different posts... but what block rule would you use to block any 53 traffic just on the lan network from going outbound to make sure your not leaking? I have a separate lan I still want 53 traffic to work.
-
If you don't want 53 outbound, then block that.. Rules are evaluated top down, first rule to trigger wins.. No other rules are evaluated..
Allow to what you want 53 to go to, below block 53 to anything else. Its that simple. Do you really need a picture?
here
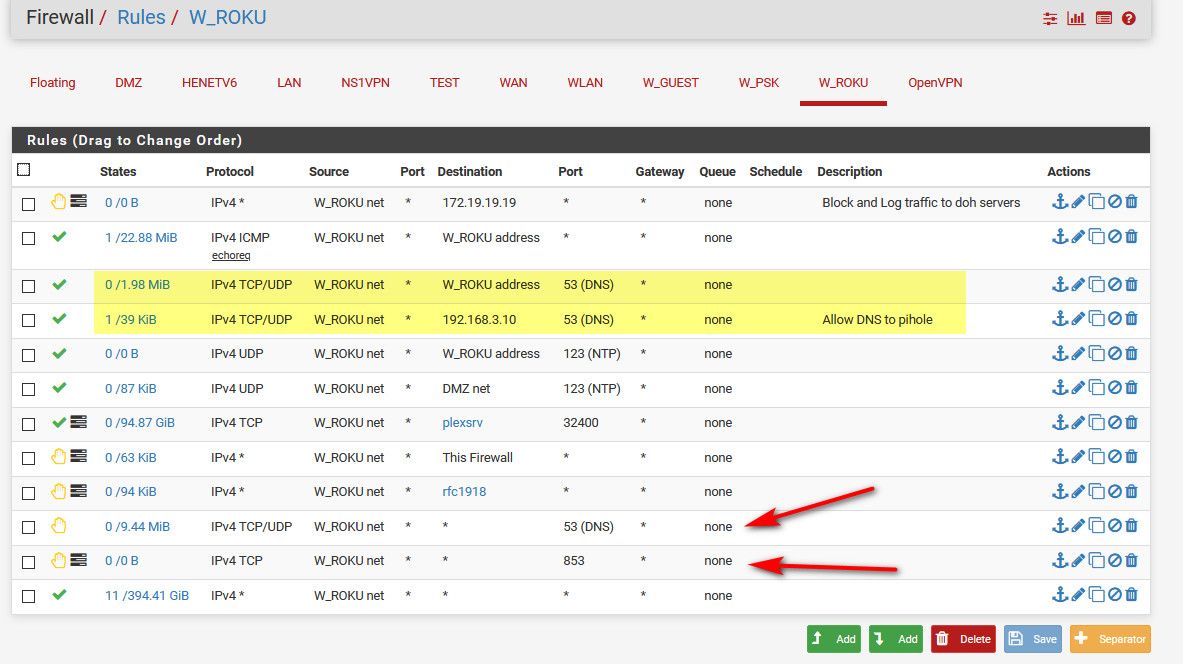
I allow dns to pfsense address, and my pihole (that sits on another segment)
I then block any other access to 53, and 853 (dot)..The top rule there blocks access to what the doh servers resolve too for doh, I have all of the known doh servers resolve to that IP.. This an attempt to block access to doh, since doh really needs to use a url to be used, and I have all of their names setup to resolve to that IP.
example snip of some of them. There are many more.
local-data: "cloudflare-dns.com. 120 IN A 172.19.19.19" local-data: "dns.quad9.net. 120 IN A 172.19.19.19" local-data: "dns9.quad9.net. 120 IN A 172.19.19.19" local-data: "dns10.quad9.net. 120 IN A 172.19.19.19" local-data: "doh.opendns.com. 120 IN A 172.19.19.19" local-data: "doh.cleanbrowsing.org. 120 IN A 172.19.19.19" local-data: "dns.nextdns.io. 120 IN A 172.19.19.19"The plan is to also create an alias with all the know IPs of the doh servers, and directly log any traffic to them on 443 - but haven't set it up yet.
For them to say your using secure dns, means your asking them directly! Its pretty clear there.. where it states "you are using encrypted transport with 1.1.1.1"
-
Hi all,
late to the thread, but related to my current issue.
First off, to block all outgoing traffic to port 53, I have a floating rules to allow lan etc in on 53 (quick), then the next rule to block all 53 traffic including on WAN "OUT". This blocks everything including packets originating from pfsense itself. I have logging turned on, so any escapees show up. The main thing to note is that floating rules can block outgoing traffic on a network, unlike normal rules which can only block incoming so are no good at blocking connections originating from pfsense.
I have set up a NAT on the LAN to force any attemped UDP:53 from the lan to use pfsense. I have a nvidia shield which insists on using 8.8.8.8 udp 53.
I have set up DNS resolver to forward to 1.1.1.1 etc using TLS etc.
Now the problem I see is occasionally PFSense is sending out requests to UDP 53. I unblocked my floating-WAN-OUT-53 rule (or changed it to a pass ) and use a looping shell script and sockstat to locate the culprit (Please tell me a more elegant way to do this). I found things like ntpd and ntopng were causing this.
Now /etc/resolv.conf shows:
nameserver 127.0.0.1
nameserver 1.1.1.1
nameserver 1.0.0.1I am thinking that local pfsense services are using the /etc/resolv.conf and sometimes not going to 127.0.0.1, in which case a direct UDP to 53 is being used.
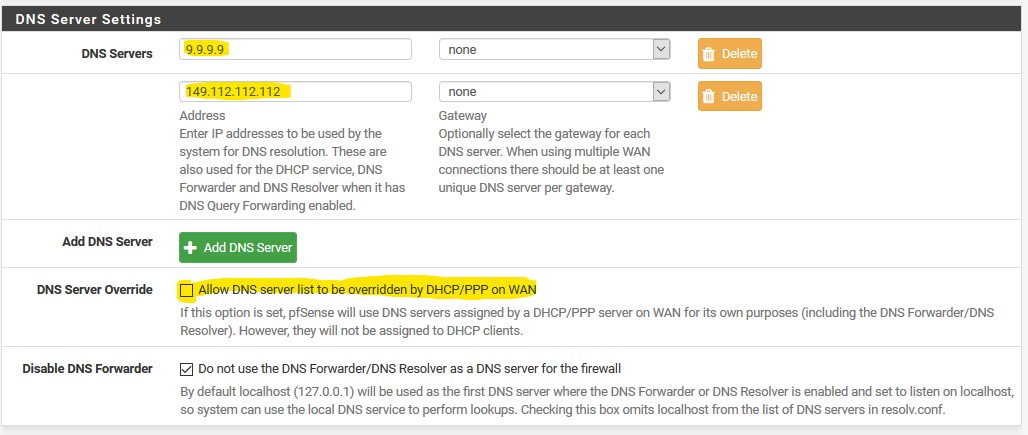
It seems to me that the resolv.conf is populated from the entries in system/generalsetup/DNS server settings/DNS servers, but idealy the forwarding resolver should be using a different list. i.e. resolve.conf: 127.0.0.1 and forwarding 1.1.1.1, 1.0.0.1 with TLS etc.My solution is to go back to the "Custom Settings" as outlined in "https://www.netgate.com/blog/dns-over-tls-with-pfsense.html" and remove all entries in general setup/DNS servers (leaving only 127.0.0.1 in resolv.conf)
I guess the other option is to just keep blocking outgoing port 53.
Comments please.
Duncan
-
@duncan-young said in Setup DNS over TLS on pfSense 2.4.4 p2 - Guide:
I am thinking that local pfsense services are using the /etc/resolv.conf and sometimes not going to 127.0.0.1, in which case a direct UDP to 53 is being used.
That means that these services have some kind of resolver integrated.
In that case you should set up these services to use the local unbound' facilities.
But, as far as I know, such kind of services are not used by pfSense.
Some package ?@duncan-young said in Setup DNS over TLS on pfSense 2.4.4 p2 - Guide:
PFSense is sending out requests to UDP 53
Do not forget to filter TCP:53 requests.
@duncan-young said in Setup DNS over TLS on pfSense 2.4.4 p2 - Guide:
but idealy the forwarding resolver should be using a different list. i.e. resolve.conf: 127.0.0.1 and forwarding 1.1.1.1, 1.0.0.1 with TLS etc.
Noop.
unbound, as any other local resolver/forwarder uses the system file /etc/resolv.conf
Check also your main unbound config file, /var/unbound/unbound.conf -
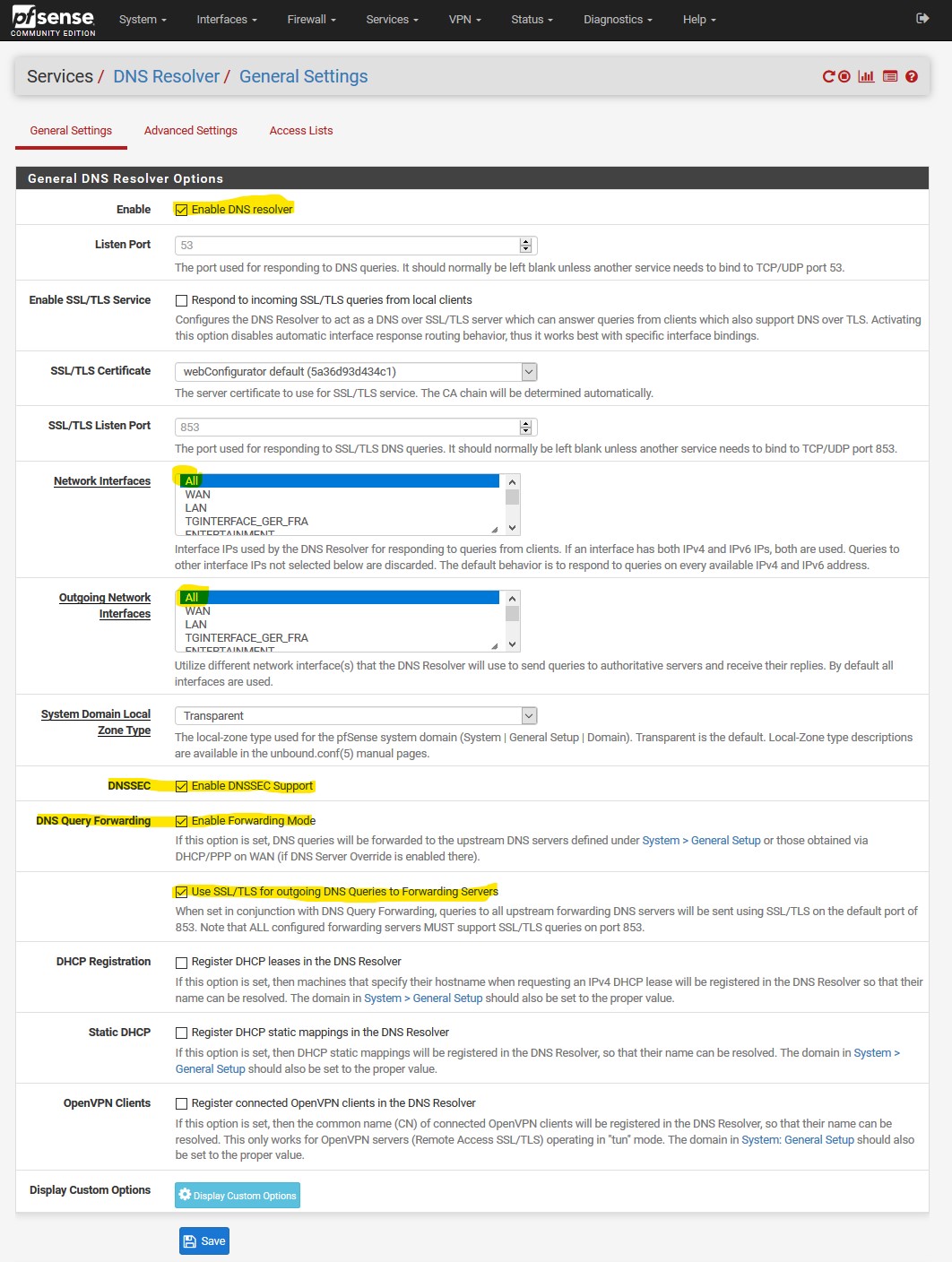
I've configured DoT using Quad9 and a floating rule to reject any to any on port 53,
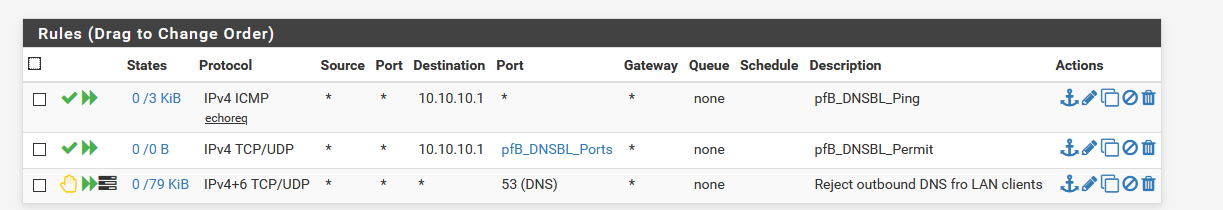
the only difference between the first picture in this tread is my "System / General Setup" as t I have unchecked "disable DNS forwarder".When I test https://tenta.com/test/ it tells me that tls is false?
Thanks for any help, cheers Qinn
-
@Qinn said in Setup DNS over TLS on pfSense 2.4.4 p2 - Guide:
as t I have unchecked "disable DNS forwarder".
Then pfsense wouldn't use itself for dns..
Do not use the DNS Forwarder/DNS Resolver as a DNS server for the firewallThat should always be "unchecked" to be honest. Unless you don't want pfsense using is own local dns be it the the forwarder or the resolver. This is not a guide to how to do dns over tls - its one persons mistaken take on how to do it.. Not correct by any means.