Unbound vs. Pihole
-
On PiVPN, looks unsupported now: https://github.com/pivpn/pivpn
"This means that there are no longer any active maintainers for this project, and that issues and PR's will not get resolved. This will eventually result in pivpn not working anymore (as openvpn gets updates, config options might get added/removed/changed)."
-
I have been using Pihole inside a Debian Linux VM running on Proxmox for a few weeks now and have been very happy with the performance. As of right now I'm only using one Pihole, but could envision launching another VM running Pihole down the the the road (for redundancy, or maybe to have a different blocklist configuration if it becomes necessary to better control what is filtered for different network segments).
In terms of caching, I use both the Pihole cache and the cache on Unbound (in my setup Pihole forwards DNS traffic to Unbound that is not cached). You'll have to do some testing, but I believe that the performance of dnsmasq on Pihole starts to become negatively affected if the cache is made too large (perhaps due to increased cache lookup time?). By default, the cache size in Pihole is 10000 entries, which works just fine on a smaller network like mine with less than 50 devices (and honestly, is likely still too big). It may/may not work well for a larger network with ~500 devices that you are describing. Having said that, a lot of DNS records these days have very short TTL, so that default cache size on Pihole may be ok (i.e. you wont' see any cache evictions). Finally, you can also disable the cache on Pihole altogether and just forward everything to Unbound - if done on a local network, it will probably add less than 1ms of latency for each DNS lookup, which is inconsequential.
Hope this helps.
-
I'm setting all this up soon. Just want to be clear. So which IP address do I use to forward my Pihole to the Pfsense Unbound resolver?
-
@liquidsuspension I used the IP v4 and v6 addresses of Lan 1
-
@stan-qaz Thanks!
-
Hi,
I currently use pfSense with Unbound as resolver and pfblockerng-devel. It works fine but I'd like to have a play with piHole and think of buying a Raspberry Pi 4 for this. If it turns out it's not for me I can easily find another use for the hardware.
But I have a question regarding fallback. What I would like to do is have my devices DNS pointed to the RPI and piHole, which is then pointed for DNS queries to Unbound on pfsense. All that should be easy I believe.
But I also would like some kind of automatic fallback so that if the RPI is not available for any reason, that my devices can temporarily and automatically fall back to sending requests directly to pfSense for uninterrupted operation (even if that means no piHole/pfblocker protection, I'm fine with that).
Is there an easy way to accomplish that? Thanks...
-
@occamsrazor There is no simple way as DNS doesn't offer a primary/secondary server option. When you supply more than one resolver address the client makes a choice between the ones based on their responses.
You could write a script that monitored the pi-hole and if it went down change the pfSense DHCP DNS settings but that wouldn't help the clients until they renewed their leases and updated from the new server settings.
You might also build a proxy to manage the fail-over and have it monitor the pi-hole and decide where to send the DNS queries it gets.
I took an alternate route and use two piholes for redundancy. That isn't really necessary as the pi-holes have proven very reliable but it is handy when I do something to break one when tweaking things.
There are scripts on the pi-hole reddit that support syncing two or more pi-holes if you want to go that route.
The only tweak I'd suggest is checking the cron settings to insure that both don't update the internal blacklists at the same time.
-
@occamsrazor I missed a comment I intended to make, a Pi 4 is overkill for a pihole, a Zero or Zero W is plenty of power. I use Pi 3s as they are much lower power and run cooler. An original Pi (square card) is barely enough to work well, the first revision with round corners and double the RAM works fine as do Pi 2s.
Many folks are happy with the Zero but I didn't want to fuss with adding Ethernet to it and I prefer wired connections for essential servers/services due to my network configuration.
-
@stan-qaz Thanks for the useful info.... I guess I had thought that I could push the two DNS servers in order to clients from pfSense DHCP.... but you are right the clients wouldn't query in strict order, so even if piHole was availabel there's probability that many requests would get answered by pfsense directly instead....
I guess perhaps I'll just have to live with manually changing the DNS server addresses if needed when the piHole is down. 2 x Pi for redundancy is smart, but more than I want to do. It'll run in a server rack on UPS, so should be reasonably reliable.
As for the models, I realise Pi4 is overkill... but with the various power supplies, case etc the price isn't all that more expensive and would rather future-proof in case I choose to use it for a different purpose later. Any idea roughly how many watts it would consume if just used for Pihole?
Another totally linux-newb question... if running pihole on it can I also easily and simultaneously run other server type services on it (cpu-permitting of course)?
Thanks :-) -
@occamsrazor Runing on a UPS fixes one of the major Pi failure modes, a corrupted SD from improper shutdown. Using one of the pi-hole recommended SD cards with good write endurance avoids many other SD issues from poor quality cards. I haven't moved my logs off the SD but for really busy systems that is also an option.
Price wasn't part of my Pi 3 consideration, stability, power use and being well understood were. The 4 will work but keep up with the firmware and software updates as they work to solve the issues with the 4, also be cautious in power supply selection with the Rev 1 board, hopefully the USB power configuration will be fixed when they go to Rev 2 but I have heard no dates on when to expect that.
CPU use and power on the Pi-hole is usually just about at idle levels, DNS lookups are not much of a load. Some of the web based queries and list updates can use about a full core but are both short duration events. Normal load looks to be about 0.25, memory use with 700K list entries is under 30% with the GUI and VNC running.
Running other stuff is not an issue as long as you can de-conflict any requirements for the same ports/services.
Probably best to take the pi-hole details discussion to the pi-hole reddit to keep from cluttering up this place with non pfSense info.
https://www.reddit.com/r/pihole/
-
@stan-qaz - Thanks a lot for the detailed information. Am still tempted by the Pi4 for it's beefier CPU in case I want to run multiple services. Will take further questions to the pihole reddit.... Thanks :-)
-
when i have to go to the supermarket to buy the toilet paper i always go with a ferrari

for the same reason even if the pi3 is more than enought for pihole i personally will buy the pi4,
the USB-C is not really a big problem, just don't buy any e-marked USB-C chargers, the official one or any chargers coming from a smartphone/tablet that can do 5v / 3a work without problem.
i didn't have any stability problem on my 3 raspberry pi 4, with kodi /ntp server/wireshark and other services i'm running, personally the only downside i see here is power consumption -
@kiokoman said in Unbound vs. Pihole:
personally the only downside i see here is power consumption
I do try and minimise power consumption as much as possible, but then again I'm running a server rack with pfsense router, QNAP NAS, 48-port Ubiquiti switch, Ubiquiti CK2+ controller/surveillance and 3 access points.... so doubt a Pi is gonna make a huge difference to that. Do you have a rough idea of Pi4 power consumption in watts for typical usage?
Also, how do you find piHole compares to pfblockerng-devel for protection against malware, ransomware, etc (as opposed to ad-tracking)? Are the lists easy to maintain? I really liked pfblockerng but I found issues with lists not downloading after a while and generally had issues with maintaining it after a while.
-
@occamsrazor

Idk, my network is more or less like what you have
I don't use pihole nor pfblocker, i have suricata on pfsense and bind9 on a server -
@occamsrazor said in Unbound vs. Pihole:
Do you have a rough idea of Pi4 power consumption in watts for typical usage?
To the power question, here I found this
https://www.tomshardware.com/reviews/raspberry-pi-4-b,6193.html
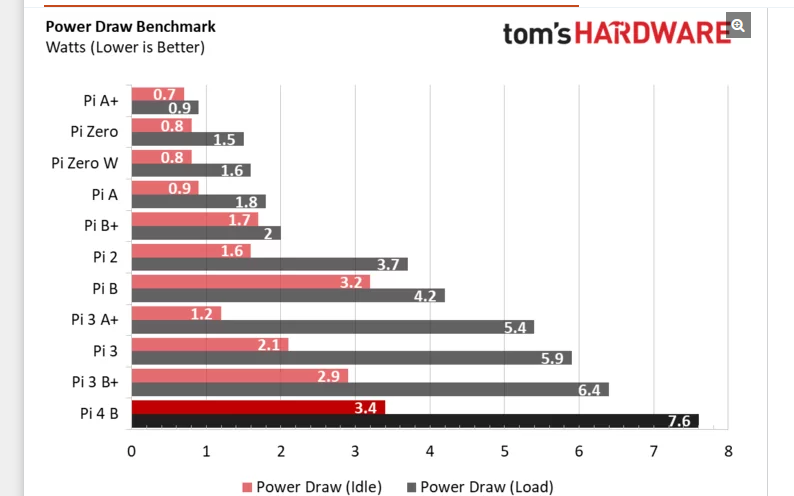
Compared to a pi3 b+ its almost not worth even discussing to be honest.. Especially when you compare overall performance differences.. I can not see for the life of my why anyone would buy a 3 vs a 4 currently.. Unless there was something very specific needed to use the 3.. Which off the top - not sure what that could be - maybe a hat a peripheral that didn't work with the 4?? Or maybe can not get a 4 because of out of stock or something, and you want the pi now, so you get just the 3
So lets say your pi4 was just balls out all the time drawing 7.6 watts.. Lets call it 8.... If you do the math...
Assuming your elec cost you 12 cents per kwh
Electricity cost per day: $0.02304
Electricity cost per month: $0.70128
Electricity cost per year: $8.41536So worse case its going to cost you something like $8 a YEAR to run your pi 24/7/365 with it just balls out running 100%..
For it to be just doing dns.. your prob going to be real near the idle usage.. So what like $4 a year.. Not sure what you pay for elec... But adjust for your cost... For each cent difference from the 12 cent, about 0.70 a year difference.. At the full balls out 8 watt number.
If your really wanting to lower the elec cost - just get a zero.. It can more than handle running pihole..
-
Thanks @johnpoz.
If you have a pihole which is set to resolve against pfsense which is DNS resolving from root servers, will the Redirecting all DNS Requests to pfSense rule still work?
ie. the rule described here: https://docs.netgate.com/pfsense/en/latest/dns/redirecting-all-dns-requests-to-pfsense.htmlDo you just need to change the Redirect Target IP to the pihole internal IP?
Does the Redirecting all DNS Requests to pfSense work with DNS over TLS, port 853?
-
I am not a fan of "redirecting" anything - I would just block anything from talking to anything other than pfsense for dns..
But sure you can still redirect anything that might ask something other than pfsense or pihole on 53 to go to pihole - but you prob need to put pihole on a different network than the client is on or you run into some weirdness... There was a thread not that long ago where this came up.
As to redirecting some client that tries to go to 1.2.3.4 on 853 for dns via dot.. While you could have have something listening on 853 for dot.. unbound can do this - you never know what the client might be doing to validate - maybe the end dns they are trying to talk to via dot has to be using a specific cert? etc..
-
Hi @johnpoz,
yes that makes sense. So maybe use this method instead to block both ports 53 and 853, and enforce only using pfsense for DNS:
https://docs.netgate.com/pfsense/en/latest/dns/blocking-dns-queries-to-external-resolvers.html
-
yup that is how you would do it..
-
There’s a simpler way to do it combined in a single rule, with an alias for the two DNS ports (if you need more than one) and a “!” to invert the meaning, see this post:
https://forum.netgate.com/post/791318
Hope am remembering/linking correctly, am on my phone at the moment...