-
So this is a mobile IPSec setup? What are you trying to connect from?
Did you follow one of the doc pages to set this up? Which one?
What error do you see in the server side logs?
Steve
-
Hi Steve,
Thank you for your reply..yes this is moble IPSEC seup with L2TP..am trying to connect from a windows 10 laptop..i have the user am using is created from the AD and when i test on pfsense the user is authenticatate. am getting this error.." The remote connection was denied because the username and password combination you provided is not recognized,or the selected authentication protocol is not permitted on the remote server"
-
on the server log am getting the following error :
Oct 2 14:59:46 charon 09[ENC] <con-mobile|154> generating ID_PROT response 0 [ ID HASH ]
Oct 2 14:59:46 charon 09[NET] <con-mobile|154> sending packet: from 41.221.97.2[500] to 192.168.101.82[500] (76 bytes)
Oct 2 14:59:46 charon 08[NET] <con-mobile|154> received packet: from 192.168.101.82[500] to 41.221.97.2[500] (476 bytes)
Oct 2 14:59:46 charon 08[ENC] <con-mobile|154> parsed QUICK_MODE request 1 [ HASH SA No ID ID ]
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> looking for a child config for 41.221.97.2/32|/0[udp/l2f] === 192.168.101.82/32|/0[udp/l2f]
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> proposing traffic selectors for us:
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> 41.221.97.2/32|/0
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> proposing traffic selectors for other:
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> 192.168.101.82/32|/0
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> candidate "con-mobile" with prio 1+1
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> found matching child config "con-mobile" with prio 2
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> selecting traffic selectors for other:
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> config: 192.168.101.82/32|/0, received: 192.168.101.82/32|/0[udp/l2f] => match: 192.168.101.82/32|/0[udp/l2f]
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> selecting traffic selectors for us:
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> config: 41.221.97.2/32|/0, received: 41.221.97.2/32|/0[udp/l2f] => match: 41.221.97.2/32|/0[udp/l2f]
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> selecting proposal:
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> no acceptable ENCRYPTION_ALGORITHM found
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> selecting proposal:
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> proposal matches
Oct 2 14:59:46 charon 08[CFG] <con-mobile|154> received proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:NULL/HMAC_SHA1_96/NO_EXT_SEQ, AH:HMAC_SHA1_96/NO_EXT_SEQ -
Looks like a mismatched encryption type at phase 2:
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ipsec-troubleshooting.html#phase-2-encryption-algorithm-mismatchDid you set AES 128 as shown here?
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/l2tp-ipsec.html#phase-2Steve
-
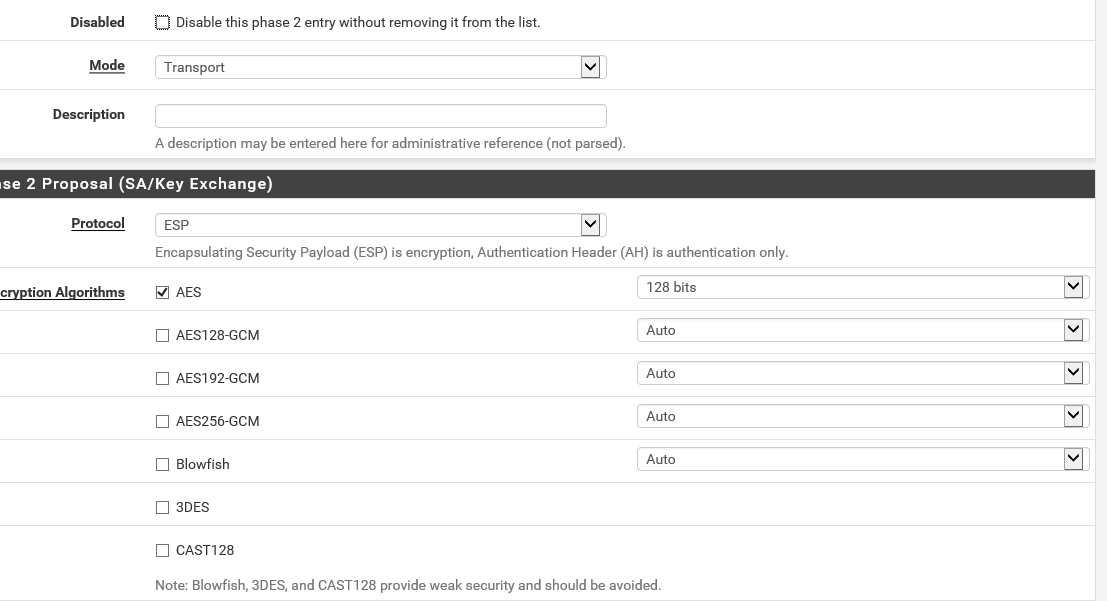
-
Did i miss something here?
-
No, that looks correct. Were there any further logs after that point?
-
Oct 2 18:00:10 charon 08[ENC] <con-mobile|175> generating ID_PROT response 0 [ ID HASH ]
Oct 2 18:00:10 charon 08[NET] <con-mobile|175> sending packet: from 41.221.97.2[500] to 192.168.101.82[500] (76 bytes)
Oct 2 18:00:10 charon 06[NET] <con-mobile|175> received packet: from 192.168.101.82[500] to 41.221.97.2[500] (476 bytes)
Oct 2 18:00:10 charon 06[ENC] <con-mobile|175> parsed QUICK_MODE request 1 [ HASH SA No ID ID ]
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> looking for a child config for 41.221.97.2/32|/0[udp/l2f] === 192.168.101.82/32|/0[udp/l2f]
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> proposing traffic selectors for us:
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> 41.221.97.2/32|/0
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> proposing traffic selectors for other:
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> 192.168.101.82/32|/0
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> candidate "con-mobile" with prio 1+1
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> found matching child config "con-mobile" with prio 2
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> selecting traffic selectors for other:
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> config: 192.168.101.82/32|/0, received: 192.168.101.82/32|/0[udp/l2f] => match: 192.168.101.82/32|/0[udp/l2f]
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> selecting traffic selectors for us:
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> config: 41.221.97.2/32|/0, received: 41.221.97.2/32|/0[udp/l2f] => match: 41.221.97.2/32|/0[udp/l2f]
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> selecting proposal:
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> no acceptable ENCRYPTION_ALGORITHM found
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> selecting proposal:
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> proposal matches
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> received proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:NULL/HMAC_SHA1_96/NO_EXT_SEQ, AH:HMAC_SHA1_96/NO_EXT_SEQ
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> configured proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 2 18:00:10 charon 06[CFG] <con-mobile|175> selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 2 18:00:10 charon 06[IKE] <con-mobile|175> received 250000000 lifebytes, configured 0
Oct 2 18:00:10 charon 06[ENC] <con-mobile|175> generating QUICK_MODE response 1 [ HASH SA No ID ID ]
Oct 2 18:00:10 charon 06[NET] <con-mobile|175> sending packet: from 41.221.97.2[500] to 192.168.101.82[500] (188 bytes)
Oct 2 18:00:10 charon 06[NET] <con-mobile|175> received packet: from 192.168.101.82[500] to 41.221.97.2[500] (60 bytes)
Oct 2 18:00:10 charon 06[ENC] <con-mobile|175> parsed QUICK_MODE request 1 [ HASH ]
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> CHILD_SA con-mobile{150} state change: CREATED => INSTALLING
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> using AES_CBC for encryption
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> using HMAC_SHA1_96 for integrity
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> adding inbound ESP SA
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> SPI 0xce74c17d, src 192.168.101.82 dst 41.221.97.2
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> adding outbound ESP SA
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> SPI 0x03949e48, src 41.221.97.2 dst 192.168.101.82
Oct 2 18:00:10 charon 06[IKE] <con-mobile|175> CHILD_SA con-mobile{150} established with SPIs ce74c17d_i 03949e48_o and TS 41.221.97.2/32|/0[udp/l2f] === 192.168.101.82/32|/0[udp/l2f]
Oct 2 18:00:10 charon 06[CHD] <con-mobile|175> CHILD_SA con-mobile{150} state change: INSTALLING => INSTALLED
Oct 2 18:00:12 charon 06[NET] <con-mobile|175> received packet: from 192.168.101.82[500] to 41.221.97.2[500] (76 bytes)
Oct 2 18:00:12 charon 06[ENC] <con-mobile|175> parsed INFORMATIONAL_V1 request 3468192345 [ HASH D ]
Oct 2 18:00:12 charon 06[IKE] <con-mobile|175> received DELETE for ESP CHILD_SA with SPI 03949e48
Oct 2 18:00:12 charon 06[CHD] <con-mobile|175> CHILD_SA con-mobile{150} state change: INSTALLED => DELETING
Oct 2 18:00:12 charon 06[IKE] <con-mobile|175> closing CHILD_SA con-mobile{150} with SPIs ce74c17d_i (1004 bytes) 03949e48_o (1312 bytes) and TS 41.221.97.2/32|/0[udp/l2f] === 192.168.101.82/32|/0[udp/l2f]
Oct 2 18:00:12 charon 06[CHD] <con-mobile|175> CHILD_SA con-mobile{150} state change: DELETING => DELETED
Oct 2 18:00:12 charon 06[CHD] <con-mobile|175> CHILD_SA con-mobile{150} state change: DELETED => DESTROYING
Oct 2 18:00:12 charon 08[NET] <con-mobile|175> received packet: from 192.168.101.82[500] to 41.221.97.2[500] (92 bytes)
Oct 2 18:00:12 charon 08[ENC] <con-mobile|175> parsed INFORMATIONAL_V1 request 715140230 [ HASH D ]
Oct 2 18:00:12 charon 08[IKE] <con-mobile|175> received DELETE for IKE_SA con-mobile[175]
Oct 2 18:00:12 charon 08[IKE] <con-mobile|175> deleting IKE_SA con-mobile[175] between 41.221.97.2[41.221.97.2]...192.168.101.82[192.168.101.82]
Oct 2 18:00:12 charon 08[IKE] <con-mobile|175> IKE_SA con-mobile[175] state change: ESTABLISHED => DELETING
Oct 2 18:00:12 charon 08[IKE] <con-mobile|175> IKE_SA con-mobile[175] state change: DELETING => DELETING
Oct 2 18:00:12 charon 08[IKE] <con-mobile|175> IKE_SA con-mobile[175] state change: DELETING => DESTROYING -
@rsohaya said in pfsense LDAP ipsec authentication not working:
Oct 2 18:00:10 charon 06[IKE] <con-mobile|175> CHILD_SA con-mobile{150} established with SPIs ce74c17d_i 03949e48_o and TS 41.221.97.2/32|/0[udp/l2f] === 192.168.101.82/32|/0[udp/l2f]
Hmm, odd it gets as far as creating the child SA even with that error. Then the client deletes it:
Oct 2 18:00:12 charon 06[IKE] <con-mobile|175> received DELETE for ESP CHILD_SA with SPI 03949e48What do you have configured at Phase 1?
Steve
-
@stephenw10 I just want to point out the notice that appears on the page you referenced at https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/l2tp-ipsec.html#phase-2
Users have reported issues with Windows L2TP/IPsec clients behind NAT. If the clients will be behind NAT, Windows clients will most likely not function. Consider an IKEv2 implementation instead.
In the logs posted, one side sure looks like it is behind a NAT.
-
Yup it is broken is fun ways but I didn't think it failed like that. It's been a while since I tried it though.
But, you're right, ultimately this probably will fail even if we get past this with a client behind NAT (which is almost all clients!)
Using some other VPN here is probably going to save pain!
Steve
-
@stephenw10 I think OP want's to use the built-in Windows IPSEC VPN functionality, but nothing works like OpenVPN. So easy to configure compared to IPSEC.
-
Indeed, for mobile it's hard to beat.
If you need to use only included clients (in Windows) it's IKEv2 with EAP-MSCHAPv2 and that can be painful.
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html
Steve
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.