Pfsense hangs when trying to update static routes
-
That is just moronic.. You want pfsense to every 5 minutes resolve 8K some fqdn? And then add routes for those?
-
How should I be doing this then?
-
Just policy route the traffic out the vpn..
Where did you get those instructions?
After all your devices contact netflix and is working place the Lan rule you created below the the default lan to any rule so that it does not leak your isp public ip assigned to you.
That is just idiotic as well..
-
https://www.privateinternetaccess.com/forum/discussion/21421/pia-vpn-neftlix-bypass-for-pfsense
Can you explain or point me where to read on using policy routes to traffic out of the vpn?
-
That is just nonsense.. But you will notice he is using static range of IPs..
And you wouldn't need to add routes, you would just policy route it out a dest out your wan.
When you policy route, you don't grab routes from your vpn service.
Simpler thing would be to do is just route your device doing netflix out your wan via its source IP. Or better yet send only the stuff you need/want out your vpn out the vpn vs everything expect some service that is hosted of CDNs
Also that thread is dated from 2016.. I can pretty much promise you those IPs are no longer viable.
-
I'm not using those IP addresses I was trying to use the same concept for sub domains. But thanks for letting me know this is a bad path to follow, I'm reading up on policy routing now.
-
BTW doing something like
54-240-196-102.amazon.com
54-240-196-172.amazon.com
54-240-196-221.amazon.comMake no sense, why would you resolve those? Do you think they would resolve to some different IP then what their fqdn is?
$ dig 54-240-196-102.amazon.com +short
54.240.196.102So why resolve it at all, just use the IP.. And those all going to fall into a network, so why would not just route the /network vs the specific IP?
Also when trying to do what your doing you would just use the ASNs which would contain all the networks and create an alias with those, etc.. pfblocker can do that for you automatically.
The simple solution would be to just say your roku/tv/firestick is on IP 192.168.1.42, just create a policy route above where you force traffic out your vpn, to say that source IP just goes out your wan.. There you go netflix works, amazon prime works, hulu works, etc. etc. etc..
-
Haha thanks for the very useful information! I'm still pretty new to all of this. I'm going to look into pfblocker now. Thanks!!!
The problem with your last suggestion is that the same computers that I use for streaming I also use for other activities. I have stuff like firestick but I thought it would just be simpler to go this route (guess not).
-
So I see how to enter a domain into the whitelist but how do I route the traffic meant for the VPN to WAN if it hits one of these domains? This appears to just allow the traffic on the vpn.
-
With a policy route to the alias.
Something like this.
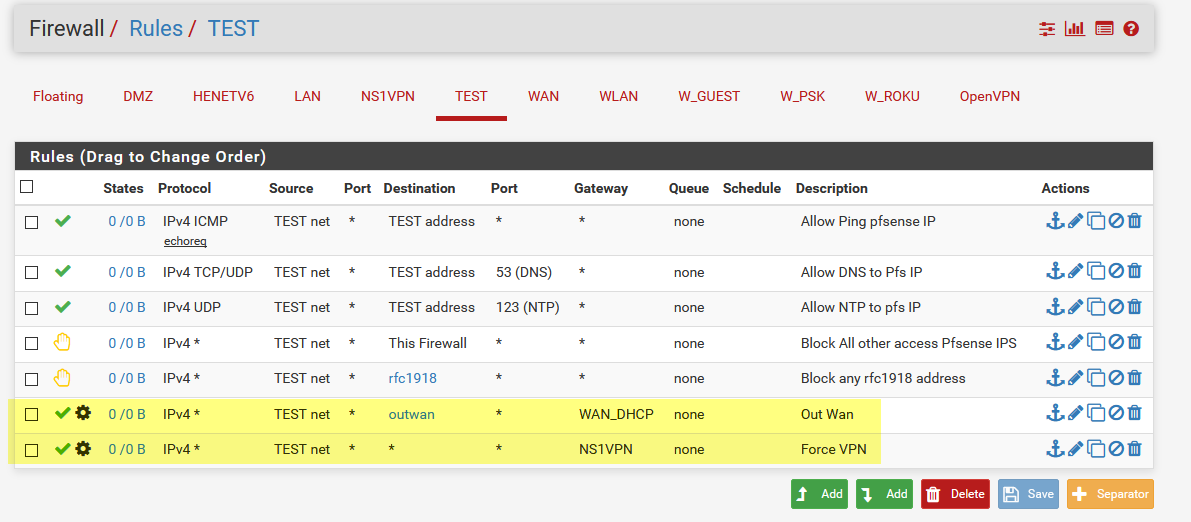
Anything with dest to what is in alias goes out wan..
Anything that is not to that alias would hit the last allow rule and go out the vpn.
-
thanks!
-
When you setup your vpn service, make sure you do not allow it to grab/set routes or it will set your default route to out the vpn..
-
I did as you said but the traffic is not being routed to wan. Is this where the static route stuff comes in? I thought I was supposed to avoid that? How is what the guys instructions were not policy routing?
-
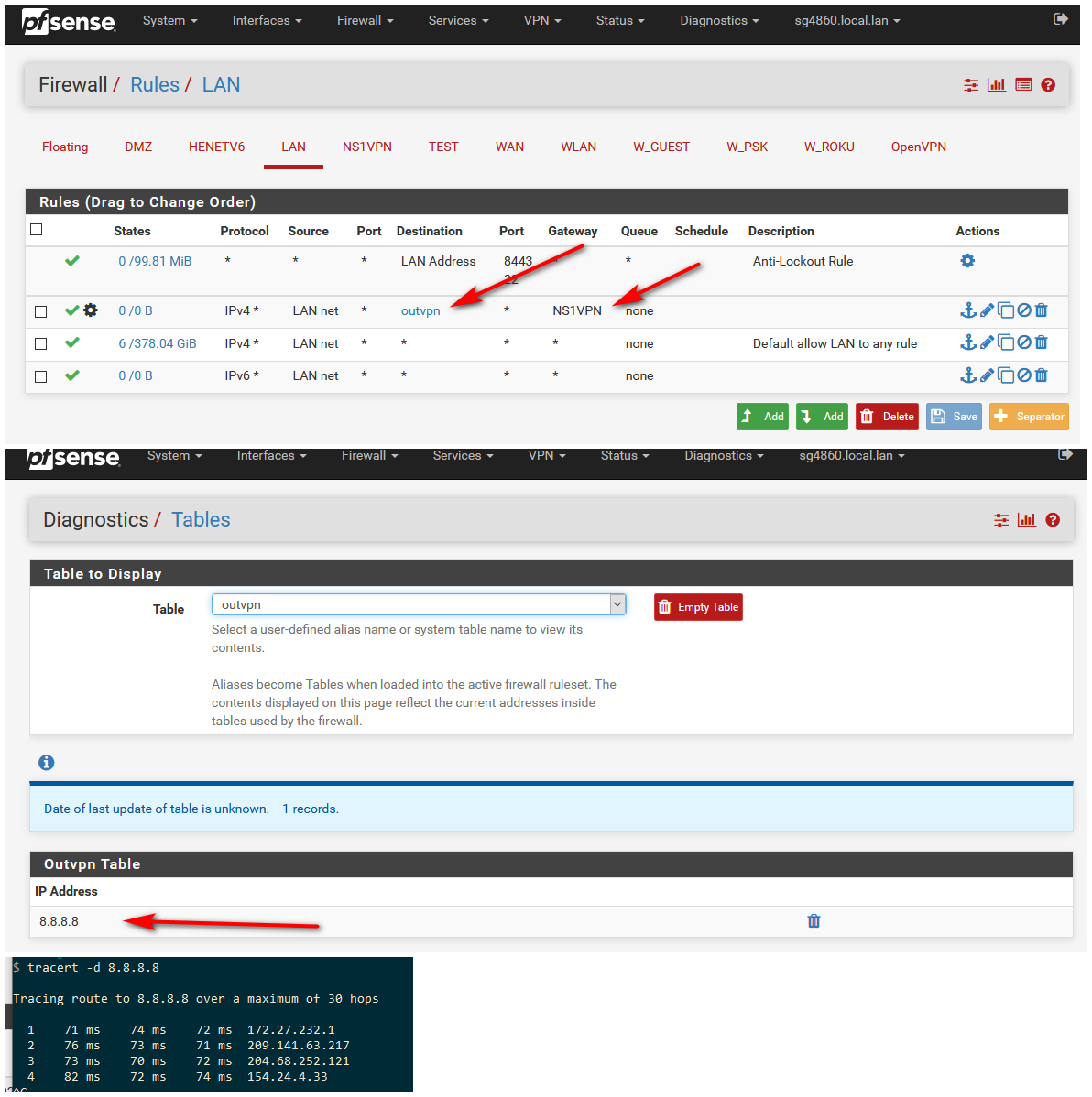
Does your alias actually populate? Lets see your rules.
Do a traceroute for some IP that is in your alias.
edit: Here I just forced traffic going to 8.8.8.8 out a vpn..
Here is normal
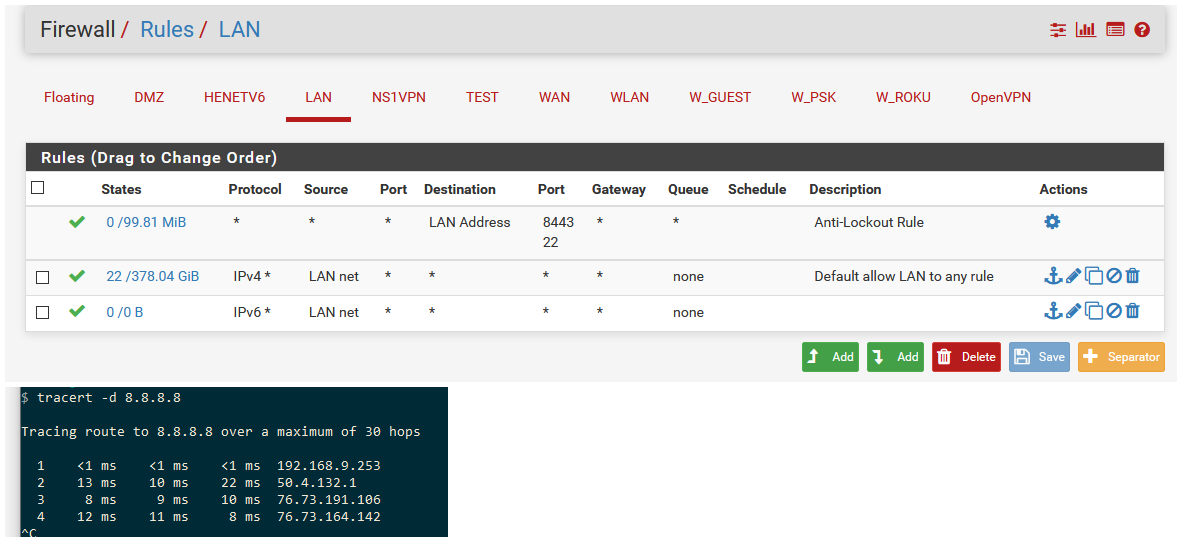
Did you setup your outbound nat? Did you change your vpn to not be default, ie don't pull routes or let it set routes?
keep in mind if you had existing states they would have to be flushed..