Simple VLAN setup
-
Help,
I have been struggling with adding VLANs to my home network. All I want to do is have what I think is the appropriate use for virtual lans and that is to have several separate IP subnets on the same wire/transport. My primary objective is to have a separate network for a home lab.
My setup is as follows:
COMCAST cable modem <-> pfSense (Intel i3 with 4 Gig ethernet)
WAN - (COMCAST DHCP) Netif- igb0
LAN - 192.168.0.1/24 Netif - igb1
ADMIN (VLAN 1) - 192.168.1.1/24 Netif- igb1.1
PRIVATE (VLAN 10) - 192.168.10.1/24 Netif- igb1.10
LAB (VLAN 20) - 192.168.20.1/24 Netif- igb1.20 (inactive until PRIVATE works!)The ADMIN network is use to manage the switch (I plan on adding additional managed switches once I get the main switch working) BTW the switch is a Netgear GS116Ev2 with port #16 marked as T and the others marked as U w/tag 10. Port #16 is connected to the pfSense igb1.
I have any/any rules for PRIVATE <-> LAN; WAN <-> LAN; WAN<-> PRIVATE but this kinda scares me but I need to get it to work first and then as I learn I will hopefully tighten thing down.
My big problem is the port forwards are not working. They did before I added the VLANs and I had problems before I discovered NAT reflection. I run an personal web/email server so I have a dozen or so ports that need to be forwarded to my server.
A novice guide would be nice, a best practice guide or just some friendly advice would be greatly appreciated.
Thanks.
-
@johntucker said in Simple VLAN setup:
ADMIN (VLAN 1) - 192.168.1.1/24 Netif- igb1.1
never ever use VLAN 1 !
it's the native vlan of almost all managed switch
it's best practice not to use vlan1
and probably the core of your problem -
Thanks,
The only reason I used VLAN 1 for the switch is Netgear recommends exactly that.
-
@kiokoman said in Simple VLAN setup:
never ever use VLAN 1 !
If he was in a corp setup, or a dod or something ok sure.. But in a home setup this is nothing wrong with using the default vlan..
But something is not right here, your lan is untagged I take it - so this would be vlan 1 on your switch.. Are you then trying to tag admin as vlan 1? That would be a nono..
Use a different ID for tagging your admin network.
-
of course it is wrong even at home, i was referring to the admin vlan1, the switch doesn't know if you are at home or in a corp. the native vlan of the switch is 1 ... if you don't change it

-
Oh yeah that is wrong... I thought you meant to not use it at all ;) For example I have default vlan set to 9 on my switches vs vlan 1 ;) But that is just so many years of not using the default vlan 1.
But in a home setup there is nothing wrong with using vlan 1 on your switch as the default vlan.. But no you can not also then tag some other vlan as 1 ;)
Depending on the level of "smart" they are using - it might not even support changing the default vlan.
-
Greetings,
Things are mostly working now, I guess that the sleep helped the firewall/router as much as I.
The issue now is that the server on the PRIVATE net can't ping its gateway. It can successfully ping the LAN gateway and other devices on the PRIVATE net but not 192.168.10.1.
This is nuts.
-
And what rules did you put on that interface?
-
Here are screen snaps of all of the rules:
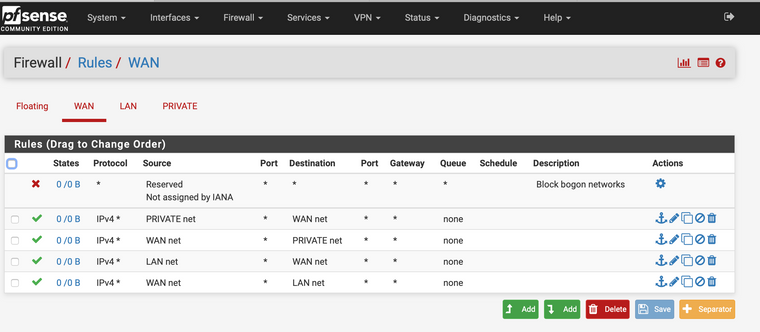
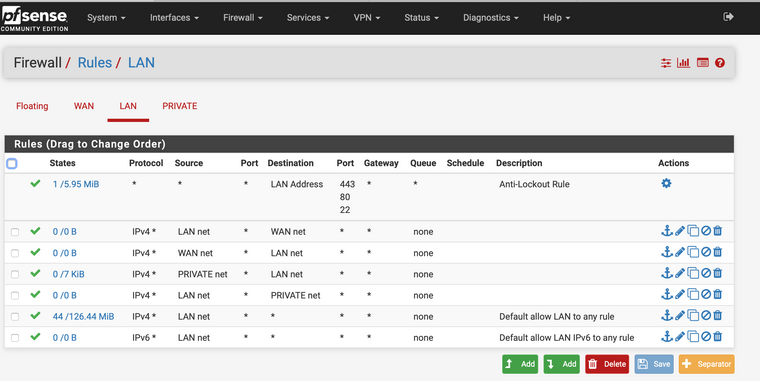
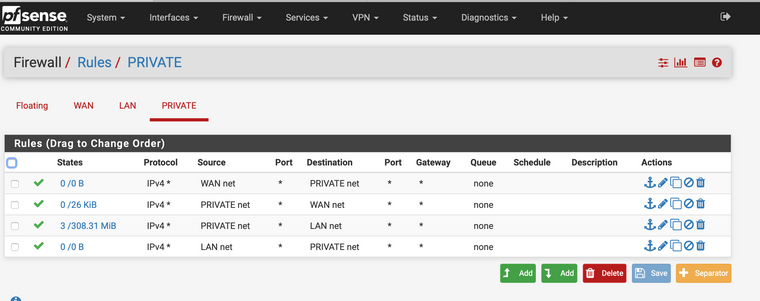
-
yeah those are ALL wrong ;) When would source lan net ever be inbound source to your wan?
I think you have a basic misunderstanding of how rules are evaluated.
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-processing-order.htmlWhere in your rules do you allow private net to ping say private address (pfsense IP on private net)
I would suggest you read how rules are evaluated, and if you have any questions ask... But you would never have wan net as source of traffic inbound to private net..
Rules are evaluated as traffic enters the interface from the network its attached too.. First rule to trigger wins, no other rules are evaluated. So its just plain impossible that wan net source would ever be inbound into private interface.
Also just so clear - wan net is NOT internet, wan net is just that - the network attached to wan.
edit: here an example of a setup for say a vlan that is restricted to only internet
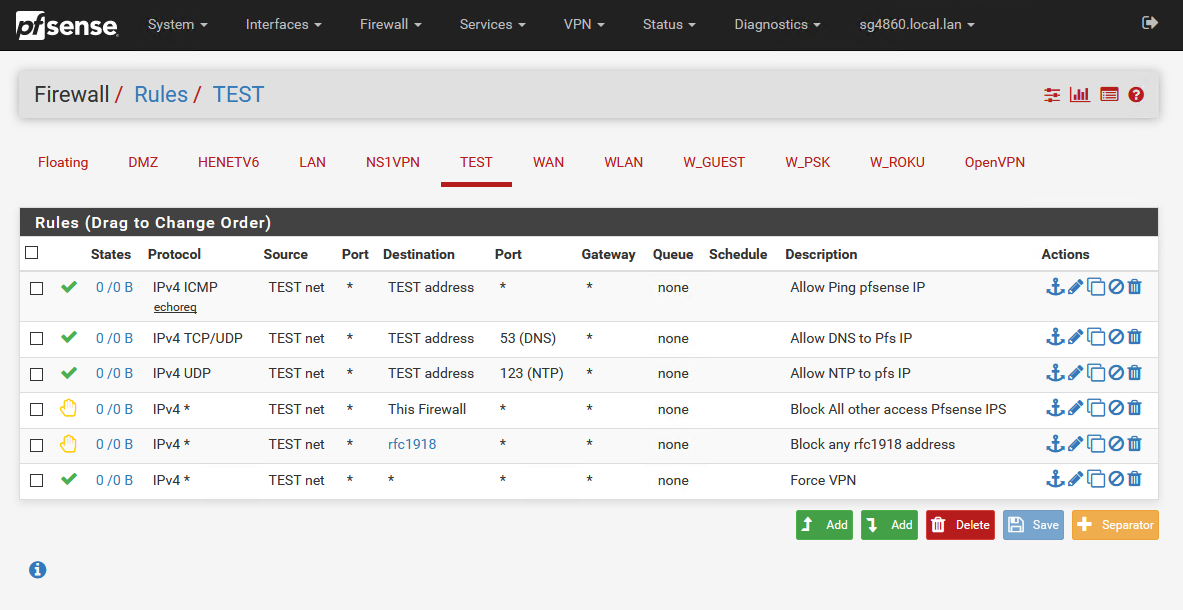
First rule allow test network to ping pfsense IP in test network.
2nd rule allows test net to use pfsense IP for dns
3rd rule allows test net to use pfsense for NTP
4th rule blocks all access to any IP of pfsense.. Wan, test, lan, etc..
5th rule blocks all access to any other vlans/networks that are local... The alias contains the rfc1918 space (10/8,192.168/16,172.16/12)
6th rule allow clients on test net to go anywhere else (internet) -
Thank you, Thank you!
Your example has informed me greatly. I now understand and that is a very good thing.
This is my first direct experience with firewalls (other than the frustration they cause at work) I have been around TCP/IP networks since around 1985 and this is the first time that I have run across problems ping'ing within a subnet. I guess that is due to my avoidance of Microsoft Windows and using only MacOS, Unix & Linux with their rare use of internal/device firewalls. I assumed to much!
Again, I appreciate the time you have taken to provide this example and I have learned a lot from it.
adios,
jt -
What we are here for - any other questions just ask..
When you have your rules adjusted - post them and we can discuss.