Had my pfSense been compromised?
-
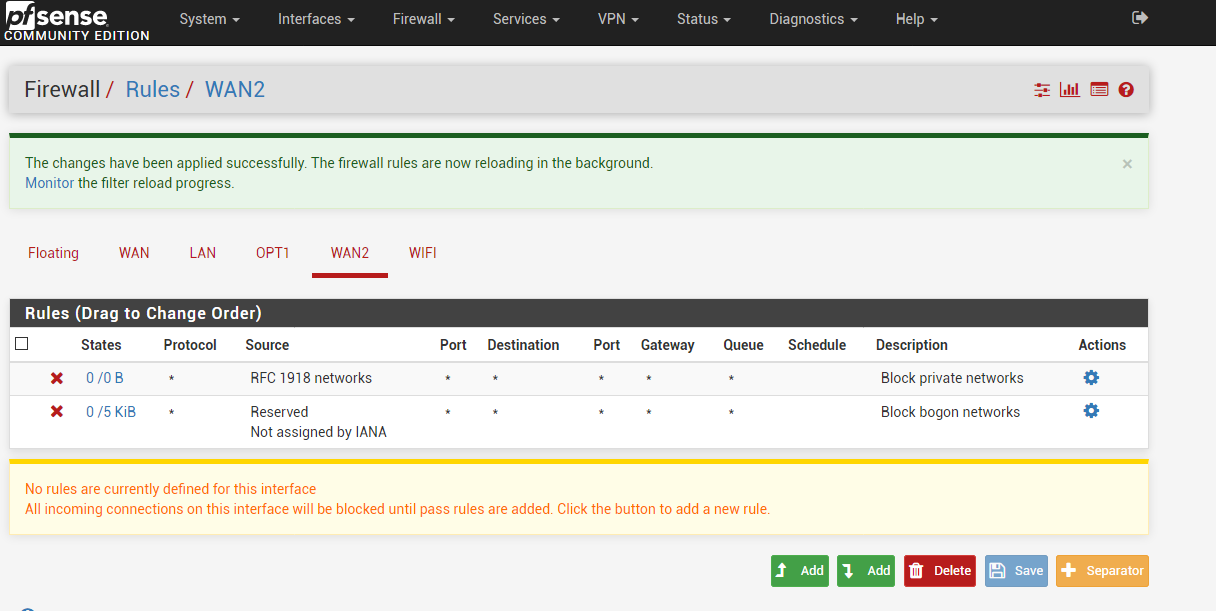
This is my first time to post here. I had been running pfSense for half a year so far so good. I have 2 WANs where WAN2 is dedicated for outgoing traffic only. I haven't set up any ACCEPT rules for WAN2 and I got the warning that all incoming traffics will be blocked. This is what I wanted. Remote SSH logon is protected by RSA private key. My admin web portal was assigned to port 3080 and I open only port 80 and 443 in NAT.
However today when I looked at the system log I found the following:
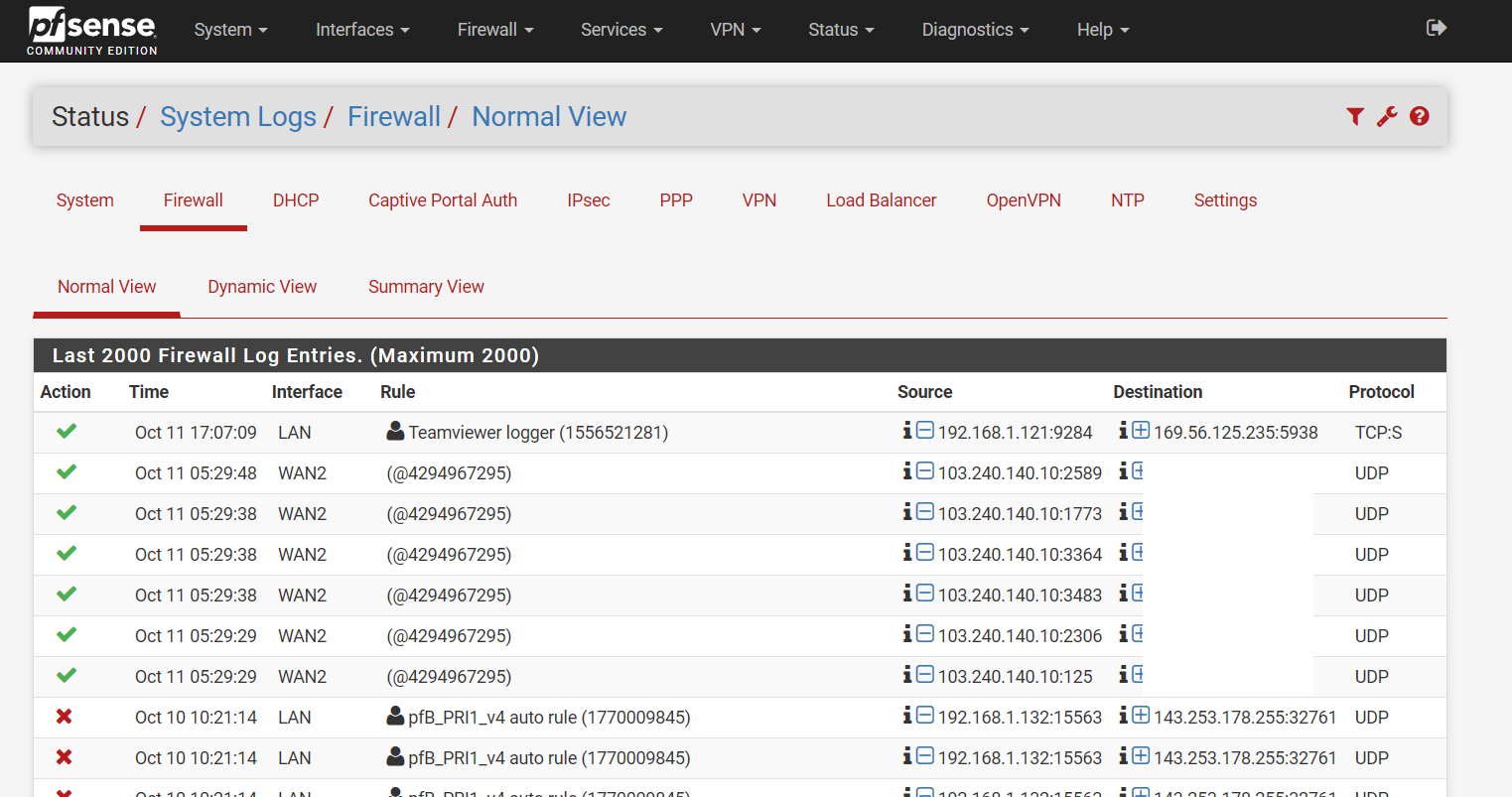
It looks like that there were incoming UDP traffic to WAN2 and were accepted (the green tick).
It seems to me that someone managed to create temp rules and got some kind of connections.
Are there anything I should be worrying about? Are there anything I can further check? -
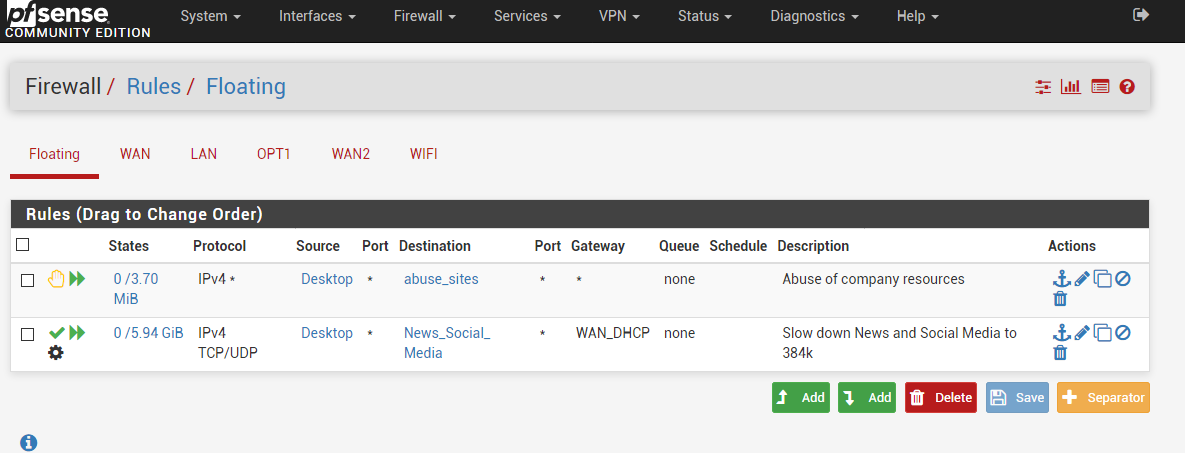
Post a pic of your WAN2 rules and your floating rules.
-
Thanks in advance for your assistances.
-
You've posted the same screenshot twice
-
@NogBadTheBad Thank u for pointing out. Pic corrected.
-
Nothing is coming in on WAN2, you have no pass rules there.
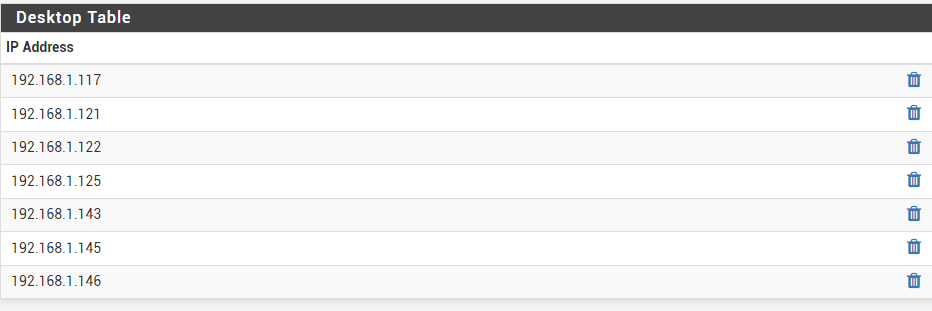
What have you defined for that "Desktop" alias you've got in your Source column on the Floating Rules tab?
Jeff
-
@akuma1x
Desktop contains list of desktop computers:
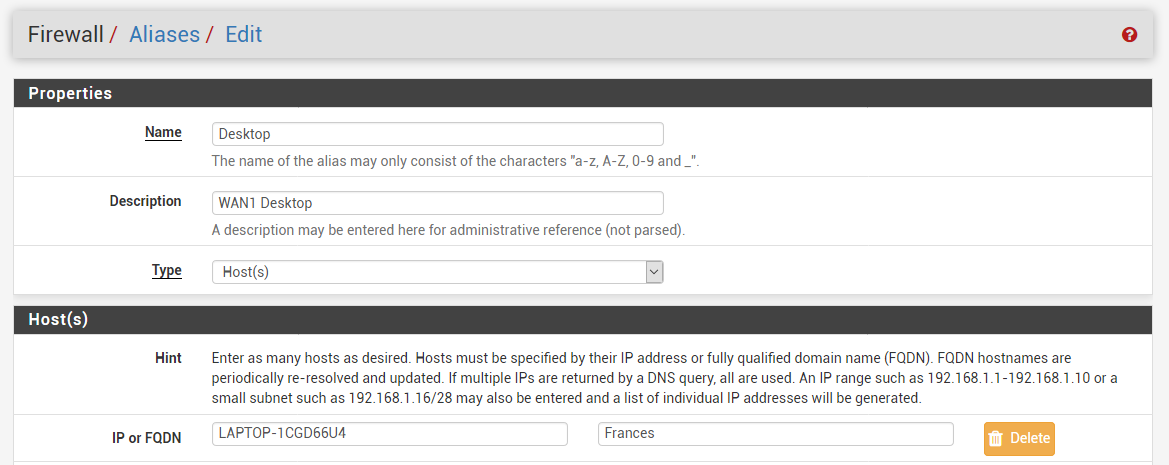
For sure it does not have the offending 103.240.140.10 in my first post.
-
And what is that rule - just look it up via
https://docs.netgate.com/pfsense/en/latest/firewall/viewing-the-full-pf-ruleset.htmlpfctl -vvsr
Will show you rule ID numbers so you can match up rules with what your seeing.. Unless the rule has been deleted.. You can look in your config change history.
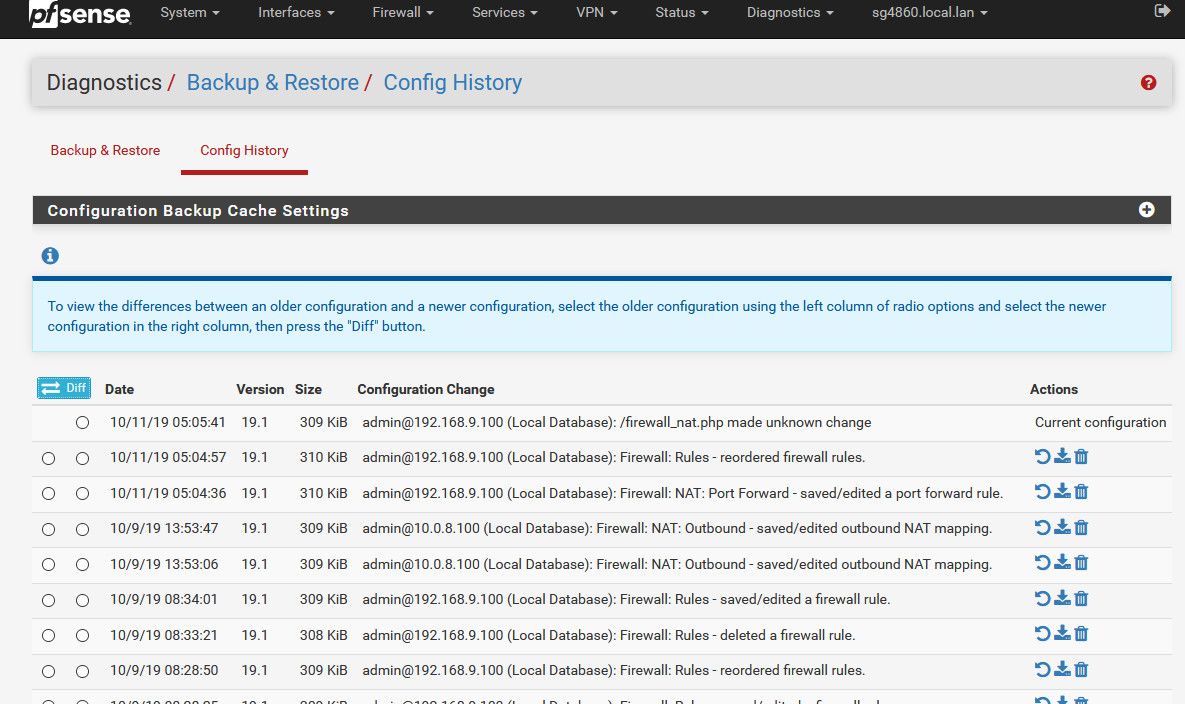
-
I have gathered additional info on the port numbers:
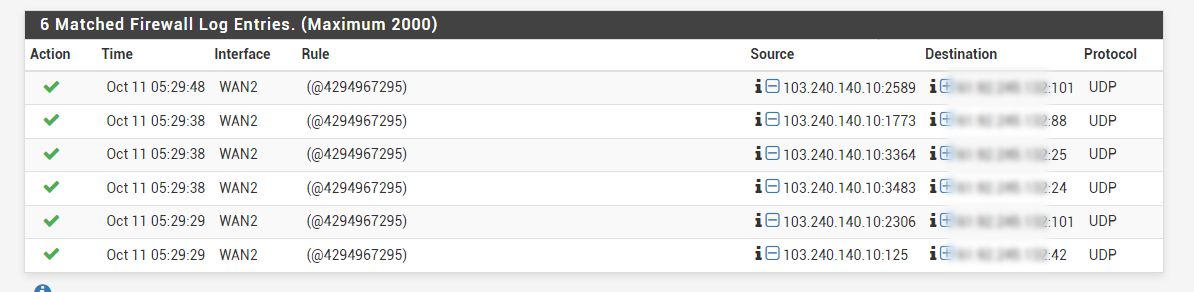
These ports seem to be related to hostname, nameserver, smtp.
-
@bchan said in Had my pfSense been compromised?:
For sure it does not have the offending 103.240.140.10 in my first post.
Yes but it has your local FQDN. You sure that resolves correctly and not to some strange web IP? I'd never use local hostnames in Aliases.
-
@johnpoz
Nothing logged around that time (05:29):
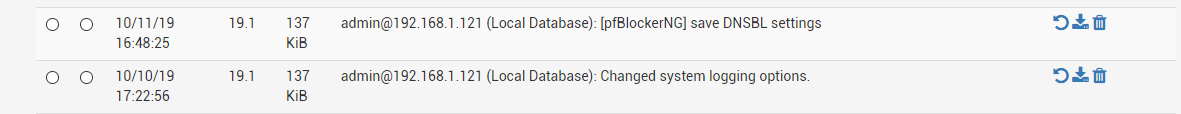
-
look in your full rule set for what that ID number matches up with.
-
whois 103.240.140.10
inetnum: 103.240.140.1 - 103.240.142.255
netname: CTCL-HK
descr: ClearDDoS Technologies
country: HKIt sounds like a web security company.
-
I'm talking about your alias. Not the IP.
-
I have checked the table values for this alias and they all resolve correctly to 192.168.x.x
-
@bchan said in Had my pfSense been compromised?:
all resolve correctly to 192.168.x.x
LAPTOP-1CGD66U4 resolves to 192.168.x.x? Even on pfsense itself? Its resolvers?
-
-
@johnpoz said in Had my pfSense been compromised?:
pfctl -vvsr
pfctl -vvsr | grep 4294967295
return nothing. -
Then the rule was deleted, make sure your grep is working by using a ID in your command that you see when just looking at the output.
Are you currently seeing logs for this?
-
@johnpoz said in Had my pfSense been compromised?:
Then the rule was deleted, make sure your grep is working by using a ID in your command that you see when just looking at the output.
Are you currently seeing logs for this?
grep works for other id e.g. the teamviewer logger.
I have 2 WANs for months. This incident was the first time I saw incoming traffic to WAN2 and were logged.
As you can see from my rules, I don't have anything that will log incoming traffic for WAN2.