What is best practice for my scenario
-
Thank you for your answers. @JeGr @riahc3 @stephenw10
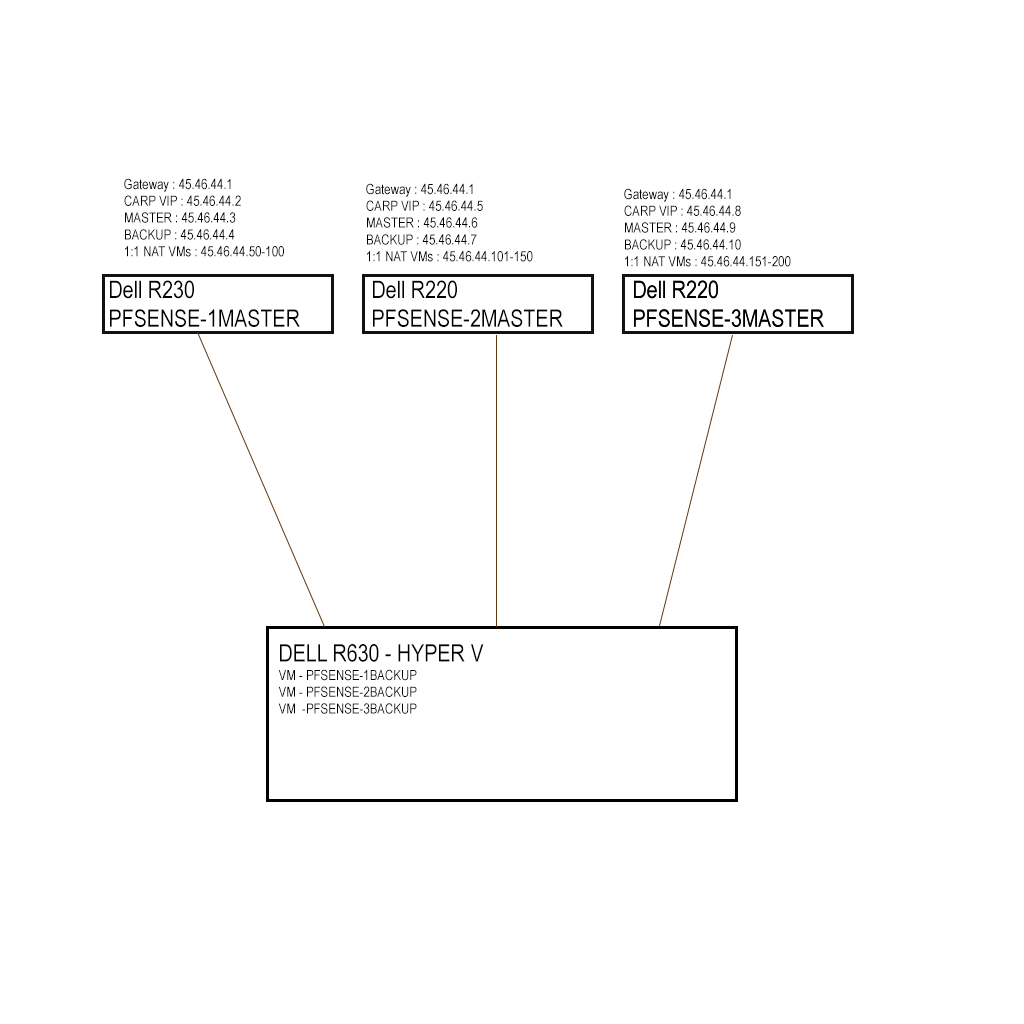
Budget is a issue, so I go with pfsense. My future plan is using 2-3 pfsense on cheap hardware and split traffic to them. I will setup backup servers as a vm so they will share resource and in case of fail over they scale up dynamically. Now I'm testing my setup I have problems with HA. When I enable HA WAN traffic lost connection during long downloads and on fail over downloads interrupted. I'm investigating issue right now.Thank you
-
hardware in an HA pair should be identical. Having a physical primary and a VM secondary is only going to be grief for you and will likely never work as well as a matching pair would.
-
Is your provider really not able to just route that subnet to you? That would be a much better setup.
What is your reasoning for splitting the subnet between 3 firewall pairs?
And, yeah, VM Secondary to a physical Primary is probably going to be painful.
Steve
-
@mrcha0s said in What is best practice for my scenario:
Thank you for your answers. @JeGr @riahc3 @stephenw10
Budget is a issue, so I go with pfsense. My future plan is using 2-3 pfsense on cheap hardware and split traffic to them. I will setup backup servers as a vm so they will share resource and in case of fail over they scale up dynamically. Now I'm testing my setup I have problems with HA. When I enable HA WAN traffic lost connection during long downloads and on fail over downloads interrupted. I'm investigating issue right now.Thank you
If you are setting up a data center and will use this in production, then you should gear your budget towards networking as it is the backbone of any infrastructure.
And pfSense is not a enterprise ready solution.
I highly suggest you consider this because when your network goes down and pfSense does not meet your RTO...
-
It seems like you've had some sort of bad experience here but I assure you there are many many people using pfSense successfully in exactly this sort of setup.
Not really sure what you're contributing at this point.
Steve
-
Ah it's Mr. Discord guy... again.
 Sorry have to do this:
Sorry have to do this:And pfSense is not a enterprise ready solution.
Yeah bullshit. There! I said it.

So back to topic: Again, yes it is. Otherwise we've been doing things wrong for the last 10y or so and I don't see that when I look into our network or customer ;) Indeed I've seen running pfsense in datacenter environments lots of times now. Not because of some BS reason or budget, but because it works and does a fine job when you have your facts straight and your requirements written out beforehand. But running pfSense on old hardware some time and then start bickering about "lack of CLI" or "automation" or "no API" or "speed (10G is not enough)" ... some users clearly didn't do a very good job at the planning stage (should've gone for TNSR in the first place in that example, but failed to see that).
But I also don't understand the intention between using 3 "old/bad/cheap" Hardware boxes to spread the load versus buying one set of cluster/carp ready good hardware and run your show with it. And if your budget is that low while trying to run a REAL network in a DC? Then shout down the line to your boss because the one thing you do not want failing if your business depends on it is your network backbone. If it goes down - how much is it going to cost per hour? per day? per week? Does that justify being a cheapskate when it comes to the integral parts of the network/security?
Don't understand those bosses these days. Everyone needs internet, cloud, datacenter, yet they still think that things come magically from some wireless fairy-tale thingy somewhere that doesn't need money, nor power, nor configuration. Just sparkles and sunshine...

-
-
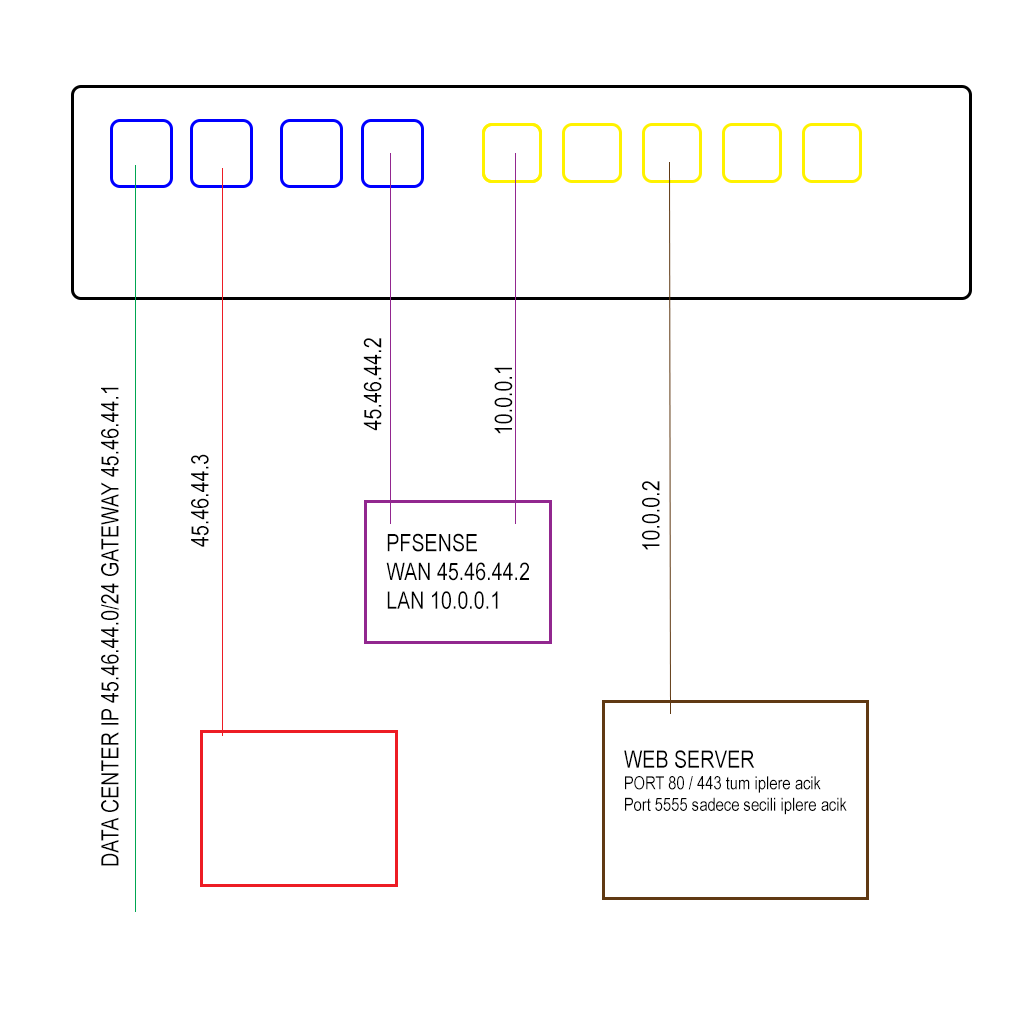
This is my experimental project. I have been using servers for more than 10 years but I always use vm, dedicated, cloud etc... 4 month ago I started to buy hardware and using colocation service. Last 2 months I'm researching firewalls and I see that fortigate, cisco asa, checkpoint, sophos are expensive for just packet filtering.
I dont want to use cisco,juniper, hpe products because I know they make discount %75-%90 if you are a whale. I will buy only two so I will get listing price.
Fortigate 100E ~3000 USD in Turkish market I need buy two for HA so its 6000 USD and in 5 years licenses will expire.
According to datasheet Fortigate 100E have 7.5Gbps firewall throughput. My aim is to get 7.5 Gbps firewall throughput with pfsense. Im using used Dell servers because they are cheap.
In my scenario I have two challenges;- Too many 1:1 NATs, its because architecture of my system. I will explain later with diagrams.
- Using virtual machines for HA slaves.
If cannot get expected results I will try Netgate hardware instead of buying fortigate, sophos, etc... Probably netgate hardware will cost me twice because of Turkish custom taxes and other delivery costs.
In a 2 week I will share my performance tests without firewall, with pfsense, cyberroam, juniper ssg and fortigate 100D
Thank you.
-
While we would love for you to buy Netgate hardware it is not absolutely necessary.
Two of the Dell 220s with the same setup for NICs, RAM, etc should work fine as an HA cluster.
Not sure about getting the throughput you are looking for from them though. When you start trying to get more traffic through the software it really matters more how many packets per second need to be forwarded, not the overall throughput.
-
@Derelict I'm not sure about netgate hardware but I want to try TNSR. I haven't review tnsr yet but if TNSR uses accelerator chip or different hardware than generic servers I can invest on it.
-
The main performance difference between TNSR software and pfSense software is that TNSR software utilizes Vector Packet Processing and DPDK so there is much less overhead in forwarding packets through the device. It is more of a software difference than hardware acceleration. Both leverage hardware acceleration such as AES-NI.
https://www.youtube.com/watch?v=nAY1SV74S88
-
@mrcha0s said in What is best practice for my scenario:
Too many 1:1 NATs, its because architecture of my system. I will explain later with diagrams.
Yes, that's going to get awkward quickly. Even if they charge you more it would be worth it to have your ISP toute the whole subnet to you so you can use the IPs directly IMO.
Steve
-
It is much easier to do it on subnet boundaries instead of human, decimal boundaries. such as a /26 of .64-.127 instead of .101-.150.
You can accomplish the former with a single 1:1 NAT entry. The latter would take several.
Routed subnets would be much better, but would put more reliance on upstream to get right.
-
@Derelict said in What is best practice for my scenario:
Thanks for the laugh!

And yes, as @Derelict and @stephenw10 already stated, try getting them to route your subnet via a transit network. Sometimes one has to be very stubborn and persistent about it, but it pays off with any kind of box behind it to be far easier configuration-wise.