IPsec nat issues
-
Hi,
first of all I'm sorry for my poor English...
I have problem with pfsense (2.4.4-p3) an IPsec NAT. I have an IPsec with my private cloud perfectly working:
Local LAN: 192.168.0.0/24
Remote LAN (cloud site): 192.168.5.0/24I have configured the phase 2 as shown in the followin screenshot (LAN_Cliente subnet = 192.168.0.0/24)
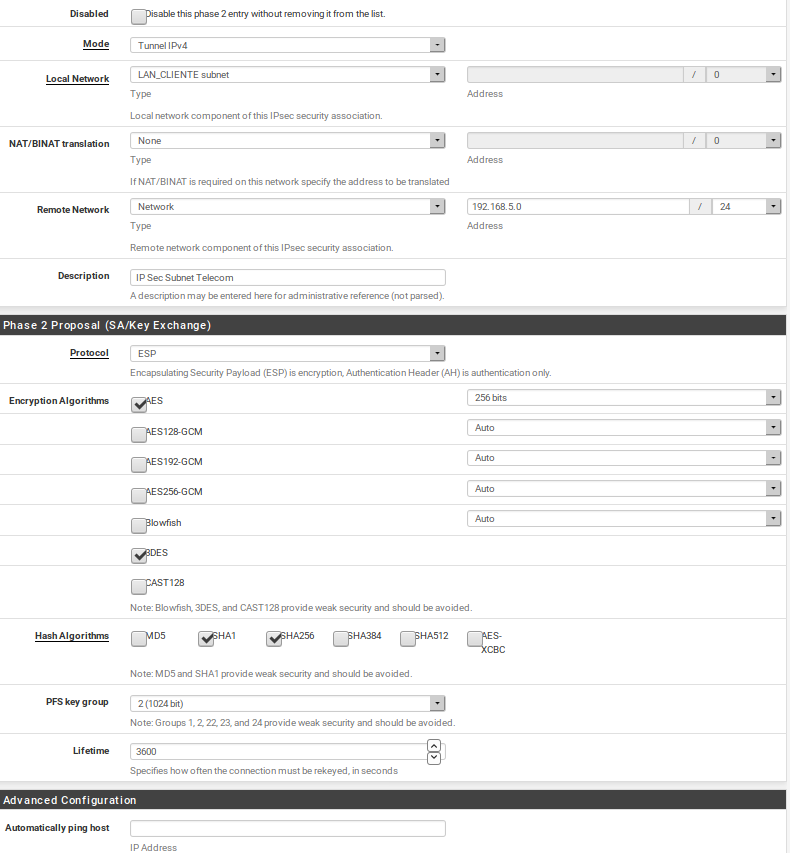
The hosts in local lan (192.168.0.0/24) can ping the host in remote lan (192.168.5.0/24) and vice versa.
Now I have configured a VPN for road warrion using OpenVPN and the IPv4 tunnel is 192.168.10.0/24. I cannot add a second IPsec VPN to my cloud, so I need to nat my OpenVPN IPv4 tunnel (192.168.10.0/24) with my local lan (192.168.0.0/24). To do that I added a second Phase 2 to my IPsec conf, whith the following conf:
Local Network: OPENVPN_ADMIN subnet (192.168.10.0/24)
NAT/BINAT Traslation: LAN_CLIENTE subnet (192.168.0.0/24)
Remote Network: Network 192.168.5.0/24
The rest of phase 2 conf is the same of the first phase 2. Then I click on save but if I return on this second phase 2 the field NAT/BINAT Traslation is set to none:
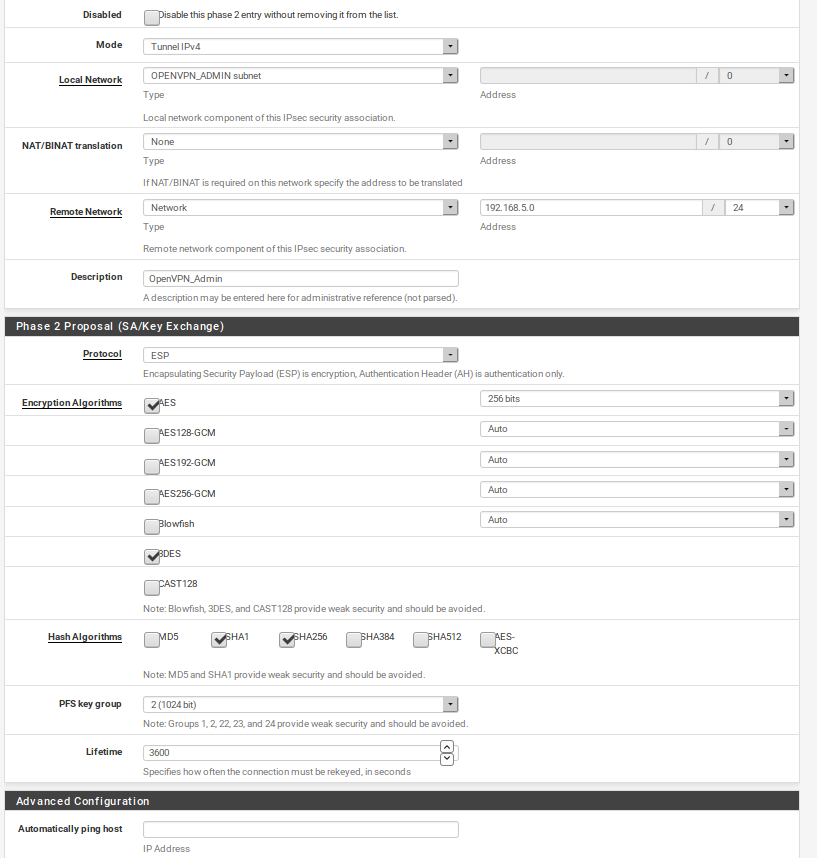
In few words pfsense doesn't save the field NAT/BINAT Traslation to the value LAN_CLIENTE subnet. Why?
I tried also to set manually NAT/BINAT Traslation to Network 192.168.10.0/24 and pfsense save correctly this configuration (if I return on this second phase 2 the field NAT/BINAT Traslation is set to Network192.168.10.0/24), but I cannot ping from my OpenVPN network (and also from the pfsense diagnostic tool selecting as source interface OPENVPN _ADMIN) the hosts in remote subnet (192.168.5.0/24). I did a traceroute and the packet stop soon, to the OpenVPN interface (192.168.10.1)For your information:
-
my outbound nat is set to manually
-
The firewall rule in IPsec pass everything...
-
the firewall rule in OpenVPN interface pass everything...
-
From my local network I can ping hosts connected via OpenVPN and vice versa...
Can someone help me please?
Thank you very much
-
-
@prx first of all your second phase2 is absolutely incorrect - you cross 2 different network. You can try 2 different cases (first one more good):
- Change OpenVPN subnet to be next subnet after your LAN like 192.168.1.0/24, and after it create only one Phase2 with 192.168.0.0/23
- Use BNAT to 1 /32 IP on LAN subnet and reserve this IP in DHCP for not existing static IP so nobody will use it really NEVER in your LAN. I doesn't sure if even this will fix because even this is network collision
And another question: why you configured 3DES and use 1024 bit key group - this is too low? It totally deprecated... This is due old gw on other side of ipsec?