Pesky flys buzzing around your head..
-
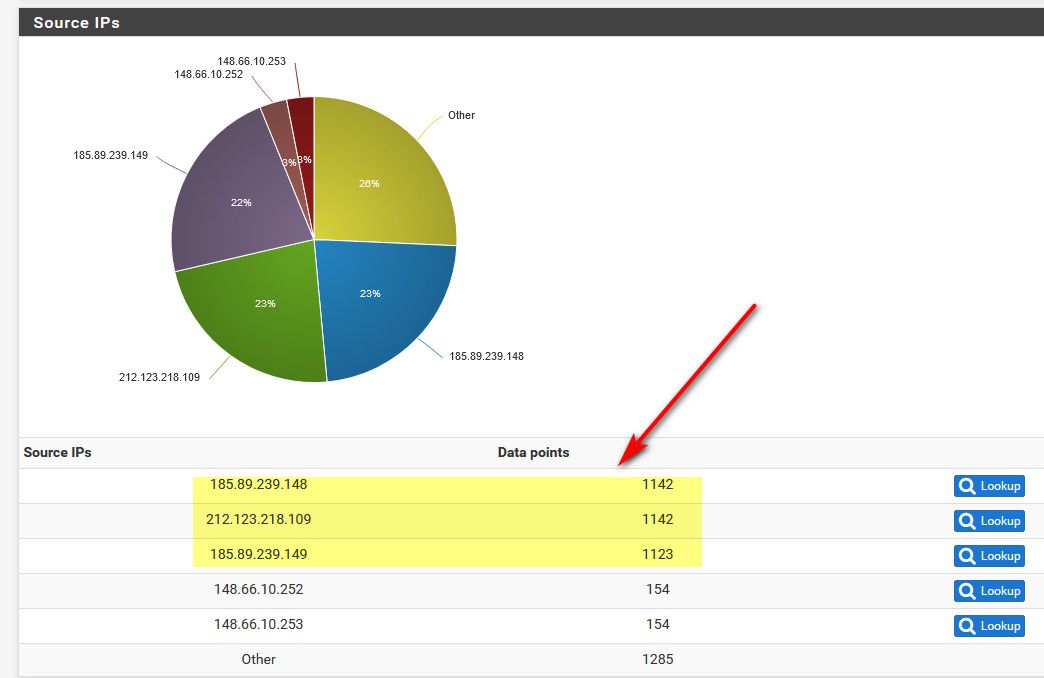
Yeah I got almost 100K hits yesterday between 443 and 8080.. 443 is what I had open so that could of put a hurt on my states... But 8080 has always just been dropped..
The only good thing come from this is it had my fire up syslog again for my firewall logs ;) So I could get some easy to access history..
Just honestly like to know what the hell they think they are doing.. Its got to be some serious amount of traffic they are pushing..
-
Probably pushing it from some compromised devices they aren't paying bandwidth for.
-
But what is the end game in such traffic? Clearly its not any sort of ddos - it pretty freaking lame for that.. What is the point of just banging your head.. At best its some sort of low level state exhaustion attempt..
What it amounts to is log spam..
-
The only time I start getting hit that hard is when I have server ports open.. Are you saying you do not?
I go over to my server logs and see all kinds of different styles of attacks happening.
Email log in attempts are a favorite by these guys... 5 a second for days on end sometimes.
-
anyway they are aware ...
you can try to use google translate on this
https://www.italiasera.it/eurobet-it-inaccessibile-i-nostri-sistemi-non-sono-al-momento-disponibili-si-teme-attacco-hacker/
hacker are asking for 80.000 $ of bitcoin -
Well so far today the flys are gone - and it back to more normal noise level
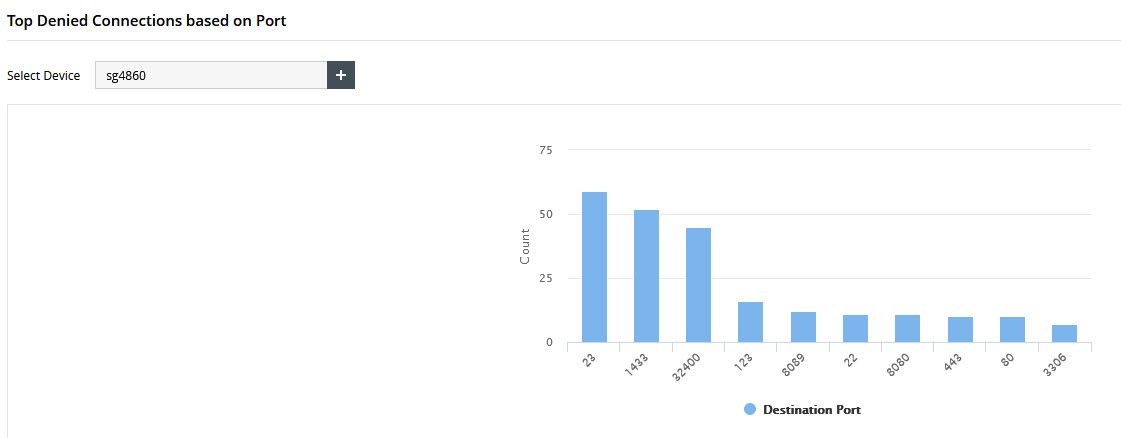
Yesterday was just banging head against 53.. atleast the 443 had stopped
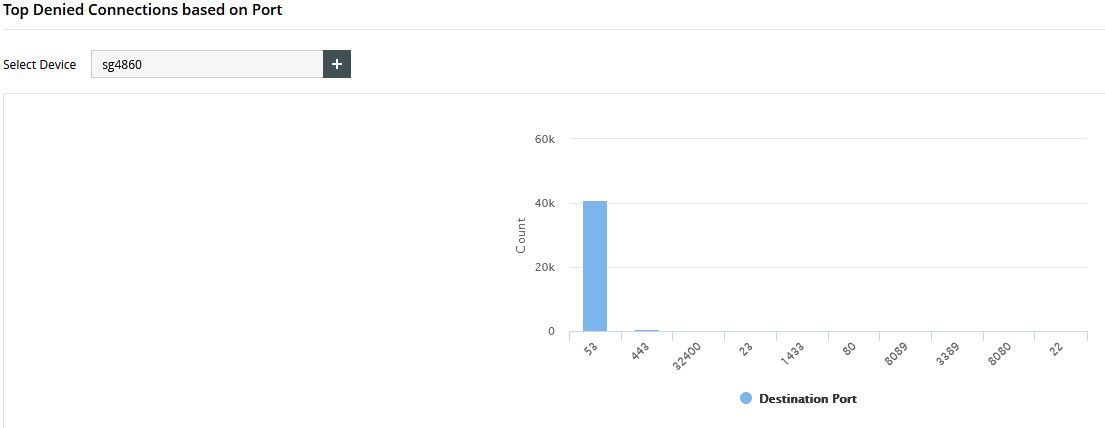
40k - and that wasn't even all day, syslog was off for a couple of hours.. And doesn't count the UDP noise (which I don't log - I might start logging common udp ports like 53, etc.) - I checked there was lots of udp hits to 53 as well.. All asking for roots. So prob atleast double that 40k number. Most of the time the udp was just all over the board and only few.. It was just cluttering up interesting info..
The only good thing from this - triggered my interest in running a syslog to keep track of hits over time.. Should prob fire up an elkstack again.. But running that on VMs is difficult currently since takes a bit of horse power.. And don't really have any hardware that can support currently without putting real hit on everything else the box is doing..
What would be slick, is something low requirement enough to just run on a pi.. And provide the eye candy dashboards you can get with elkstack (kibana).. Might have to look to see what kind of dashboard can setup for firewall hits, dest ports and such with Grafana setup.. Most of seen of those setups is more geared towards cpu, memory, io stats via graphs over time.. Vs details of the firewall hits by source IP, dest port, passed allowed, etc.
-
if you come up with something pls share as i have a spare pi myself, it would be a nice addon
-
Yeah for sure... You be up for a low requirement vm as well? What would be extra slick is a just a vm image anyone could just fire up and make very min changes to and be up and running.
-
52.192.154.0/24 multiple addresses from this range hitting my email server after hours tonight. Every port we have open.
Time for the fly swatter.
-
In the last 24 hours I've seen that whole subnet plus every single IP in:
52.192.157.0/24
112.175.120.0/24
112.175.124.0/24I'm only seeing these on port 25, as that's all that's open. Found a way to identify the packets, though. They now fall into a fail2ban trap and are blocked at pfSense.
EDIT: And last week it was the whole of 185.40.12.0/24, 185.40.13.0/24, 185.40.14.0/24 and 185.40.15.0/24.
185.40.12.0/22?