Non-TLS DNS Leaks when PFsense looks up host alias(es)
-
This post is deleted! -
Set the firewall to use the local DNS resolver and delete all of those.
With the new default gateway settings you should not need those multi-wan DNS servers any longer.
You will probably need to manually set forwarding using custom options though, thinking about it. I'll look at it but it might be tomorrow.
-
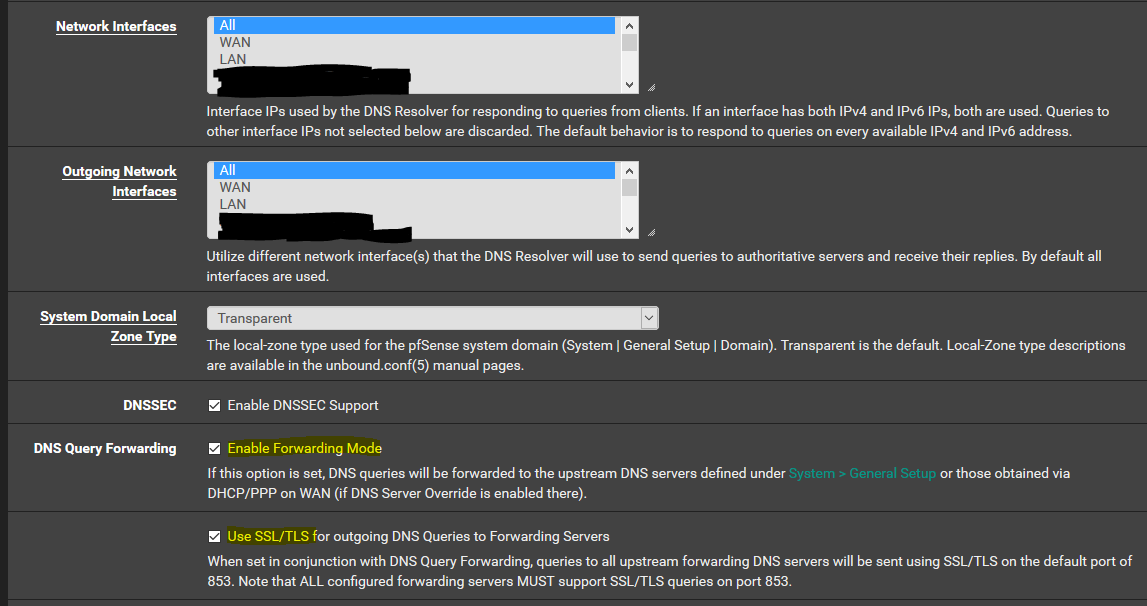
@Kirin Try this:
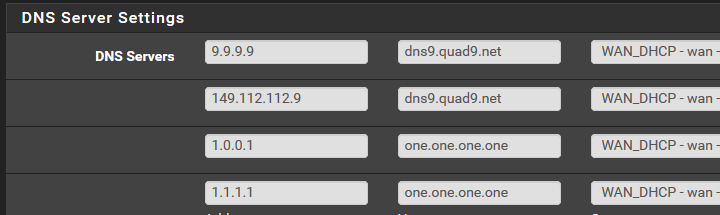
And this:
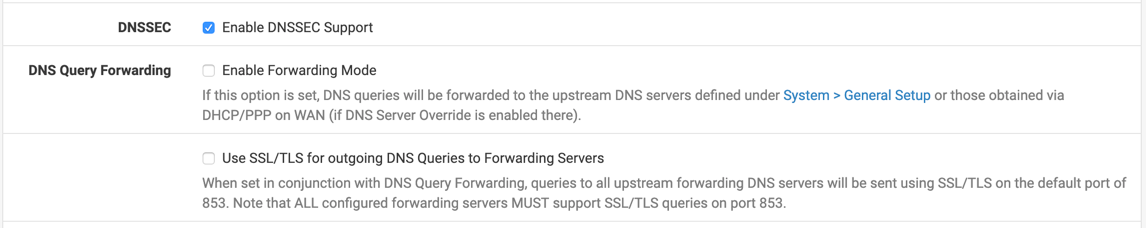
And this in custom options in the DNS resolver:
server: # Forwarding forward-zone: name: "." forward-tls-upstream: yes forward-addr: 9.9.9.9@853#dns9.quad9.net forward-addr: 149.112.112.9@853#dns9.quad9.net forward-addr: 1.0.0.1@853#one.one.one.one forward-addr: 1.1.1.1@853#one.one.one.one -
This post is deleted! -
You understand such a setup not good right... You are forwarding to 2 different types here quad 9 filters, while 1.1.1.1 does not.. This is a borked setup..
What do you want - filtering or not? Since you are not going to be sure which one gives you an answer.. So you may be filtered when you don't want to be, or not filtered when you want to be..
And now that is cached, and the next guy asking gets maybe the wrong sort of answer as well. You can not point to NS that resolve differently or you will have problems.. If your going to forward to multiple NS, they need to resolve the same way.. filtered or not filtered - you can not mix them without just having a mess.
Even picking 2 filtering providers is going to be problematic. Since you have different filtering lists, where site X might be filtered on 1, and not on the other... So sometimes it resolves, sometimes it doesn't.
-
Your dns tls hostname verification servers appear to be wrong for quad9,
dns.quad9.net
-
This post is deleted! -
@Kirin said in Non-TLS DNS Leaks when PFsense looks up host alias(es):
when you have a DNS server under General Setup it gets added to resolv.conf
Well Duh ;) Not sure why this was even a question then? No shit if you tell the OS to use NS X, that it could use NS X ;)
Why didn't you just ask that, how do I have unbound forward to NS that Pfsense will not use for its own use..
-
This post is deleted! -
It is also pretty useless to use DNSSEC when forwarding. Since you don't get signature information all the way from the roots, you are blindly trusting whatever the forwarding server gives you.