Impact of adding "ip route 0.0.0.0 0.0.0.0 192.168.0.1" to L3 switch downstream PFSense?
-
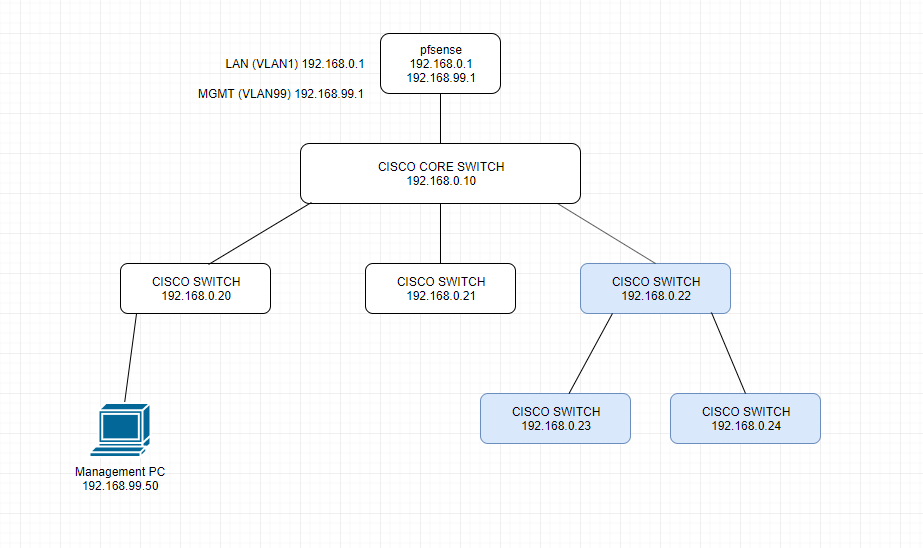
Currently we are using router-on-a-stick approach with PFsense.
PFSENSE connected to a CISCO "core" switch that is connected to serveral other switches.
We have a few VLAN's with pfsense routing between the VLANs.
Now I have chained a couple more switches below that main core and assigned a single IP to each of these switches interface for VLAN1.
I have a management VLAN99 where I can reach all other switches in VLAN1, but I am unable to reach the newly added switches unless I am in their (VLAN1) subnet.
So for some reason I am unable to reach 192.168.0.22 (switch) from 192.168.99.50 (management pc) unless on that cisco switch I set up route:
ip route 0.0.0.0 0.0.0.0 192.168.0.1
But I am wondering if there is a negative impact of this? I read a lot about NAT issues and not having routing downstream from pfsense. Is this considered that?
-
Not sure where there is any routing going on here in your switches... Your only showing single L3 network 192.168.0... With another vlan on pfsense 192.168.99... If your client is using pfsense as its default gateway, pfsense would know how to get to 192.168.0 since you show it directly attached... If your 192.168.0 was downstream of pfsense there would be a transit network connecting pfsense to this 192.168.0 network.
Are you switches actually in L3 mode, then why are they all on the same network?
As management of your switches from a different vlan - then yes the switches would need to talk to pfsense to know how to get to your 192.168.99 network... Looks to me all your switches are just in L2 mode, but if you want to manage them from another network they need a gateway.
-
The switches' management interfaces will obviously need to have a route back to 192.168.99.50 via 192.168.0.1.
If all you want is a route back to the management network, you could just use this:
ip route 192.168.99.0 255.255.255.0 192.168.0.1
or for just the mgmt workstation:
ip route 192.168.99.50 255.255.255.255 192.168.0.1
I would personally put the switch management interfaces on VLAN99 so the switch management interfaces were out-of-band from the user data.
-
Not sure where there is any routing going on here in your switches..
Correct, not trying to do any routing on any of the switches below pfsense. Just want to get inter-vlan/wan traffic up to Pfsense to decide what to do.
So that said I didn't get the results I was expecting adding any kind of route via ip route ...... on the Ciscos.
But...
ip default-gateway 192.168.0.1
seems to have fixed it :)
-
I would personally put the switch management interfaces on VLAN99 so the switch management interfaces were out-of-band from the user data.
Sorry... to clarify these are not our actual network/subnets, I just made a quick simple version to ask the question here. In our case no user-data on VLAN1 (I don't think so anyway!). All user data is in their own respective VLANs. VLAN1 is basically network operation VLAN and VLAN99 is for management PC's and a couple other things like that. VLAN99 can see into everything . All unused/not in use switch ports moved to VLAN666.
Anyway I guess since we're not really using the switches for routing (just trunking everything back up to pfsense) then I just needed to add ip default-gateway 192.168.0.1 and seems to work now.