how connect freeradius to MS AD
-
dear @free4
thanks for your answer
i tried your solution
here is my configuration
NAS server (work fine)
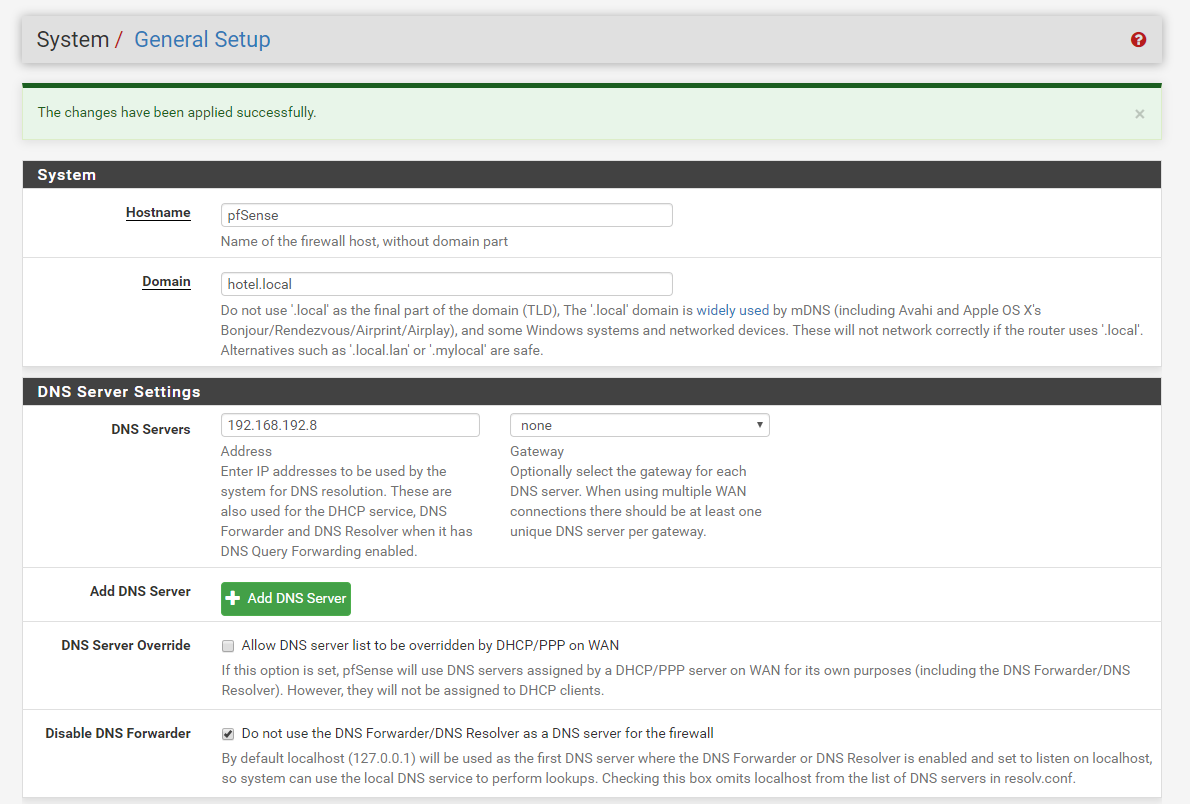
Pfsense DNS configuration (work fine)
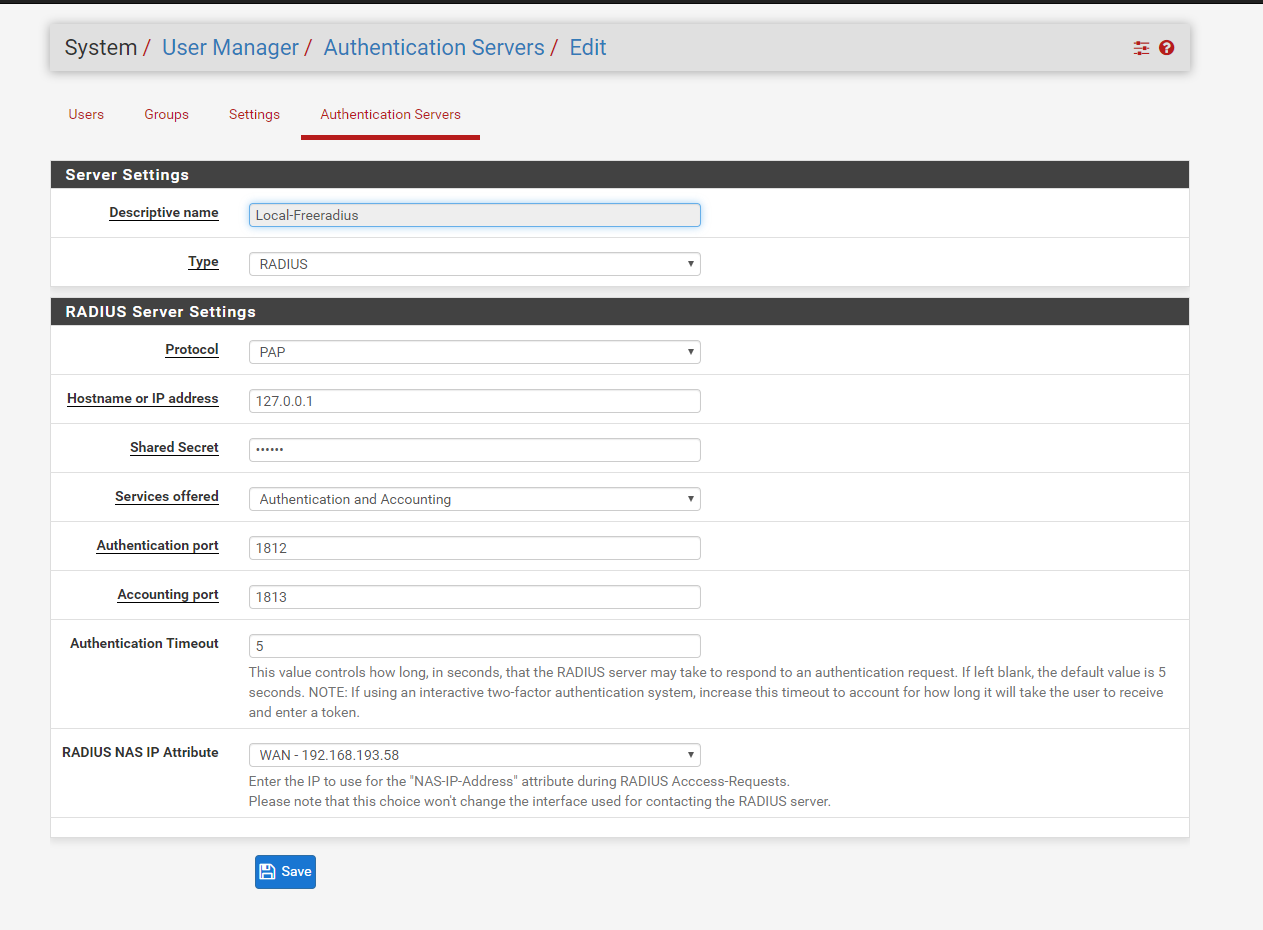
RADIUS config
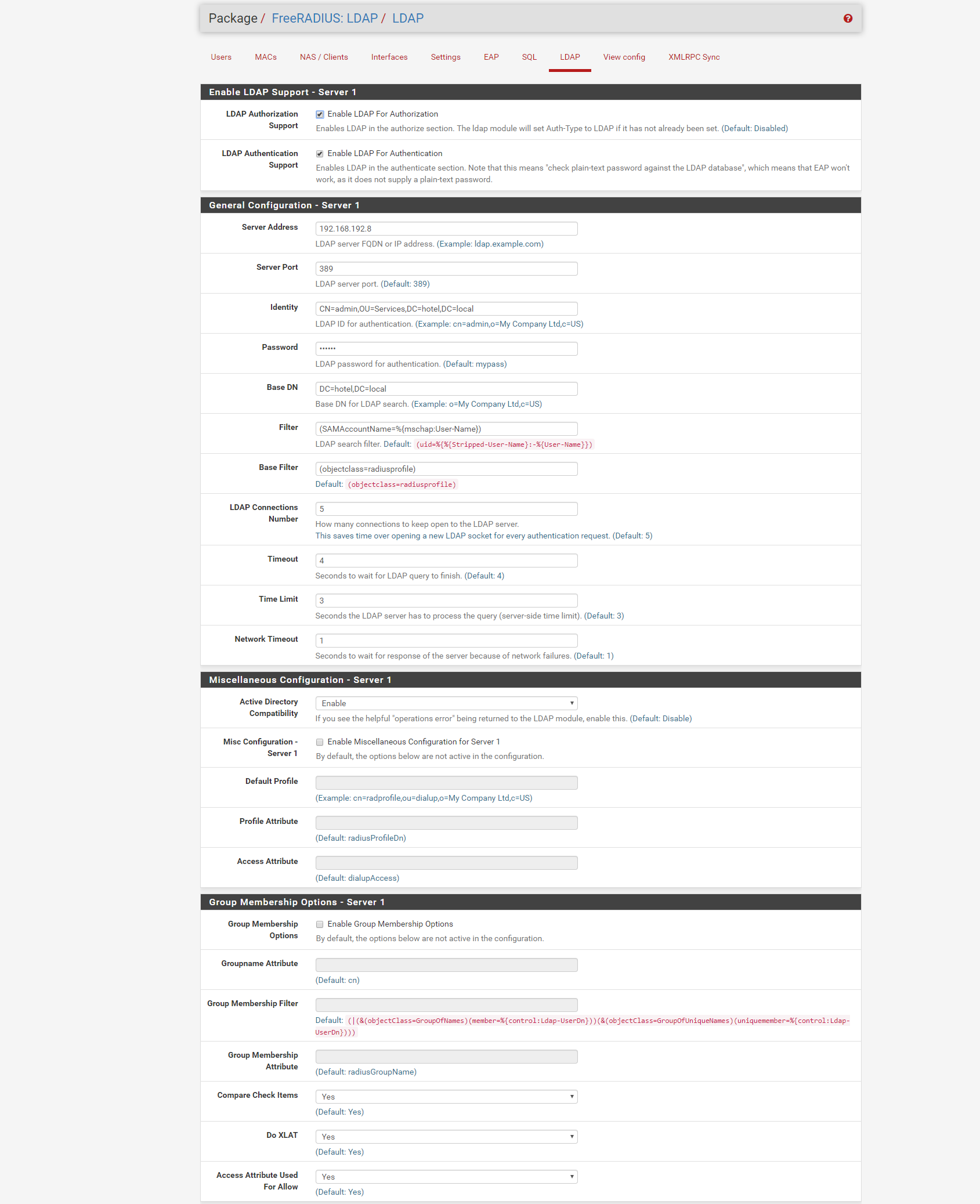
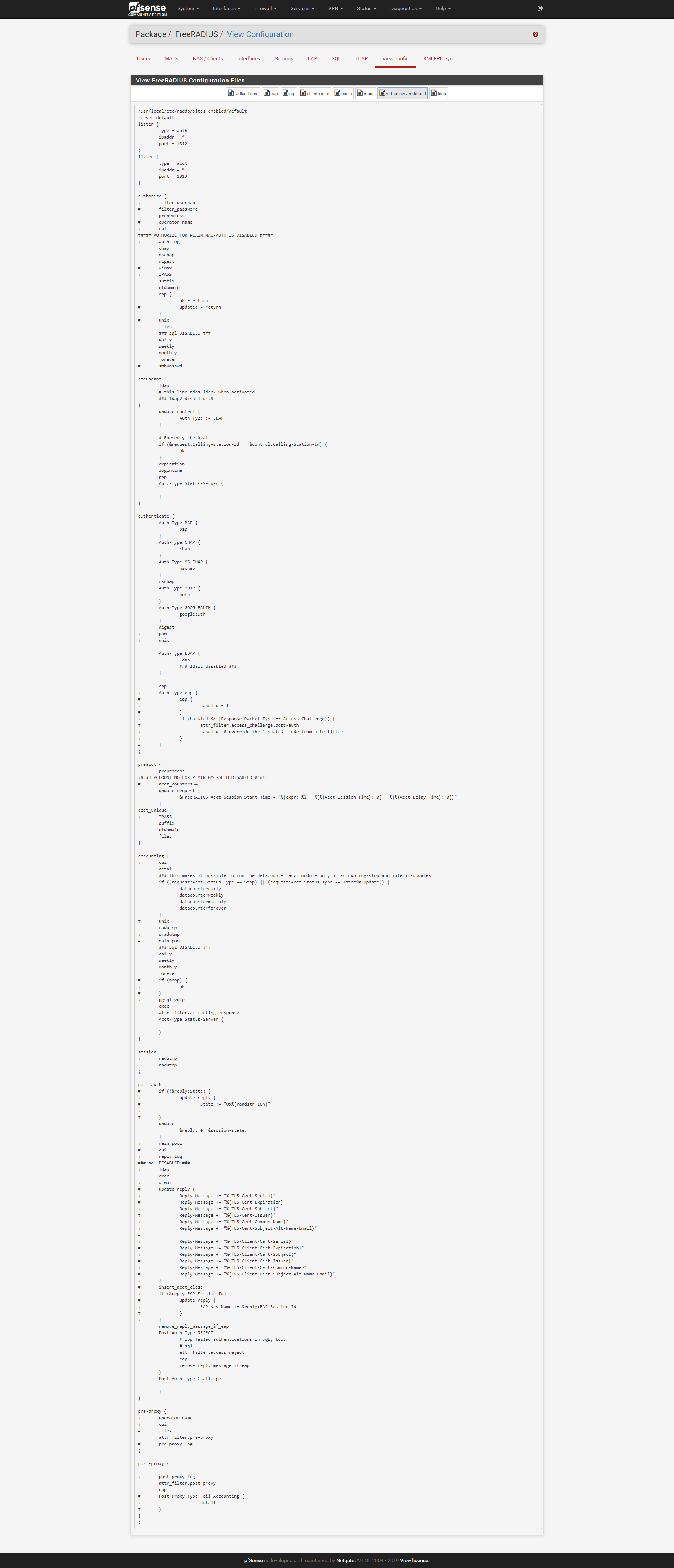
my virtual-server configuration
but my authentication test is failed
system log
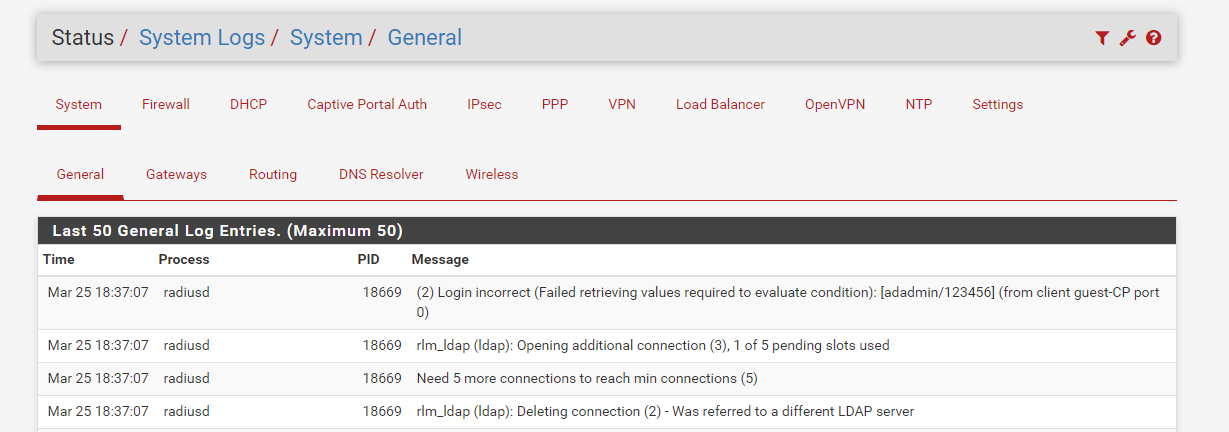
-
@free4 your explenation is great, thanks! You saved part of my time. I want to add litle trick to your comment:
my pfSense is use Unbound transparent resolver over TLS to Cloudflare, and Windows DNS can't do TLS stuff so their upstream is pfSense, and DNS resolvers for end-clients is AD controllers. I don't want remove this flow, so I simply add to my Unbound config:# Local resolving for AD domains local-zone: "subdomain1.active-directory.com" transparent private-domain: "subdomain1.active-directory.com" local-zone: "subdomain2.active-directory.com" transparent private-domain: "subdomain2.active-directory.com" # Forwarding forward-zone: name: "subdomain1.active-directory.com." forward-addr: 10.1.0.10 forward-addr: 10.1.0.20 forward-addr: 2001:xxxx:xxxx:1::10 forward-addr: 2001:xxxx:xxxx:1::20 forward-first: yes forward-no-cache: yes forward-zone: name: "subdomain2.active-directory.com." forward-addr: 10.1.0.30 forward-addr: 10.1.0.40 forward-addr: 2001:xxxx:xxxx:1::30 forward-addr: 2001:xxxx:xxxx:1::40 forward-first: yes forward-no-cache: yesAfter this pfSense can lookup to any AD
 record.
record. -
@free4 but still I can't authorize via FreeRADIUS.
- Plaintext LDAP over 389 is not secure and MUSN'T be used, but atleast it suceffully connect to dc1.subdomain1.active-directory.com. Still strange logs appiers:
Mar 29 12:53:29 radiusd 13316 (0) Login incorrect (Failed retrieving values required to evaluate condition): [someuser] (from client pfsense port 0) someuser Mar 29 12:53:29 radiusd 13316 rlm_ldap (ldap): Opening additional connection (1), 1 of 1 pending slots used Mar 29 12:53:29 radiusd 13316 Need 1 more connections to reach min connections (1) Mar 29 12:53:29 radiusd 13316 rlm_ldap (ldap): Deleting connection (0) - Was referred to a different LDAP server Mar 29 12:53:29 radiusd 13316 rlm_ldap (ldap): Opening additional connection (0), 1 of 1 pending slots usedDeleting connection (0) - Was referred to a different LDAP server is really strange one.
Another case is: filter issues? What is correct filter ro MS AD? I saw many examples but still all diferent. My current config:
Filter: (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})
Base Filter: (objectClass=*)- For my configuration LDAPS dosn't works.
Root and Intermidiate CA with DC Certs in pfSense Cert Manager. I genereted CSR on DCs and signed them by Intermidiate CA on pfSensne after witch imported them to DCs. Create GPO to put Root CA to Trusted, and Intermidiate CA to Intermidiate CAs store. All DCs trust each-other fine.
But in SystemLogs:
rlm_ldap (ldap): Bind with CN=some-user,CN=Users,DC=subdomain1,DC=active-directory,DC=com to ldap://dc1.subdomain1.active-directory.com:636 failed: Can't contact LDAP serverWhere to look why it doesn't work?
I already checked:- telnet to dc1.subdomain1.active-directory.com:636 from pfSense works;
- dc1.subdomain1.active-directory.com is work with correct SSL certificate. Tested from my PC via LDAP utility.
Tried FreeRADIUS LDAP config many combinations:
- SSL CA Certificate: none (auto) or choose Root CA or choose Intermidiate CA
- SSL Server Certificate: none (auto) or choose DC1 Server CA
- Choose Certificate Verification Method: tried all of them.
I gived up, and begin use Windows Radius over pfSense FreeRADIUS

P.S.
@soheil-amiri have same issue in SystemLog: Deleting connection (0) - Was referred to a different LDAP server
The only info on Inet about this is https://github.com/FreeRADIUS/freeradius-server/issues/1969
But I can't understand how them can be referred to a different LDAP server, and how do I figure out what this server is? -
great explanation.. when i start to setup captive portal/radius i not found any solution like described here... them i configured my enviroment adding a radius server role on domain controller to setup.. and today is working well .. for example making filted setting calback option adding MAC Adress autorize to connect to the user setting on AD..
but is good to know maybe in near future i wiil make my setup like described here
thanks -
@luisenrique pfsense support Microsoft AD authentication for captive portal for out of the box, why would you need a radius server?
-
@free4 for my radius needed to authorize of WPA ESK. And pfSense authorization for MS AD is poor on second dc controller. Only one option for second controller create additional "connection". Most people who care about safety have 2 DC in domain, or maybe even more. When freeRadius have load-balacer with failover, except it not working

-
hi @free4
do you have any idea about this error ?Login incorrect ( failed retrieving values required to evaluate condition )it would so nice to solve this issue.
-
EDIT: turns out i missed an important part of the logs - the is actually freeradius thinks my user's password is incorrect ("if (ok && User-Password) -> FALSE"), so the "Auth-Type := LDAP" is actually ignored correctly. but now the question is, what's different in the live setup via CISCO WLC 2504, in comparison to running radtest, which authenticates just fine :/
*has this been resolved?
I put together bits and pieces from various forums, and kinda got this working, but, the only way to get an LDAP user authenticated, is to run
"radtest <user> <pass> 127.0.0.1 1812 <secret>"
which returns Access-Acceptif I try to login to a real WLAN (cisco WLC 2504) hooked up to the same freeradius, the user gets Authenticated, but not Authorized - according to logs
"ERROR: No Auth-Type found: rejecting the user via Post-Auth-Type = Reject
(3) Failed to authenticate the user"a "Auth-Type := LDAP" is configured in case of successfull authentication, which is correctly respected when testing locally with radtest (see above), however, the live test receives "Access-Rejected" with the error message listed above.*
-
This post is deleted! -
try this:
vi /usr/local/etc/raddb/sites-enabled/default
add following in
authorize {}block, restart freeradiusif (!control:Auth-Type) { ldap if (ok && User-Password) { update { control:Auth-Type := LDAP } } } expiration logintimeAuth server under System - User Manager - Authentication servers must use PAP.
EDIT: on every freeradius config change this gets deleted, so you need to copy/paste and restart freeradius server every time :/.
-
@opti2k4 please have a look go https://forum.netgate.com/topic/140135/how-connect-freeradius-to-ms-ad/8
-
@free4 that works until you make a change on freeradius that causes service to restart. Then added stuff is gone.
There is also another problem, OTP is useless. I can connect to VPN without using OTP even though user is configured with OTP.
-
hi,
Could you solve the problem?
I have the same problem -
@ahmad-rostami please have a look go https://forum.netgate.com/topic/140135/how-connect-freeradius-to-ms-ad/8
as reminder, freeradius package has been created long time ago by the community.
this package Is mostly legacy and unmaintained nowadays.if you would like to fix the issues related to this package, feel free to contribute !
-
@free4 Thank you very much for solving my problem
Now how do I prevent reconnection user when finish the quota in captive portal ? -
@ahmad-rostami said in how connect freeradius to MS AD:
Now how do I prevent reconnection user when finish the quota in captive portal ?
Fill in these settings :
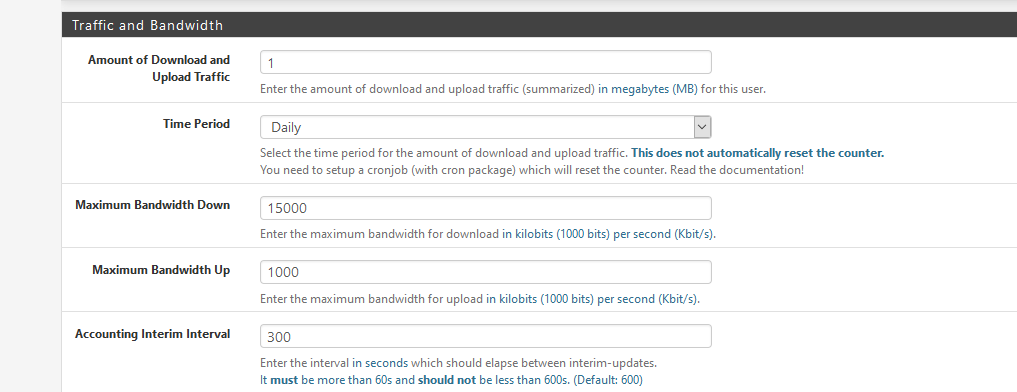
Login :
Jan 7 15:25:20 logportalauth 8909 Zone: cpzone1 - ACCEPT: x, b0:xx:2d:44:fc:da, 192.168.2.5After a 22 Megabyte download (this exceedings 21 MB ) I'm kicked out :
Jan 7 15:25:59 logportalauth 15139 Zone: cpzone1 - QUOTA EXCEEDED: x, b0:xx:2d:44:fc:da, 192.168.2.5Now I can login any more ....
I see these logs in the General System logs :Jan 7 15:30:13 root FreeRADIUS: User x has reached the daily amount of upload and download traffic (22 MB of 1 MB). The login request was denied.A cron job cleans out the daily totals, so tomorrow (for me : after 12h00) I can re login.
Btw : I'm using the FreeRadius package, and an external 'MariaDB' SQL database.
-
@Gertjan thanks for your reply
but this option for create user in radius
my user atuthentication With ldap(microsoft active directory) in radius
now how i can prevent user login when finish the quota
(I think it's impossible , That's the only solution creat user in freeradius?) -
Humm. Don't no. Never used 'LDAP', just FreeRadius and a database.
-
Hello soheil.amiri,
Hello free4,Did you ever get this up and running?
I am currently at the same point as you were.Out of the box nothing worked. Only the group membership check always works.
Setting the LDAP Auth in sites-enabled/default (as per free4) I can get it working with NTRadPing,
but only with CHAP disabled. With CHAP enabled it does not work.In an ordinary Windows-Client (WIFI) authenticating over Radius on an AP, I never get it running.
FreeRadius keeps complaining about a non clear-text pw. -
@free4
Hello Free4,
can you help me out a little bit with your three steps?What do I need to change in step 1.
I did step 2 already. Checking group memberships seems to work fine.I also did the workaround in step 3, which also works for me. It nearly looks perfect, but
it only works if I disable CHAP in NTRadPing.
If I try it from a Windows client it also wont work.
It keeps complaining about a non-clear-text password.rlm_ldap (ldap): Reserved connection (5) (2) ldap: EXPAND (sAMAccountName=%{mschap:User-Name}) (2) ldap: --> (sAMAccountName=test2) (2) ldap: Performing search in "DC=localdomain,DC=local" with filter "(sAMAccountName=test2)", scope "sub" (2) ldap: Waiting for search result... rlm_ldap (ldap): Rebinding to URL ldap://ForestDnsZones.localdomain.local/DC=ForestDnsZones,DC=localdomain,DC=local rlm_ldap (ldap): Waiting for bind result... rlm_ldap (ldap): Rebinding to URL ldap://DomainDnsZones.localdomain.local/DC=DomainDnsZones,DC=localdomain,DC=local rlm_ldap (ldap): Waiting for bind result... rlm_ldap (ldap): Rebinding to URL ldap://localdomain.local/CN=Configuration,DC=localdomain,DC=local rlm_ldap (ldap): Waiting for bind result... rlm_ldap (ldap): Bind successful rlm_ldap (ldap): Bind successful rlm_ldap (ldap): Bind successful (2) ldap: User object found at DN "CN=test2,OU=Spezialkonten-IT,OU=Users,OU=MyBusiness,DC=localdomain,DC=local" (2) ldap: Processing user attributes (2) ldap: WARNING: No "known good" password added. Ensure the admin user has permission to read the password attribute (2) ldap: WARNING: PAP authentication will *NOT* work with Active Directory (if that is what you were trying to configure) rlm_ldap (ldap): Deleting connection (5) - Was referred to a different LDAP server (2) [ldap] = ok (2) } # redundant = ok (2) if (&request:Calling-Station-Id == &control:Calling-Station-Id) { (2) ERROR: Failed retrieving values required to evaluate condition (2) [expiration] = noop (2) [logintime] = noop Not doing PAP as Auth-Type is already set. (2) [pap] = noop (2) } # authorize = ok (2) Found Auth-Type = CHAP (2) # Executing group from file /usr/local/etc/raddb/sites-enabled/default (2) Auth-Type CHAP { (2) chap: ERROR: &control:Cleartext-Password is required for authentication (2) [chap] = fail (2) } # Auth-Type CHAP = fail (2) Failed to authenticate the user (2) Using Post-Auth-Type Reject (2) # Executing group from file /usr/local/etc/raddb/sites-enabled/default (2) Post-Auth-Type REJECT { (2) attr_filter.access_reject: EXPAND %{User-Name} (2) attr_filter.access_reject: --> test2 (2) attr_filter.access_reject: Matched entry DEFAULT at line 11 (2) [attr_filter.access_reject] = updated (2) [eap] = noop (2) policy remove_reply_message_if_eap { (2) if (&reply:EAP-Message && &reply:Reply-Message) { (2) if (&reply:EAP-Message && &reply:Reply-Message) -> FALSE (2) else { (2) [noop] = noop (2) } # else = noop (2) } # policy remove_reply_message_if_eap = noop (2) } # Post-Auth-Type REJECT = updated (2) Login incorrect (Failed retrieving values required to evaluate condition): [test2/<via Auth-Type = CHAP>] (from client pfSense_NAT port 0) (2) Delaying response for 1.000000 seconds Waking up in 0.3 seconds. Waking up in 0.6 seconds. (2) Sending delayed response (2) Sent Access-Reject Id 42 from 172.16.1.254:1812 to 172.16.1.253:59069 length 20