how connect freeradius to MS AD
-
This post is deleted! -
try this:
vi /usr/local/etc/raddb/sites-enabled/default
add following in
authorize {}block, restart freeradiusif (!control:Auth-Type) { ldap if (ok && User-Password) { update { control:Auth-Type := LDAP } } } expiration logintimeAuth server under System - User Manager - Authentication servers must use PAP.
EDIT: on every freeradius config change this gets deleted, so you need to copy/paste and restart freeradius server every time :/.
-
@opti2k4 please have a look go https://forum.netgate.com/topic/140135/how-connect-freeradius-to-ms-ad/8
-
@free4 that works until you make a change on freeradius that causes service to restart. Then added stuff is gone.
There is also another problem, OTP is useless. I can connect to VPN without using OTP even though user is configured with OTP.
-
hi,
Could you solve the problem?
I have the same problem -
@ahmad-rostami please have a look go https://forum.netgate.com/topic/140135/how-connect-freeradius-to-ms-ad/8
as reminder, freeradius package has been created long time ago by the community.
this package Is mostly legacy and unmaintained nowadays.if you would like to fix the issues related to this package, feel free to contribute !
-
@free4 Thank you very much for solving my problem
Now how do I prevent reconnection user when finish the quota in captive portal ? -
@ahmad-rostami said in how connect freeradius to MS AD:
Now how do I prevent reconnection user when finish the quota in captive portal ?
Fill in these settings :
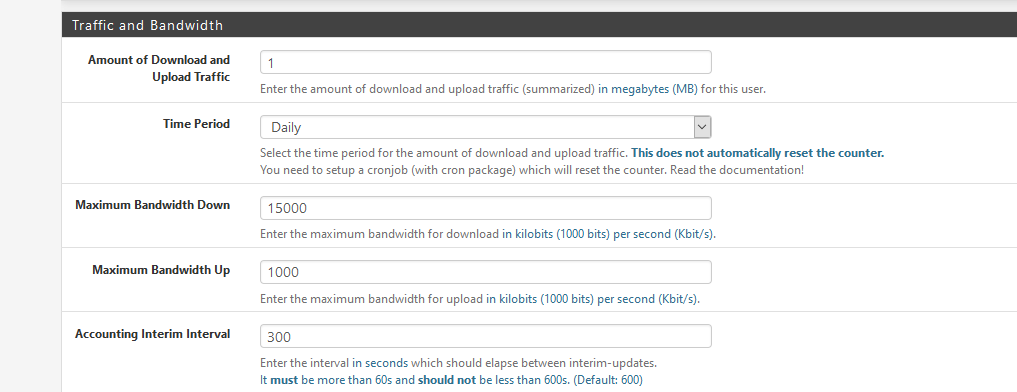
Login :
Jan 7 15:25:20 logportalauth 8909 Zone: cpzone1 - ACCEPT: x, b0:xx:2d:44:fc:da, 192.168.2.5After a 22 Megabyte download (this exceedings 21 MB ) I'm kicked out :
Jan 7 15:25:59 logportalauth 15139 Zone: cpzone1 - QUOTA EXCEEDED: x, b0:xx:2d:44:fc:da, 192.168.2.5Now I can login any more ....
I see these logs in the General System logs :Jan 7 15:30:13 root FreeRADIUS: User x has reached the daily amount of upload and download traffic (22 MB of 1 MB). The login request was denied.A cron job cleans out the daily totals, so tomorrow (for me : after 12h00) I can re login.
Btw : I'm using the FreeRadius package, and an external 'MariaDB' SQL database.
-
@Gertjan thanks for your reply
but this option for create user in radius
my user atuthentication With ldap(microsoft active directory) in radius
now how i can prevent user login when finish the quota
(I think it's impossible , That's the only solution creat user in freeradius?) -
Humm. Don't no. Never used 'LDAP', just FreeRadius and a database.
-
Hello soheil.amiri,
Hello free4,Did you ever get this up and running?
I am currently at the same point as you were.Out of the box nothing worked. Only the group membership check always works.
Setting the LDAP Auth in sites-enabled/default (as per free4) I can get it working with NTRadPing,
but only with CHAP disabled. With CHAP enabled it does not work.In an ordinary Windows-Client (WIFI) authenticating over Radius on an AP, I never get it running.
FreeRadius keeps complaining about a non clear-text pw. -
@free4
Hello Free4,
can you help me out a little bit with your three steps?What do I need to change in step 1.
I did step 2 already. Checking group memberships seems to work fine.I also did the workaround in step 3, which also works for me. It nearly looks perfect, but
it only works if I disable CHAP in NTRadPing.
If I try it from a Windows client it also wont work.
It keeps complaining about a non-clear-text password.rlm_ldap (ldap): Reserved connection (5) (2) ldap: EXPAND (sAMAccountName=%{mschap:User-Name}) (2) ldap: --> (sAMAccountName=test2) (2) ldap: Performing search in "DC=localdomain,DC=local" with filter "(sAMAccountName=test2)", scope "sub" (2) ldap: Waiting for search result... rlm_ldap (ldap): Rebinding to URL ldap://ForestDnsZones.localdomain.local/DC=ForestDnsZones,DC=localdomain,DC=local rlm_ldap (ldap): Waiting for bind result... rlm_ldap (ldap): Rebinding to URL ldap://DomainDnsZones.localdomain.local/DC=DomainDnsZones,DC=localdomain,DC=local rlm_ldap (ldap): Waiting for bind result... rlm_ldap (ldap): Rebinding to URL ldap://localdomain.local/CN=Configuration,DC=localdomain,DC=local rlm_ldap (ldap): Waiting for bind result... rlm_ldap (ldap): Bind successful rlm_ldap (ldap): Bind successful rlm_ldap (ldap): Bind successful (2) ldap: User object found at DN "CN=test2,OU=Spezialkonten-IT,OU=Users,OU=MyBusiness,DC=localdomain,DC=local" (2) ldap: Processing user attributes (2) ldap: WARNING: No "known good" password added. Ensure the admin user has permission to read the password attribute (2) ldap: WARNING: PAP authentication will *NOT* work with Active Directory (if that is what you were trying to configure) rlm_ldap (ldap): Deleting connection (5) - Was referred to a different LDAP server (2) [ldap] = ok (2) } # redundant = ok (2) if (&request:Calling-Station-Id == &control:Calling-Station-Id) { (2) ERROR: Failed retrieving values required to evaluate condition (2) [expiration] = noop (2) [logintime] = noop Not doing PAP as Auth-Type is already set. (2) [pap] = noop (2) } # authorize = ok (2) Found Auth-Type = CHAP (2) # Executing group from file /usr/local/etc/raddb/sites-enabled/default (2) Auth-Type CHAP { (2) chap: ERROR: &control:Cleartext-Password is required for authentication (2) [chap] = fail (2) } # Auth-Type CHAP = fail (2) Failed to authenticate the user (2) Using Post-Auth-Type Reject (2) # Executing group from file /usr/local/etc/raddb/sites-enabled/default (2) Post-Auth-Type REJECT { (2) attr_filter.access_reject: EXPAND %{User-Name} (2) attr_filter.access_reject: --> test2 (2) attr_filter.access_reject: Matched entry DEFAULT at line 11 (2) [attr_filter.access_reject] = updated (2) [eap] = noop (2) policy remove_reply_message_if_eap { (2) if (&reply:EAP-Message && &reply:Reply-Message) { (2) if (&reply:EAP-Message && &reply:Reply-Message) -> FALSE (2) else { (2) [noop] = noop (2) } # else = noop (2) } # policy remove_reply_message_if_eap = noop (2) } # Post-Auth-Type REJECT = updated (2) Login incorrect (Failed retrieving values required to evaluate condition): [test2/<via Auth-Type = CHAP>] (from client pfSense_NAT port 0) (2) Delaying response for 1.000000 seconds Waking up in 0.3 seconds. Waking up in 0.6 seconds. (2) Sending delayed response (2) Sent Access-Reject Id 42 from 172.16.1.254:1812 to 172.16.1.253:59069 length 20 -
@FrankoniaDKB
hello dear
unfortunately i could not bring it up.
with my test freeradius does not connect to MS AD DS. -
yep, I tried to configure it, and it simply not work. Better add NTP role to your MS AD DC servers, it simply will work without pain.
-
Hello soheil
Hello dragonangel,thanks for your answer. After messing around with it for two days, I now really tried using NPS one of my Windows Servers.
This worked easily like a charme and was done relatively fast. And it works cleanly.Thank you very much.
-
@soheil-amiri do you have any news about your issue? I'´m, trying to implmenet a similar scenario. My scenariou include FreeRadius with LDAP background authentication for WAP2-Enterprise authentication.
I setted up FreeRadius and background LDAP authentication, i tried authentication form pfsense, and works well.
But when i'm trying to authenticate users over WPA2-Enterprise SSID, i have authentication errors.
my users file config:
DEFAULT Ldap-Group == "cn=account-users,ou=wireless,dc=example,dc=com"
Tunnel-Type = VLAN,
Tunnel-Medium-Type = IEEE-802,
Tunnel-Private-Group-Id = "1010"Errors Logs:
jul 3 18:53:55radiusd98680(39) Login incorrect (eap_peap: The users session was previously rejected: returning reject (again.)): [radiuser1] (from client AP_LAB port 0 cli 92-1F-E6-B9-E9-1E)Jul 3 18:53:55radiusd98680(38) Login incorrect: [radiuser1] (from client AP_LAB port 0 cli 92-1F-E6-B9-E9-1E via TLS tunnel)
Can you help me?