IPSEC connectivity dropping (tunnel stays UP)
-
Hello guys;
About a month from now we have started experiencing some issues regarding our IPSEC connection do AWS.
Basically we lose connection to our AWS instances although the IPSEC tunnel appears connected on the webui and the connection is normalized only after around 30-40 min or when we manually disconnect and connect the tunnel.
Attached follows my configuration and part of the IPSEC logs from the moment the moment happens. I´ve activated a more verbose log mode and will monitor it fot more information.
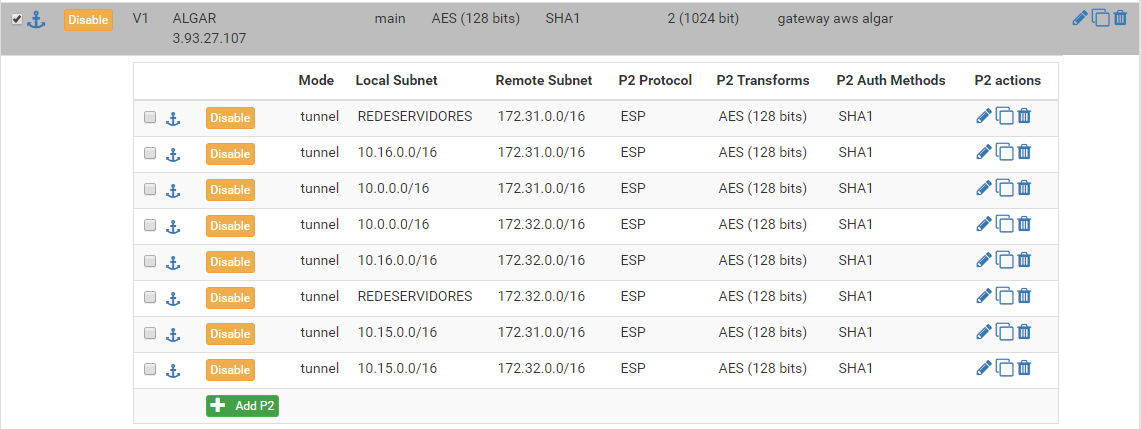
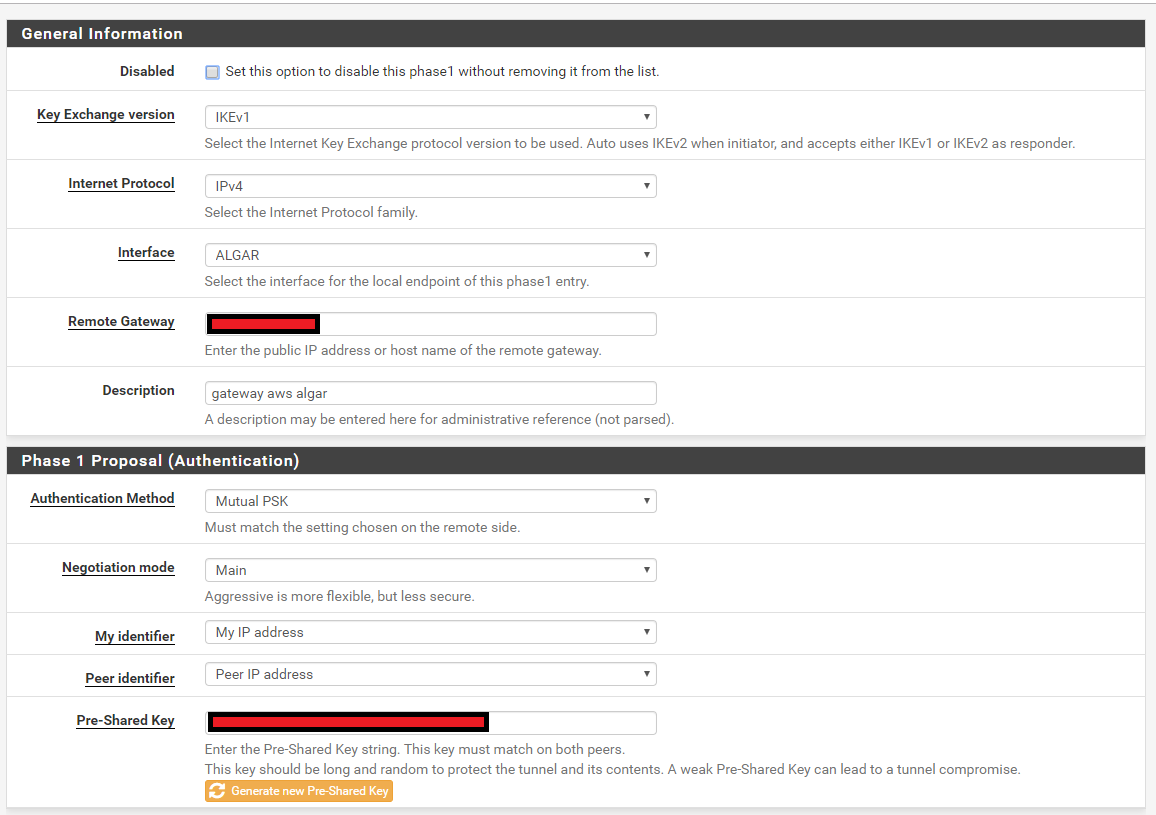
I have already recreated the VPN connections on AWS and on PFSENSE, double checked all configuration (IKE versios, key and networks) but the problem persists.
Any ideas on this?
Thanks a lot!
Andre.
-
@armandelli
Hello
What device is on the other side of the tunnel ?
Cisco ?
In my opinion , there is a problem in the remote side
Note that starting at 08: 10: 41, the remote side begins to close the connections.Nov 22 08:10:41 srvfw02 charon: 09[IKE] <con5000|2> received DELETE for ESP CHILD_SA with SPI b26262a5 Nov 22 08:10:41 srvfw02 charon: 09[IKE] <con5000|2> closing CHILD_SA con5000{29} with SPIs c78cf6e8_i (9333422 bytes) b26262a5_o (71040 bytes) and TS 172.23.1.0/24|/0 === 172.31.0.0/16|/0 Nov 22 08:14:15 srvfw02 charon: 14[IKE] <con5000|2> received DELETE for ESP CHILD_SA with SPI 25f06df5 Nov 22 08:14:15 srvfw02 charon: 14[IKE] <con5000|2> closing CHILD_SA con5001{30} with SPIs c5649cba_i (5500748 bytes) 25f06df5_o (3841456 bytes) and TS 10.16.0.0/16|/0 === 172.31.0.0/16|/0 Nov 22 08:16:17 srvfw02 charon: 06[IKE] <con5000|2> received DELETE for ESP CHILD_SA with SPI b9884f1c Nov 22 08:16:17 srvfw02 charon: 06[IKE] <con5000|2> closing CHILD_SA con5003{31} with SPIs c8eb8f42_i (3988132 bytes) b9884f1c_o (1890702160 bytes) and TS 10.0.0.0/16|/0 === 172.32.0.0/16|/0 Nov 22 08:17:43 srvfw02 charon: 06[IKE] <con5000|2> received DELETE for ESP CHILD_SA with SPI 60eafc3a Nov 22 08:17:43 srvfw02 charon: 06[IKE] <con5000|2> closing CHILD_SA con5002{32} with SPIs cbd8db6d_i (182517679 bytes) 60eafc3a_o (898633496 bytes) and TS 10.0.0.0/16|/0 === 172.31.0.0/16|/0It is necessary to look logs of the second participant of connection
-
-
@armandelli I would look closely at the Phase 2 lifetime on both sides. The dump doesn't show it, neither does your screenshot, but both sides must agree to use the same lifetime. If AWS is using shorter lifetime than pfSense, it will tear down the sessions.
-
@awebster Hello! Thanks for the input!
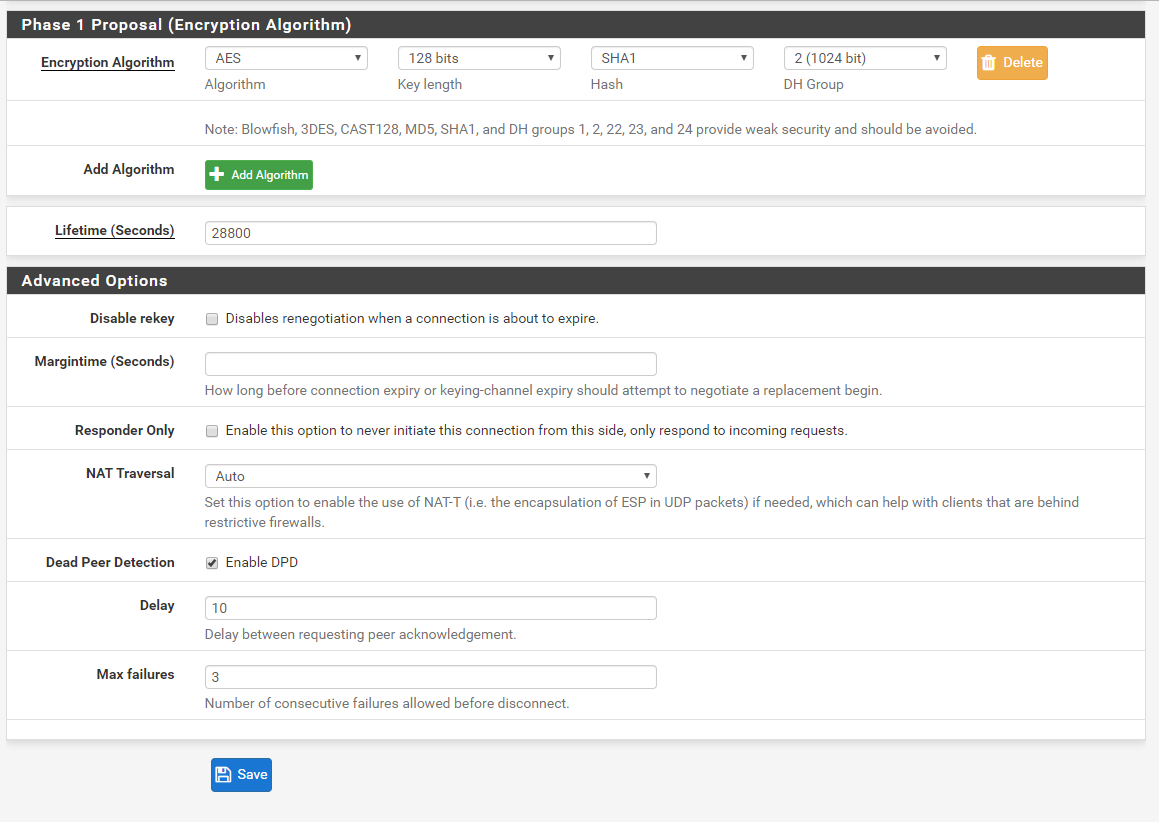
I've checked the Phase 2 configuration and they are using a lifetime of 3600, as per AWS configuration file.
! #2: IPSec Configuration
!
! The IPSec transform set defines the encryption, authentication, and IPSec
! mode parameters.
! Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
! Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24.
! Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".Expand the VPN configuration clicking in "+" and then create a new Phase2 entry as follows:
***a. Disabled :uncheck
b. Mode : Tunnel
c. Local Network : Type: LAN subnet
Address : ! Enter your local network CIDR in the Address tab
d. Remote Network : Type : Network
Address : ! Enter your remote network CIDR in the Address tab
e. Description : Amazon-IPSec-vpnxxxPhase 2 proposal (SA/Key Exchange)
a. Protocol : ESP
b. Encryption algorithms :aes128
c. Hash algorithms : hmac-sha1-96
d. PFS key group : 2
e. Lifetime : 3600 seconds***