Setting up a VLAN with pfSense, Ubiquiti, and ESXi
-
@pfSenseUser78 said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
added a DHCP range that isn't apart of my existing network,
Did you just add a range to the existing DHCP config or create another config for the VLAN? Each interface requires it's own separate configuration. You should see the VLAN interface on the DHCP server tab.
-
This post is deleted! -
I created another config for the VLAN (I think). Internal DHCP is handled by a Window Server. VLAN 90 (for IoT) can be DHCP server from pfSense.
-
@pfSenseUser78 said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
I created another config for the VLAN (I think). Internal DHCP is handled by a Window Server. VLAN 90 (for IoT) can be DHCP server from pfSense.
I thought you said the DHCP server was on the firewall. Now you're saying it's on the Windows server. Which is it? If it's on the Windows server, then the problem has nothing to do with pfSense.
-
@pfSenseUser78 said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
I saw something about using VLAN 4095 on the ESXi host but
If you want to pass tags to pfsense virtual nic, then yes you would have to set the vlan ID on your esxi vswitch/port group to be 4095 or it will strip tags.. Pfsense can not see vlans then.
-
For the internal NON-IoT network DHCP is handled by a windows domain controller. For the VLAN being setup for the IoT devices I do NOT need DHCP handled by a windows DC; I was saying that this can be handled by pfSense directly.
-
@johnpoz said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
@pfSenseUser78 said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
I saw something about using VLAN 4095 on the ESXi host but
If you want to pass tags to pfsense virtual nic, then yes you would have to set the vlan ID on your esxi vswitch/port group to be 4095 or it will strip tags.. Pfsense can not see vlans then.
Ok, so, after finding where to make that change AND making it, I now get a DHCP IP address in the 192.168.90.x/24 range. Hurray!
My next issue is that DNS doesn't appear to be working. I'd like to point DNS to my two internal DNS servers in the 172.16.249.x/24 range as I'm not using pfSense for DNS either; how do I do that? If you can point me in the right direction it'd be much appreciated.
-
To point your clients to other NS, just edit your dhcp scope to had out what you want.. out of the box pfsense if running dns, be it unbound (resolver or can be forwarder mode) or dnsmasq (forwarder) will point to itself for dns. If not running either, then it will hand out what is in its general tab.
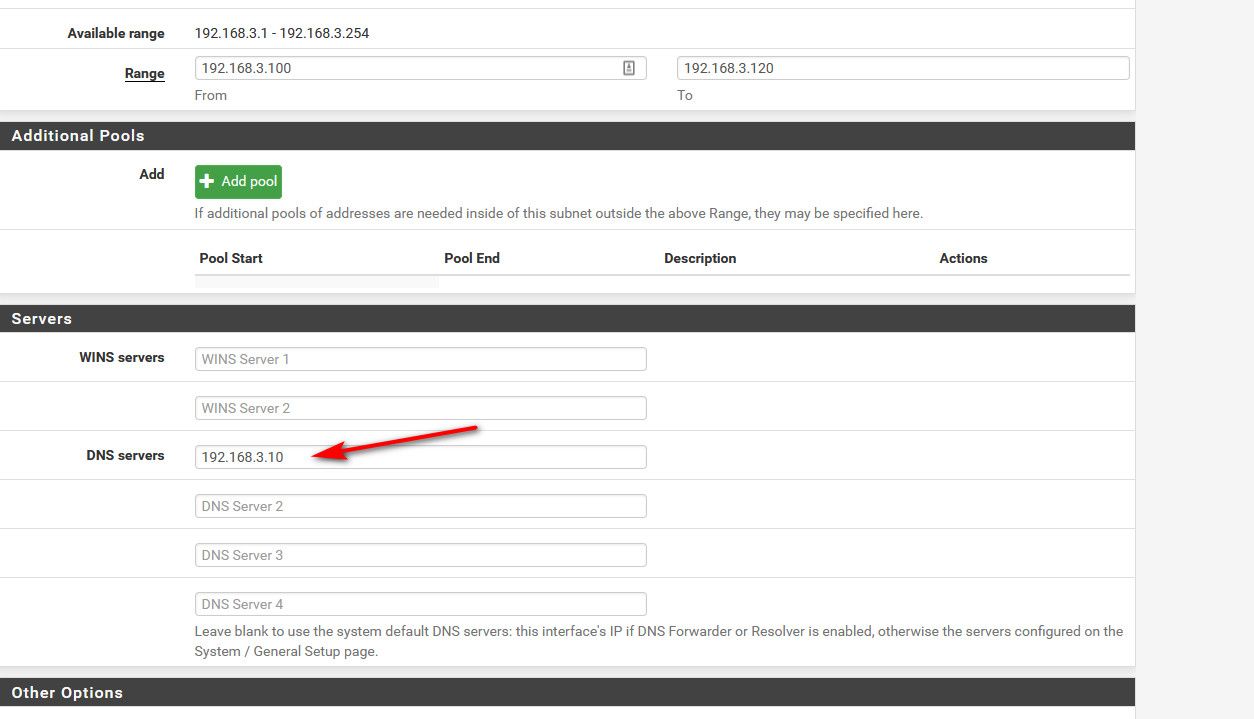
To hand out something other, like your internal NS - just edit the dhcp scope..
example - here I hand out 192.168.3.10 to clients in this network
-
@pfSenseUser78 said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
For the internal NON-IoT network DHCP is handled by a windows domain controller. For the VLAN being setup for the IoT devices I do NOT need DHCP handled by a windows DC; I was saying that this can be handled by pfSense directly.
Then we're back to my original question, did you set up the DHCP config on the VLAN? In the DHCP config, there are pages for each interface. The way I read your original post, it sounded like you just added an address pool to the main interface.
-
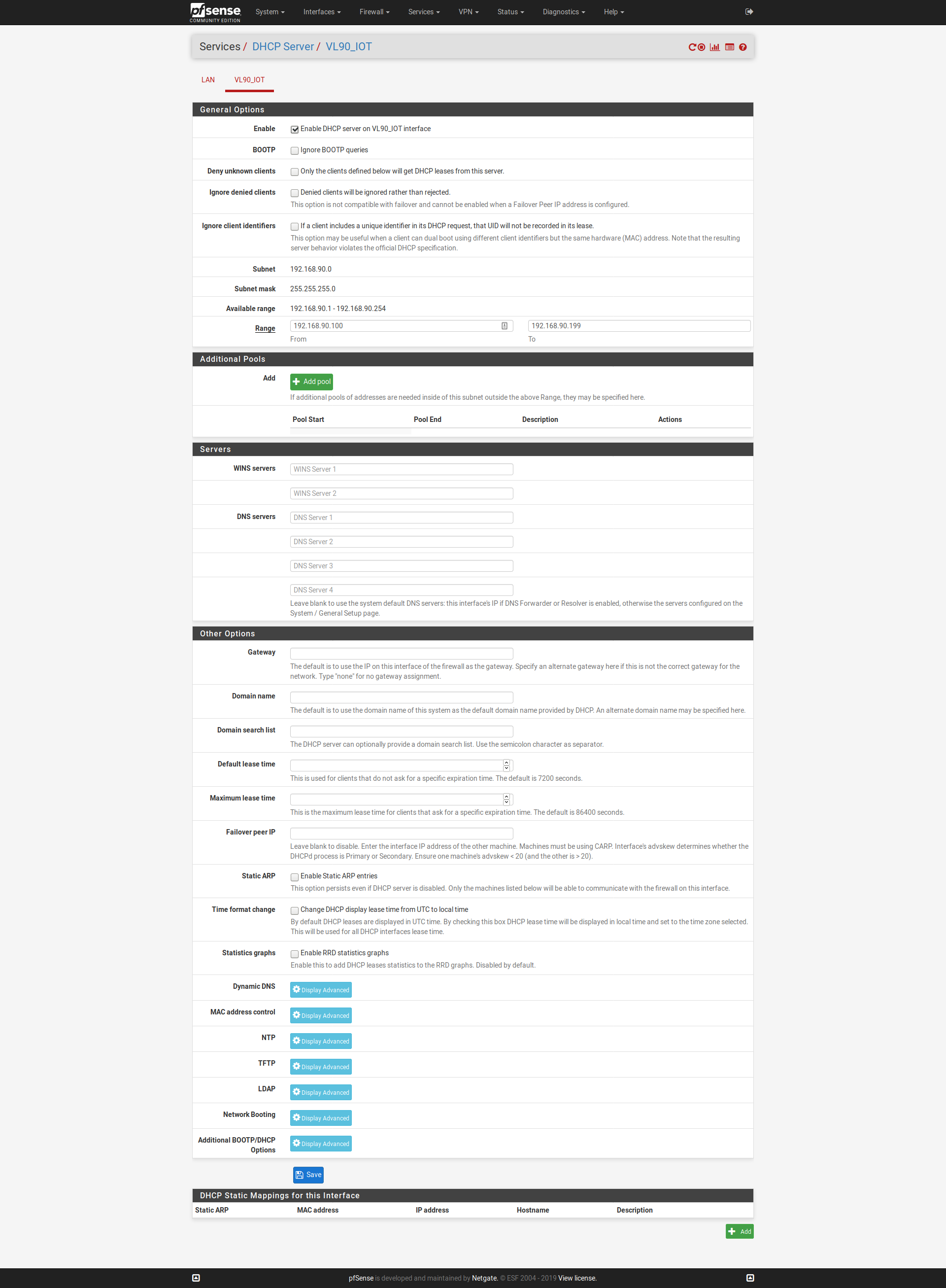
So this is what I have for DNS in the VLAN DHCP config:
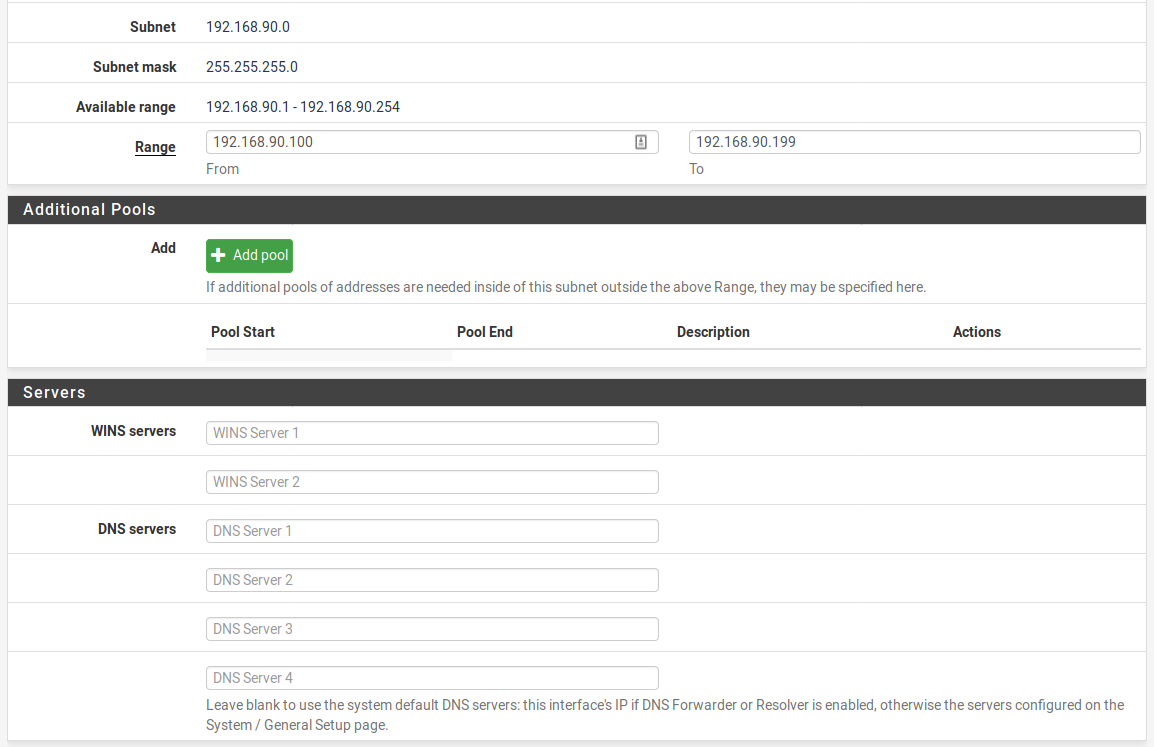
I have this as a firewall rule:
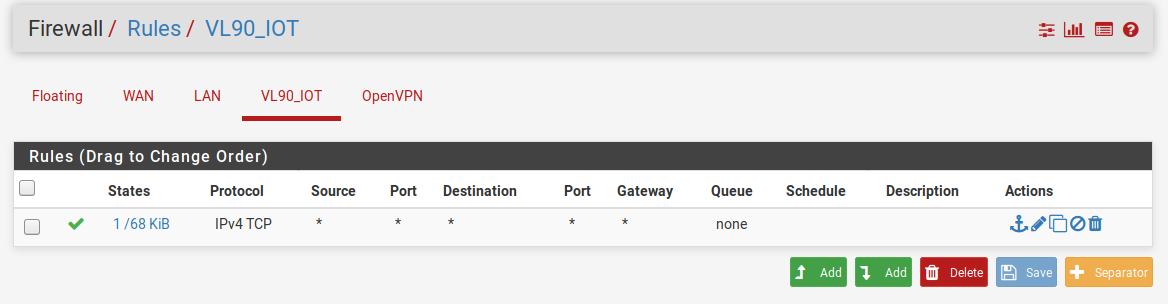
When I connect to the network on my iPhone I connect and get an IP address, however, the spinny thing next to the network name never goes away. If I try to load a website, nothing happens. If I manually specific a DNS server, nothing happens. Note that on my non-VLAN network I have a rule blocking all DNS traffic that doesn't originate from one of the two internal servers; not sure if this would be affecting a VLAN on a different IP range or not (the greyed out rule was a failed attempt to redirect errant DNS queries back to one of the two internal DNS servers at 105 or 106 - 78 & 79 are there for other reasons):
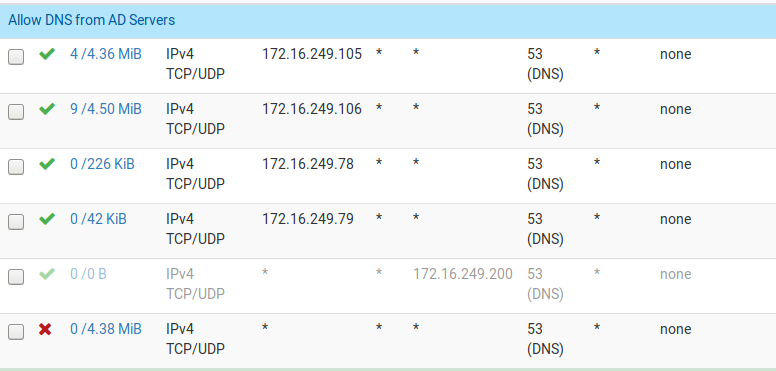
And here is the DNS servers setup in general:

Please let me know if there is any additional information I can provide; I greatly appreciate everything so far.
-
@JKnott said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
@pfSenseUser78 said in Setting up a VLAN with pfSense, Ubiquiti, and ESXi:
For the internal NON-IoT network DHCP is handled by a windows domain controller. For the VLAN being setup for the IoT devices I do NOT need DHCP handled by a windows DC; I was saying that this can be handled by pfSense directly.
Then we're back to my original question, did you set up the DHCP config on the VLAN? In the DHCP config, there are pages for each interface. The way I read your original post, it sounded like you just added an address pool to the main interface.
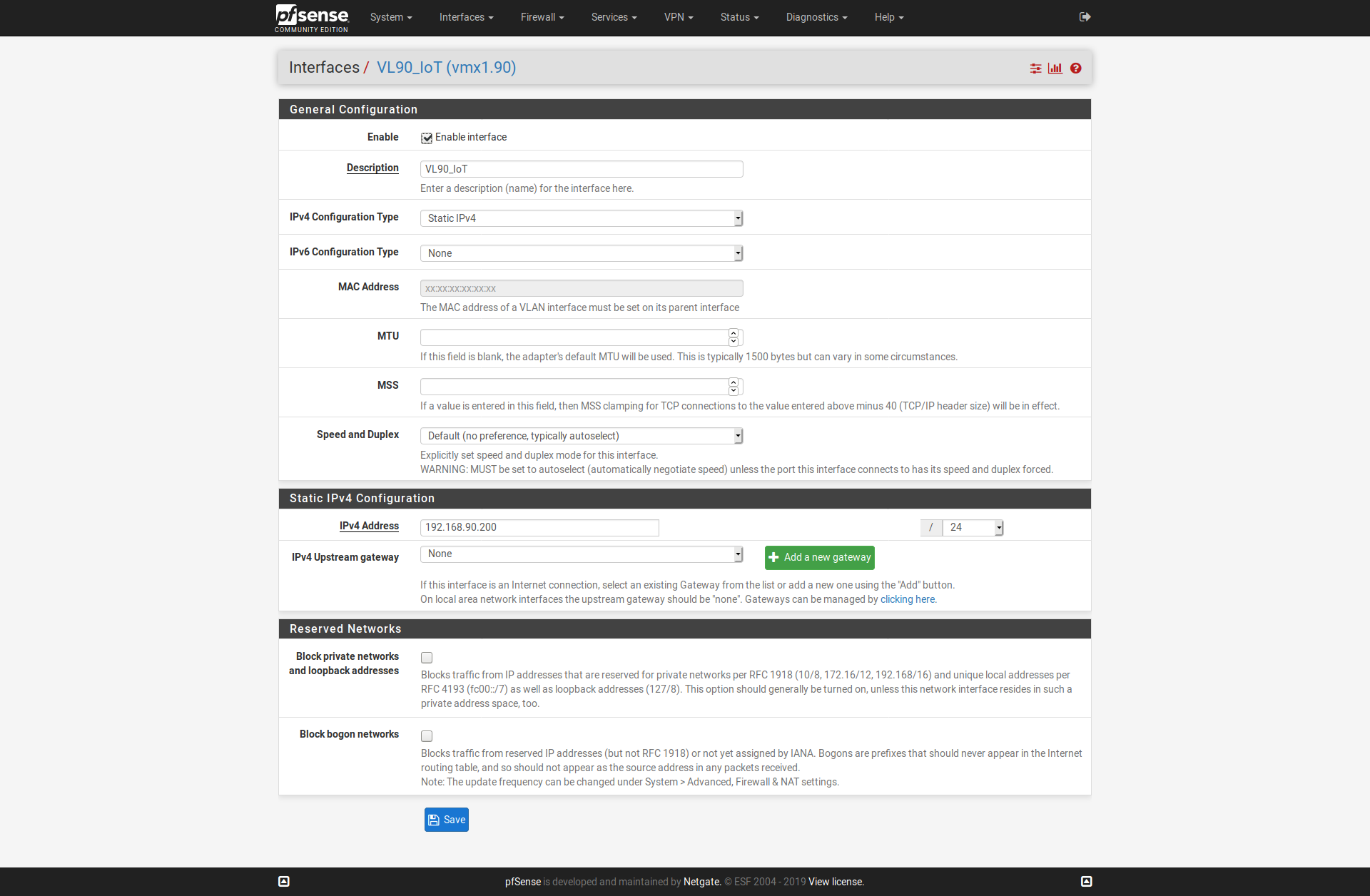
.
..
Hope this helps - if not let me know what else I can provide a screenshot of.
-
You are not setting DNS servers in the DHCP configuration so this is what DNS servers will be sent to the clients (just like it says right there):
Leave blank to use the system default DNS servers: this interface's IP if DNS Forwarder or Resolver is enabled, otherwise the servers configured on the System / General Setup page.
So it depends on whether or not you have the resolver or forwarder configured, in which case the clients will get 192.168.90.200 as their DNS server. If DNS forwarder/resolver are NOT configured, they'll get whatever is configured in System > General.
-
Here's what's set as my DNS servers in System > General:
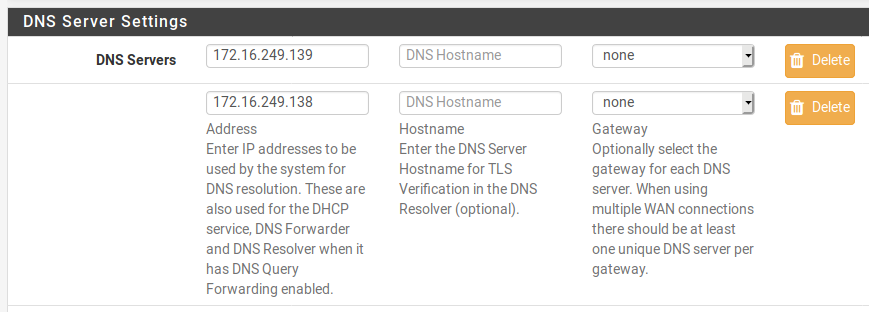
Could it be that the VLAN devices can't connect to the DNS servers?
-
Look at the DNS servers the clients are being assigned. Can the resolve names from them? If not, then yest that's a problem.
-
@Derelict DNS server being assigned to the clients is the firewall itself (172.16.249.200).
-
Can they resolve names using that?
-
Ok. I can connect to the network (via WiFi) with my laptop. I get an IP address on the VLAN range. From there, I cannot ping 8.8.8.8 and I can't ping 192.168.90.200 (which should be the VLAN Firewall).
Not being able to ping 8.8.8.8 tells me I might have a rule issue somewhere. I know I have one to block DNS queries on my main network (172.16.249.1/24) that don't originate from one of two DNS servers (on that same network) but that shouldn't block me from pinging 8.8.8.8.
-
Vlans when created have zero rules on them - so not being able to do anything would be default.. What rules did you put on your vlan interface? Just that tcp rule, well no you wouldn't be able to do dns which is udp normally, and no you wouldn't be able to ping which is icmp..
-
Two things:
- Rules on the new interface passing traffic from the hosts on that interface.
- Outbound NAT on the WAN for the new interface source addresses if you strayed from Automatic or Hybrid outbound NAT.
Those two things are installed by default on the LAN but not for any interfaces you might subsequently create.
-
@johnpoz Makes sense, where would I find the rules I need to create? I've searched but I've not been able to find what they are.
Edit: I've also looked at the default rules and don't see what get setup to try and duplicate on the VLAN.