HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox
-
@JeGr said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
canary
But the canary stayed the same, so that should already disable it.
-
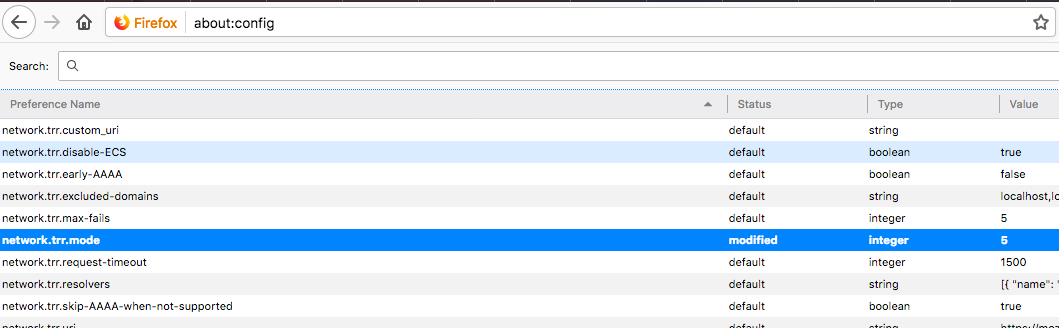
I have been reading this thread and have added the list found in the link that BBcan177 provided above to DNSBL. However, where is the about:config mentioned by Jim so I can set network.trr.mode to 5? This is what I saw in Firefox preference:
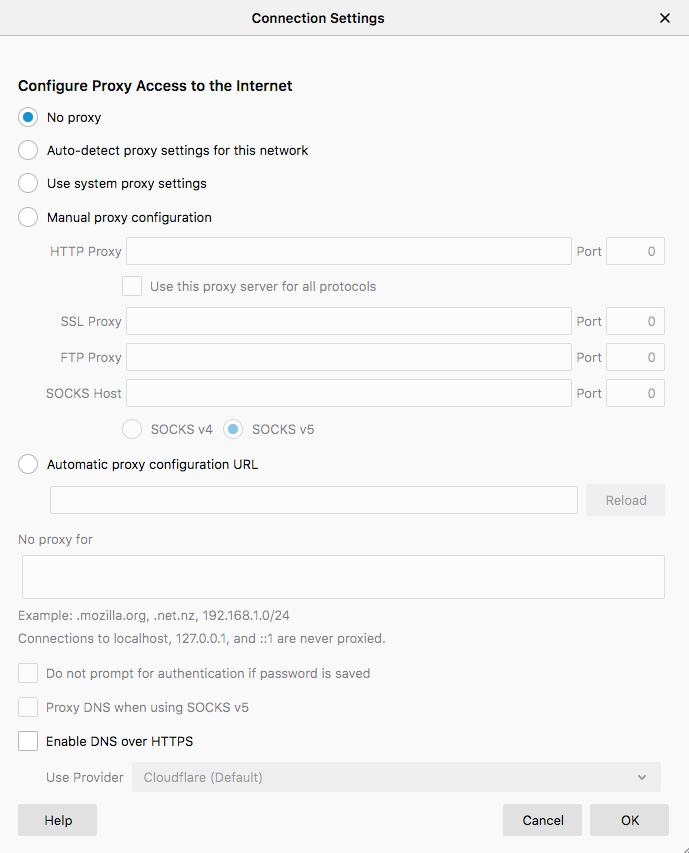
-
in the about:config section
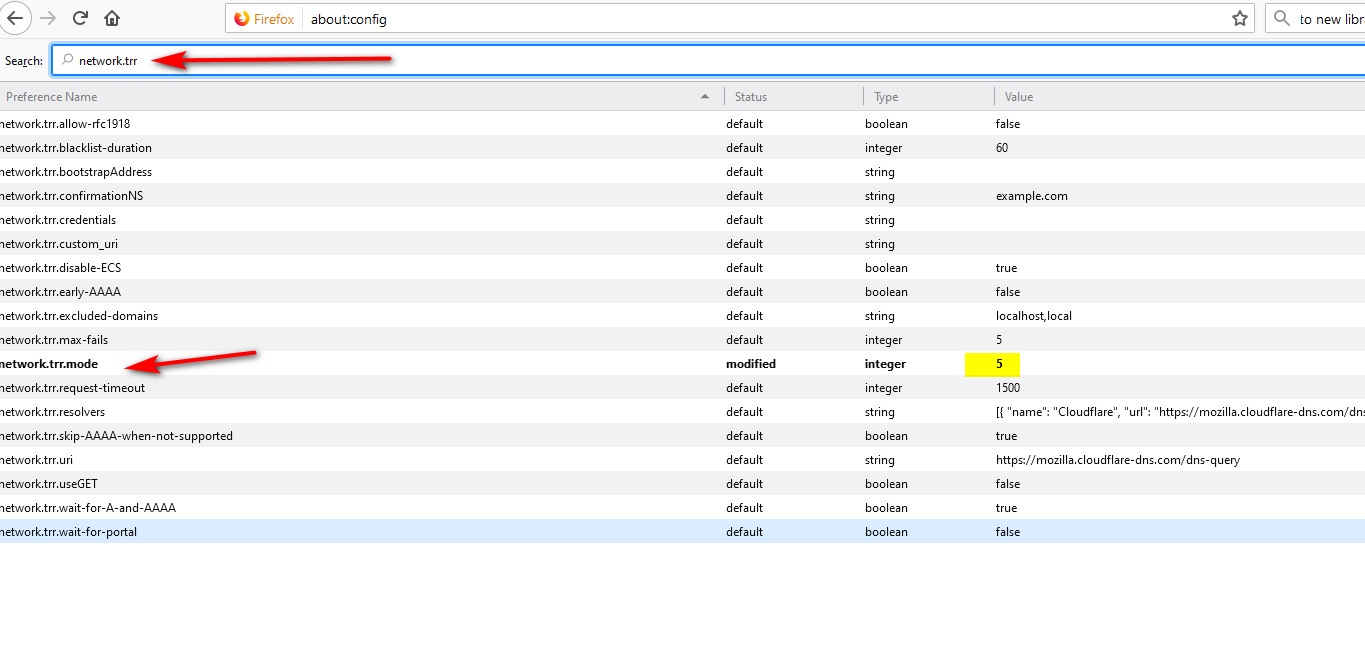
-
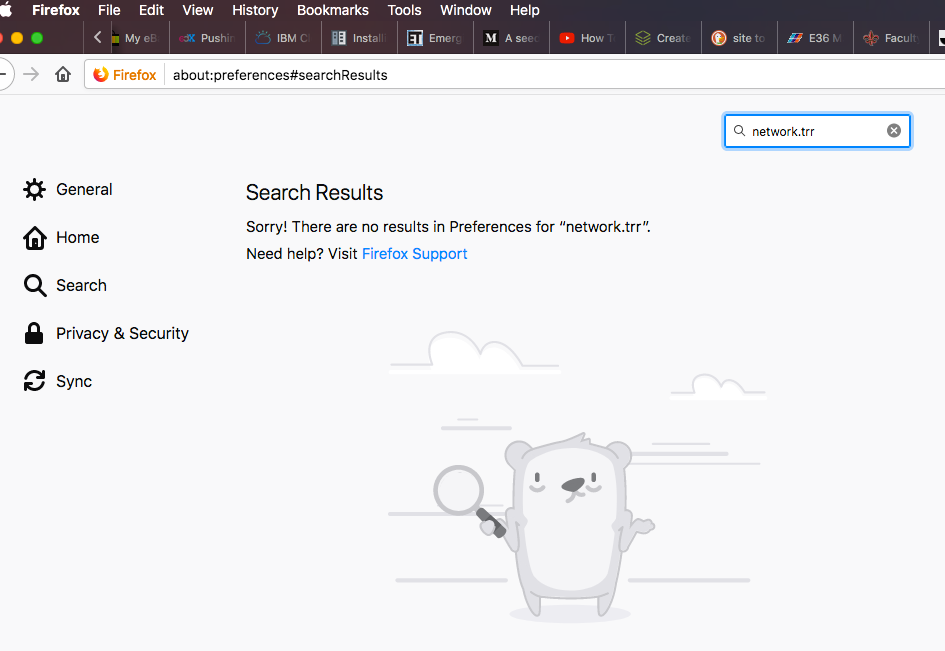
@johnpoz Thanks John for responding...it seems that Macs don't have that options...I am using Firefox 69.0.2...
-
I don't have a mac to test with.. But your at about:preferences not about:config?
No you wouldn't find it there - see I went there in my windows firefox
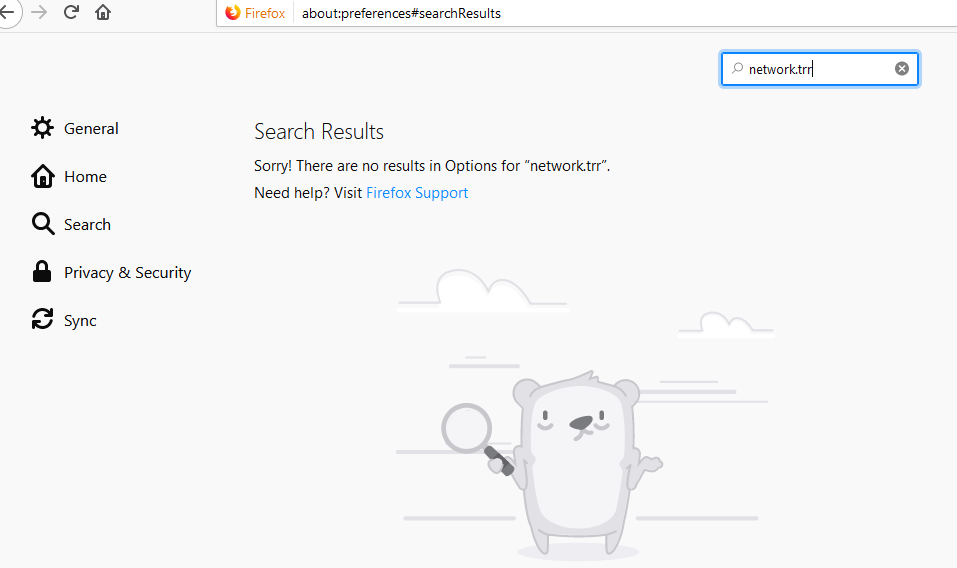
-
@johnpoz Found it John...one has to type about:config in the URL bar and accept the risk...thank you!
-
I've just tried the unbound custom option... it seems Firefox keeps asking for its DoH stuff, Suricata seeing some associated traffic.
1 TCP A Network Trojan was Detected 10.X.X.X 51133 104.16.249.249 443 1:2027695 ET POLICY Observed Cloudflare DNS over HTTPS Domain (cloudflare-dns .com in TLS SNI) -
Did you set TRR in firefox to 5? Without some details of what you actually did there is little anyone can do to help you find out what you did wrong.
You need to make sure unbound return NX..
I watch this like a hawk and have rules in place to log any sort of doh to any of the know ns doing doh, and block tos - and have not seen any hits on the rules at all.
-
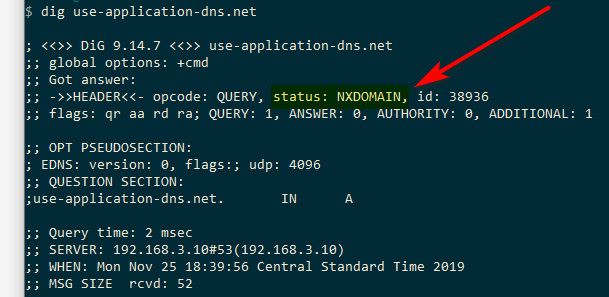
The purpose was to test the usage that Firefox makes of its canary domain and if it obey their published rules.
First of all, the status is NOERROR not NXDOMAIN
; <<>> DiG 9.10.6 <<>> use-application-dns.net ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27411 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;use-application-dns.net. IN A ;; ANSWER SECTION: use-application-dns.net. 60 IN A 10.10.10.1 ;; Query time: 45 msec ;; SERVER: 10.0.0.1#53(10.0.0.1) ;; WHEN: Tue Nov 26 21:31:02 CET 2019 ;; MSG SIZE rcvd: 68TRR was 2 as it was the intend of that quick test.
-
Well that is not how canary is meant to work - so yeah it would fail... It needs to return NX..
https://support.mozilla.org/en-US/kb/canary-domain-use-application-dnsnet
You returned no error and A record... So yeah its going to be able to use doh.
-
I've changed
local-zone: "use-application-dns.net" staticto
local-zone: "use-application-dns.net" always_nxdomainAnd it now works
; <<>> DiG 9.10.6 <<>> use-application-dns.net ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 58414 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;use-application-dns.net. IN A ;; Query time: 37 msec ;; SERVER: 10.0.0.1#53(10.0.0.1) ;; WHEN: Wed Dec 04 20:16:56 CET 2019 ;; MSG SIZE rcvd: 52Well kind of, Suricata keeps logging the same alert (ET POLICY Observed Cloudflare DNS over HTTPS Domain (cloudflare-dns .com in TLS SNI))
-
@HuskerDu said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
cloudflare-dns .com in TLS SNI)
Who says that is firefox? That could be some malware/trojan you have on your network.
I see zero hits to 1.1.1.1 or 1.0.0.1, so firefox wouldn't doing it.. Unless your client not using pfsense for dns, and not seeing the nx for the canary..
-
This only happens when I launch Firefox from the machine which generates an alert in Suricata. No worms/trojans and co, it only happens when :
- Firefox is set to use DNS over HTTPS
- Firefox is launched
My firewall rules only allow DNS to pFsense (including NATing 8.8.8.8:53 towards the firewall for Android devices.... whatever you are telling them, they keep checking "Internet connectivity" on that).
Interestingly, it is not hitting 1.1.1.1 but 104.16.249.249. Maybe the anycast IP is used for marketing purposes but not always used in real life traffic ?
-
@HuskerDu said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
104.16.249.249
https://community.cloudflare.com/t/dns-over-https-using-https-104-16-249-249-dns-query
-
I skimmed the comments and didn’t see any mention of this...
I’m now seeing IOS devices trying to connect out to google DoH servers.
For now I’ve just blocked Google’s DoH infrastructure but it looks like we’re on the cusp of a technological arms-race.
-
@motific said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
looks like we’re on the cusp of a technological arms-race.
Yup!! Its going to be interesting to be sure.. I think this is is an understatement to be sure. But I really do not think its the place of applications to try and circumvent local dns no matter if their intentions are good or not..
Unless the user of said application be it a browser or any other application specifically sets this application to use some dns be it direct or doh or dot, the application should use the OS set dns..
I am not a fan of the browser using anything other than what my OS is set to use for dns, without my explicit validation to do so.. It for sure its an arms race to have users dns point to a specific location.. I have no problem with the browser offering the ability to do doh or dot.. But its not something the application should just assume - it should have to be called out to do such things by the person running the application.. If they want to default the application to do such a thing it should be a clear op in sort of thing.. There is no scenario where opt out makes any sense - and opt out is a bad thing for sure..
This goes for any sort of device or application - you should use the dns handed you via dhcp, or set by the user in the os or device. Circumvention of this in anyway is violation of user choice! If the user wanted to use xyz for dns - then they should set that be it on the device/application specifically or what they hand out via dhcp..
Using the excuse that the user is too stupid to set this, and we are going what is best for the user is just nonsense!! And just looking to grab information from the users too stupid to know what is going on. Even IF!!! this was being done with the best of intentions - which it is not.. Its the wrong way to go about it.. Education of the user is the correct way!! Let the user chose and set what they want to use..
-
When I put
local-zone: "use-application-dns.net" staticin my Custom options box, I get
The following input errors were detected: The generated config file cannot be parsed by unbound. Please correct the following errors: /var/unbound/test/unbound.conf:102: error: syntax error read /var/unbound/test/unbound.conf failed: 1 errors in configuration fileLine 102 in that file is the local-zone line from above.
I'm running 2.4.4-RELEASE-p3 (amd64)
-
You need the
server:
Statement in the box before you can add any other custom commands
here
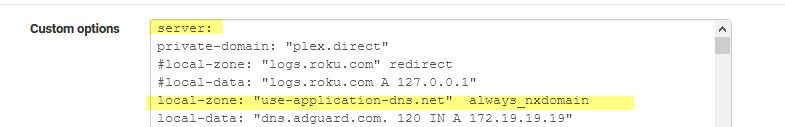
You can also add the always_nxdomain for good measure.
-
hurricane electric joined the doh and dot party
The public recursors at 74.82.42.42 / 2001:470:20::2 / ordns.he.net now also support DNS over TLS (DoT) and DNS over HTTPS (DoH) for those who wish to use those interfaces. or for those who want to block it ... -
Just in time for Firefox to crank up the DoH setting
https://arstechnica.com/information-technology/2020/02/firefox-turns-encrypted-dns-on-by-default-to-thwart-snooping-isps/