Chrome and Safari not liking pfSense generated certificates (gives revoked error and non compliant)
-
I have pfSense running with hostname of pfsense.homedomain.com (not the actual domain for security of course).
I have created a CA using the certificate manager, and then exported the keys and have them trusted as a CA root on my OSX machine. Likewise, I have imported the CA into Firefox's chain as well.
Then I created a new internal certificate, using pfsense.homedomain.com as my common name, and created a few SAN's using "pfsense" another SAN using the IP of the machine just to be sure. Once I had the cert created I configured the WebUI to use this new certificate.
Now, here's where it gets stupid. Firefox will work 100% since I have the CA from pfsense imported into its chain. I also get a green lock and the entire chain looks great!
Wrong. Chrome and Safari REFUSE to let me access the site. I have confirmed that the CA is in my OSX keychain as a trusted CA. but when I browse I get this error on Chrome:
https://share.getcloudapp.com/NQuvL7rB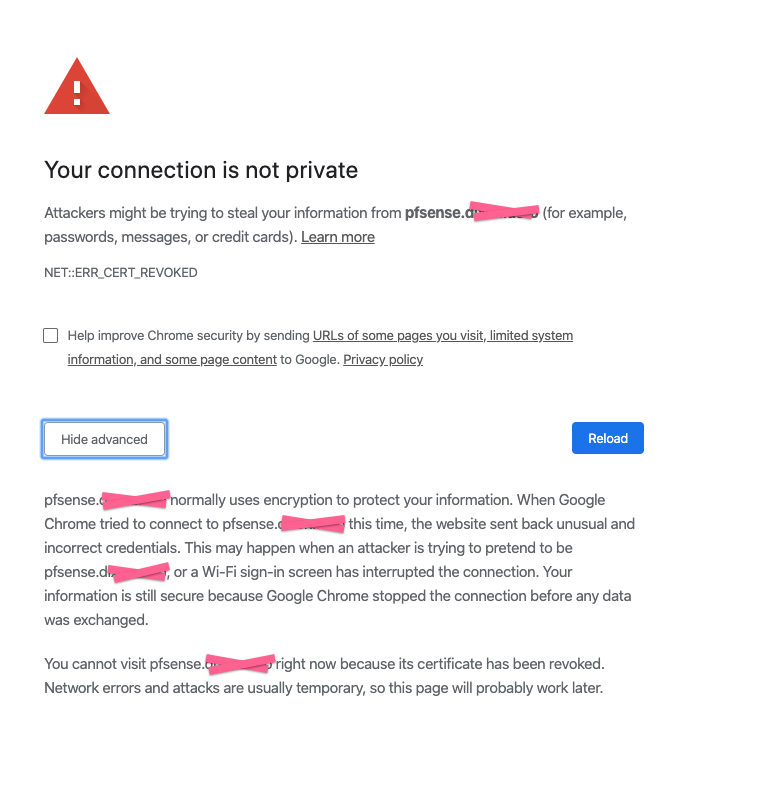
Likewise, when I try to visit the page using Safari I get a different message about the certificate:
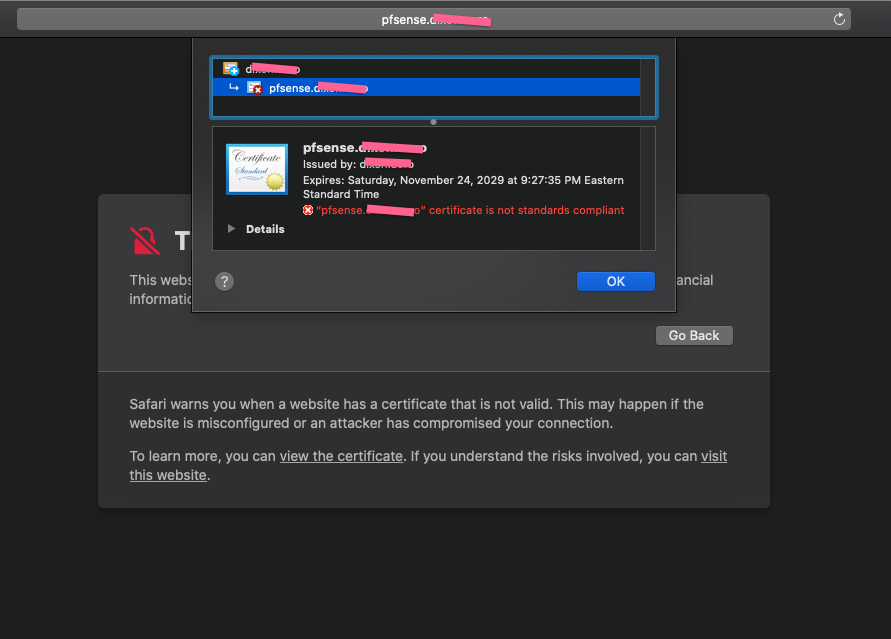
I can't get this to work with Chrome or Safari, and the errors aren't leading me to anything concrete to fix. Can someone give me some suggestions?
-
Hi @CubedRoot - are you running MacOS 10.15.x by chance? If so, you are probably running into this:
https://support.apple.com/en-us/HT210176
Hope this helps.
-
Yes, try using a cert with less that 825 days lifetime. pfSense uses 3650 by default.
Steve
-
Holy crap! The expiration date was the key! I bumped it down to 800 days and it worked perfectly.
Thanks everyone! This one had me pulling my hair out trying to figure it out. I would have never figured it was the expiration date on the cert.
-
Yeah that for sure could bite some people in the ass ;) Prob should change the default time and add a note in the cert manager..
Since all my local certs where issued before the March 1, 2018 timeframe - they should still be good for the 10 years ;)
But will have to double check them all ;)
Tuesday, December 12, 2017
Friday, December 10, 2027I might have redone some recently..
-
Thats not a bad idea @johnpoz . I haven't tried chrome on Windows, but with how strict Chrome is with SSL certs, I imagine they are heading to this direction (if not already there).
-
Already done in 2.5: https://redmine.pfsense.org/issues/9825
-
On 2.4.4-p3 you can apply
71185882dc168e49347f0924f33a207aaf6e2db0with the system patches package and then runpfSsh.php playback generateguicertand it will make you a new GUI cert with the new 825-day default.