How to find spambot? Got network abuse report from my ISP
-
Back then (2014) when i did set up Snort the tutorial said WAN.
But i made a search now and it seems like the recommendation is to put Snort on the LAN.I guess unless that spam thing happens again i will never know what it was.
As i said i did a lot of testing/playing the last days and maybe it was something on a Raspberry Pi -
@MrGlasspoole There may be differing options on this subject, but I have Suricata running on both interfaces. The WAN to identify incoming nefarious activity and the LAN to identify the same thing outgoing (e.g. infected machines or the same thing you're experiencing right now, etc)
-
@marvosa said in How to find spambot? Got network abuse report from my ISP:
The WAN to identify incoming nefarious activity
Why would it matter unless forwarded, if forwarded through to lan - you would see it there, and stop it, etc.
-
@marvosa said in How to find spambot? Got network abuse report from my ISP:
I have Suricata running on both interfaces. .... and the LAN to identify the same thing outgoing (e.g. infected machines or the same thing you're experiencing right now, etc)
You are aware of the fact that most traffic is "invisible" these day : SSL encrypted.
The unwanted traffic also encrypted these days.Site that use 'http' web access start to fade away, as do 'clear' smtp / pop and imap communication. It's smtps these days (or pops or imaps).
Suricata can not inspect that SSL traffic flow.The information that is known at the firewall level is : the destination IP, port, DNS and reverse DNS.
What's in the subsequent traffic stays hidden. -
If you have the spare CPU cycles then inspect traffic on both but that's going to be double inspecting on the vast majority of traffic. If you run on only one interface I would recommend LAN. You don't see hits on the firewall itself but having visibility on the internal IPs of more valuable IMO. I depends what you're trying to catch.
Steve
-
@johnpoz said in How to find spambot? Got network abuse report from my ISP:
Why would it matter unless forwarded, if forwarded through to lan - you would see it there, and stop it, etc.
I just like to see what alerts are generated on the WAN.. just because I'm curious... also, IMO, if you're going to run it at all... you might as well run it on both fronts.
@Gertjan said in How to find spambot? Got network abuse report from my ISP:
You are aware of the fact that most traffic is "invisible" these day : SSL encrypted.
The unwanted traffic also encrypted these days.
Site that use 'http' web access start to fade away, as do 'clear' smtp / pop and imap communication. It's smtps these days (or pops or imaps).
Suricata can not inspect that SSL traffic flow.
The information that is known at the firewall level is : the destination IP, port, DNS and reverse DNS.
What's in the subsequent traffic stays hidden.Yes, I am aware of encrypted traffic and neither said Suricata could inspect SSL traffic nor do I expect it to. It's all about rules, signatures, and reputation.
-
@marvosa said in How to find spambot? Got network abuse report from my ISP:
you might as well run it on both fronts.
Nope - that logic makes no sense..
-
@MrGlasspoole FWIW, I'd block the mail ports as suggested overnight. Probably be able to come up with the offender by morning. Also, how many clients are you serving and what kind of antivirus protection do you have in place? Could also possibly a laptop someone brought in.
-
I have the ports blocked since 3 days and Snort runs now on LAN.
Nothing shows up. All phones, PCs, tablets, the print server, satellite receiver, DECT station are connected as ever.
Nobody was here with a another device.
As i said: could be something temporary from playing around and it's no longer present.
But it's hard to believe there was something in Raspbian, Armbian or DietPi.
Maybe something i did but on the new Fire TV stick that i already did uninstall...The funny thing is that the day before someone from my ISP was here because bridge mode did not work and there box sometimes did crash/reboot.
He was the only one with other devices.
He told me the router did not receive the last firmware automatically and made a reset to factory defaults. After that the router did pull the newest firmware. -
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
Nothing shows up
You mean : even you didn't send a mail ?
Show us the LAN firewall ?@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
He was the only one with other devices.
These devices are not passing through pfSense ...
-
Does anybody know what this means, in his screenshot above?
source_port: 33431
Jeff
-
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
source_port: 33431 source-port: 33431 original-rcpt-to: www.tiaanxxxxxxxx.09@gmail.com source-ip: 176.199.xxx.xxxWhen the mail was send, it cam from the IP 176.199.xxx.xxx using port 33431.
The device that send the mail the mail was behind pfSense (but was it - see my question just above) and so it was NATted.
The original source LAN IP and source port can't be known to the ISP.
The only thing they and we know is the destination, a gmail mail server and one of the mail destination ports : 465 or 25 if gmail still accepts mail on port '25'. -
@Gertjan said in How to find spambot? Got network abuse report from my ISP:
You mean : even you didn't send a mail
What i mean is that nothing shows up that is trying to send mails.
Sure, if I try to send one (what of course is not working) it shows up. -
It happened again.
Nothing in Snort and mail ports are blocked:
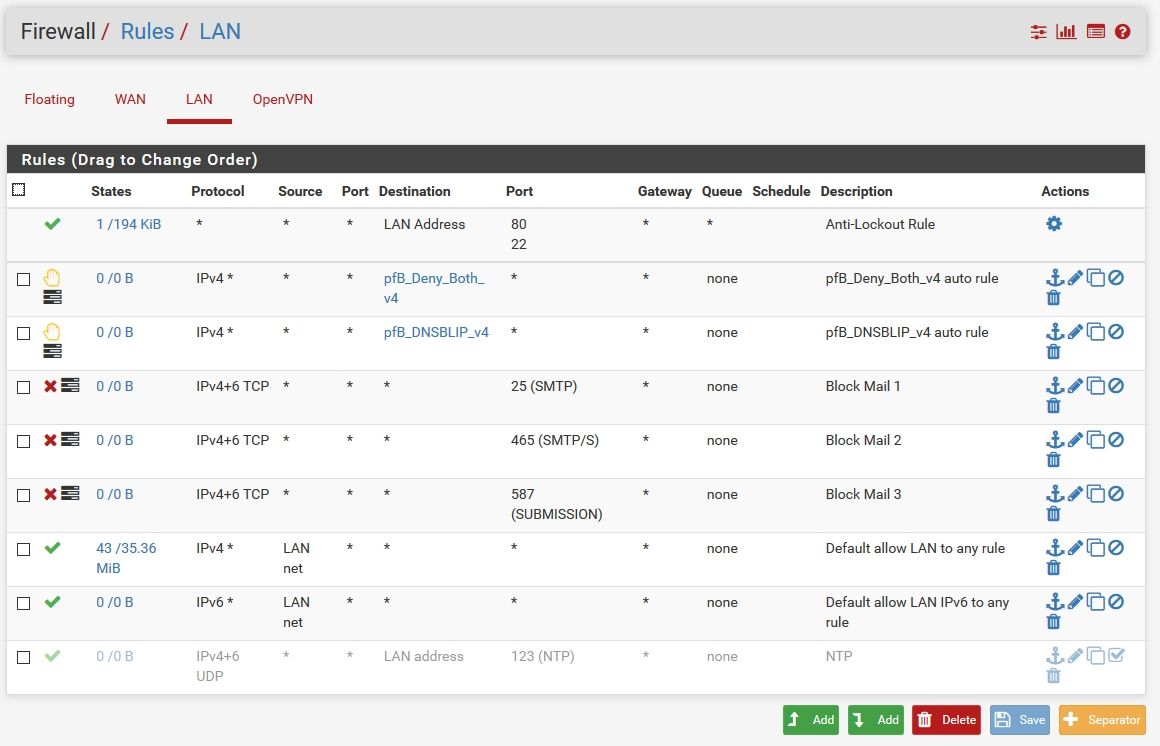
I have a lot of blocked UDP but i don't know what device it is with that IPv6:
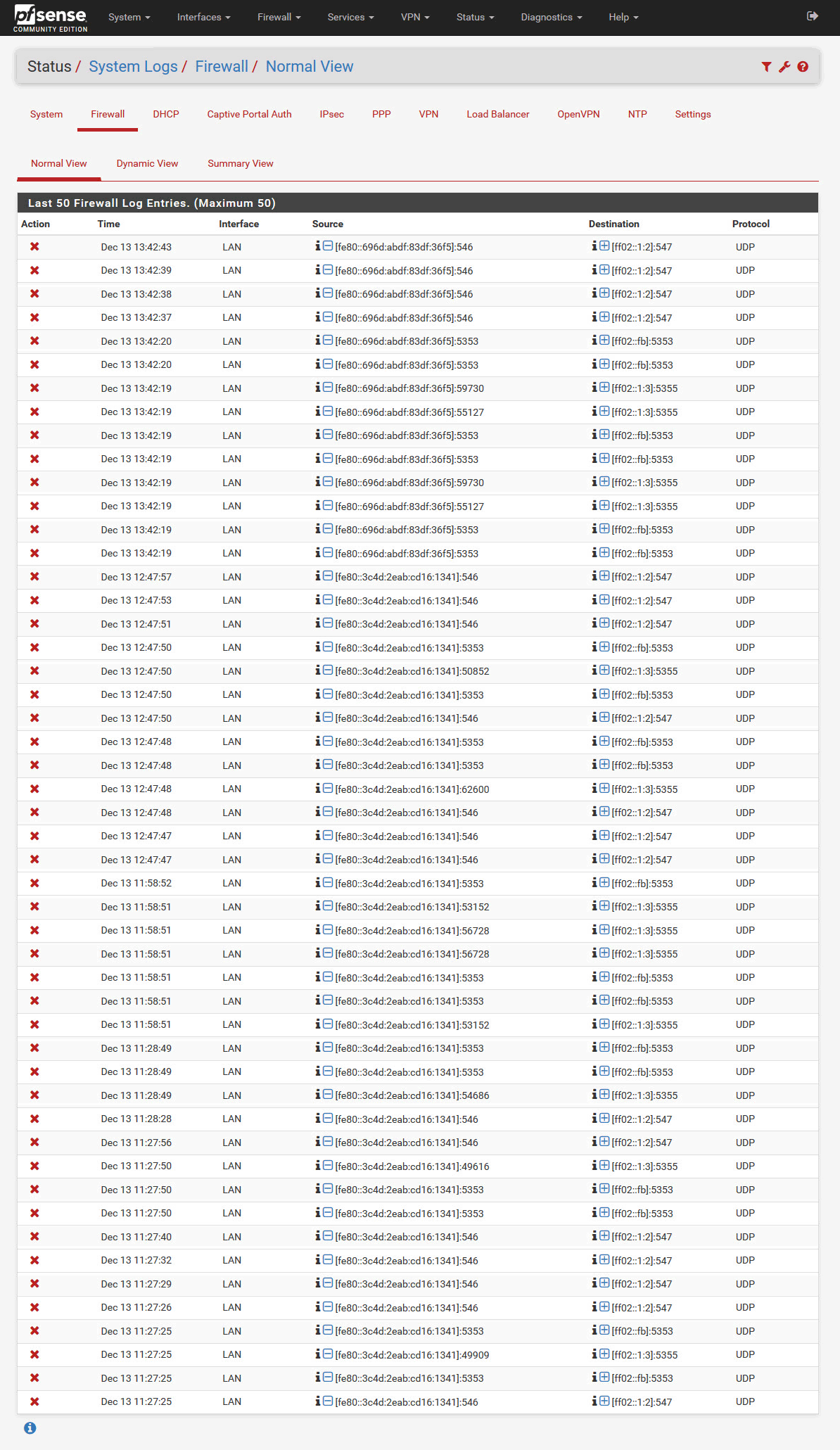
And this and 10.1.254.10 is my Nvidia Shield:
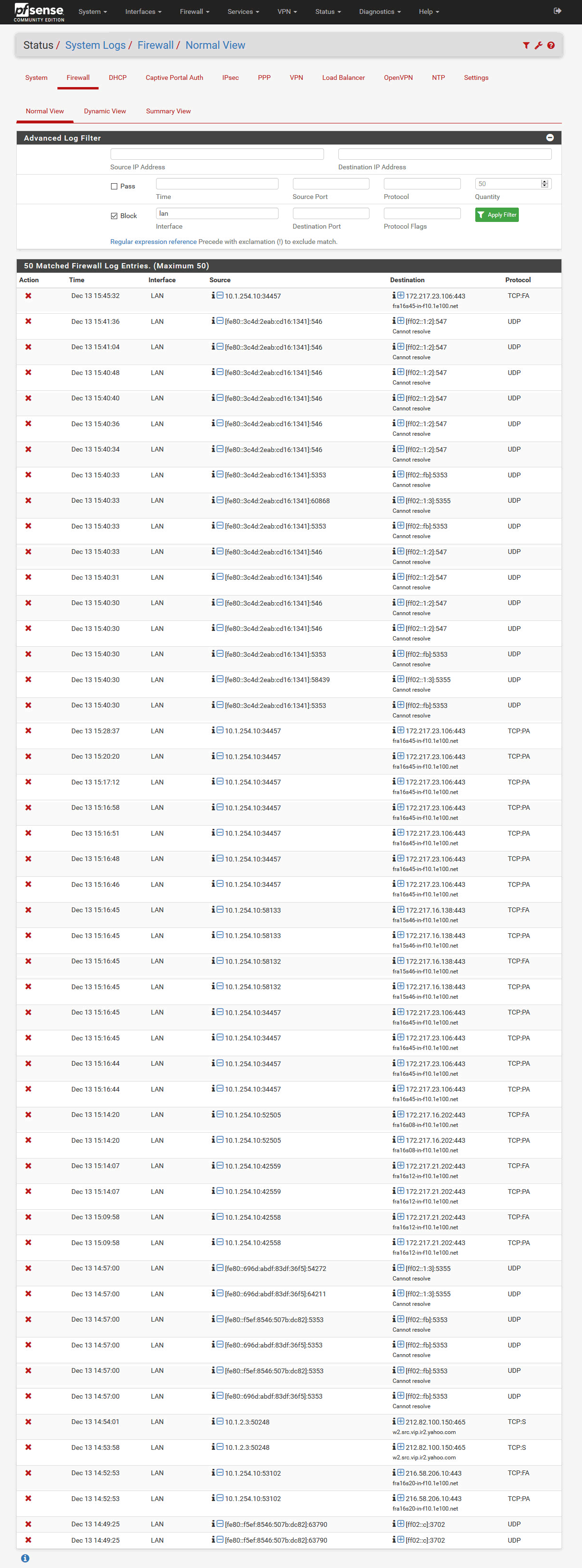
-
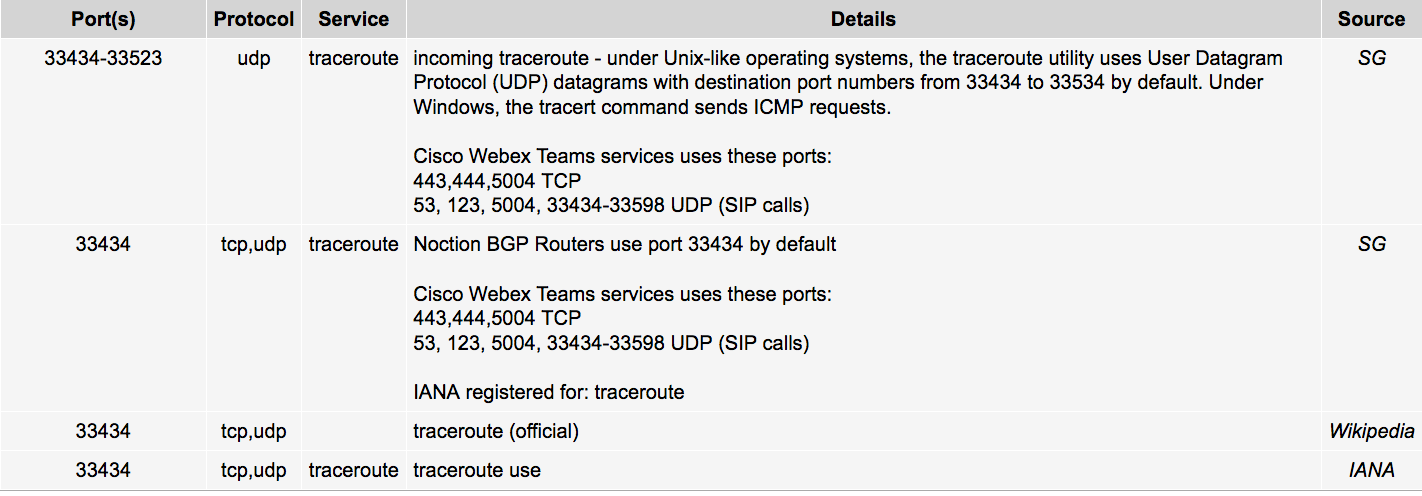
@akuma1x said in How to find spambot? Got network abuse report from my ISP:
Does anybody know what this means, in his screenshot above?
source_port: 33431
Jeff
A quick search revealed this...could it be his router in front of pfSense doing the spamming?
-
Humm.
No need to list firewall logs - or the rules. As the link (from your ISP ?) shows, the last 2 days there were no spam mails. It stopped 11 December, that was two days ago.
Your firewall rules look ok to me.
I played with an identical rule :
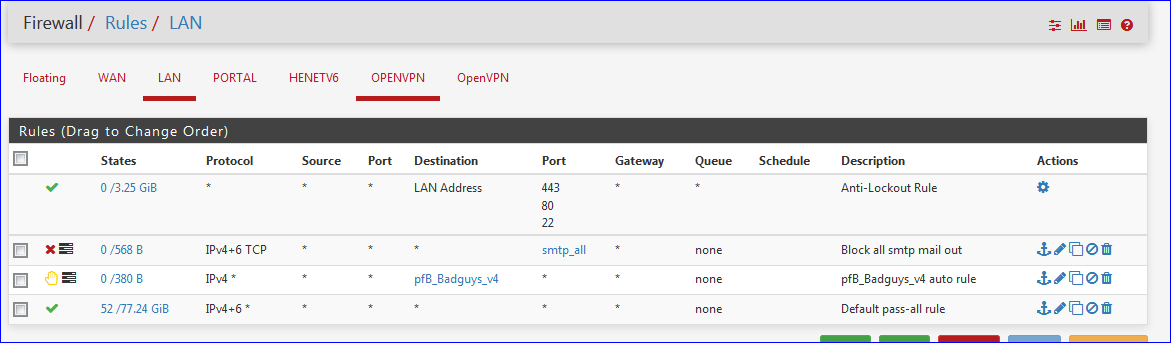
My second rules, with the port-alias including 25,465,587 works just fine : Outlook, the mail client is now hurling it can't mail out any mails ....
That the rules is capturing traffic can be seen by :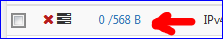
What this all means : if mail reaches the Internet by your WAN IP, it isn't injected via your LAN (?) interface.
By OpenVPN (is this a VPN server interface ?) ?
If not, that it's pretty save to say : this spam mail does flow through pfSense. What this means : you can disconnect the LAN interface and spam will still be send. Because it's not originating from a device 'behind' pfSense - on it's LAN.
pfSense is connected to what upstream device ? A router with wifi or other devices connected to it ? -
@Gertjan Wondered whether his ISP serviceman loaded a corrupted firmware on the router!
-
There is only the ISP router/modem in front of pfSense.
Until last week i had double NAT but it is now switched to bridged mode.
So the routers WLAN and everything is off.OpenVPN is the OpenVPN Server in pfSense.
What also changed is that i moved from Proxmox to Hyper-V (in Windows 10) that is giving me trouble and not working reliable. Had pfSense running in Proxmox for a long time and also in Hyper-V 2016 Core without problems.
https://forum.netgate.com/topic/148638/can-t-get-puplic-ip-in-pfsense-with-hyper-v-in-windows-10-pro -
That only happens in fake Youtube movies and other SF films.
It can be done, though .... but who wins what where and when ?
If only the tech service can update such a router, the scandal would be huge : ISP out of business .... that's mega $$$$$$.
If one can't trust his ISP router any more .....
Said that : my ISP router is just a router : no TV - phone - Wifi facilities are enabled. It's a pure VDSL to LAN-port device, having pfSense as it's only client-device. No one connects to the other 3 available LAN ports - never.
-
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
OpenVPN is the OpenVPN Server in pfSense.
So, this could be another vector ?!
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
Hyper-V (in Windows 10)
Yet another vector : if the hosting W10 machine has access to the pfSense WAN interface (ir shouldn't) any software in the host (W10) could output mail, completely bypassing pfSense.
Again : these spam mails are not passing through pfSense. Up to you to test the rest.
Btw :
https://docs.netgate.com/pfsense/en/latest/virtualization/virtualizing-pfsense-with-hyper-v.htmlWhen they talk about the WAN :
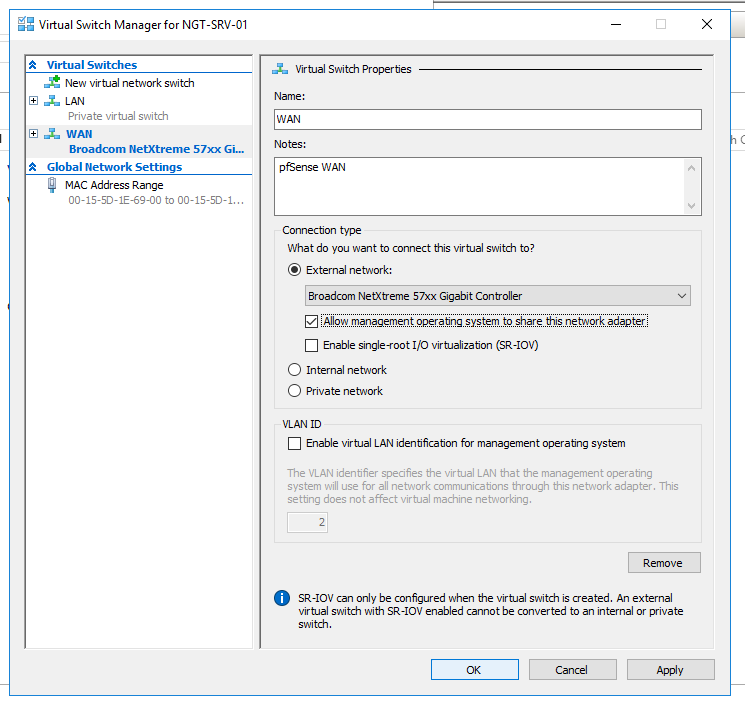
the option : "Allow management operating system to share this network adapter" should be unchecked !!
If not, the host could use it, bypassing pfSense.