ipsec phase 2 goes up only if traffic initiate from one side
-
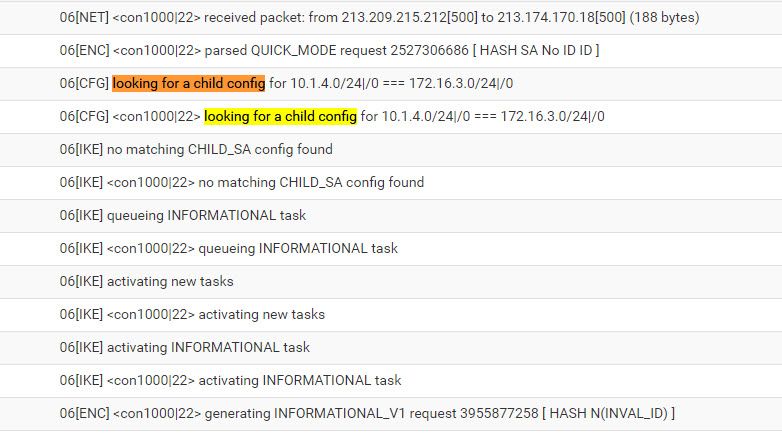
if traffic initiate from the other side in the receiver pfSense log I see "no matching CHILD_SA config found".
but there is.
Following there are a few screenshot that explain log and configuration.
Initiator:
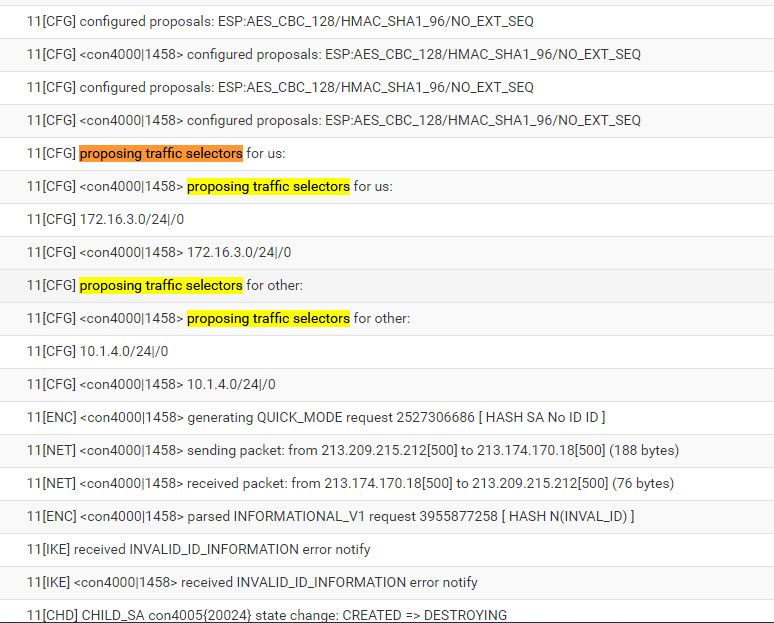
Receiver:
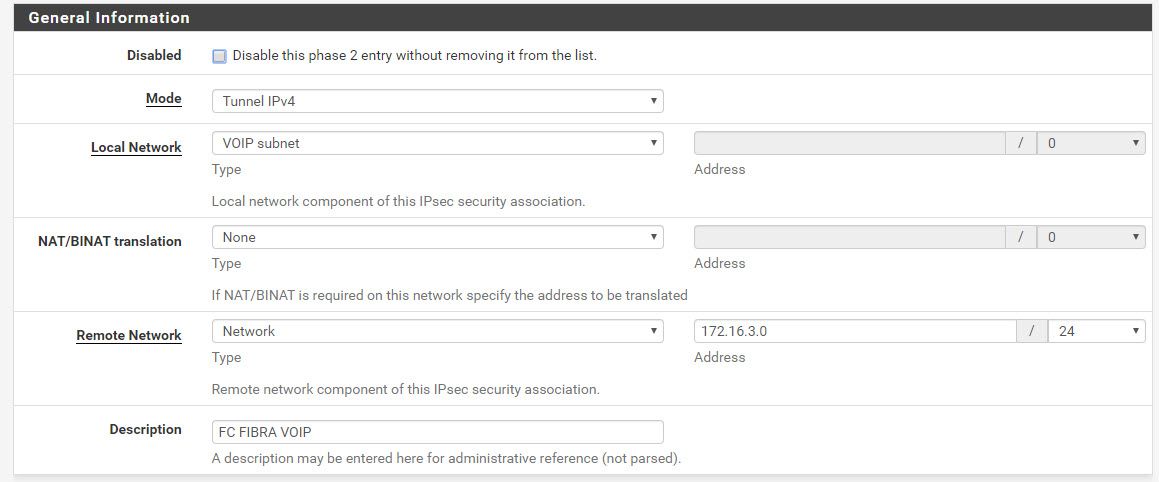
Phase 2 config:
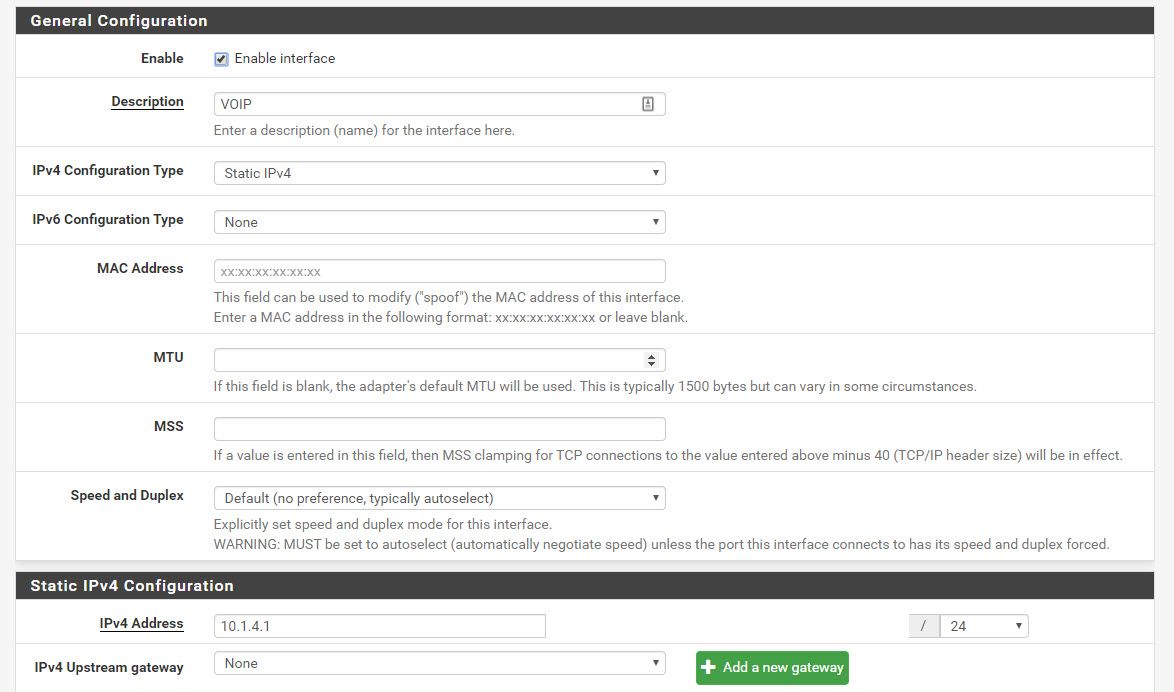
Subnet config:
Thank's
Maurizio
-
Hello
Show the output of the command
ipsec statusall con1000on the responder side
and check the traffic selectors -
Status of IKE charon daemon (strongSwan 5.7.1, FreeBSD 11.2-RELEASE-p10, amd64):
uptime: 5 days, since Dec 04 16:47:32 2019
worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 7
loaded plugins: charon unbound aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey ipseckey pem openssl fips-prf curve25519 xcbc cmac hmac curl attr kernel-pfkey kernel-pfroute resolve socket-default stroke vici updown eap-identity eap-sim eap-md5 eap-mschapv2 eap-dynamic eap-radius eap-tls eap-ttls eap-peap xauth-generic xauth-eap whitelist addrblock counters
Listening IP addresses:
213.174.170.18
172.16.4.1
10.1.4.1
Connections:
con1000: 213.174.170.18...213.209.215.212 IKEv1, dpddelay=10s
con1000: local: [213.174.170.18] uses pre-shared key authentication
con1000: remote: [213.209.215.212] uses pre-shared key authentication
con1000: child: 172.16.4.0/24|/0 === 172.16.3.0/24|/0 TUNNEL, dpdaction=restart
con1001: child: 172.16.4.0/24|/0 === 172.16.88.0/24|/0 TUNNEL, dpdaction=restart
con1002: child: 172.16.4.0/24|/0 === 10.1.0.0/24|/0 TUNNEL, dpdaction=restart
con1003: child: 172.16.4.0/24|/0 === 172.16.2.0/24|/0 TUNNEL, dpdaction=restart
con1004: child: 10.1.4.0/24|/0 === 10.1.0.0/24|/0 TUNNEL, dpdaction=restart
con1005: child: 10.1.4.0/24|/0 === 172.16.3.0/24|/0 TUNNEL, dpdaction=restart
Routed Connections:
con1000{910}: ROUTED, TUNNEL, reqid 1
con1000{910}: 172.16.4.0/24|/0 === 172.16.3.0/24|/0
Security Associations (1 up, 0 connecting):
con1000[24]: ESTABLISHED 91 minutes ago, 213.174.170.18[213.174.170.18]...213.209.215.212[213.209.215.212]
con1000[24]: IKEv1 SPIs: 9365cc70167be506_i* 8e46636af8669131_r, pre-shared key reauthentication in 6 hours
con1000[24]: IKE proposal: AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
con1000{1166}: REKEYED, TUNNEL, reqid 1, expires in 11 minutes
con1000{1166}: 172.16.4.0/24|/0 === 172.16.3.0/24|/0
con1000{1173}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: c251c669_i c56ee6db_o
con1000{1173}: AES_CBC_128/HMAC_SHA1_96, 25832 bytes_i (208 pkts, 0s ago), 144144 bytes_o (210 pkts, 0s ago), rekeying in 46 minutes
con1000{1173}: 172.16.4.0/24|/0 === 172.16.3.0/24|/0I don't know about "check the traffic selectors", sorry, let me know and I'll do.
Maurizio
-
Hi Konstanti,
have you seen the data ?
regards
Maurizio