Block Internet access on static ip address
-
I have DHCP pool with 192.168.1.100 - 192.168.1.254. I would like to provide limited internet access on that range.
I also have static range with 192.168.1.2 - 192.168.1.99. I would like to provide unrestricted access on that range.
My problem is that, unauthorized user can set there ip statically within the range 192.168.1.2 - 192.168.1.99 to have unrestricted access.
My question is, how can I block unauthorized ip set statically by unauthorized user even they use that unrestricted ip range?
I already tried the "Enable Static ARP entries" on DHCP server but it's not working. All dhcp clients cannot access the internet which is not my goal.
-
You can't. If pfSense supported filtering on MAC address, you might be able to do something, but it doesn't. There is nothing else to filter on. However, some managed switches can be configured to allow only authorized MACs.
-
@JKnott said in Block Internet access on static ip address:
You can't. If pfSense supported filtering on MAC address, you might be able to do something, but it doesn't. There is nothing else to filter on. However, some managed switches can be configured to allow only authorized MACs.
Is there any other ways to achieve this even using different equipment aside from pfsense? I'm just starting my network career so kindly guide me. Thanks.
-
Why would you not split these vlans? And control who can connected to the unrestricted vlan..
-
@johnpoz said in Block Internet access on static ip address:
Why would you not split these vlans? And control who can connected to the unrestricted vlan..
Because I only have simple setup. I have ISP-->PFsense-->Unmanaged Switches.
I can't set vlans on unamaged switches, especially on different departments
-
Filtering MAC's might help (a bit).
The facilities that does so, is the captive portal.
Then you could use password identification, or vouchers, or you go to the FreeRadius way using certs to be installed on the (each) user devices. That should 'non-wanted' users occupied for a while.Note that, in theory, you should make your LAN's accessible to non-wanted users.
@yanafig said in Block Internet access on static ip address:
different equipment aside from pfsense?
If these users are all Wifi bound, you could use an access point (starts around 20 $). These have their Wifi password, can often do some basic MAC filtering.
-
@yanafig said in Block Internet access on static ip address:
Because I only have simple setup
Sounds like a good reason to up your equipment to support what your wanting to do..
You mention using something other than pfsense - when all you need is switch(es) that support vlans.
You mention users changing IPs, you understand its childs play to change mac as well... When you want to control like you ask, you use different vlans.. Does not matter what the users IP is nor the mac..
But static arp has nothing to do with your firewall rules.. You can for sure set static arp to prevent a mac from using a different IP... The control of what IPs can do via firewall rules has nothing to do with that setting.
You understand this could also be accomplished with dumb switches, as long as your pfsense has more than 1 nic to use for lan side networks, and or a $30-40 smart switch to put between pfsense and the dumb switches. There are multiple ways to isolate your networks.
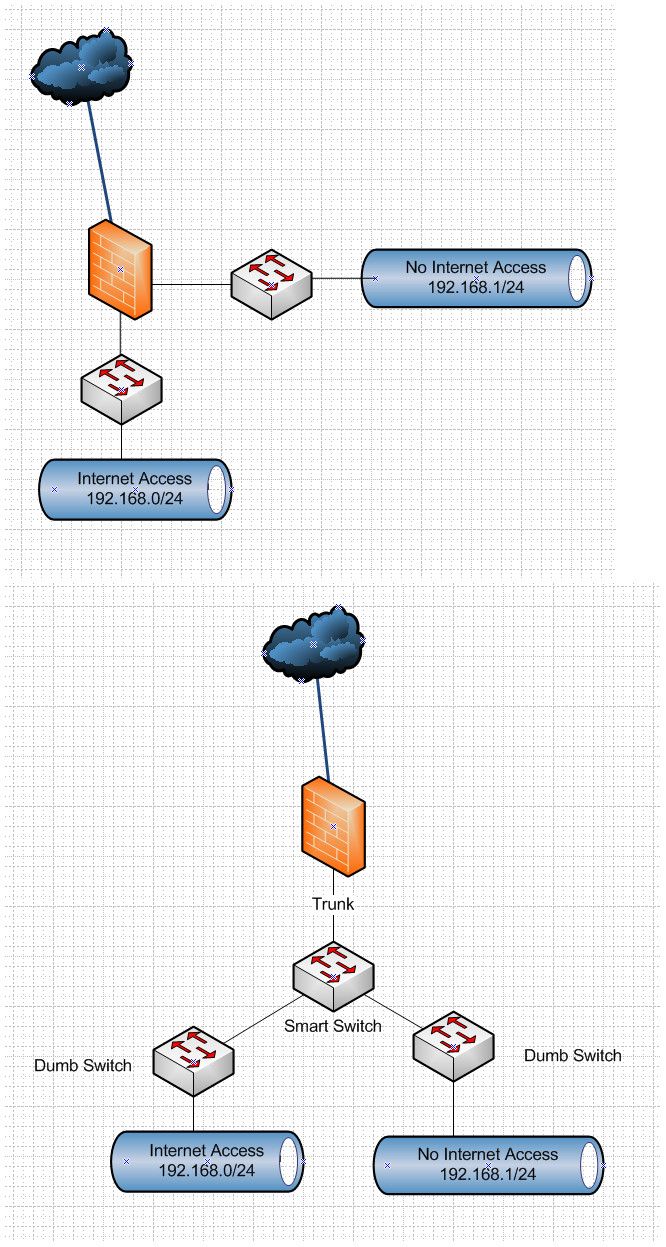
Even dumb wireless can be added to these now different networks be it vlans or actual physical separation.