block custom domains in pfblocker
-
Dude post up what your putting in the box... This is not rocket science... I showed you EXACTLY how to block something..
edit:
Here I just blocked anything.facebook.com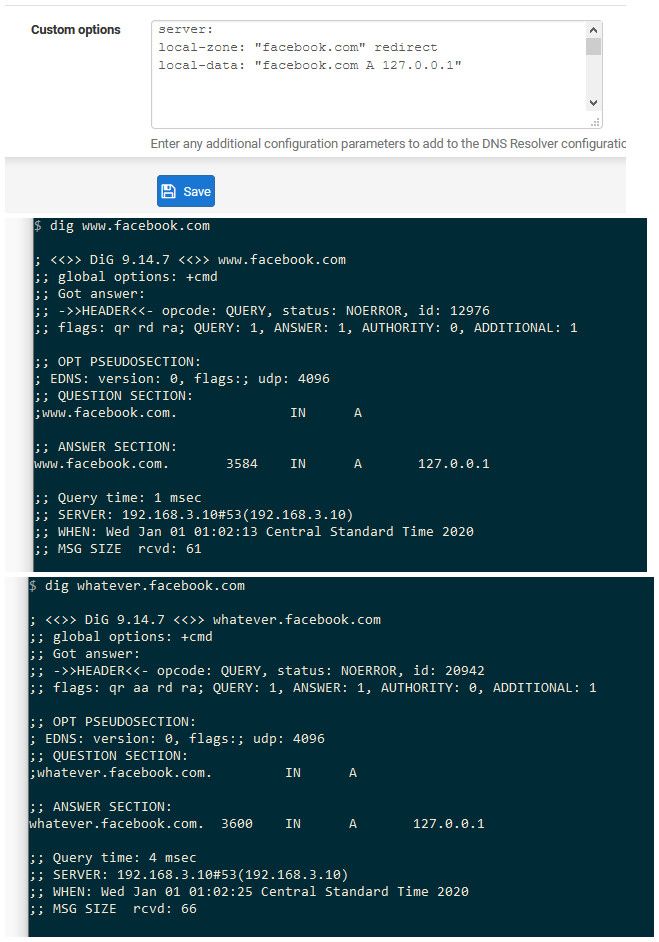
For any client on your network using pfsense for their dns.
-
If you want to do this through pfBlocker (non-dev version) as I showed above go to:
Firewall > pfBlockerNG > DNSBL > DNSBL-FeedsAdd a new feed configured as in my screenshot above. The Custom Blocklist field is there.
Steve
-
Folks I don't need the attitude here. I have spent hours reading/researching how to do this. With no firm consensus on the solution, I keep trying them all and then I come here.
So how does your response relate to my question of the contents of my Custom Options - "server:include: /var/unbound/pfb_dnsbl.*conf"?
Help or more attitude?
Do I add your lines to a "xyz.conf" file or just enter them in the custom box below whats there?
-
There are multiple ways to skin this cat... You can do it in pfblocker directly, you could do it in the custom option box for unbound. Or sure you could hand edit a conf file - but if you hand edit some conf unless your loading that extra conf you created into unbound via the option box and directly editing the normal unbound.conf then it would get overwritten.
edit: removed my remarks after reading them - they had too much attitude in them... And just don't feel like dealing with this sort of nonsense so early in the year.
Good luck!
-
@johnpoz
Thanks, John. I've been around this game for a LONG time and everytime I have to learn a new firewall, there always seems to be some head-banging that I have to go through.I agree that editing a conf file will not work as they will get overwritten. So I'm looking at using the custom option box. So first, the only custom option I find is under "DNS Resolver/General Settings" will lines suggested:
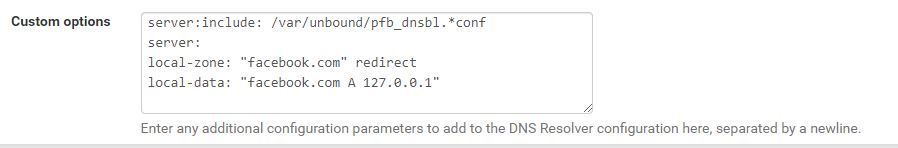
But that then produces this:
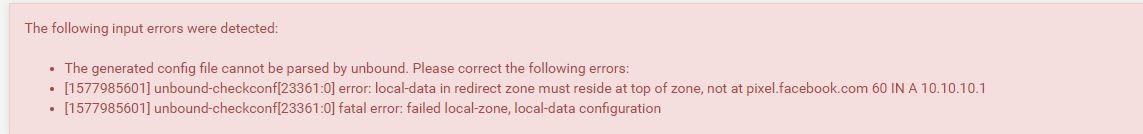
So perhaps I don't know where the "control box of unbound" is as was suggested earlier. Am I even in the right neighborhood?
Thanks for your patience.
-
Tom, try this:
server:
local-zone: "facebook.com" redirect
local-data: "facebook.com A 127.0.0.1"
include: /var/unbound/pfb_dnsbl.*conf -
@GregBinSD
Same error..... -
Sorry, Tom. Try one more thing.
Looking above a little, johnpoz pasted just these lines into the Customs options box, leaving out the pfblocker line:
server:
local-zone: "facebook.com" redirect
local-data: "facebook.com A 127.0.0.1"So, clear out the Customs options box and paste in the 3 lines above, like johnpoz did.
BTW, at Windows cmd prompt, clear the DNS cache by typing:
ipconfig /flushdns...and clear your browser's cache of history and files, as well, before testing your results.
Greg
-
But isn't the pfblocker line responsible for loading the blocklist feeds?
-
Tom, johnpoz knows for sure, but from what I have gathered, the DNS used by pfSense is called "unbound", and it can be seen running in the background if you go to Status/Services. Unbound can read those 3 lines without the help of pfBlockerNG. In fact, I am experimenting with a TLS encrypted DNS service, without using pfBlockerNG. The developer had me put 8 lines into the Custom options box, along with setting some parameters giving me an account on his web interface. None of those lines reference pfb.
-
I would add them through pfBlocker as I outlined above. But pfBlocker just adds it's own additional config there so you can add it manually to Unbound if you want.
If the pfb_dnsbl include file already has a zone defined for facebook.com you might be conflicting. Try adding something completely different there.
Steve
-
@TopperTom Hey Tom, I made an account just to answer your question here, as you're very very close to having this correct.
You can put the include for your conf file at the bottom of the box and any server includes you need at the top. I run this exact thing on my box while I'm experimenting with blocking Youtube ads. Here's what my custom options look like:
server: local-zone: "manifest.googlevideo.com" redirect local-data: "manifest.googlevideo.com A 10.10.10.1" include: /var/unbound/pfb_dnsbl.*confI hope this helps relieve the frustrations you've had with this so far.
-
Yes, that should work as long as
manifest.googlevideo.comis not defined as a local-zone in pfb_dnsbl.conf already. I think that was the problem previously. Once we removed the two server entries.Steve
-
@stephenw10 said in block custom domains in pfblocker:
Yes, that should work as long as
manifest.googlevideo.comis not defined as a local-zone in pfb_dnsbl.conf already. I thing that was the problem previously. Once we removed the two server entries.Steve
Ah, that makes sense. After reading back through the thread again, I see that GregBinSD made the same recommendation that I did and Tom still had problems with that. In this use case, I'd have to echo what others have already said about just making a custom feed and putting any entries needed in there.
-
S SteveITS referenced this topic on
-
 L LPD7 referenced this topic on
L LPD7 referenced this topic on
-
This is an old topic but it's the second search result. In the current (ex-devel, now same as -devel) version of pfBlockerNG it is under:
- Firewall/pfBlockerNG/DNSBL/DNSBL Groups
- edit an existing group or create a new group
- expand DNSBL Custom_List towards the bottom (below Advanced Tuneables)
- add hostnames to the large text box
Save. If you created a new group remember to set Action=Unbound (instead of Disabled). Run a pfB Update.
-
@SteveITS I'm trying to use StevenBlack's list. How would I link to it's online location as opposed to pasting in a vast list of url's?
I pasted https://raw.githubusercontent.com/StevenBlack/hosts/master/alternates/porn/hosts into the source filed but it complains it needs a header - any idea what it is aksing for?
The entries in the list are in the format of0.0.0.0 ck.getcookiestxt.com
0.0.0.0 eu1.clevertap-prod.com
0.0.0.0 wizhumpgyros.com
0.0.0.0 coccyxwickimp.cometc
Many thanks
-
Just add a new feed and enter the URL.
-
It's possible to create a blocklist only to 1 host?
Lets say: I want to block youtube to host 192.168.0.10.
What i've tried:
- Add custom "DNSBL Group"
- Add youtube.com in DNSBL Custom_List option
- Save and Reload
- Add LAN Firewall Rule to block the custom list in destination option. In source option add host IP (192.168.0.10).
But it doesn't work.
-
Right you can't use DNS based lists in firewall rules. Potentially you could create a custom view in Unbound for just that host to prevent it resolving youtube. That's not in pfBlocker though, you should open a new thread for that if you choose to try it.
-
@guile said in block custom domains in pfblocker:
Add LAN Firewall Rule to block the custom list in destination option.
A firewall rule is build with source and destination IP addresses or networks, source and destinations port.
The thing is, youtube.com doesn't have 'one' IP, but several, or worse , a lot of IP addresses.
Even if you were able to get them all, that list would be valid for a small amount of time - a couple of minutes.Let's test :
[25.03-BETA][root@pfSense.bhf.tld]/root: host www.youtube.com www.youtube.com is an alias for youtube-ui.l.google.com. youtube-ui.l.google.com has address 172.217.18.206 youtube-ui.l.google.com has address 142.250.74.238 youtube-ui.l.google.com has address 142.250.75.238 youtube-ui.l.google.com has address 216.58.214.174 youtube-ui.l.google.com has address 172.217.20.174 youtube-ui.l.google.com has address 172.217.20.206 youtube-ui.l.google.com has address 216.58.215.46 youtube-ui.l.google.com has address 216.58.213.78 youtube-ui.l.google.com has address 142.250.179.78 youtube-ui.l.google.com has address 142.250.179.110 youtube-ui.l.google.com has address 142.250.178.142 youtube-ui.l.google.com has address 142.250.201.174 youtube-ui.l.google.com has IPv6 address 2a00:1450:4007:80c::200e youtube-ui.l.google.com has IPv6 address 2a00:1450:4007:810::200e youtube-ui.l.google.com has IPv6 address 2a00:1450:4007:80d::200e youtube-ui.l.google.com has IPv6 address 2a00:1450:4007:80e::200eSo, throw "www.youtube.com" in a Alias :
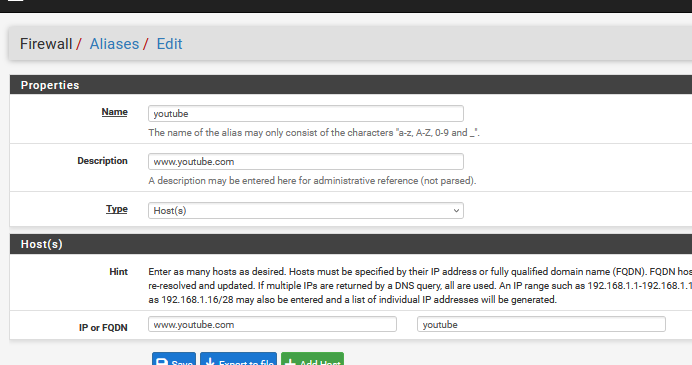
and now, go check this Alias :
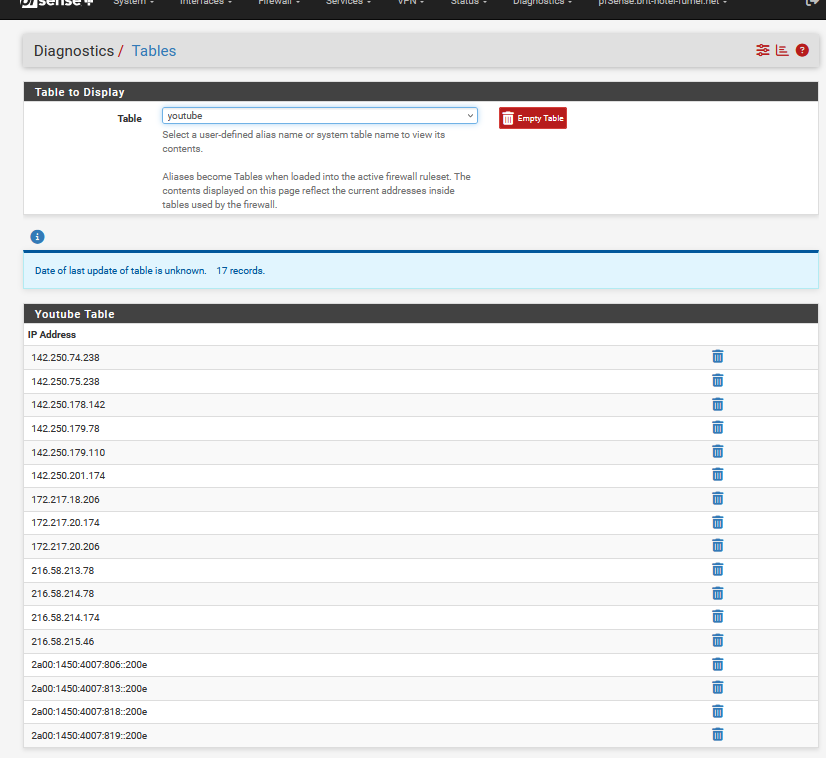
and by magic, the Alias get filled with the actual IPs. Even better : the alias will get refreshed this IP list every 300 seconds or 5 minutes.
This works pretty well, and probably enough so the owner of "192.168.0.10" stops trying to visit "www.youtube.com".
Now, all you have to do is : create a block firewall rule on your LAN, with the source IP set to the IP of the victim : 192.168.0.10 - and a destination set the name of the alias : "youtube". Ports and other are not important = 'any'. The protocol should be set to TCP.
save the rule, and have a casual visit to the owner of 192.168.0.10 and ask if "all is well ?" ;) If you don't, he'll be visiting you shortly after.Be aware : if this owner knows how to look things up, he'll find out that changing his IP to "192.168.0.11" will by pass your firewall rule ...
( and randomize its MAC, etc etc - and eventually just not using your (LAN) network anymore )