Providing NAT to a LAN behind the LAN interface
-
drawing would be great.
Also you might need to adjust the rules on your interface this downstream network is going to hit. is this downstream network via an actual transit network... If its routed through a network you have hosts on, you could have a asymmetrical routing problem
-
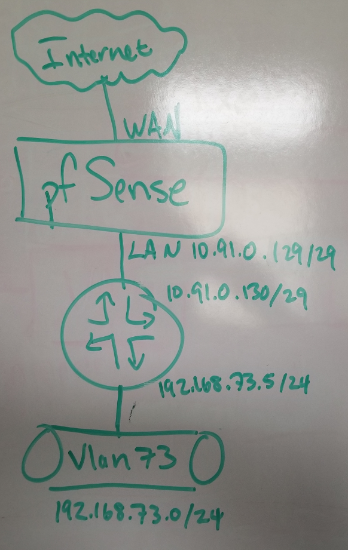 Drawing
DrawingI quickly whiteboarded this to get you a quick answer on the drawing.
It is not routed through a transit network, unless I am wrong with how I define a transit network. As you can see in the drawing, these two local networks sit on 1 router.
Not sure where the asymmetrical routing would come in as these networks only have a single path.
Thanks for the prompt reply.
-
Do you have hosts on this 10.91.0.128/29 network that your wanting to talk to or from your downstream network?
What rules do you have on the .129 interface?
-
Only hosts are pfSense and the router.
I am still getting the hang of pfSense, what rules are you referring to?
Under Firewall>Rules>LAN I have a list of addresses that can access 22 and 443 from both 10.91.0.128/29 and the 192.168.73.0/24 networks. Along with a block on 22 and 443 from any. Other rules I believe are the default rules on the firewall, allow LAN to any and allow LAN IPv6 to any.
Firewall>Rules>LAN:
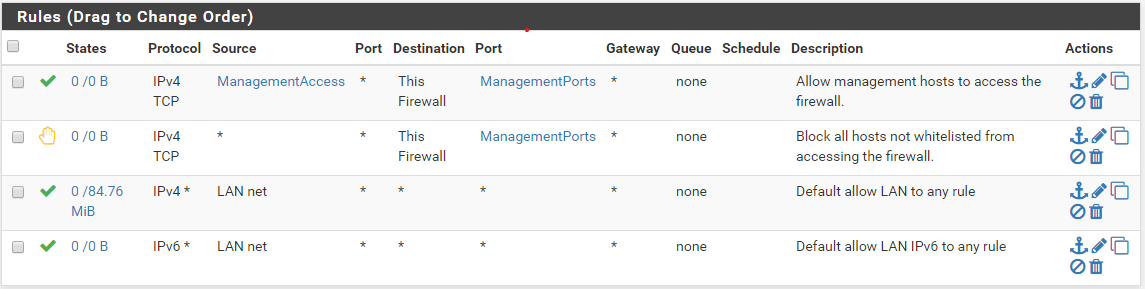 spoiler
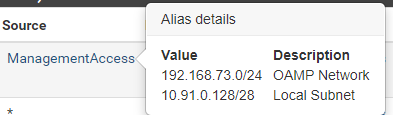
spoilerManagementAccess:
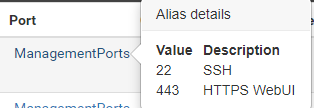
ManagementPorts:
-
That is the rules for the 10.91.0.129 interface? Your lan in pfsense"
So while those rules would allow access to your management ports from your downstream 192.168.73/24 network your other rules do not allow your downstream to go anywhere - only the lan net which is your /29 only.
-
Thanks. That has been driving me crazy all day.
Another question, you seem surprised by my seemingly lack of rules on the LAN, why? (Or I am massively mis-reading what your first line is to mean there.)
-
Not surprised.. just wanted to validate you were showing the correct interface.
-
I see what you mean, terrible capture on my part.
Thanks again for the quick resolution!
-
glad you got it sorted.. Just remember in such a setup if you put any sort of devices/hosts on that /29 you would need to do host routing on them... Or your going to run into asymmetrical routing.
-
This is a test bed before I move this into a more production environment. I will probably end up with the pfSense to router connection being a smaller subnet to completely avoid that scenario.
Curious though, where would the asymmetrical routing come from? This is my first major dive into this sort of networking detail and just want to know what the downfall of that would be.
Thanks.
-
So if host say on .131 wants to talk to 73.x he hits pfsense as his gateway... Which pfsense sends to .130, but return traffic will just go straight to .131 So now you are asymmetrical
If 73.x is wanting to talk to say .131 on your /29 no need to send to pfsense, so pfsense never see syn, and the syn,ack the .131 box would send back via pfsense would be out of state and pfsense would not allow the traffic, etc..
You would have to be natting on your downstream, or do host routing to prevent such things.. Its best to just use it as pure transit and not put any hosts on it..