Multi Lan segments isolated from each other
-
So about a month ago I setup Pfsense and assumed I got it right, well running nmap last night revealed that my lan segments are not isolated from each other. I do not have a switch involved but may add that in the future if I add more devices (most likely a POE sw).
Current setup:
WAN - built in PC NIC
cheap USB adaptor for crap network.
4port NIC- LAN (one wired PC)
- Wireless (Ubiquiti AP)
- Voip phone
- POE Security camera POE injector (camera is not working right now but will get to that at a later date)
So I followed the YT video from Lawrance systems for system setup https://www.youtube.com/watch?v=9kSZ1oM-4ZM except that I wanted to segment each network from the other (not just keep one network seperate). I could not really care about segmenting LAN and wifi, but wanted to keep the sec cam, voip phone and crap net isolated. I went through the video again and it appears that I have it all right but still I can ping each segment. I am guessing my problem lies in that I am trying to follow his rule advice but instead of a simple 2 network setup I have 5 and somplace screwed it up major. I may end up deleting everything and starting over with just just 2 segments to find my error and then add the rest in.
Is it better to do vlans for each segment or my current setup?
Since I have 5 segments is it better to setup the isolation using the "inverted" allow rule or just setup a block right away? I was think of changing to block, but then if I were to add another segment It would take more work to add in more rules to keep that isolated from the other networks again. Any suggestions are appreciated. -
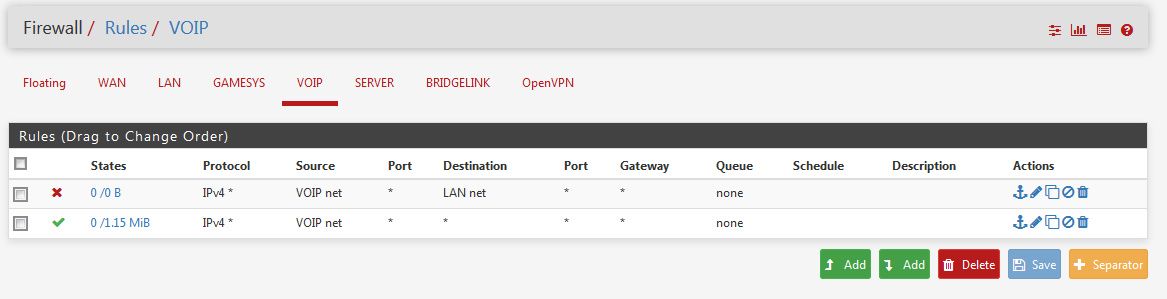
Make firewall rules on the interfaces blocking "VOIP net" from LAN net. And another from VOIP to WIFI.
rinse and repeat for any interface that you want to keep away from your LAN interfaces.
-
Yes, adding block rules for the traffic you don't want and then a pass rule is the simplest to read and understand.
You can use an inverted rule but it can pass traffic unintentionally. So pass traffic to !local_subnets where local_subnets is a alias of the subnets on each interface or a supernet containing them. You usually need to also pass traffic to the interfaces itself so clients get access to dns and ntp.
Steve
-
Thank you.
I think I must have tried to get too cute with some of the rules or something. I disabled all of the "everything but" rules and did straight block rules instead and it works now. Or should I say ping no longer works across segments. A simple copy of one rule and it did not take too much time to get it working.
I wonder if one of the rules that I had allowed for open communication and I simply missed it, or what I had wrong.
Thanks again guys. I have really been looking forward to getting this machine setup for quite some time and now that I have the hardware it is a fun and challenging experience. Now the next step is to get snort/pfblocker up and running.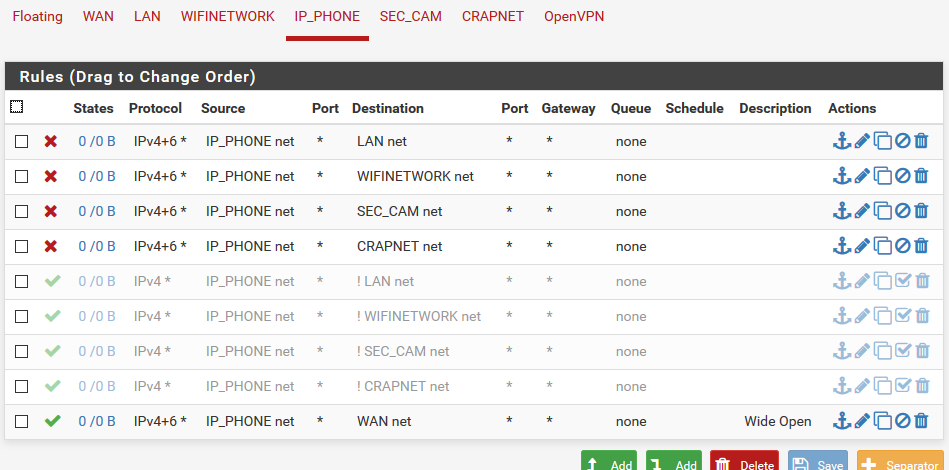
-
Yeah that's where inverted rules can bite you. !LAN net or !WIFI net is effectively everywhere.

Your 'Wide Open' rule is actually only to the WAN subnet which is probably only small subnet with your public IP in it. You probably want destination 'any' there to allow traffic to any external IP.
Steve