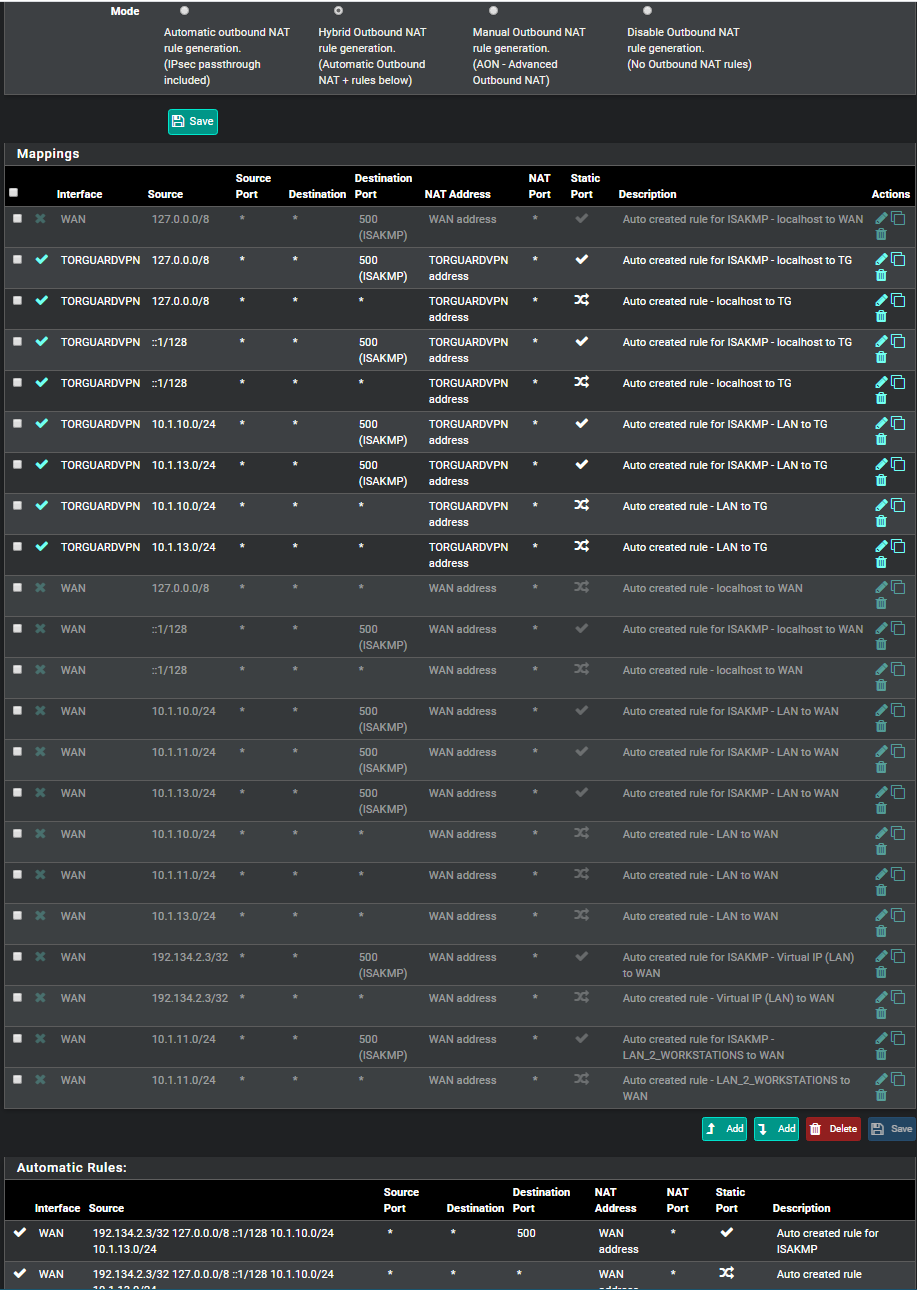
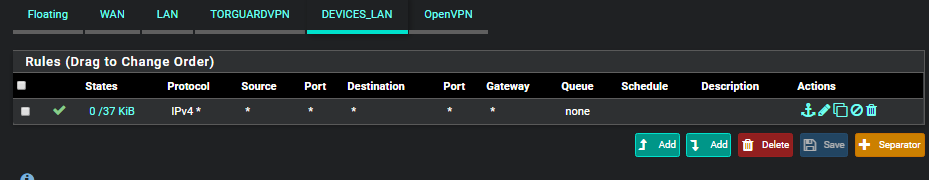
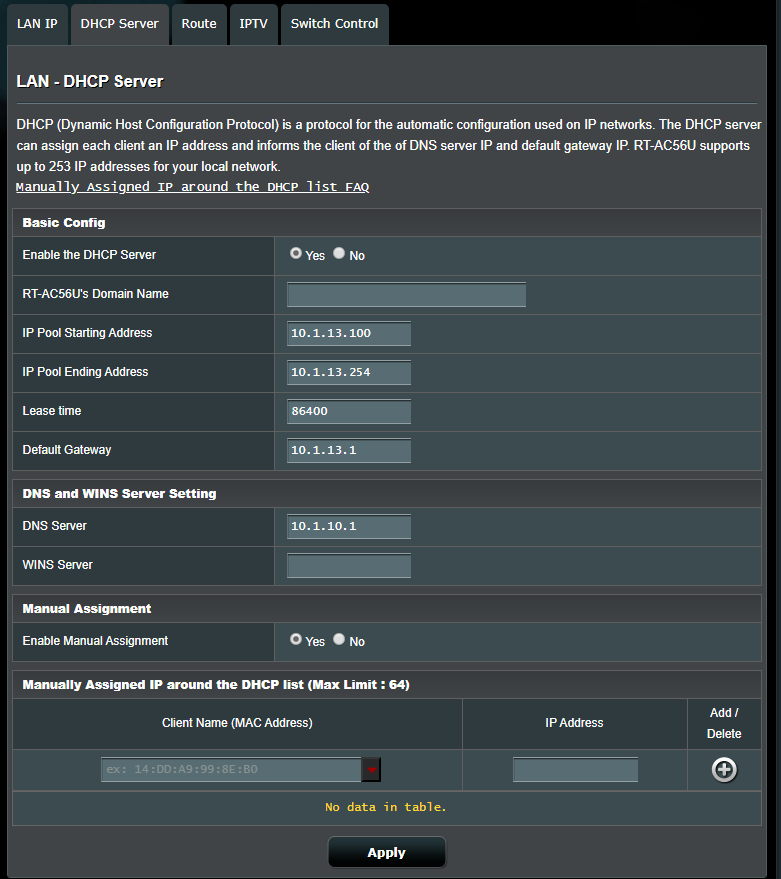
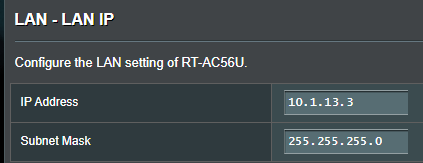
No Internet from WIFI connection on Router from 2nd LAN subnet
-
Hmm, yet no state on DEVICES_LAN.... the client was definitely trying to connect at that point?
-
@stephenw10 Yeet! Sorry, I mis-understood.
Nothing was trying to connect at that moment I did the filter.
I re-did it when my phone was trying to connect to wifi:
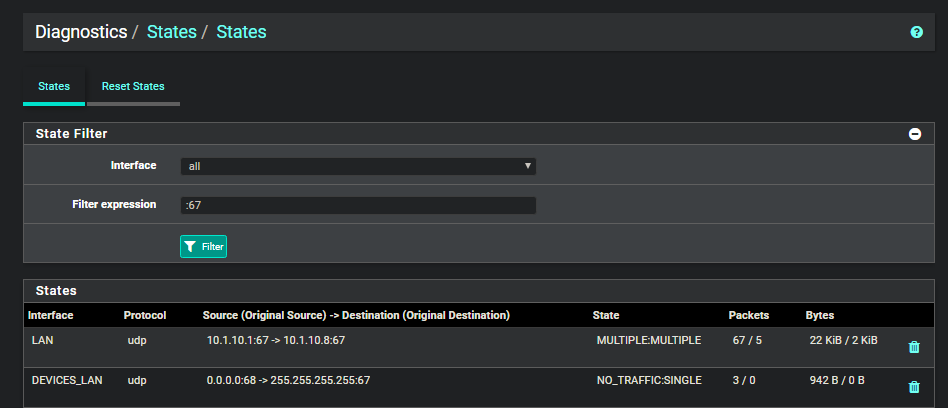
-
@stephenw10 Here is one of my laptop, directly connected to the asus router with ethernet:
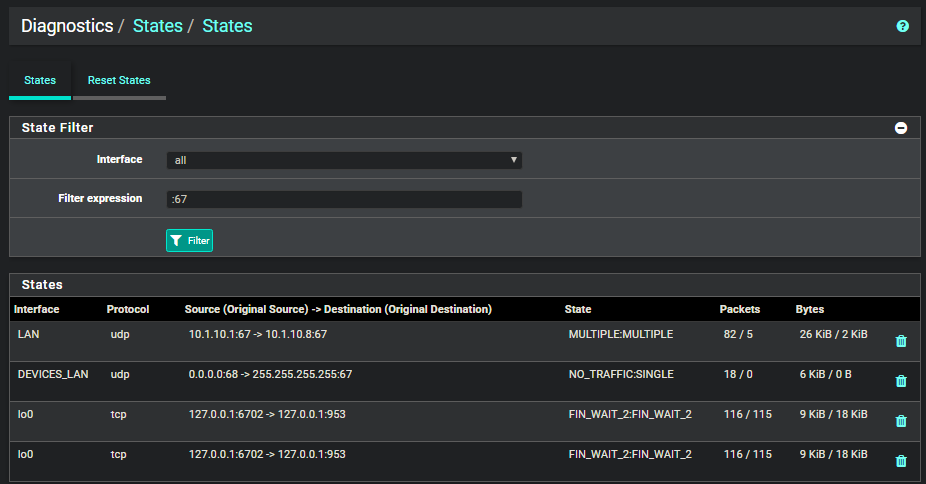
-
Hmm, that looks correct in terms of open states. But nothing going back to the client. Anything logged on the server?
Might have to pcap on LAN filtered by the server IP to see if the requests are actually going to it.
Steve
-
:(
Here is packet capture that I did on pfSense when my phone was trying to connect to wifi:
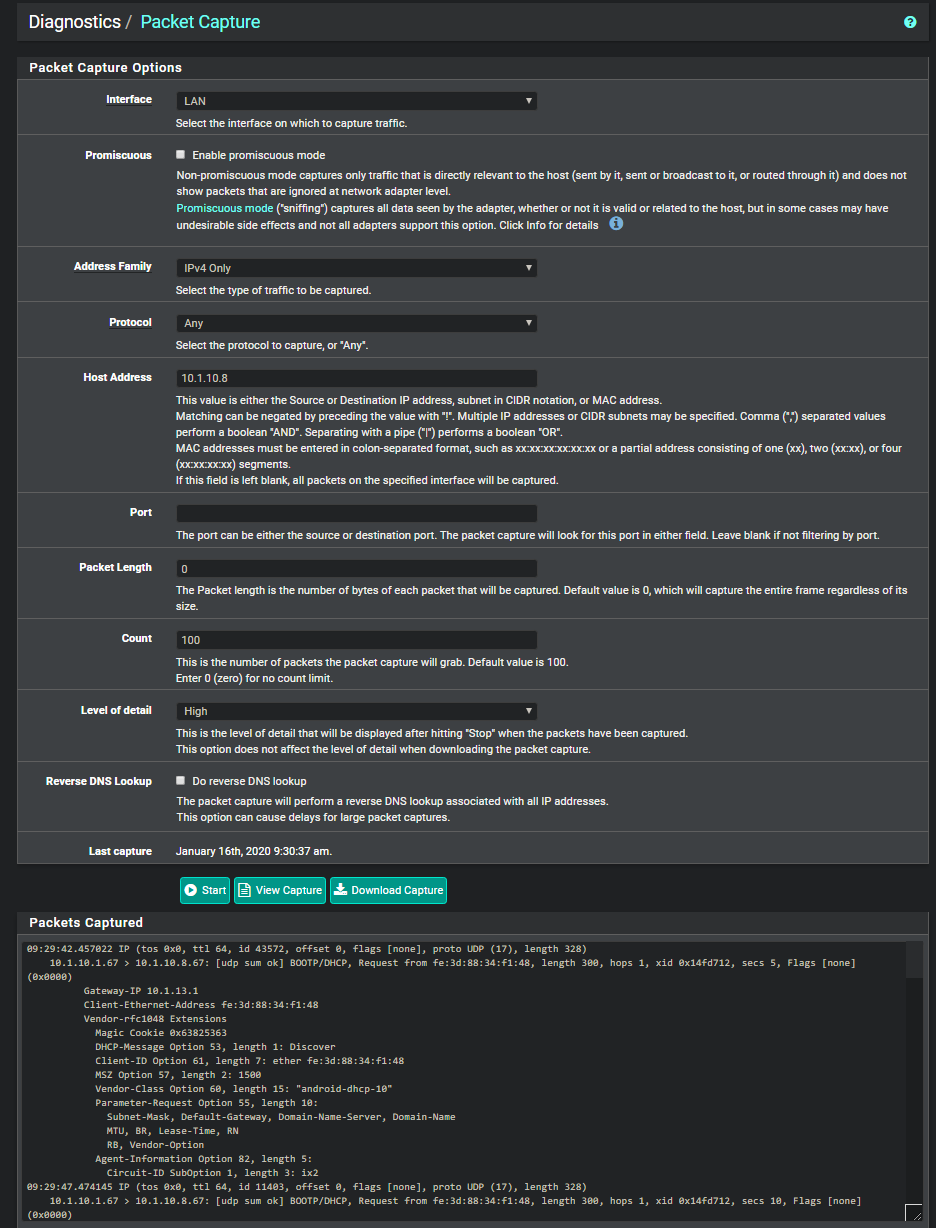
09:29:42.457022 IP (tos 0x0, ttl 64, id 43572, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0x14fd712, secs 5, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2
09:29:47.474145 IP (tos 0x0, ttl 64, id 11403, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0x14fd712, secs 10, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2
09:29:47.635729 IP (tos 0x0, ttl 128, id 5587, offset 0, flags [none], proto UDP (17), length 82)
10.1.10.8.58751 > 10.1.10.1.53: [udp sum ok] 55300+ [1au] A? eus-oi-ods-b.cloudapp.net. ar: . OPT UDPsize=4000 (54)
09:29:47.650479 IP (tos 0x0, ttl 64, id 4119, offset 0, flags [none], proto UDP (17), length 98)
10.1.10.1.53 > 10.1.10.8.58751: [udp sum ok] 55300 q: A? eus-oi-ods-b.cloudapp.net. 1/0/1 eus-oi-ods-b.cloudapp.net. A 40.79.154.85 ar: . OPT UDPsize=4096 (70)
09:29:55.696010 IP (tos 0x0, ttl 64, id 26722, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0x14fd712, secs 18, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2
09:30:12.750834 IP (tos 0x0, ttl 64, id 41397, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0x14fd712, secs 35, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2
09:30:16.207646 IP (tos 0x0, ttl 64, id 38410, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0xa26f2a53, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2
09:30:21.213556 IP (tos 0x0, ttl 64, id 60954, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0xa26f2a53, secs 5, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2
09:30:25.183289 IP (tos 0x0, ttl 64, id 56349, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0xa26f2a53, secs 8, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2
09:30:32.659175 IP (tos 0x0, ttl 64, id 38685, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.8.67: [udp sum ok] BOOTP/DHCP, Request from fe:3d:88:34:f1:48, length 300, hops 1, xid 0xa26f2a53, secs 16, Flags [none] (0x0000)
Gateway-IP 10.1.13.1
Client-Ethernet-Address fe:3d:88:34:f1:48
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
Client-ID Option 61, length 7: ether fe:3d:88:34:f1:48
MSZ Option 57, length 2: 1500
Vendor-Class Option 60, length 15: "android-dhcp-10"
Parameter-Request Option 55, length 10:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Domain-Name
MTU, BR, Lease-Time, RN
RB, Vendor-Option
Agent-Information Option 82, length 5:
Circuit-ID SubOption 1, length 3: ix2 -
Ok so no replies from the DHCP server back to the client. Either the server is not able to respond or it's refusing to respond.
Steve
-
@stephenw10 Interesting, not sure what the issue is but I guess i'll have to do some digging..
Thank you for your help! I will update when/if I find anything.
-
@techgeek055 Wow, I found the issue. I removed my default gateway on the NIC interface on my Windows DHCP server a while back. I did this so that it had no internet connection for security.
Once I added the default gateway back to point to my pfsense box , I am getting IP from DHCP on my other subnet.
Do you know what would be the "proper" way of taking the server off the internet while not breaking DHCP for other subnets?
-
Ah, nice. So it had no route back to 10.1.13.0/24.
You should be able to just add that as a permanent route on the Windows server rather than adding a default route.
So add 10.1.13.0/24 via 10.1.10.1.
It will still have no default route so no way to reach external IPs.Or you could just block that traffic in pfSense.
Steve
-
Sweet, that worked! I opened command prompt on the windows server and entered:
route add /p 10.1.13.0 mask 255.255.255.0 10.1.10.1
Thank you sooooooooo much! You guys are so awesome.
Now that I fixed this issue, I can attempt VLANs again! Yahooo!
-
I would've gone the firewall route as a safeguard to any future design changes and/or misconfigurations. The firewall route would also generate records of all internet attempts by the server for better auditing/troubleshooting. While a persistent route on the server does accomplish your short term goal... it just doesn't scale well.
As a reminder to yourself, I would definitely document somewhere the fact that a persistent route exists on the server... or at some point...6 months, 1 year, 2 years, etc from now... you'll forget and it may come back to haunt you as your network design evolves and your needs/priorities change.
-
That's a good point. On second thought, i think I may go the firewall route. I've already documented the route for future reference!
Thank you very much for your assistance in this frustrating issue I had!
Till we meet again!
-
Yup, I would go with firewall rules there too.
Obscure routing tables on each host becomes difficult to track very quickly. The firewall is the natural place to check when traffic is not flowing as expected. It will almost certainly save you time in the long run.
Steve
-
@stephenw10 kk, that solves it. I'll go firewall route! Thanks!