Sonos speakers and applications on different subnets (VLAN's)
-
If you're running 2.4.5 or 2.5 snapshots (or are able to) you might want to test the new pimd package to make sure it can be configured for this role.
Steve
-
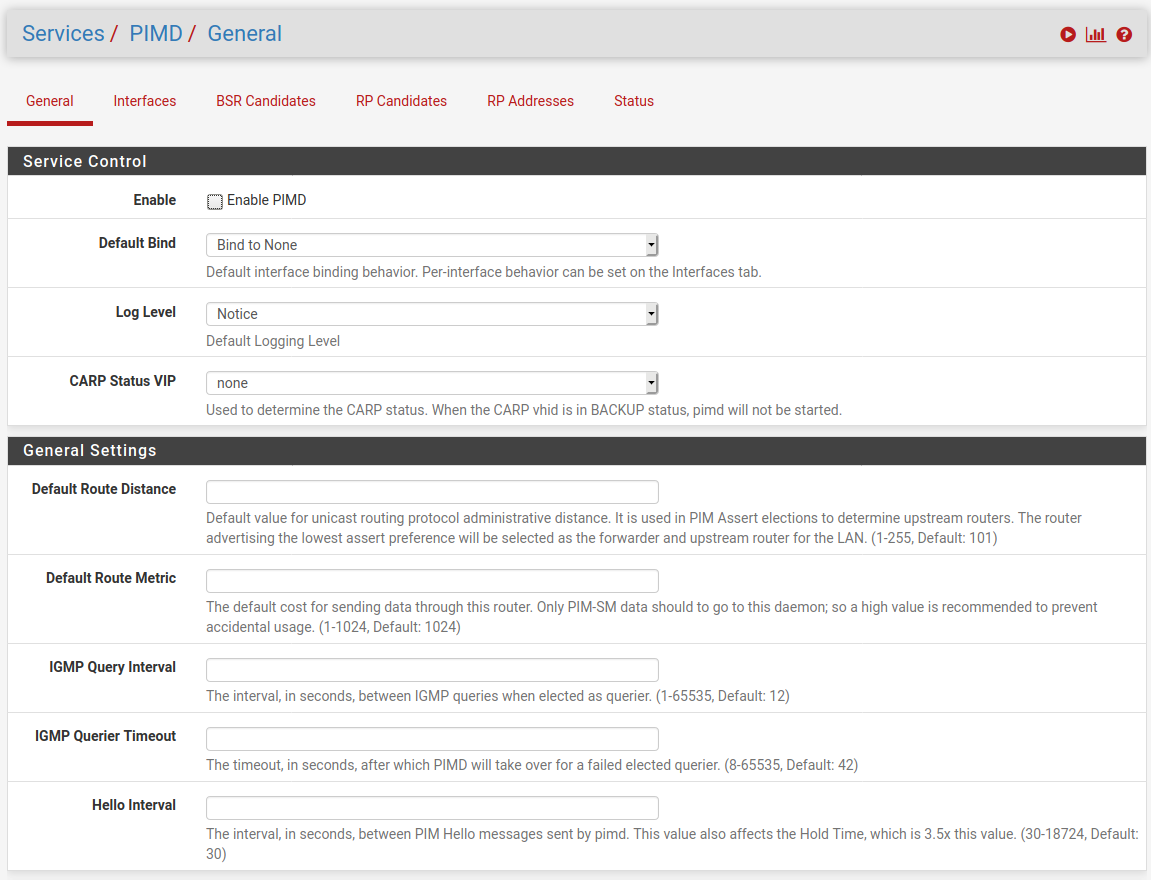
I'll just say, since I just spent a while scratching my head, that you probably want to leave the Default Bind value at 'Bind to None' and then enable the interfaces you want set as 'Always Bind'.
That results in a conf file that looks like:
/var/etc/pimd/pimd.conf################################################################### # This file was created by an automatic configuration generator. # # The contents of this file will be overwritten without warning! # ################################################################### phyint igb2 enable phyint igb0 enableSteve
-
@netgate and @jimp Great that you have added PIMD, Kudos and I have adapted my how to and removed the warning that it wasn't an official package as it is now, and available for users on current 2.5.0 and 2.4.5 snapshots, so anyone download it using the package manager in pfSense and set it up.
-
@stephenw10 Sorry I can't test it, as I have no 2.4.5 or 2.5 operating at the moment. only 2.4.4 . Btw "Bind to none" is different from the default config file, as that one enables all the interfaces by default, so you had to disable the ones that should not be used. This approach (Bind to none by default) seems more logical

-
Yeah, it's not the pimd default but seems better to me. You have to explicitly define the interfaces you want it enabled on.
Steve
-
I enabled pimd for 2.4.4-p3 as well now, so anyone can install it.
As for the default behavior, I deliberately chose the more secure mode. Less room for error there, and I wanted to ensure that a user had to explicitly choose to activate it.
Makes it slightly more difficult to configure but it's also more difficult to create a broken or insecure config.
-
@jimp You made my day! Thank you!
Do you have tips on how to confiure it? The only thing I do manually is to do disable non sonos interfaces by doing this:
phyint mvneta0 disable phyint mvneta1 disable phyint mvneta2 disable phyint ovpnc2 disable phyint ovpnc4 disable phyint mvneta1.1002 disable phyint mvneta1.1004 disable phyint mvneta1.1005 disable phyint mvneta1.99 disableHow does this translate to the new plugin? I understand I have to go the other way - enable only the interfaces I need. How do i do that? And anything else? What about Avahi? Do we still need it?
-
Just install it, enable it, add the interfaces you want it on with binding set to always.
If you really want to blacklist interfaces instead of whitelist, then set the default binding on the general tab to bind to all, then add the interfaces you list there set to never bind.
-
@jimp Going to kick it around now! .... and avahi? . Is it still needed to make multicasting work? Or pimd is the one multicast plugin to rule them all ?
-
pimd does not replace Avahi
-
So I installed and enabled it. I set the default bind to "bind to none" and only enabled the interfaces I need with "always bind" I removed the previous pimd I installed manually. I then reboot my machine.
I see pimd service running. I also see only the two interfaces I enabled in the pimd.conf file at /var/etc/pimd/pimd.conf.
But my sonos app is not working anymore . Also I don't see pimd when I run a "top" command in diagnostics. I used to see it listed there in the output. Did I miss anything?
EDIT: Sonos app started working. Took awhile - maybe 5 minutes. But everything started working. I will monitor it for awhile and report if something comes up.
-
If you removed the pimd you installed manually after installing the package, it might have taken out something needed by the new pimd.
In case others are in the same situation, to be safe you should uninstall the third-party repo copy before installing the new one.
You may want to uninstall and then install the package again (don't use the reinstall link) to make sure that all of the components are there.
-
Sonos worked for me prior to installing pimd but the iOS app would always fail to find the system then I'd turn wifi off and back on that would allow the app to find my Sonos speakers. Thought I'd give pimd a try to see if it resolves the issue, wifi clients are on VLAN 192.168.20.1/24 and Sonos is on 192.168.50.1/24, no change in behaviour. I opened up IGMP on VLAN50:
Virtual Interface Table ====================================================== Vif Local Address Subnet Thresh Flags Neighbors --- --------------- ------------------ ------ --------- ----------------- 1 192.168.1.1 192.168.1 1 DISABLED 2 192.168.0.3 192.168 1 DISABLED 3 192.168.10.1 192.168.10 1 DISABLED 4 192.168.20.1 192.168.20 1 DR NO-NBR 5 192.168.30.1 192.168.30 1 DISABLED 6 192.168.50.1 192.168.50 1 DR NO-NBR 7 10.1.90.1 10.1.90/24 1 DISABLED 8 10.1.70.1 10.1.70/24 1 DISABLED 9 192.168.20.1 register_vif0 1 Vif SSM Group Sources Multicast Routing Table ====================================================== --------------------------------- (*,*,G) ------------------------------------ Number of Groups: 0 Number of Cache MIRRORs: 0 ------------------------------------------------------------------------------ -
Do you have IGMPproxy enabled also? Disable that if so. It's hard to see how it would have worked otherwise.
Steve
-
@stephenw10 no, IGMP proxy is off.
edit: this is my iPhone Sonos App behaviour, prior to and with pimd. If the Sonos App isn't in background memory, the first time it opens it'll spend some time scanning then fail. If I then turn wifi off and back on again it'll detect my Sonos system.
There is something happening during that initial wifi connection that allows the app to locate the system. Once it has found it, as long as the app runs in the background it'll remain connected to my Sonos system.
https://imgur.com/uvcZyeD
-
@edz Same issue here, but this happens since a Sonos App update some months ago (also with pimd installed manually). Looks like the app is not storing the requried information anymore, like on the Mac app, and searching everytime again starting up.
edit: https://en.community.sonos.com/setting-up-sonos-228990/vlan-issue-on-unifi-network-after-10-6-update-on-ios-6833871
-
Thought I would share my experience manually installing pimd as well as the new pfSense pimd package. First, a great big shout out of thanks to Qinn for his work on this!
A brief description of my setup: I have three separate physical interfaces (not VLANS) labeled LAN, WIFI and SONOS . They are, of course, all on separate subnets. My desktop clients are all wired to my LAN interface. My wireless mobile clients (all Apple devices) connect through an access point on my WIFI interface and all my Sonos devices are connected to the SONOS interface. All my desktop clients and Sonos devices have statically assigned IP's. My mobile devices all receive DHCP leases.
When I installed pimd manually as initially described by Qinn, I eventually managed to have all of my clients on the wired LAN interface and the wireless WIFI interface recognize my Sonos devices on the SONOS interface. After extensive testing, I determined that I needed to enable "Allow packets with IP options to pass" on the SONOS interface but not the other two interfaces. My wireless mobile devices are all iphones and ipads. I have no android devices. Although I am certainly no expert, this makes sense to me as I would expect the source of such packets to be coming from my Sonos devices and thus would be filtered by the SONOS interface.
I also experienced that the pimd.conf file gets deleted on reboot as initially descibed by vacquah. The pimd daemon, however, is not deleted and is still present. The service cannot restart because pimd.conf is not present. I discovered that if I kept a copy of my edited configuration file in /usr/local/etc that it was not deleted. I could just copy it back to /var/etc and restart the service. Unlike Qinn, I could NOT turn off the service as he described being able to do and still have my Sonos devices be discovered. Every time I attempted to do so made my Sonos network undiscoverable. In my setup, pimd has to be a continually running service. I have given alot of thought to this and have wondered if there may be some differences in the discovery process of the different Sonos devices. What got me to thinking about this was a message that popped up on my iphone when I opened the Sonos app after reinstalling it. It stated "Sonos would like to use Bluetooth. Sonos uses Bluetooth to find nearby speakers". Turns out, I am not using any Sonos speakers. My Sonos devices consist of a single bridge (ZP90) and four amps (ZP120) which do not use Bluetooth. The ZP90 bridge is directly wired to the SONOS interface and the four ZP120 amps are wirelessly connected over Sonos's proprietary network. My knowledge of such matters is very limited but could Bluetooth be figuring into the discovery process and explain some of the different experiences which have been described?
Although I experienced success manually installing pimd, I have not had the same success when I tried installing the recent pfSense pimd package. I tried using both "bind to all" under the general tab as well as the default "bind to none" and then selectively binding my three interfaces under the interfaces tab without any success. All other options I left as default. Neither my wired desktop or my wireless devices could discover my Sonos system . I tried using both the recent Sonos 10.6 desktop app as well as an older 10.3 version I had running on another computer. I have tried the Sonos desktop app on both Windows and Mac operating systems. I made sure the service was enabled and running. I tried rebooting every device on my network multiple times. All to no avail. I then deleted the pfSense pimd package and then manually reinstalled pimd with instant success on all clients. There must be something that is being configured with the manual installation that is not configured by default on the pfSense package. Unfortunately, I am not knowledgeable enough to figure this out. I will leave my current set-up running until I learn from others how to configure the new package.
-
I've removed all rules on my Sonos VLAN (50) and allowed any/any TCP UDP with IP options but the below errors are still appearing in my system log:
pimd 73046 Sendto to 224.0.0.1 on 192.168.50.1: Permission denied -
That can sort of error can often be Snort blocking the traffic.
Steve
-
Can everyone post their status pages? Im looking to see comparisons against manual installs and the package installs..
Virtual Interface Table ======================================================Vif Local Address Subnet Thresh Flags Neighbors
0 24.xx.xxx.xx 24.xx.xx/20 1 DISABLED
1 192.168.1.1 192.168.1 16 DR NO-NBR
2 10.50.1.1 10.50.1/30 16 PIM 10.50.1.2
3 192.168.1.1 register_vif0 1Vif SSM Group Sources
Multicast Routing Table ======================================================
--------------------------------- (,,G) ------------------------------------
Number of Groups: 0
Number of Cache MIRRORs: 0

