Sonos speakers and applications on different subnets (VLAN's)
-
pimd -d -c /var/etc/pimd.conf.delThat's the old conf file and it still works 'when loading it in the PIMD daemon on the command line, the file the GUI makes eg uses is in
[2.4.4-RELEASE][root@pfSense.localdomain]/: find / -name 'pimd.*' /var/etc/pimd/pimd.conf /var/etc/pimd.conf.del /var/run/pimd/pimd.dump /etc/inc/priv/pimd.priv.inc /usr/local/etc/pimd.conf /usr/local/etc/rc.d/pimd.sh /usr/local/etc/pimd.conf.sample /usr/local/pkg/pimd.inc /usr/local/pkg/shortcuts/pimd.sc.inc /usr/local/pkg/pimd.xml /usr/local/man/man8/pimd.8.gz [2.4.4-RELEASE][root@pfSense.localdomain]/: cat /var/etc/pimd/pimd.conf ##################### DO NOT EDIT THIS FILE! ###################### ################################################################### # This file was created by an automatic configuration generator. # # The contents of this file will be overwritten without warning! # ################################################################### phyint igb1.1005 enable phyint igb1.1001 enable [2.4.4-RELEASE][root@pfSense.localdomain]/: -
Yes it starts with the
--disable-vifsswitch so the conf file is the inverse of yours but both ways should result in it using igb1.1001 and igb1.1005. By default at least.You can set the pfSense package to 'Bind to all' by default and then set those interfaces to 'Do not bind' and the resulting conf file should be exactly the same as yours was.
Steve
-
When I start PIMD using the commandline and with option -d I can see what happens and I see that it works
[2.4.4-RELEASE][root@pfSense.localdomain]/root: pimd -d -c /var/etc/pimd.conf.del debug level 0xffffffff (dvmrp_detail,dvmrp_prunes,dvmrp_routes,dvmrp_neighbors,dvmrp_timers,igmp_proto,igmp_timers,igmp_members,trace,timeout,packets,interfaces,kernel,cache,rsrr,pimdetail,pim_hello,pim_register,pim_join_prune,pim_bootstrap,pim_asserts,pim_cand_rp,pim_routes,pim_timers,pim_rpf) 13:19:09.017 pimd version 2.3.2 starting ... 13:19:09.019 Got 262144 byte send buffer size in 0 iterations 13:19:09.019 Got 262144 byte recv buffer size in 0 iterations 13:19:09.019 Got 262144 byte send buffer size in 0 iterations 13:19:09.019 Got 262144 byte recv buffer size in 0 iterations 13:19:09.019 Getting vifs from kernel 13:19:09.019 Installing igb0 (192.168.100.2 on subnet 192.168.100) as vif #0 - rate 0 13:19:09.019 Installing igb1.1002 (192.168.2.1 on subnet 192.168.2) as vif #1 - rate 0 13:19:09.020 Installing igb1.1005 (192.168.5.1 on subnet 192.168.5) as vif #2 - rate 0 13:19:09.020 Installing igb1.1003 (10.0.0.1 on subnet 10/24) as vif #3 - rate 0 13:19:09.020 Installing igb1.1004 (172.16.0.1 on subnet 172.16/24) as vif #4 - rate 0 13:19:09.020 Installing igb1.1010 (172.16.10.1 on subnet 172.16.10/24) as vif #5 - rate 0 13:19:09.020 Installing igb1.1007 (172.16.20.1 on subnet 172.16.20/24) as vif #6 - rate 0 13:19:09.020 Installing igb1.1001 (192.168.1.1 on subnet 192.168.1) as vif #7 - rate 0 13:19:09.020 Ignoring igb1.1001 (10.10.10.1 on subnet 10.10.10/24) (alias for vif#7?) 13:19:09.020 Installing igb1.1008 (192.168.8.1 on subnet 192.168.8) as vif #8 - rate 0 13:19:09.020 Installing pppoe0 (194.xxx.xxx.xxx -> 194.xxx.xxx.xxx) as vif #9 - rate=0 13:19:09.020 Getting vifs from /var/etc/pimd.conf.del 13:19:09.020 Local Cand-BSR address 192.168.5.1, priority 5 13:19:09.020 Local Cand-RP address 192.168.5.1, priority 20, interval 30 sec 13:19:09.020 spt-threshold packets 0 interval 100 13:19:09.020 Local static RP: 169.254.0.1, group 232.0.0.0/8 13:19:09.020 IGMP query interval : 12 sec 13:19:09.020 IGMP querier timeout : 41 sec 13:19:09.021 Interface igb0 is DISABLED; vif #0 out of service 13:19:09.021 Interface igb1.1002 is DISABLED; vif #1 out of service 13:19:09.021 Interface igb1.1005 comes up; vif #2 now in service 13:19:09.022 query_groups(): Sending IGMP v3 query on igb1.1005 13:19:09.022 Send IGMP Membership Query from 192.168.5.1 to 224.0.0.1 13:19:09.022 SENT 36 bytes IGMP Membership Query from 192.168.5.1 to 224.0.0.1 13:19:09.022 SENT 46 bytes PIM v2 Hello from 192.168.5.1 to 224.0.0.13 13:19:09.022 Interface igb1.1003 is DISABLED; vif #3 out of service 13:19:09.022 Interface igb1.1004 is DISABLED; vif #4 out of service 13:19:09.022 Interface igb1.1010 comes up; vif #5 now in service 13:19:09.022 query_groups(): Sending IGMP v3 query on igb1.1010 13:19:09.023 Send IGMP Membership Query from 172.16.10.1 to 224.0.0.1 13:19:09.023 SENT 36 bytes IGMP Membership Query from 172.16.10.1 to 224.0.0.1 13:19:09.023 SENT 46 bytes PIM v2 Hello from 172.16.10.1 to 224.0.0.13 13:19:09.023 Interface igb1.1007 is DISABLED; vif #6 out of service 13:19:09.023 Interface igb1.1001 comes up; vif #7 now in service 13:19:09.023 query_groups(): Sending IGMP v3 query on igb1.1001 13:19:09.023 Send IGMP Membership Query from 192.168.1.1 to 224.0.0.1 13:19:09.023 SENT 36 bytes IGMP Membership Query from 192.168.1.1 to 224.0.0.1 13:19:09.023 SENT 46 bytes PIM v2 Hello from 192.168.1.1 to 224.0.0.13 13:19:09.023 Interface igb1.1008 is DISABLED; vif #8 out of service 13:19:09.023 Interface pppoe0 is DISABLED; vif #9 out of service 13:19:09.023 Interface register_vif0 comes up; vif #10 now in service Virtual Interface Table ====================================================== Vif Local Address Subnet Thresh Flags Neighbors --- --------------- ------------------ ------ --------- ----------------- 0 192.168.100.2 192.168.100 1 DISABLED 1 192.168.2.1 192.168.2 1 DISABLED 2 192.168.5.1 192.168.5 1 DR NO-NBR 3 10.0.0.1 10/24 1 DISABLED 4 172.16.0.1 172.16/24 1 DISABLED 5 172.16.10.1 172.16.10/24 1 DR NO-NBR 6 172.16.20.1 172.16.20/24 1 DISABLED 7 192.168.1.1 192.168.1 1 DR NO-NBR 8 192.168.8.1 192.168.8 1 DISABLED 9 194.xxx.xxx.xxx 194.xxx.xxx.xxx/32 1 DISABLED 10 192.168.5.1 register_vif0 1 Vif SSM Group Sources Multicast Routing Table ====================================================== --------------------------------- (*,*,G) ------------------------------------ Number of Groups: 0 Number of Cache MIRRORs: 0 ------------------------------------------------------------------------------ 13:19:09.024 Received IGMP Membership Query from 172.16.10.1 to 224.0.0.1 13:19:09.024 RECV 46 bytes PIM v2 Hello from 192.168.5.1 to 224.0.0.13 13:19:09.025 Received IGMP Membership Query from 192.168.1.1 to 224.0.0.1 13:19:09.025 RECV 46 bytes PIM v2 Hello from 172.16.10.1 to 224.0.0.13 13:19:09.025 RECV 46 bytes PIM v2 Hello from 192.168.1.1 to 224.0.0.13 13:19:09.029 Received IGMP v3 Membership Report from 192.168.1.1 to 224.0.0.22 13:19:09.029 accept_membership_report(): IGMP v3 report, 32 bytes, from 192.168.1.1 to 224.0.0.22 with 3 group records. 13:19:09.029 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:09.029 Set delete timer for group: 224.0.0.22 13:19:09.029 SM group order from 192.168.1.1 (*,224.0.0.22) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:09.030 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.2 13:19:09.030 SM group order from 192.168.1.1 (*,224.0.0.2) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:09.030 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.13 13:19:09.030 SM group order from 192.168.1.1 (*,224.0.0.13) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:09.030 Received IGMP v3 Membership Report from 172.16.10.1 to 224.0.0.22 13:19:09.030 accept_membership_report(): IGMP v3 report, 32 bytes, from 172.16.10.1 to 224.0.0.22 with 3 group records. 13:19:09.030 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.22 13:19:09.030 SM group order from 172.16.10.1 (*,224.0.0.22) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:09.030 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.2 13:19:09.030 SM group order from 172.16.10.1 (*,224.0.0.2) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:09.030 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.13 13:19:09.030 SM group order from 172.16.10.1 (*,224.0.0.13) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:09.030 Received IGMP v3 Membership Report from 192.168.5.1 to 224.0.0.22 13:19:09.030 accept_membership_report(): IGMP v3 report, 32 bytes, from 192.168.5.1 to 224.0.0.22 with 3 group records. 13:19:09.030 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.22 13:19:09.030 SM group order from 192.168.5.1 (*,224.0.0.22) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:09.030 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.2 13:19:09.030 SM group order from 192.168.5.1 (*,224.0.0.2) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:09.030 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:09.030 Set delete timer for group: 224.0.0.13 13:19:09.030 SM group order from 192.168.5.1 (*,224.0.0.13) 13:19:09.030 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:09.229 Received IGMP v3 Membership Report from 172.16.10.1 to 224.0.0.22 13:19:09.229 accept_membership_report(): IGMP v3 report, 32 bytes, from 172.16.10.1 to 224.0.0.22 with 3 group records. 13:19:09.229 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:09.229 Set delete timer for group: 224.0.0.22 13:19:09.229 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:09.229 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:09.229 Set delete timer for group: 224.0.0.2 13:19:09.229 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:09.229 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:09.229 Set delete timer for group: 224.0.0.13 13:19:09.229 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:09.234 Received IGMP Leave message from 172.16.10.20 to 224.0.0.2 13:19:09.234 accept_leave_message(): src 172.16.10.20 dst 224.0.0.2 group 224.0.0.251 13:19:09.234 Received IGMP v2 Membership Report from 172.16.10.20 to 224.0.0.251 13:19:09.234 accept_group_report(): igmp_src 172.16.10.20 ssm_src 224.0.0.251 group 224.0.0.251 report_type 22 13:19:09.234 Change IGMP compatibility mode to v2 for group 224.0.0.251 13:19:09.234 Set delete timer for group: 224.0.0.251 13:19:09.234 SM group order from 172.16.10.20 (*,224.0.0.251) 13:19:09.234 Not creating routing entry for LAN scoped group 224.0.0.251 13:19:10.029 Received IGMP v3 Membership Report from 192.168.1.1 to 224.0.0.22 13:19:10.029 accept_membership_report(): IGMP v3 report, 32 bytes, from 192.168.1.1 to 224.0.0.22 with 3 group records. 13:19:10.029 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:10.029 Set delete timer for group: 224.0.0.22 13:19:10.029 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:10.029 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:10.029 Set delete timer for group: 224.0.0.2 13:19:10.029 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:10.030 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:10.030 Set delete timer for group: 224.0.0.13 13:19:10.030 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:10.600 Received IGMP v2 Membership Report from 192.168.1.100 to 224.0.0.252 13:19:10.600 accept_group_report(): igmp_src 192.168.1.100 ssm_src 224.0.0.252 group 224.0.0.252 report_type 22 13:19:10.600 Change IGMP compatibility mode to v2 for group 224.0.0.252 13:19:10.600 Set delete timer for group: 224.0.0.252 13:19:10.600 SM group order from 192.168.1.100 (*,224.0.0.252) 13:19:10.600 Not creating routing entry for LAN scoped group 224.0.0.252 13:19:11.229 Received IGMP v3 Membership Report from 172.16.10.1 to 224.0.0.22 13:19:11.229 accept_membership_report(): IGMP v3 report, 32 bytes, from 172.16.10.1 to 224.0.0.22 with 3 group records. 13:19:11.229 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:11.229 Set delete timer for group: 224.0.0.22 13:19:11.229 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:11.229 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:11.229 Set delete timer for group: 224.0.0.2 13:19:11.229 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:11.229 accept_group_report(): igmp_src 172.16.10.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:11.229 Set delete timer for group: 224.0.0.13 13:19:11.229 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:11.829 Received IGMP v3 Membership Report from 192.168.5.1 to 224.0.0.22 13:19:11.829 accept_membership_report(): IGMP v3 report, 32 bytes, from 192.168.5.1 to 224.0.0.22 with 3 group records. 13:19:11.829 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:11.829 Set delete timer for group: 224.0.0.22 13:19:11.829 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:11.829 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:11.829 Set delete timer for group: 224.0.0.2 13:19:11.830 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:11.830 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:11.830 Set delete timer for group: 224.0.0.13 13:19:11.830 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:12.260 Cache miss, src 192.168.1.100, dst 239.255.255.250, iif 7 13:19:12.260 create group entry, group 239.255.255.250 13:19:12.829 Received IGMP v3 Membership Report from 192.168.1.1 to 224.0.0.22 13:19:12.829 accept_membership_report(): IGMP v3 report, 40 bytes, from 192.168.1.1 to 224.0.0.22 with 4 group records. 13:19:12.829 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:12.829 Set delete timer for group: 224.0.0.22 13:19:12.830 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:12.830 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:12.830 Set delete timer for group: 224.0.0.2 13:19:12.830 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:12.830 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:12.830 Set delete timer for group: 224.0.0.13 13:19:12.830 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:12.830 accept_group_report(): igmp_src 192.168.1.1 ssm_src 0.0.0.0 group 224.0.0.251 report_type 34 13:19:12.830 Set delete timer for group: 224.0.0.251 13:19:12.830 SM group order from 192.168.1.1 (*,224.0.0.251) 13:19:12.830 Not creating routing entry for LAN scoped group 224.0.0.251 13:19:13.092 Received IGMP v2 Membership Report from 192.168.1.4 to 224.0.0.251 13:19:13.092 accept_group_report(): igmp_src 192.168.1.4 ssm_src 224.0.0.251 group 224.0.0.251 report_type 22 13:19:13.092 accept_group_report(): al_pv=3 13:19:13.092 Change IGMP compatibility mode to v2 for group 224.0.0.251 13:19:13.092 Set delete timer for group: 224.0.0.251 13:19:13.092 Not creating routing entry for LAN scoped group 224.0.0.251 13:19:13.780 Cache miss, src 192.168.1.100, dst 239.255.255.250, iif 7 13:19:13.780 create group entry, group 239.255.255.250 Virtual Interface Table ====================================================== Vif Local Address Subnet Thresh Flags Neighbors --- --------------- ------------------ ------ --------- ----------------- 0 192.168.100.2 192.168.100 1 DISABLED 1 192.168.2.1 192.168.2 1 DISABLED 2 192.168.5.1 192.168.5 1 DR NO-NBR 3 10.0.0.1 10/24 1 DISABLED 4 172.16.0.1 172.16/24 1 DISABLED 5 172.16.10.1 172.16.10/24 1 DR NO-NBR 6 172.16.20.1 172.16.20/24 1 DISABLED 7 192.168.1.1 192.168.1 1 DR NO-NBR 8 192.168.8.1 192.168.8 1 DISABLED 9 194.xxx.xxx.xxx 194.xxx.xxx.xxx/32 1 DISABLED 10 192.168.5.1 register_vif0 1 Vif SSM Group Sources Multicast Routing Table ====================================================== --------------------------------- (*,*,G) ------------------------------------ Number of Groups: 0 Number of Cache MIRRORs: 0 ------------------------------------------------------------------------------ 13:19:14.782 SENT 34 bytes PIM v2 Bootstrap from 192.168.5.1 to 224.0.0.13 13:19:14.782 SENT 34 bytes PIM v2 Bootstrap from 172.16.10.1 to 224.0.0.13 13:19:14.782 SENT 34 bytes PIM v2 Bootstrap from 192.168.1.1 to 224.0.0.13 Candidate Rendezvous-Point Set =============================================== RP address Incoming Group Prefix Priority Holdtime --------------- -------- ------------------ -------- --------------------- ------------------------------------------------------------------------------ Current BSR address: 192.168.5.1 13:19:14.782 RECV 34 bytes PIM v2 Bootstrap from 192.168.5.1 to 224.0.0.13 13:19:14.782 RECV 34 bytes PIM v2 Bootstrap from 172.16.10.1 to 224.0.0.13 13:19:14.782 RECV 34 bytes PIM v2 Bootstrap from 192.168.1.1 to 224.0.0.13 13:19:15.840 Cache miss, src 192.168.1.100, dst 239.255.255.250, iif 7 13:19:15.840 create group entry, group 239.255.255.250 13:19:16.100 Received IGMP v2 Membership Report from 192.168.1.100 to 239.255.255.250 13:19:16.100 accept_group_report(): igmp_src 192.168.1.100 ssm_src 239.255.255.250 group 239.255.255.250 report_type 22 13:19:16.100 Change IGMP compatibility mode to v2 for group 239.255.255.250 13:19:16.100 Set delete timer for group: 239.255.255.250 13:19:16.100 SM group order from 192.168.1.100 (*,239.255.255.250) 13:19:16.100 create group entry, group 239.255.255.250 13:19:17.384 Cache miss, src 192.168.1.100, dst 239.255.255.250, iif 7 13:19:17.384 create group entry, group 239.255.255.250 Virtual Interface Table ====================================================== Vif Local Address Subnet Thresh Flags Neighbors --- --------------- ------------------ ------ --------- ----------------- 0 192.168.100.2 192.168.100 1 DISABLED 1 192.168.2.1 192.168.2 1 DISABLED 2 192.168.5.1 192.168.5 1 DR NO-NBR 3 10.0.0.1 10/24 1 DISABLED 4 172.16.0.1 172.16/24 1 DISABLED 5 172.16.10.1 172.16.10/24 1 DR NO-NBR 6 172.16.20.1 172.16.20/24 1 DISABLED 7 192.168.1.1 192.168.1 1 DR NO-NBR 8 192.168.8.1 192.168.8 1 DISABLED 9 194.xxx.xxx.xxx 194.xxx.xxx.xxx/32 1 DISABLED 10 192.168.5.1 register_vif0 1 Vif SSM Group Sources Multicast Routing Table ====================================================== --------------------------------- (*,*,G) ------------------------------------ Number of Groups: 0 Number of Cache MIRRORs: 0 ------------------------------------------------------------------------------ Candidate Rendezvous-Point Set =============================================== RP address Incoming Group Prefix Priority Holdtime --------------- -------- ------------------ -------- --------------------- ------------------------------------------------------------------------------ Current BSR address: 192.168.5.1 13:19:22.340 Cache miss, src 192.168.1.100, dst 239.255.255.250, iif 7 13:19:22.340 create group entry, group 239.255.255.250 13:19:23.871 Cache miss, src 192.168.1.100, dst 239.255.255.250, iif 7 13:19:23.871 create group entry, group 239.255.255.250 13:19:24.873 query_groups(): Sending IGMP v3 query on igb1.1005 13:19:24.873 Send IGMP Membership Query from 192.168.5.1 to 224.0.0.1 13:19:24.873 SENT 36 bytes IGMP Membership Query from 192.168.5.1 to 224.0.0.1 13:19:24.873 query_groups(): Sending IGMP v3 query on igb1.1010 13:19:24.873 Send IGMP Membership Query from 172.16.10.1 to 224.0.0.1 13:19:24.873 SENT 36 bytes IGMP Membership Query from 172.16.10.1 to 224.0.0.1 13:19:24.873 query_groups(): Sending IGMP v3 query on igb1.1001 13:19:24.873 Send IGMP Membership Query from 192.168.1.1 to 224.0.0.1 13:19:24.874 SENT 36 bytes IGMP Membership Query from 192.168.1.1 to 224.0.0.1 Virtual Interface Table ====================================================== Vif Local Address Subnet Thresh Flags Neighbors --- --------------- ------------------ ------ --------- ----------------- 0 192.168.100.2 192.168.100 1 DISABLED 1 192.168.2.1 192.168.2 1 DISABLED 2 192.168.5.1 192.168.5 1 DR NO-NBR 3 10.0.0.1 10/24 1 DISABLED 4 172.16.0.1 172.16/24 1 DISABLED 5 172.16.10.1 172.16.10/24 1 DR NO-NBR 6 172.16.20.1 172.16.20/24 1 DISABLED 7 192.168.1.1 192.168.1 1 DR NO-NBR 8 192.168.8.1 192.168.8 1 DISABLED 9 194.xxx.xxx.xxx 194.xxx.xxx.xxx/32 1 DISABLED 10 192.168.5.1 register_vif0 1 Vif SSM Group Sources Multicast Routing Table ====================================================== --------------------------------- (*,*,G) ------------------------------------ Number of Groups: 0 Number of Cache MIRRORs: 0 ------------------------------------------------------------------------------ Candidate Rendezvous-Point Set =============================================== RP address Incoming Group Prefix Priority Holdtime --------------- -------- ------------------ -------- --------------------- ------------------------------------------------------------------------------ Current BSR address: 192.168.5.1 13:19:24.874 Received IGMP Membership Query from 192.168.5.1 to 224.0.0.1 13:19:24.874 Received IGMP Membership Query from 172.16.10.1 to 224.0.0.1 13:19:24.874 Received IGMP Membership Query from 192.168.1.1 to 224.0.0.1 13:19:25.110 Received IGMP v2 Membership Report from 192.168.1.100 to 239.255.255.250 13:19:25.110 accept_group_report(): igmp_src 192.168.1.100 ssm_src 239.255.255.250 group 239.255.255.250 report_type 22 13:19:25.110 accept_group_report(): al_pv=2 13:19:25.110 Set delete timer for group: 239.255.255.250 13:19:25.110 create group entry, group 239.255.255.250 13:19:25.110 route to: 169.254.0.1 13:19:25.110 destination is: 0.0.0.0 13:19:25.110 gateway is: 194.xxx.xxx.xxx 13:19:25.110 iif is 9 13:19:25.110 For src 169.254.0.1, iif is 9, next hop router is 194.xxx.xxx.xxx: NOT A PIM ROUTER 13:19:25.911 Cache miss, src 192.168.1.100, dst 239.255.255.250, iif 7 13:19:25.911 create group entry, group 239.255.255.250 13:19:26.107 Received IGMP v3 Membership Report from 192.168.5.58 to 224.0.0.22 13:19:26.107 accept_membership_report(): IGMP v3 report, 32 bytes, from 192.168.5.58 to 224.0.0.22 with 3 group records. 13:19:26.107 accept_group_report(): igmp_src 192.168.5.58 ssm_src 0.0.0.0 group 230.199.198.133 report_type 34 13:19:26.107 Set delete timer for group: 230.199.198.133 13:19:26.107 SM group order from 192.168.5.58 (*,230.199.198.133) 13:19:26.107 create group entry, group 230.199.198.133 13:19:26.107 accept_group_report(): igmp_src 192.168.5.58 ssm_src 0.0.0.0 group 239.255.255.250 report_type 34 13:19:26.107 Set delete timer for group: 239.255.255.250 13:19:26.107 SM group order from 192.168.5.58 (*,239.255.255.250) 13:19:26.107 create group entry, group 239.255.255.250 13:19:26.107 accept_group_report(): igmp_src 192.168.5.58 ssm_src 0.0.0.0 group 224.0.0.251 report_type 34 13:19:26.107 Set delete timer for group: 224.0.0.251 13:19:26.107 SM group order from 192.168.5.58 (*,224.0.0.251) 13:19:26.107 Not creating routing entry for LAN scoped group 224.0.0.251 13:19:26.228 Received IGMP v3 Membership Report from 192.168.5.1 to 224.0.0.22 13:19:26.228 accept_membership_report(): IGMP v3 report, 40 bytes, from 192.168.5.1 to 224.0.0.22 with 4 group records. 13:19:26.228 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.22 report_type 34 13:19:26.228 Set delete timer for group: 224.0.0.22 13:19:26.228 Not creating routing entry for LAN scoped group 224.0.0.22 13:19:26.228 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.2 report_type 34 13:19:26.228 Set delete timer for group: 224.0.0.2 13:19:26.228 Not creating routing entry for LAN scoped group 224.0.0.2 13:19:26.228 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.13 report_type 34 13:19:26.228 Set delete timer for group: 224.0.0.13 13:19:26.228 Not creating routing entry for LAN scoped group 224.0.0.13 13:19:26.229 accept_group_report(): igmp_src 192.168.5.1 ssm_src 0.0.0.0 group 224.0.0.251 report_type 34 13:19:26.229 Set delete timer for group: 224.0.0.251 13:19:26.229 Not creating routing entry for LAN scoped group 224.0.0.251 13:19:27.014 Received IGMP v2 Membership Report from 192.168.5.68 to 239.255.255.250 13:19:27.014 accept_group_report(): igmp_src 192.168.5.68 ssm_src 239.255.255.250 group 239.255.255.250 report_type 22 13:19:27.014 accept_group_report(): al_pv=3 13:19:27.014 Change IGMP compatibility mode to v2 for group 239.255.255.250 13:19:27.014 Set delete timer for group: 239.255.255.250 13:19:27.014 create group entry, group 239.255.255.250 13:19:27.192 Received IGMP v2 Membership Report from 192.168.1.4 to 224.0.0.251 13:19:27.192 accept_group_report(): igmp_src 192.168.1.4 ssm_src 224.0.0.251 group 224.0.0.251 report_type 22 13:19:27.192 accept_group_report(): al_pv=2 13:19:27.192 Set delete timer for group: 224.0.0.251 13:19:27.192 Not creating routing entry for LAN scoped group 224.0.0.251 13:19:27.371 Received IGMP v3 Membership Report from 192.168.5.60 to 224.0.0.22 13:19:27.371 accept_membership_report(): IGMP v3 report, 32 bytes, from 192.168.5.60 to 224.0.0.22 with 3 group records. 13:19:27.371 accept_group_report(): igmp_src 192.168.5.60 ssm_src 0.0.0.0 group 230.199.198.133 report_type 34 13:19:27.371 Set delete timer for group: 230.199.198.133 13:19:27.371 create group entry, group 230.199.198.133 13:19:27.372 accept_group_report(): igmp_src 192.168.5.60 ssm_src 0.0.0.0 group 239.255.255.250 report_type 34 13:19:27.372 Set delete timer for group: 239.255.255.250 13:19:27.372 create group entry, group 239.255.255.250 13:19:27.372 accept_group_report(): igmp_src 192.168.5.60 ssm_src 0.0.0.0 group 224.0.0.251 report_type 34 13:19:27.372 Set delete timer for group: 224.0.0.251With the GUI it doesn't work/ do it's job and I cannot see the output, well just a few lines in the system.log, although it set log level in the GUI to debug.
-
Read our last few replies again. You are not comparing apples to apples. We have already explained what is happening.
-
Sorry @jimp that I don't get it. When I use the GUI and set it as shown below the Sonos devices are not accessible.
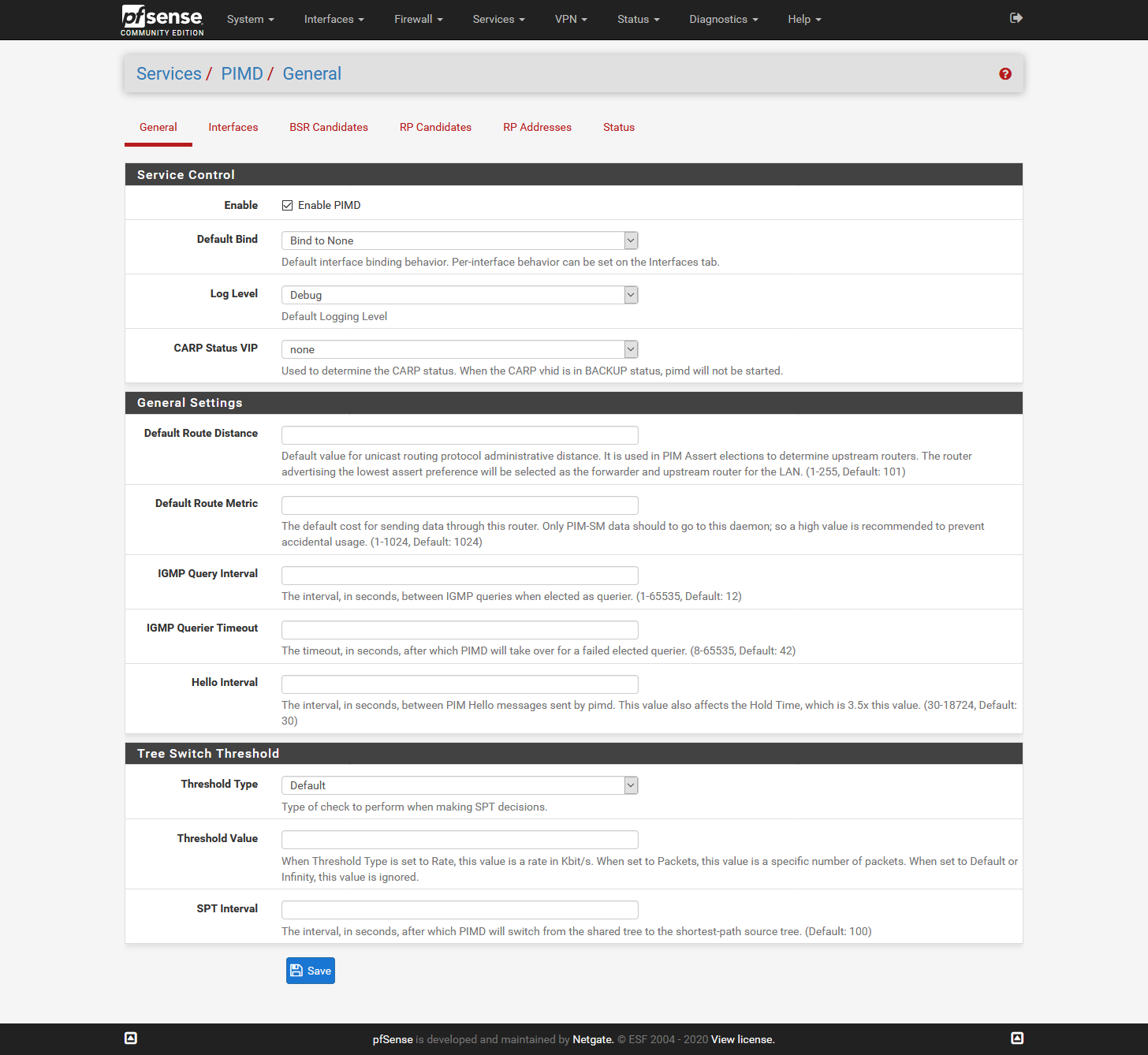
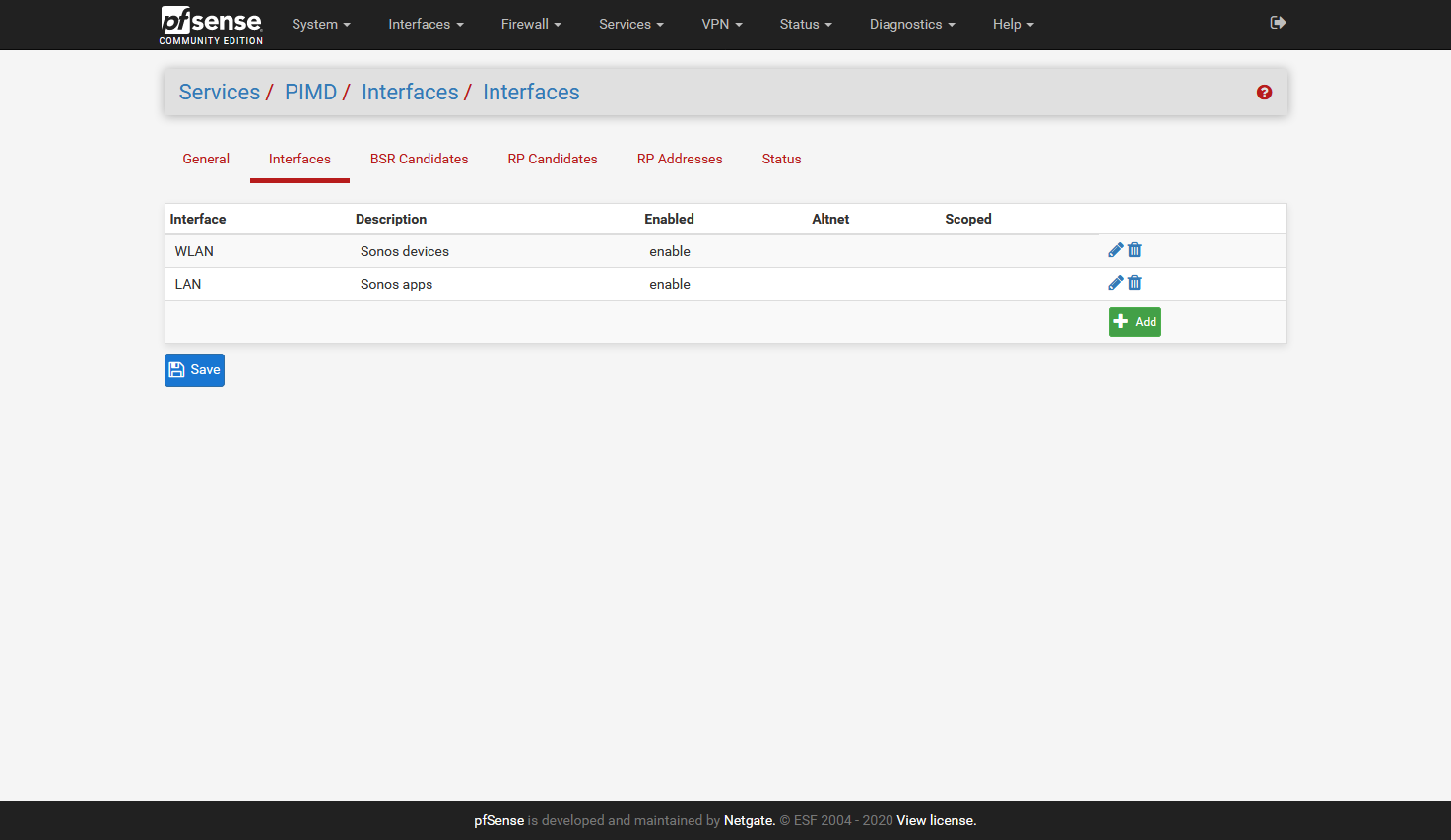
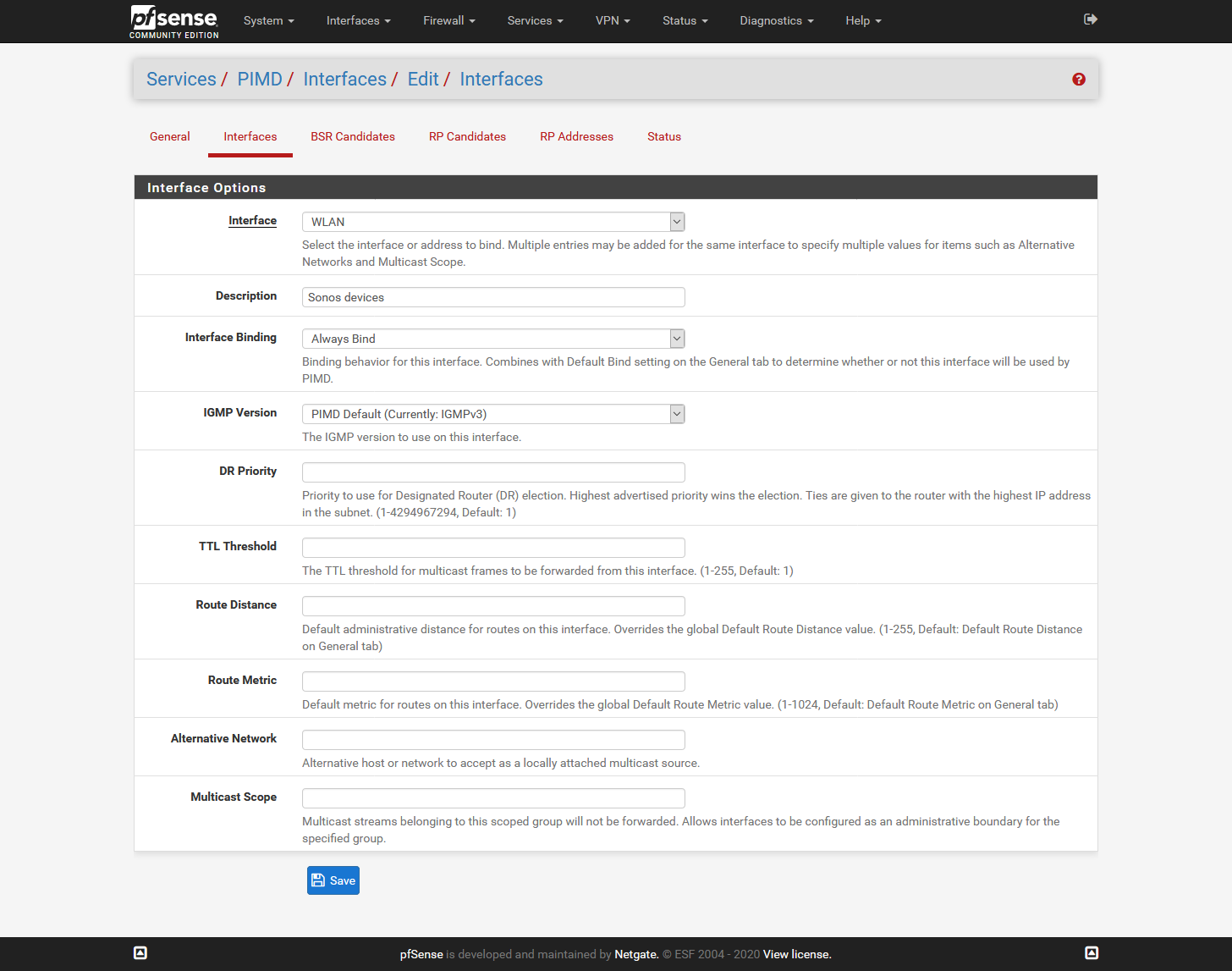
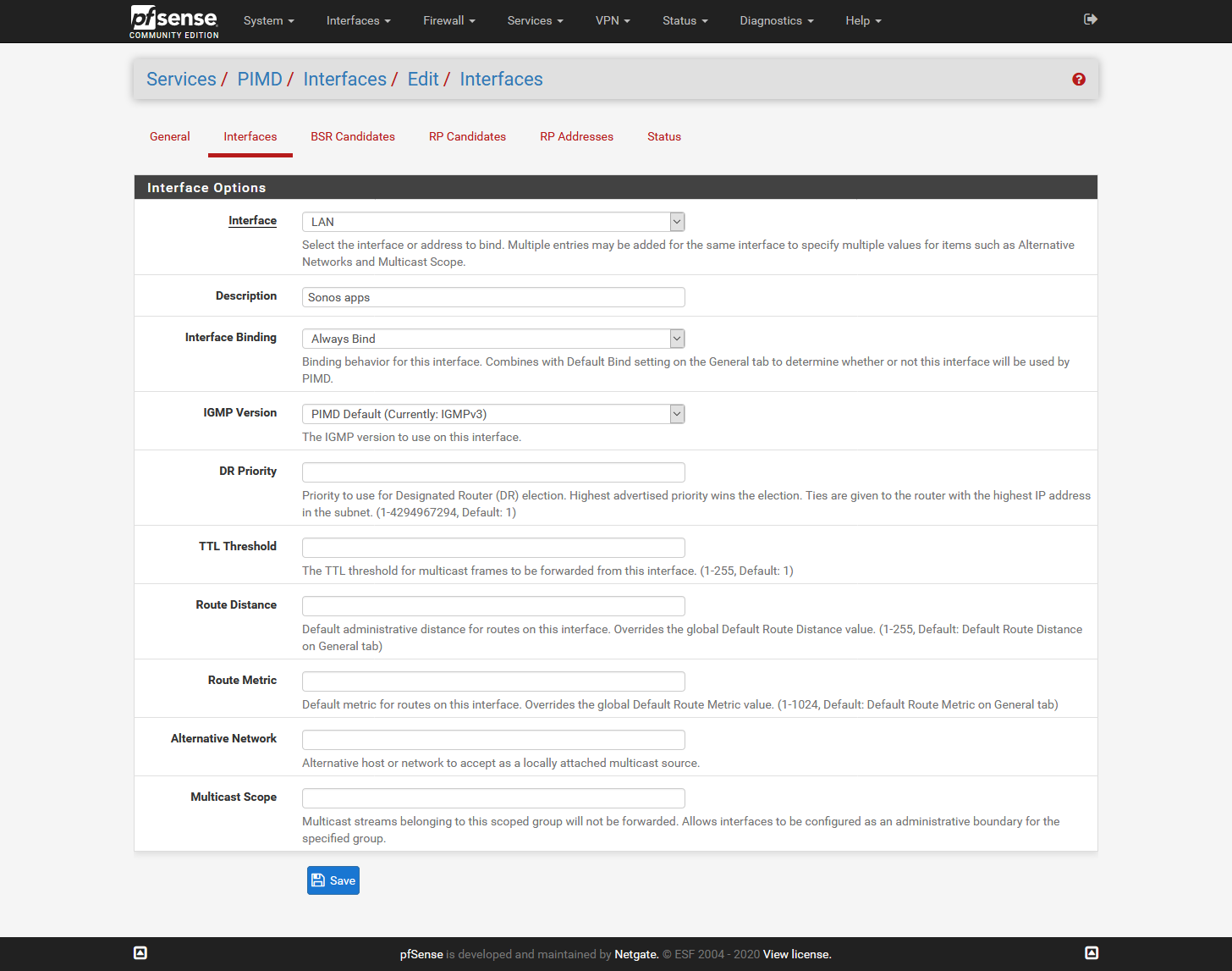
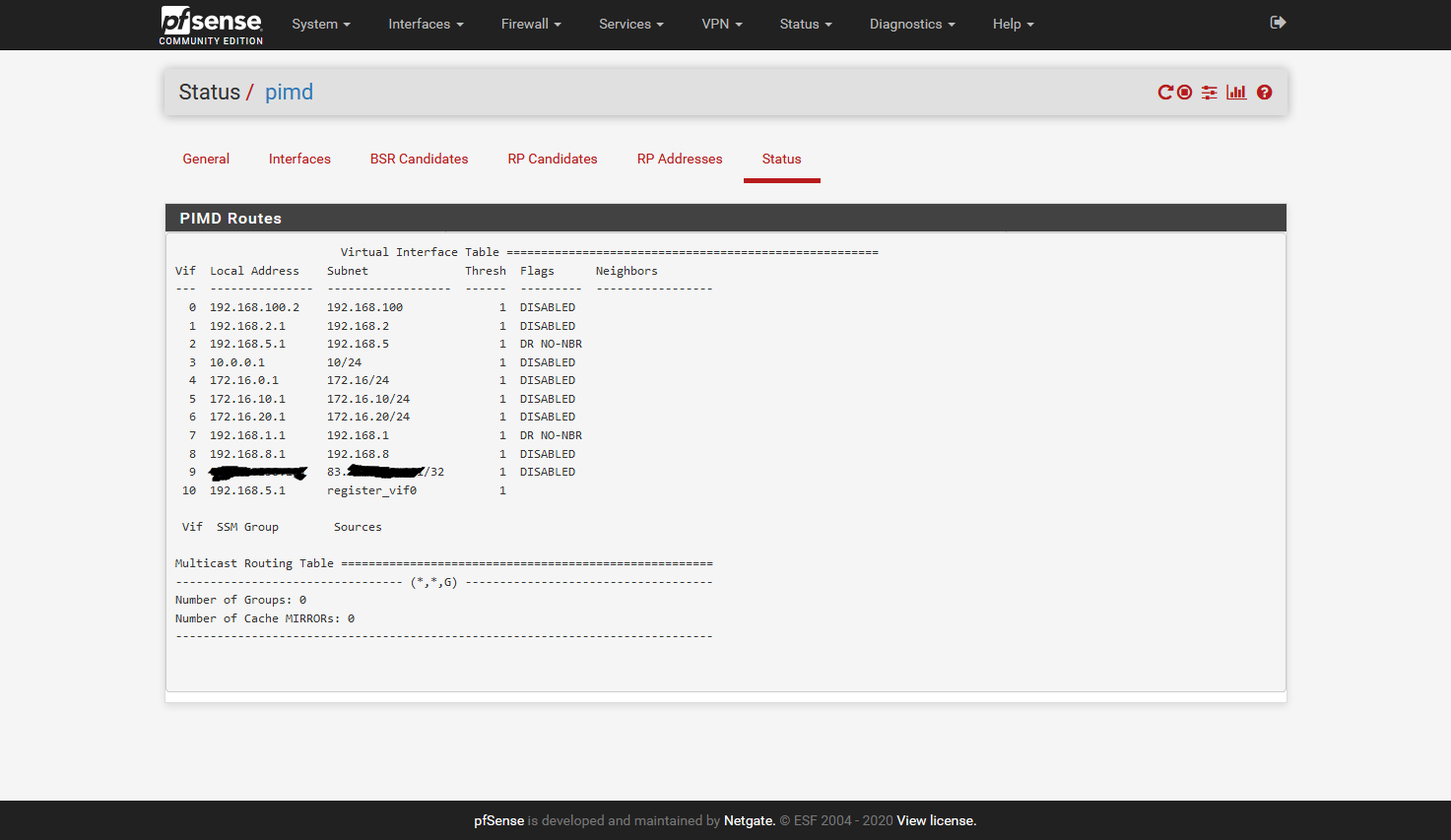
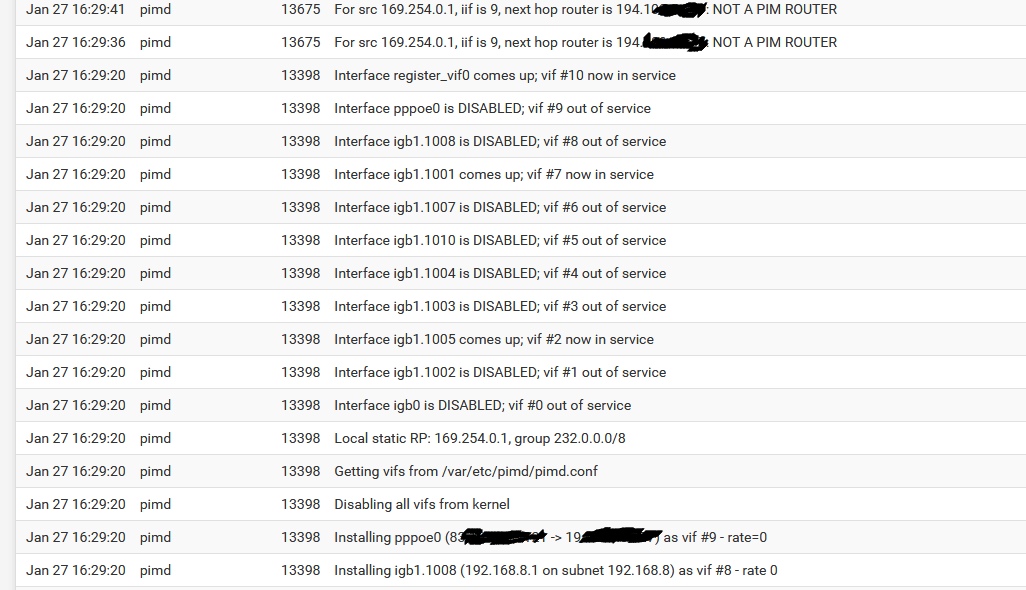
The moment I load the "old"config file manually it works.
-
Read our replies again. We explained exactly what to change. No need to repeat yourself.
-
Thanks for your patience. I just tested what I think you both suggested;
Default bind "Bind to All" and then added every interface I dont want to use in the interfaces tab to "Never Bind", then enabled PIMD in the General tab, alas I cannot connect to the Sonos interfaces.
-
@Qinn said in Sonos speakers and applications on different subnets (VLAN's):
Thanks for your patience. I just tested what I think you both suggested;
Default bind "Bind to All" and then added every interface I dont want to use in the interfaces tab to "Never Bind", then enabled PIMD in the General tab, alas I cannot connect to the Sonos interfaces.
As I described above, I am having the exact same experience. I have not been successful in getting the pfSense package working for me. I have tried both “Bind to All” and deselecting the interfaces I don’t want to bind, as well as “Bind to None” and selecting the the interfaces that I do want to bind in the interfaces tab without success. When I deleted the pfSense package and manually reinstalled pimd, everything works! BTW, I made sure I uninstalled pimd and rebooted before I installed the pfSense package. I confirmed that the service was enabled and running. Is it possible that the manual installation configures something that is not configured by default in the pfSense package?
-
If it works differently then there is either a difference in your configuration or a difference in the command line the package is running. Check the config you are using with the FreeBSD package compared to the GUI, and look at the
ps uxaww | grep pimdoutput for both as well.The version of
pimdis the same, and there shouldn't be anything different about how it operates. -
I was able to get this working by adding an RP address, specifying the IP address of one of my Sonos speakers and
239.255.255.250for the multicast group. All of my other settings are identical to your screenshots above.Update: I was able to confirm using the GUI method is working after configuring all of my Sonos devices in the RP address section with nothing configured for multicast group.
-
I can confirm, that did the trick, strange that you have to add this, when using the GUI and it seems adding the ip of a Sonos device does the trick, but it should not be that way as the ip address of a multicast device should not be needed to make it work and it will not work when using DHCP and not static or reserved addresses.
-
This post is deleted! -
The difference between your working output and the package, at least when you were using default 'do not bind' appears to be that you were enabled on 172.16.10.1 in the manual method but disabled in the package status.
Hard to see how it could be any different otherwise though.
Maybe post the command lines and config files for comparison here from each method. There must be some difference.
Steve
-
@stephenw10 said in Sonos speakers and applications on different subnets (VLAN's):
That can sort of error can often be Snort blocking the traffic.
Steve
hmm, ok I'm not using snort but I am using pfblockerNG. Could this be the cause?
-
@Deviant0ne said in Sonos speakers and applications on different subnets (VLAN's):
I was able to get this working by adding an RP address, specifying the IP address of one of my Sonos speakers and
239.255.255.250for the multicast group. All of my other settings are identical to your screenshots above.Update: I was able to confirm using the GUI method is working after configuring all of my Sonos devices in the RP address section with nothing configured for multicast group.
Strange, neither one of those options is working for me. Tried out the PIMd package, configured it extremely basic:
- VLAN with media devices (Sonos et al)
- VLAN LAN
- VLAN Guest/Wifi
- allowed all VLANs access to each other
set up pimd with
- bind none
- added the three vlans as "allowed"
- default anywhere else
-> no function
- under "RP addresses" added my Sonos Beam IP with 239... as group address
-> still nope
- removed group address and added other Sonos devices
-> still nope (and many more errors like:)
For src 172.27.3.30, iif is 5, next hop router is 172.27.3.30: NOT A PIM ROUTERgot entries in status like
Source Group RP Address Flags --------------- --------------- --------------- --------------------------- 172.27.1.128 239.255.255.250 172.27.3.30 CACHE SG Joined oifs: ..........j Pruned oifs: ........... Leaves oifs: ........... Asserted oifs: ........... Outgoing oifs: ..........o Incoming : .I......... TIMERS: Entry JP RS Assert VIFS: 0 1 2 3 4 5 6 7 8 9 10 210 45 0 0 0 0 0 0 0 0 0 0 0 0 0 Source Group RP Address Flags --------------- --------------- --------------- --------------------------- 172.27.3.1 239.255.255.250 172.27.3.30 CACHE SG Joined oifs: ..........j Pruned oifs: ........... Leaves oifs: ........... Asserted oifs: ........... Outgoing oifs: ..........o Incoming : .....I..... TIMERS: Entry JP RS Assert VIFS: 0 1 2 3 4 5 6 7 8 9 10 185 10 0 0 0 0 0 0 0 0 0 0 0 0 0but still the android app on the phone won't find the sonos devices/network at all.
-
I was using an iOS device for testing and found that I was experiencing the same issue as some of the other users where my Sonos system could not be located at first - after disabling and re-enabling WiFi on my iOS device, I was able to access my Sonos system without issue. Otherwise, my configuration is nearly identical to what you're describing.
-
@Deviant0ne I have a second WiFi patched into the SONOS network VLAN - if I switch to that (obviously) all is fine. If I switch back to LAN (which should use PIM) it doesn't. Toggling Wifi doesn't do anything for my Androids around here. No one is finding the Sonos devices. Added all of them as RP addresses - nope. Removed all but one - nope. Don't know what's the key to get this to work yet. :/
-
@jimp said in Sonos speakers and applications on different subnets (VLAN's):
If it works differently then there is either a difference in your configuration or a difference in the command line the package is running. Check the config you are using with the FreeBSD package compared to the GUI, and look at the
ps uxaww | grep pimdoutput for both as well.The version of
pimdis the same, and there shouldn't be anything different about how it operates.@jimp In my original working setup with the manual install of the FreeBSD package, the only options enabled ( by default ), besides the interfaces I had to disable are:
bsr-candidate priority 5 rp-candidate time 30 priority 20 spt-threshold packets 0 interval 100I have since switched to the use of the recommended setup for the new package - "bind to none" and only enable interfaces needed. It seems to be working for me - but not anyone else in the house. Before, it all worked.
ps uxaww | grep pimdwith my current setup gives me :root 14572 0.0 0.1 6500 2276 - S 18:10 0:00.00 sh -c ps uxaww | grep pimd 2>&1 root 14782 0.0 0.0 388 272 - R 18:10 0:00.00 grep pimd root 57669 0.0 0.1 5996 1956 - S 04:09 0:01.05 /usr/local/sbin/pimd -c /var/etc/pimd/pimd.conf --disable-vifs -s notice -
Can we see the conf file the package generates compared to your manually created workinh one?
-
manualy conf file - only changes I add to this is the interface to disable :
# Exmaple configuration file for pimd, the original PIM-SM router # # See the pimd(8) man page for details on all the settings. This file # only gives very brief examples and is intended as a quick start. # # NOTE: The order of the settings matter! # ## # default-route-distance <1-255> # default-route-metric <1-1024> # hello-interval <30-18724> # # igmp-query-interval <SEC> # igmp-querier-timeout <SEC> # # phyint <local-addr | ifname> # [disable | enable] [igmpv2 | igmpv3] # [dr-priority <1-4294967294>] # [ttl-threshold <1-255>] [distance <1-255>] [metric <1-1024>] # [altnet <network> [/<masklen> | masklen <masklen>]] # [scoped <network> [/<masklen> | masklen <masklen>]] # # bsr-candidate [local-addr | ifname] [priority <0-255>] # rp-candidate [local-addr | ifname] [priority <0-255> ] [time <10-16383>] # group-prefix <group-addr>[/<masklen> | masklen <masklen>] # group-prefix <group-addr>[/<masklen> | masklen <masklen>] # . # . # group-prefix <group-addr>[/<masklen> | masklen <masklen>] # rp-address <local-addr> [<group-addr>[/<masklen> | masklen <masklen>] # # spt-threshold [rate <KBPS> | packets <NUM> | infinity] [interval <SEC>] ## # # By default PIM is activated on all interfaces. Use `phyint disable` # on interfaces where PIM should not run. You can also use the `-N, # --disable-vifs` command line option along with `enable` to get the # inverse behavior. # # The routing protocol admin distance (or metric preference per the RFC) # is used in PIM Assert elections to elect the forwarder of multicast. # Currently pimd cannot obtain distance and metric from the underlying # routing protocols, so a default distance may need to be configured per # interface. If left out, the default-route-distance is used for the # phyint. In PIM assert elections the router advertising the lowest # preference (distance) will be selected as forwarder (upstream router) # for that LAN. An admin distance of 101 should be sufficiently high so # that asserts from Cisco or GateD routers are prefered over poor-little # pimd. # # It is reccommended that preferences (admin distance) be set such that # metrics are never consulted. However, default metrics may also be set # and default to 1024. # # A phyint directive can use either the interface name, ifname, or the # IP address. The distance and metric settings define administrative # distance and metric, respectively, for PIM Assert messages sent on # that interface. Usually you do not need this, but if you do, think of # them like distance and metric defined on an inbound interface (iif), # but used by PIM Asserts on the outbound interfaces (oifs). # # If you want to add "alternative (sub)net" to a physical interface, # e.g., if you want to make incoming traffic with a non-local source address # to appear as it is coming from a local subnet, then use the command: # # phyint <local-addr | ifname> altnet <net-addr> masklen <len> # # NOTE: if you use this command, make sure you know what you are doing! # # If you want administratively scoped multicast filtering, use the # following command: # # phyint <local-addr | ifname> scoped <net-addr> masklen <masklen> # # This allows interfaces to be configured as an administrative boundary # for the specified scoped address, or address range. Packets belonging # to the scoped range will not be forwarded. Use `--enable-scoped-acls` # flag to the configure script to activate this at build time. # # Both rp-candidate and bsr-candidate are enabled in the default config, # below. Disabling them for all PIM capable routers is a bad idea. At # least one PIM router in the backbone must act as a bootstrap router. # The optional local-addr or ifname arguments after the rp-candidate and # bsr-candidate settings specify the local address to be used in the # Cand-RP and Cand-BSR messages. In case ifname is given as argument, # the first IPv4 address of that interface is used. If either is # unspecified, the largest local IP address will be used, excluding # phyint interfaces where PIM has been disabled. # # The time argument to rp-candidate specifies how often to send Cand-RP # messages. The default value is 30 seconds. Use smaller values for # faster convergence. # # The group-prefix setting is the prefix(es) advertised if rp-candidate. # It is possible to set up to 255 group-prefix records. # # Using the rp-address setting it is possible to set a static rendezvous # point. The argument can be either a unicast or a multicast address # followed by an optional group address and optional masklen to that. # # The spt-threshold specifies the minimum rate in kbps before the last # hop router initiates a switch to the shortest path. The `packets` # argument is an alternative notation, `infinity` means to never switch, # and `interval` specifies the interval for periodical testing of the # threshold. Currently, `interval` must be at least 5 (seconds) # # Interface defaults, like default-route-distance and -metric must be # set before the phyint section -- the .conf parser is not clever. #default-route-distance 101 # smaller is better #default-route-metric 1024 # smaller is better #hello-interval 30 # Don't set lower than 30 # The phyint settings currently *MUST BE* ordered after the default # source preference and metric settings, but before everything else. # By default, all non-loopback multicast capable interfaces are enabled. # If you want to use loopback, set the interface multicast flag on it. #phyint eth0 disable # IGMP default query interval and querier timeout. The latter should # per RFC always be (robustness * interval) + (query-response / 2), for # pimd this means: (3 * 12) + (10 / 2) = 41, we've rounded it up to # honor the late Douglas Adams. You can set it to a higher value, but # it is not recommended to set it lower. #igmp-query-interval 12 #igmp-querier-timeout 42 # Bigger value means "higher" priority bsr-candidate priority 5 # Smaller value means "higher" priority rp-candidate time 30 priority 20 # Candidate for being RP of complete IPv4 multicast range #group-prefix 224.0.0.0 masklen 4 # Static rendez-vous point #rp-address 192.168.10.1 224.0.0.0/4 # Switch to shortest-path tree after first packet, but only after 100 sec. spt-threshold packets 0 interval 100The conf file generated by the package I see at
/var/etc/pimd/##################### DO NOT EDIT THIS FILE! ###################### ################################################################### # This file was created by an automatic configuration generator. # # The contents of this file will be overwritten without warning! # ################################################################### phyint mvneta1.1001 enable phyint mvneta1.1003 enable

