Blocking Port 53 & Issues Resolving Host Names
-
Dear Negate Community,
I recently setup DNS over TLS with cloudflare and it's working for the most part except some websites take a long time to load (or even fail occasionally). But once the web page loads, navigating the web page is normal and speedy and will work for a little bit but then revert back to taking a long time to load.
Also, for example, it stopped pfsenes from finding the new pfsense update, my vpn fails to restart properly and stops pfblockerng from updating until I disable the rule.
I have isolated the issue to this firewall rule that is blocking port 53:
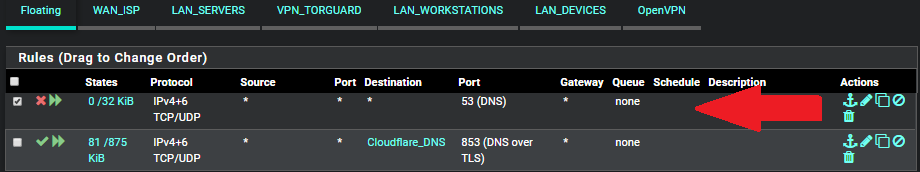
If I disable this firewall rule, all websites load fine. But then, DNS starts going over port 53 and not 853.
Here are other rules I have for port 53, but I don't think they are affecting my issue:
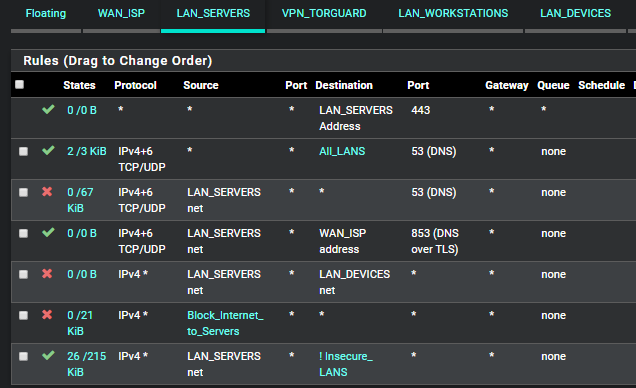
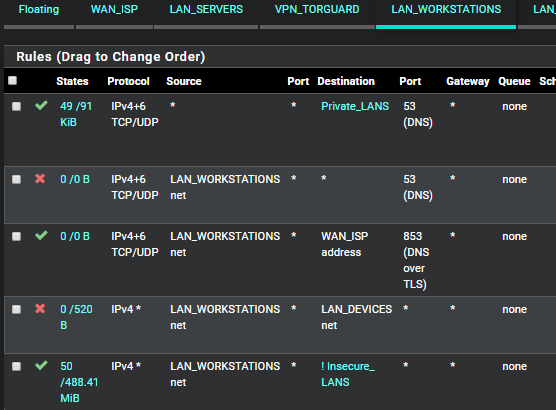
Here is a sample of my state table for 1.0.0.1:
https://hastebin.com/oqusazuxep.nginxIs anyone else experiencing this? Any tips / recommendation would be greatly appreciated!
Thank you very much!
-
i would check this under dns resolver
DNS Query Forwarding
Enable Forwarding Mode If this option is set, DNS queries will be forwarded to the upstream DNS servers defined under System > General Setup or those obtained via DHCP/PPP on WAN (if DNS Server Override is enabled there).Use SSL/TLS for outgoing DNS Queries to Forwarding Servers When set in conjunction with DNS Query Forwarding, queries to all upstream forwarding DNS servers will be sent using SSL/TLS on the default port of 853. Note that ALL configured forwarding servers MUST support SSL/TLS queries on port 853. <- and check this
-
Hi kiokoman,
Thanks you, I just double checked and all those settings are checked off already and I am using cloudflare which supports DNS over TLS.
-
and that is 1.1.1.1 and 1.0.0.1 ?
-
@kiokoman yes sir! and for hostname, I have: 1dot1dot1dot1.cloudflare-dns.com for both of them.
I broke my internet somehow, fixing that right now

Update: oh it's back now!
-
This post is deleted! -
Hello,
Just an update:
It looks like some websites failing/taking a long time to load was related to snort (although I disabled all packages before as a test and it was still having issues but looks like that's not the case now)
In terms of external host names not resolving, such as:
- pfsense not finding an update for itself,
- pfblockerng failing updates, for example with: Could not resolve host: ransomwaretracker.abuse.ch Retry in 5 seconds...
- VPN not working unless I put an IP in the config (instead of hostname)
- No packages appearing under the "available packages"
I found that if I did the following it fixed this (But please let me know if this is wrong!):
- Go to System -> General Setup
- Uncheck "Disable DNS Forwarder"
Do not use the DNS Forwarder/DNS Resolver as a DNS server for the firewall
By default localhost (127.0.0.1) will be used as the first DNS server where the DNS Forwarder or DNS Resolver is enabled and set to listen on localhost, so system can use the local DNS service to perform lookups. Checking this box omits localhost from the list of DNS servers in resolv.conf. - Go to: Services -> DNS Resolver
- Select "All" for the Network Interfaces and Outgoing Network Interfaces.
So in summary,
- I have All domain devices' DNS pointing to my internal AD DNS servers via DHCP scope
- I added the pfsense ip to the forwarder list of my AD DNS servers
- Added my AD DNS servers to the DNS resolver domain override setting
- I enabled all interfaces for "network interfaces" and "outgoing network interfaces" in the DNS resolver setting
- I unchecked "Disable DNS forwarder" under System -> General Setup
- Blocking port 53 outbound
- Using cloudflare for DNS over TLS in System -> General Setup
If this is borked please let me know! (but it everything seems to be working now... even while blocking port 53 outbound)
-
@techgeek055 Just another update:
all issues seem to be resolved except when visiting websites, I will randomly get 2 different white pages with 2 different errors: DNS_PROBE_STARTED then DNS_PROBE_FINISHED_NXDOMAIN ,then it will load the webpage normally after half a second.
Edit: Actually i think it's working without this issue
-
@techgeek055 hostname one.one.one.one not 1dot1dot1dot1.cloudflare-dns.com
-
Yep, confirmed :
[2.4.5-RELEASE][root@priv.brit-hotel-fumel.net]/root: host 1.1.1.1 1.1.1.1.in-addr.arpa domain name pointer one.one.one.one.