Dual WAN Setup on XG-7100
-
Hello,
I also encountered this problem but I succed to set up the Dual WAN.
Here (http://naalpv.tk/memo/2018/08/24/pfsense-configuration-dual-wan-avec-xg-7100/) you will find the configuration steps I made.
Thank you. -
Check out https://www.youtube.com/watch?v=NgRy14rYhV8 -- Last month for the hangout I walked through how to configure the switch for separate ports like you're after.
-
@jimp this was perfect, thank you!
-
@ragnarxyz could you give your insight on how you have accomplished to have the second wan up and working?
-
You need to separate your switch Port(s) first: https://www.netgate.com/resources/videos/configuring-netgate-appliance-integrated-switches-on-pfsense-244.html
After that it is the default pfSense MultiWAN Configuration:
https://www.netgate.com/docs/pfsense/routing/multi-wan.html
https://www.netgate.com/docs/pfsense/book/multiwan/index.html
https://www.netgate.com/resources/videos/multi-wan-on-pfsense-23.html-Rico
-
@rico thanks a lot!
-
I have the same problem as well. I tried dual wan being wan (default 4090) as the first wan connection, and for the second wan I created another vlan 4092 and assigned port members 2,9t,10t, and removed port 2 from vlan 4091.
Then enabled the interface , setup rules, add gateway groups. and it did not work. The second wan connection is offline ..not sure why ... see my configs below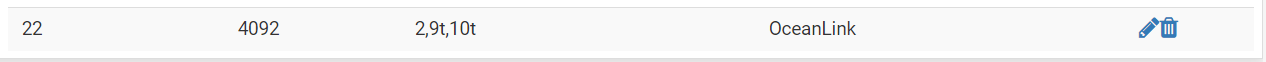
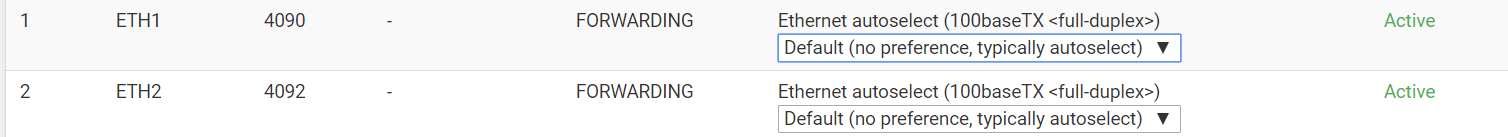
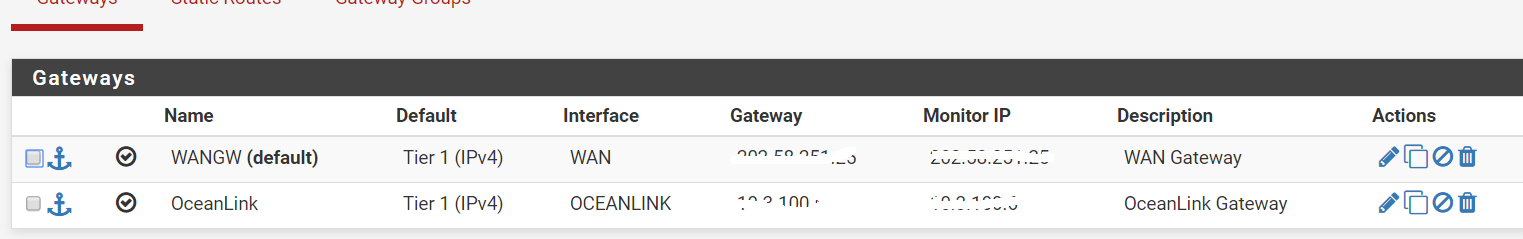
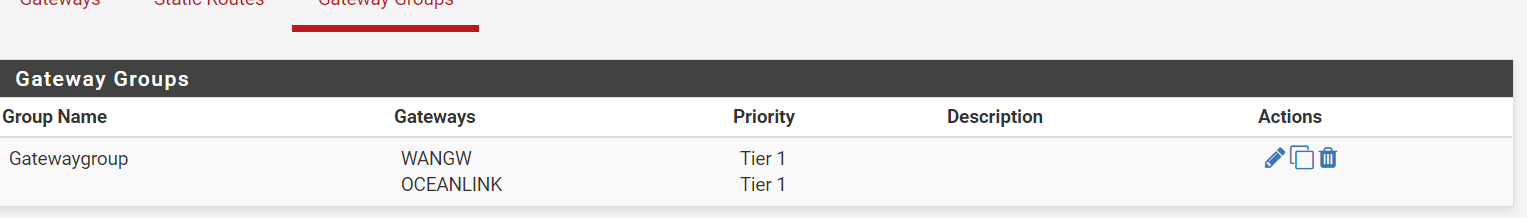
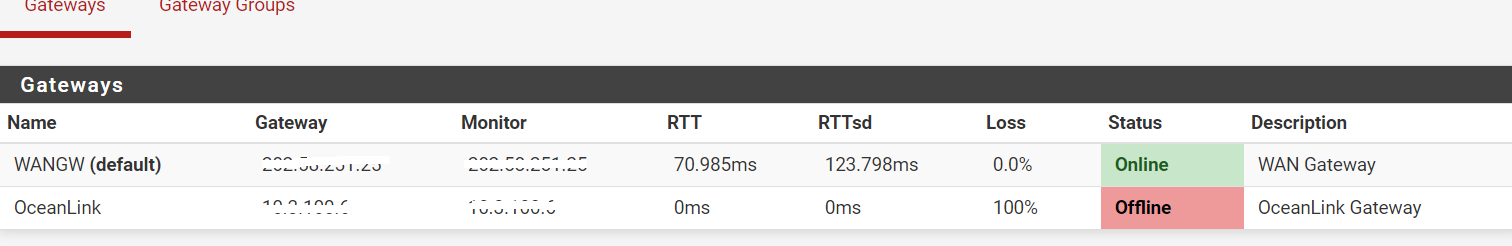
any suggestions ?
-
What we can see looks correct. We don't see the vlan 4092 interface setup.
The gateway IP (which looks like a private IP that doesn't need to be obscured) might not respond to pings. Can you ping out to some public IP choosing that WAN as source?
Steve
-
Thanks stephew10 for your reply. Now that I manually set it the Monitro IP for second wan connection (ocean link) the status is still offline while RTT, RTTsd , and Loss values some activities going on.
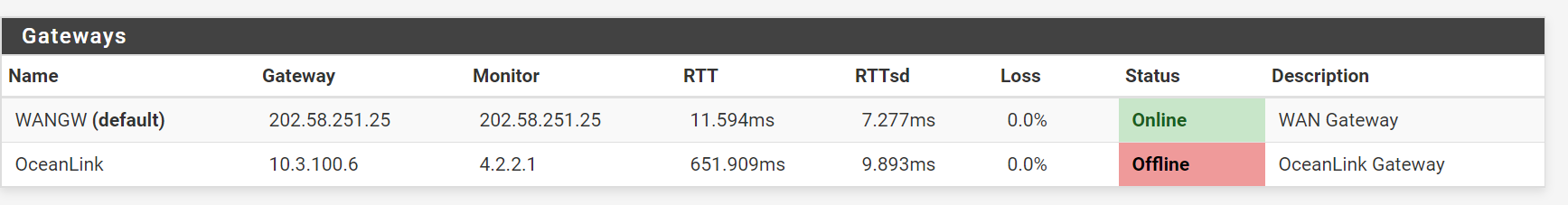
For the second WAN connection my ISP has assigned me private , and I already made request for my truly public IP.
So having the true public will solve the issue ?
-
Show your WAN Interface configuration via screenshots.
-Rico
-
What is the Oceanlink WAN, what tyep of connection. You are showing zero packet loss but 650ms lattency.
If it's some sort of wireless link you might just need to tune the monitoring parameters to match it.
Steve
-
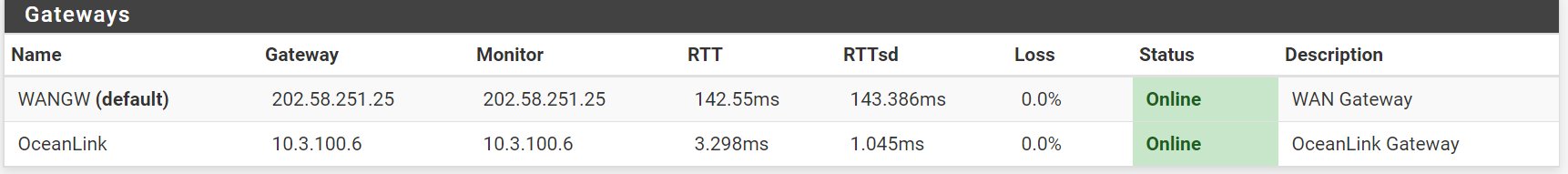
It is a wireless link to our ISP here , about 100 meters away from our office. I think there is another issue , ISP block ICMP protocol , and the ping to the oceanlink gateway blocked , and I asked them last yesterday to allow ping and they did. I checked this morning in pfsense Status->Gateways and there were both online. The 650 ms latency is our normal internet speed from both ISPs here, very slow but we have no choice.
Now that both gateways are online I tested to see if load balance worked by disabling the other gateway (ATHKL) and it did'n work. There are no internet at all. Pfsense did realize that one gateway has gone and jumped to Oceanlink but no internet access.
-
If 650ms is normal for that link then tune the latency values for dpinger by editing the gateway. That way it will only throw an alarm if latency rises unexpectedly high.
How are you using the load-balance gateway? Let's see the rules where that is set.
Steve
-
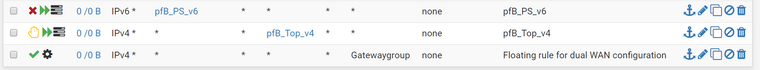
I use load balance
Floating rules below
Gateway status
-
Hi naalpv
The link did not work. I wonder how you actually did it. Can you fix the link so we can see what configurations you made
-
First Wan connection configurations (default 4090)
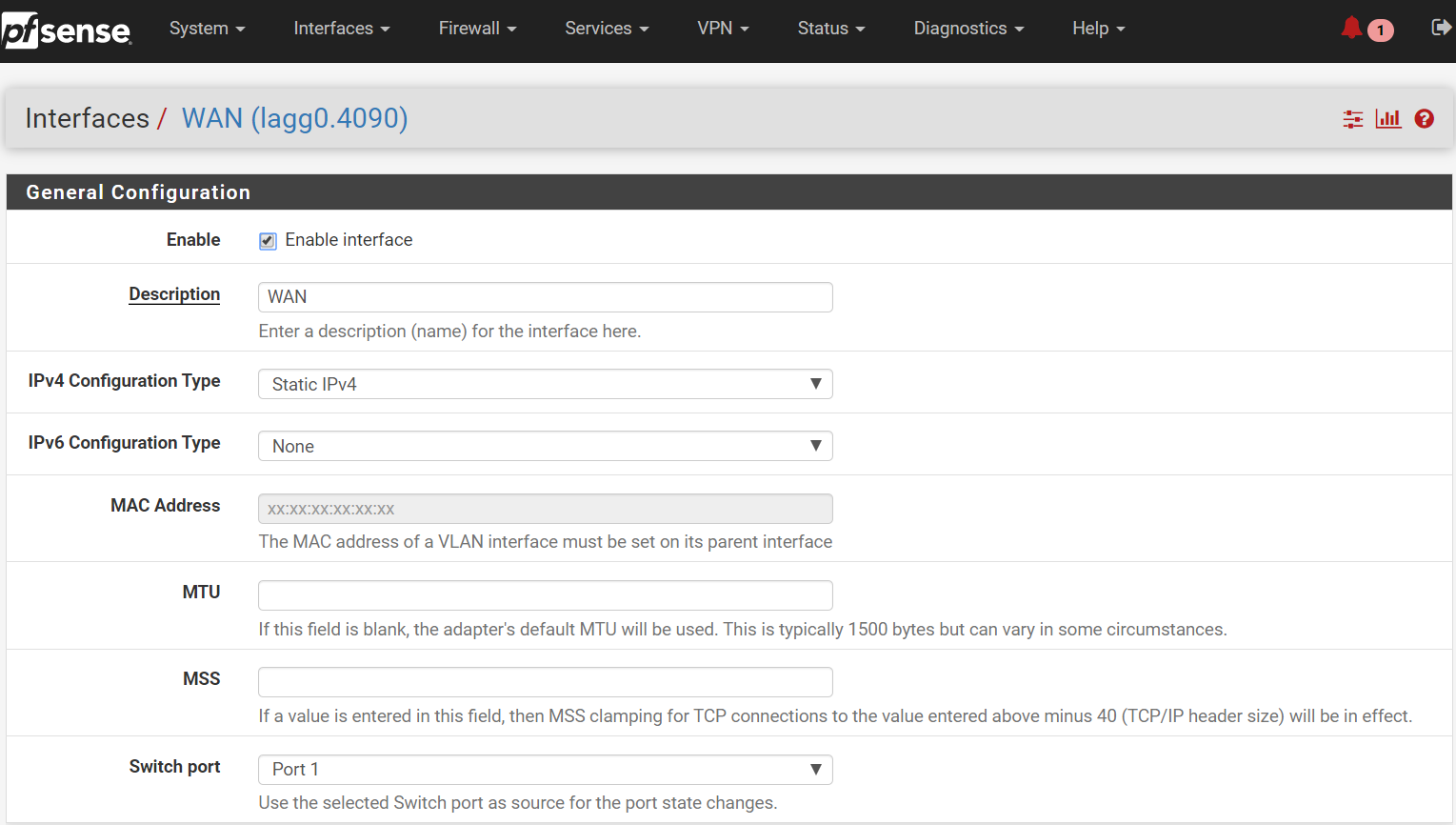
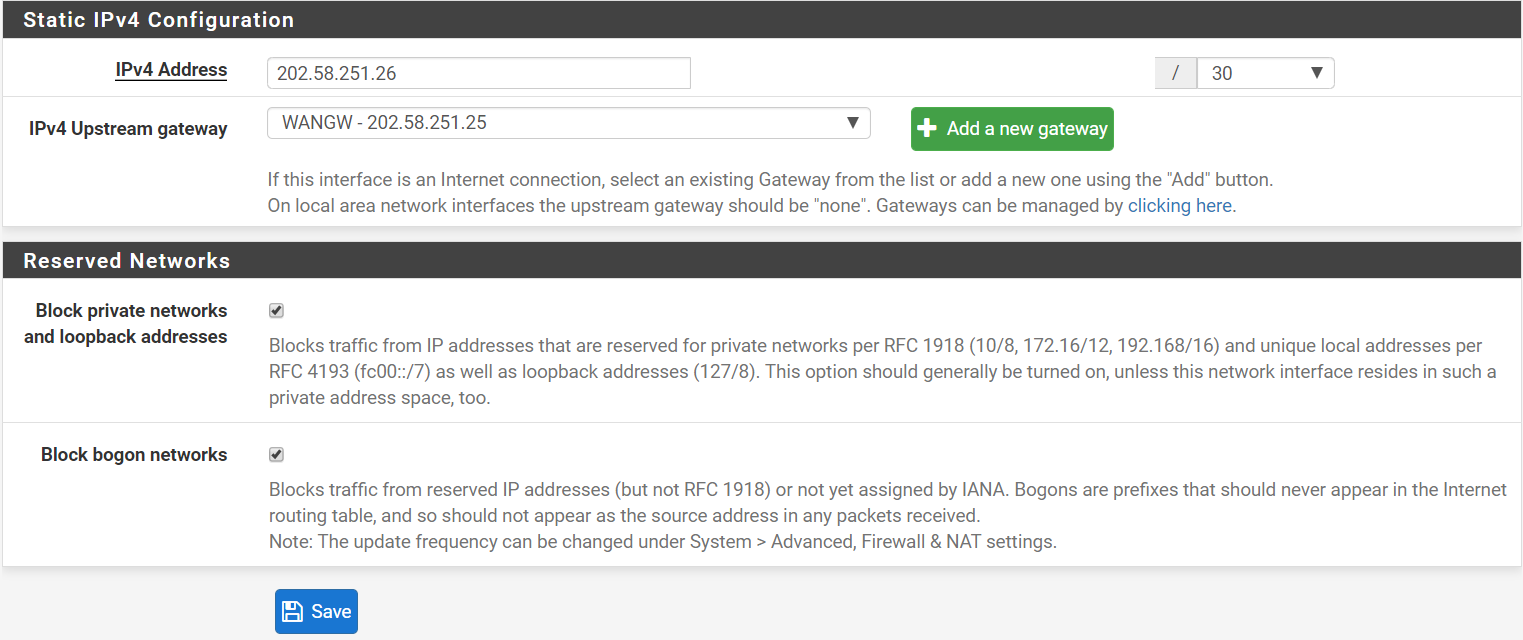
Second WAN connection
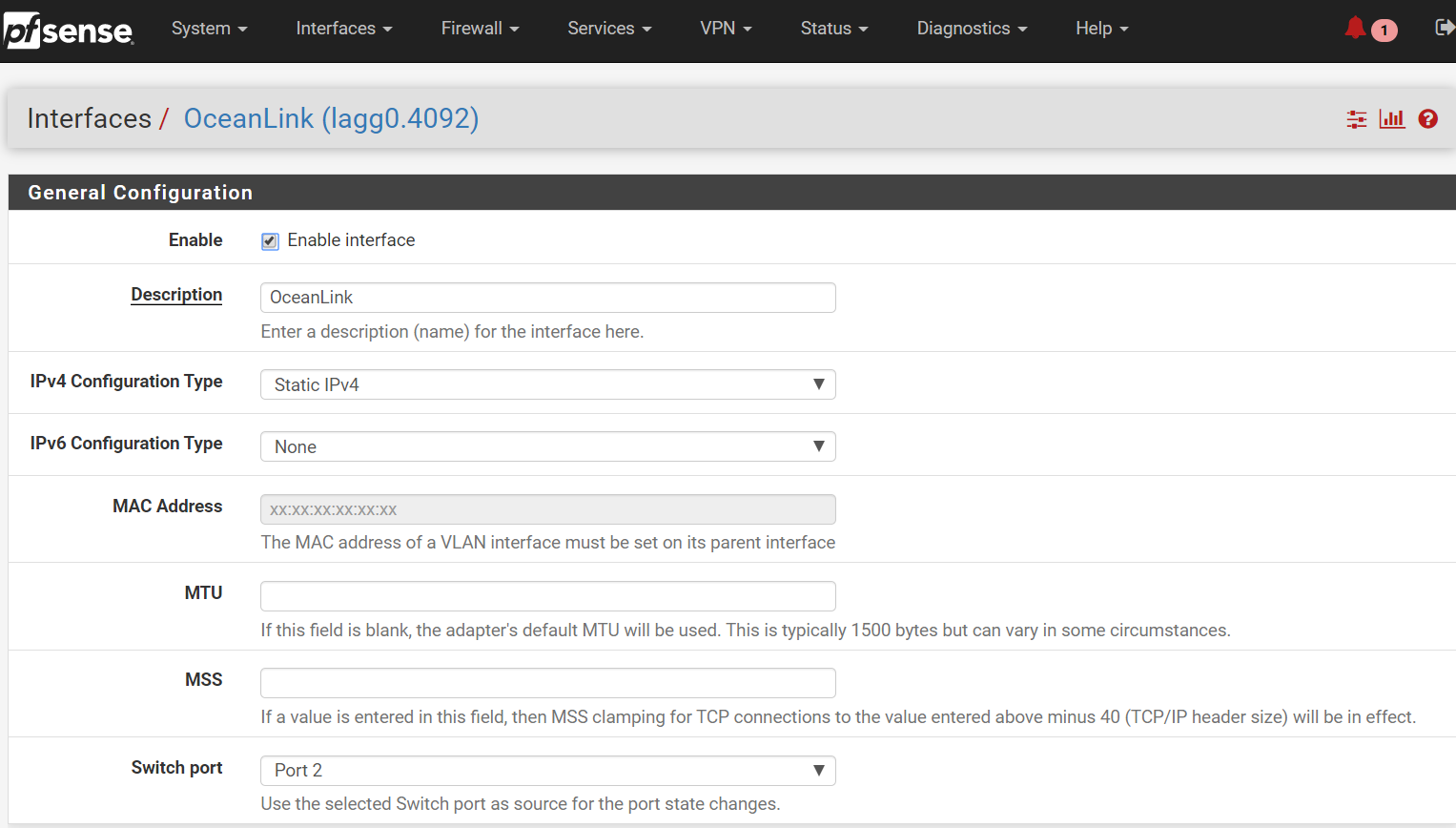
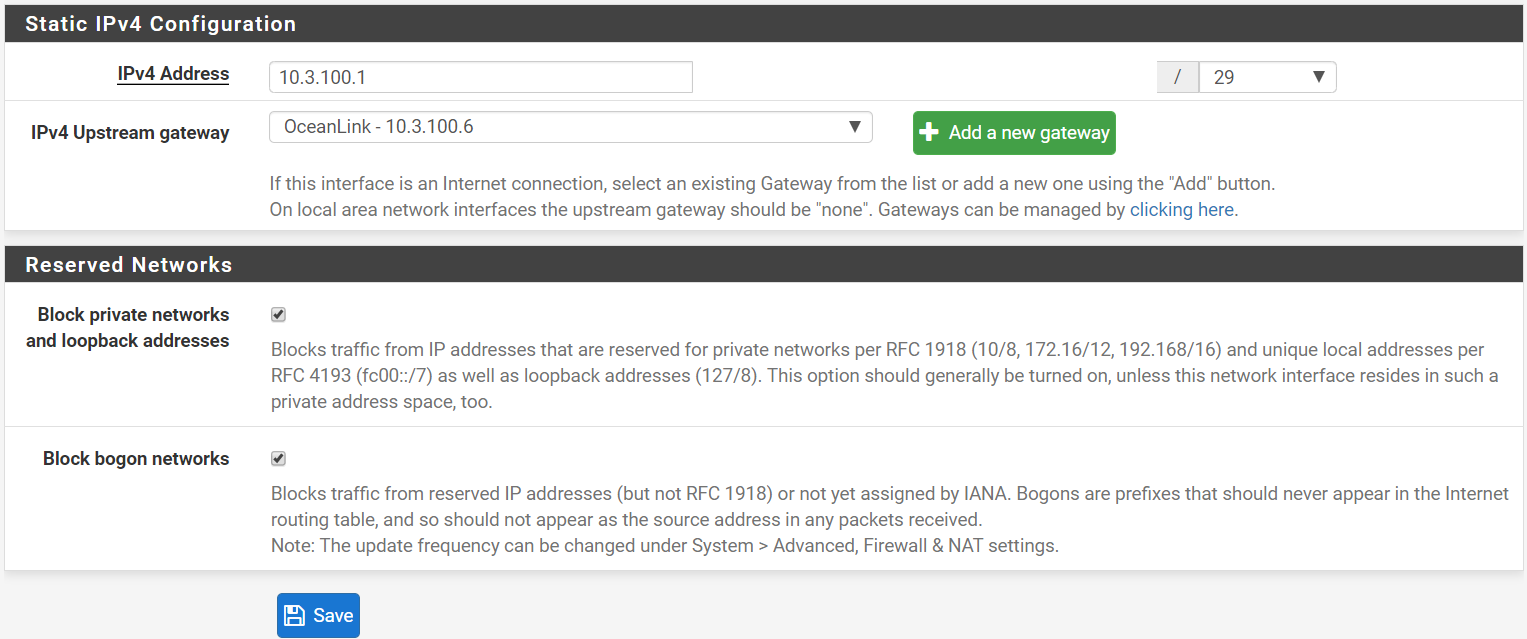
-
What it that floating rule applied to?
-
floating rules applies to Lan + other vlans created. Beside the floating rules I also set each vlans to use groupgateway instead of the default.
see below for one of the vlans I created
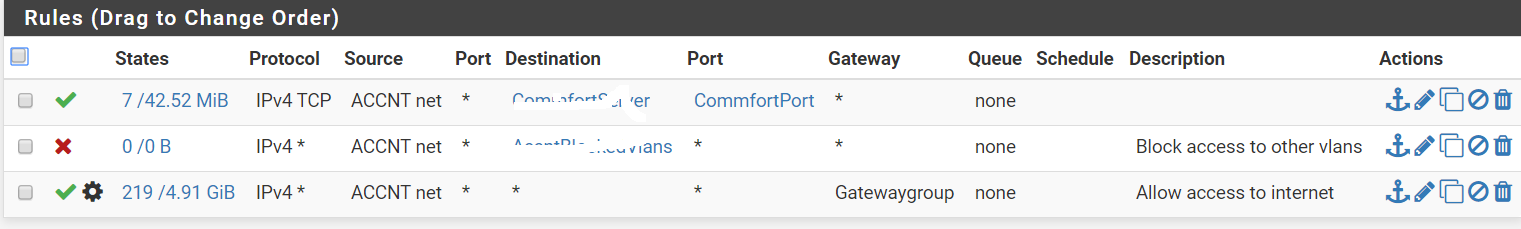
-
Hmm, that floating rule cannot be applied correctly. There are no states and no traffic recorded against it. Instead evetything is hitting the rule on the interface.
However that should work for load-balancing as long as clients are using some DNS server other than Unbound in pfSense.Does it load-balance correct when both WANs are up?
Steve
-
@stephenw10 Are you suggesting to force vlans to use Unbound (pfsense) as the primary DNS and block outside DNS request ?