XG-7100U PPPoE static IP w/ vlan
-
Hey folks,
I'm just getting fired up with a new internet provider (CenturyLink) and they have a bit of an oddball setup for me. Combine that with my having only a basic understanding of the 7100's SoC switch and I've gotten myself in a bit of a pickle. I've got the PPPoE configuration worked out (easy mode) but I've not been able to figure out a way of passing the traffic over CL vLAN (201) without tearing down 802.1q. Anyone have some good links or search terms that I might have not thought of to find the solution here? The thing that's throwing me off is 802.1q seems to be stripping the vlan tagging once it goes external and I haven't found the right place to apply the vlan to the actual WAN link.
Thanks for any advice you may be able to provide!
-Rob
-
https://docs.netgate.com/pfsense/en/latest/solutions/xg-7100/switch-overview.html
Access Port:
Adds a VLAN tag to inbound untagged traffic
Trunk Port:
Allows tagged traffic containing specified VLAN IDs
In the default configuration, two VLANs are used to create the ETH1 WAN interface and ETH2-8 LAN interface:
WAN
VLAN 4090
LAN
VLAN 4091if i understand it right,4090 is access mode and you need to set the vlan to 4091 to set it as trunk, but idk i can be wrong
-
Check out https://www.netgate.com/resources/videos/configuring-netgate-appliance-integrated-switches-on-pfsense-244.html for a better understanding how the XG-7100 switch works.
-Rico
-
Were you able to resolve this? You need to pass the PPPoE connection out on a VLAN tagged 201?
Steve
-
Hey folks,
Thanks for the feedback. I haven't had an opportunity to get back to my stack yet but will try the things and let you know how it progresses.
@kiokoman - I think it needs to stay in access, as trunk mode lets any vLAN pass and I need it to be forcing everything over 201. Where I'm lost is that it seems to only be passing the vlan internally and I don't see where to change that handling. @Rico dropped a link that seems valuable but I haven't been able to get through the video yet. At the very least, it looks like it should have some good pointers to direct my further searches, as my issue is understanding how the vswitch is handled.
@stephenw10 I've not figured it out yet but I also haven't really been able to address it after the link rico sent.
I've got a few minutes at work today and am going to try to get through the video now. I'll ping back if I have any "ah ha!" moments.
-
Update:
I've been bouncing around quite a bit but I did what I thought was the needful and set eth1 to tagged on the switch. From what I've gathered, that should have tagged all traffic coming through the interface and resolved my issue with traffic not being properly tagged. I was not successful. Obviously, I'm still missing some details here.
Some interesting information regarding an older issue with PPPoE and vLAN's that was marked resolved then re-opened on p3:
https://docs.netgate.com/pfsense/en/latest/releases/2-5-0-new-features-and-changes.html?highlight=ppp#interfacesI'll keep poking at the setup to see if I can figure out what I'm doing wrong here.
I know I could tear out 802.1q and relatively easily get things up and running but I'd like to figure out how to do this the right way. I'm just missing some fundamental blocks of knowledge.
-
Ok here's what you need to do:
Add the new vlan 201 interface:
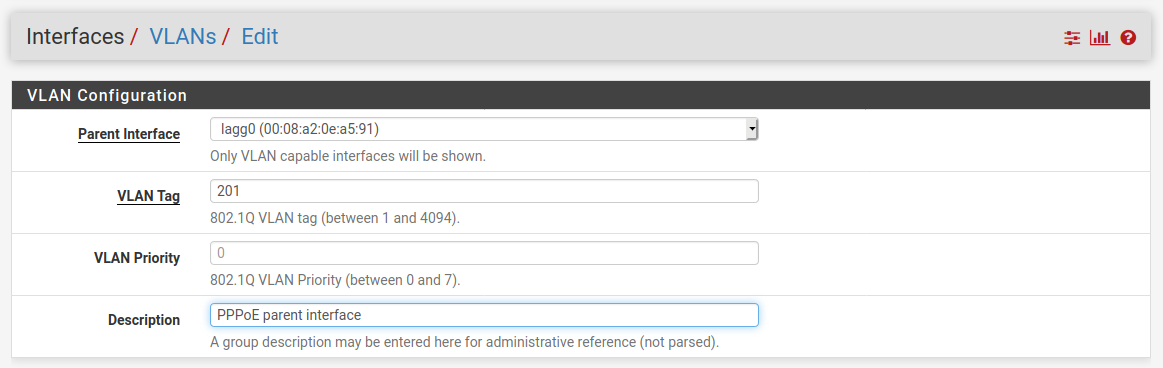
Create the PPPoE connection on that VLAN:
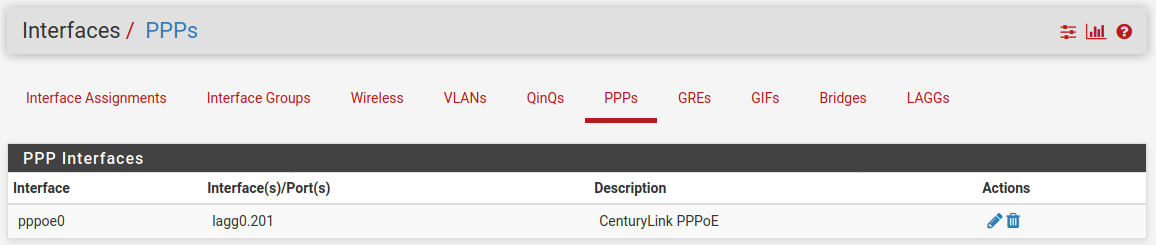
Assign that as the WAN:
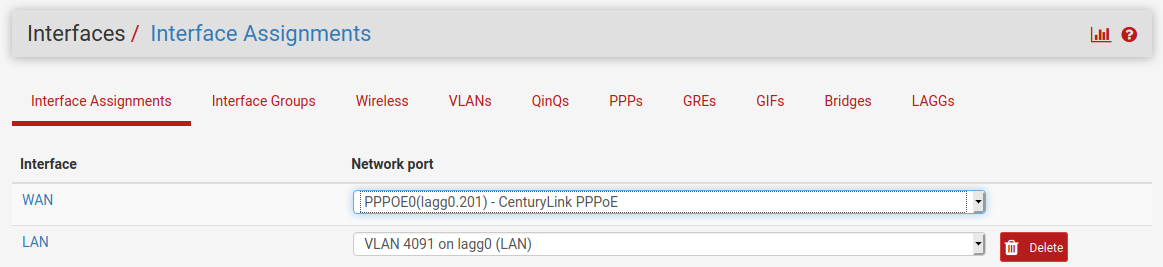
Configure the switch to trunk that VLAN tagged from Eth1:
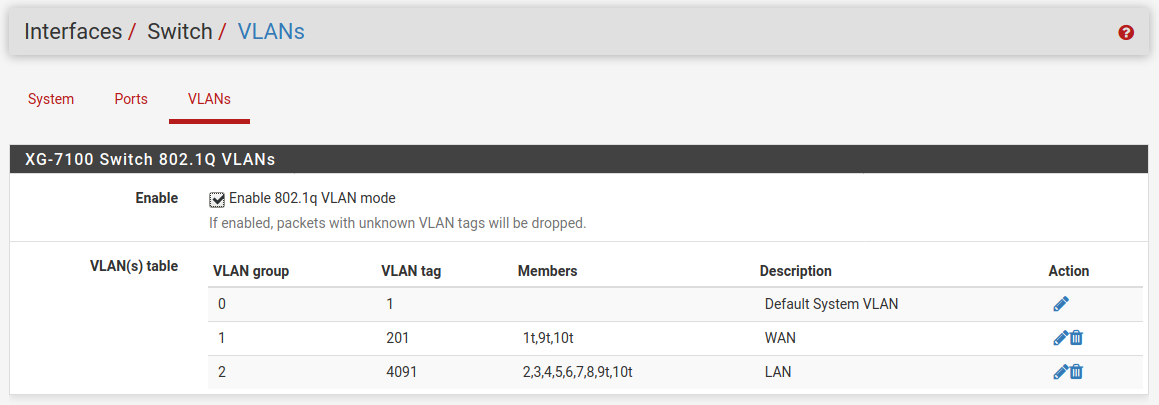
Enjoy the fruits of your labour.

Steve
-
You rock!!! I was putting the right configs into the wrong places. It's up and running now!
-
Great to hear.
