How to get 2 separate networks to talk to each other?
-
@johnpoz
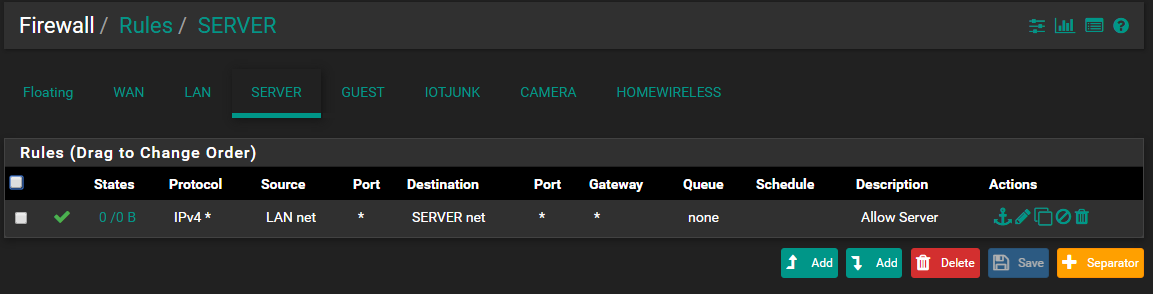
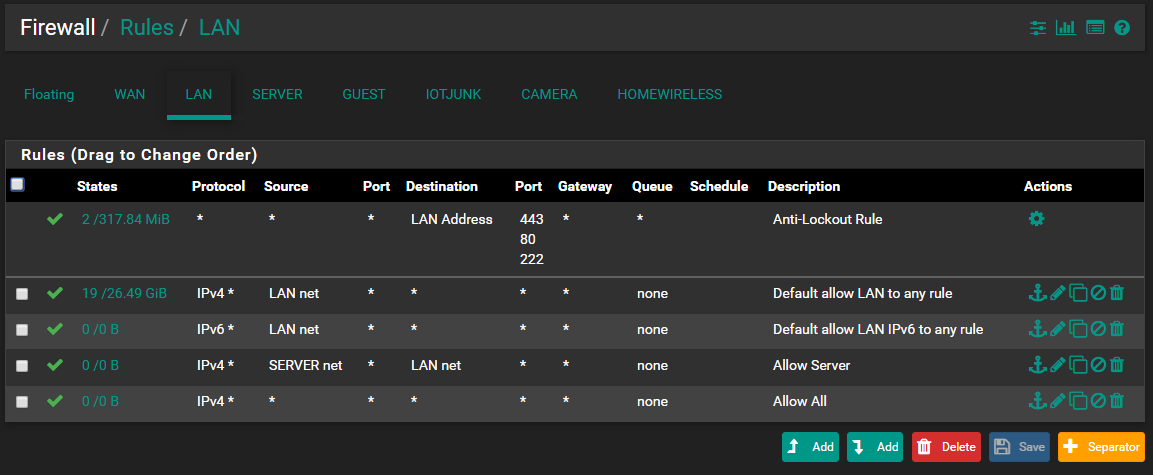
Current floating and LAN rules
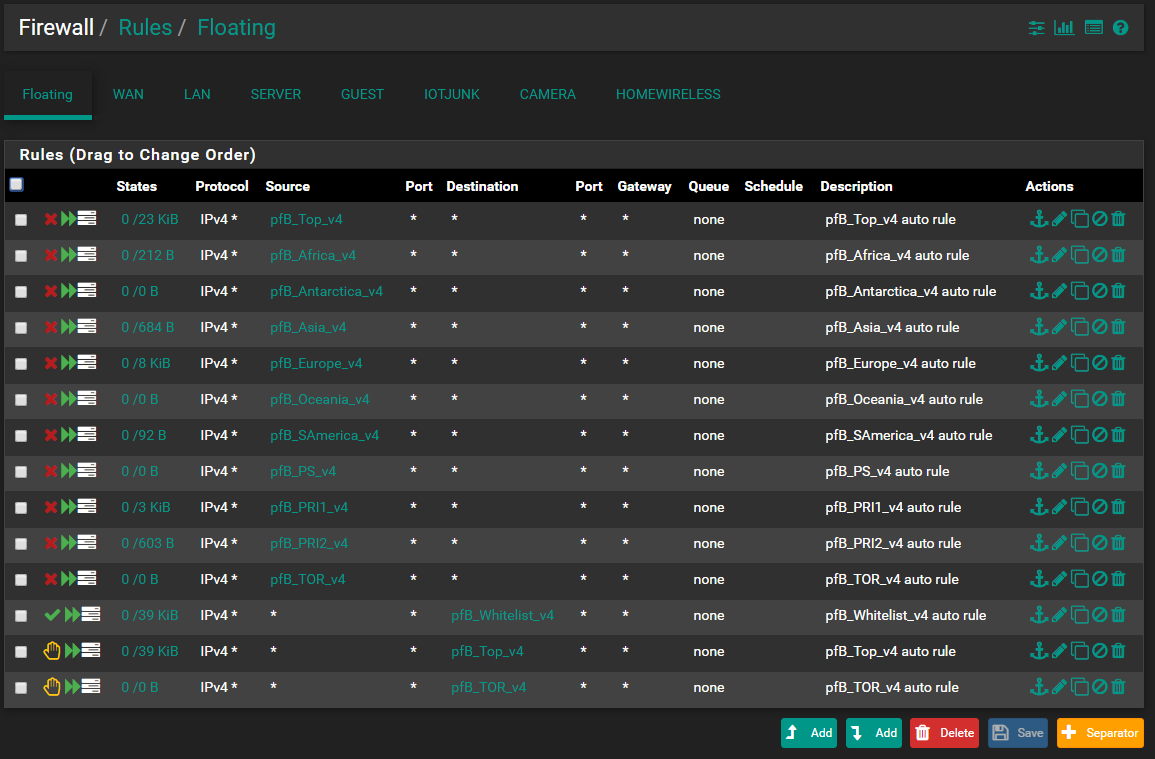
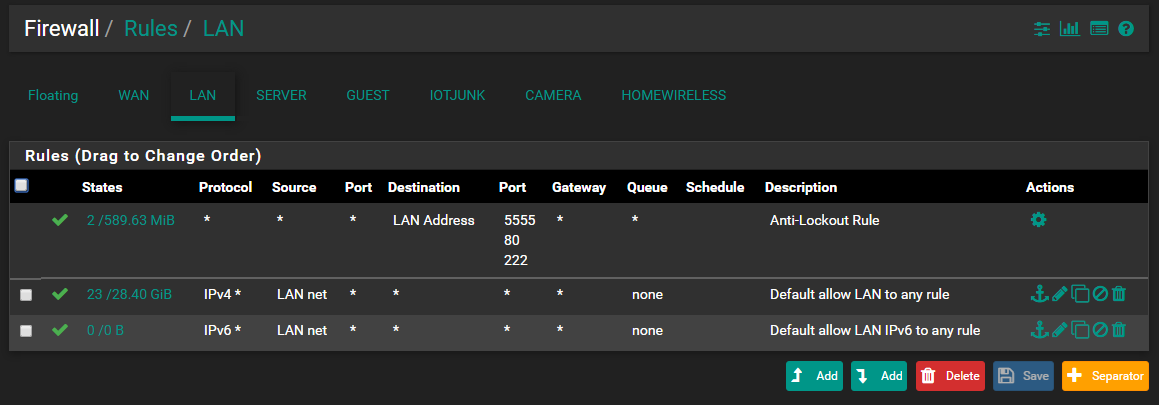
-
Well what interfaces do you have all those rules on? Its quite possible your blocking something in all those rules...
Disable them all for "testing"
Your lan and server rules mean nothing for pinging from pfsense - the only thing that could cause what seeing would be a outbound rule on your server interface blocking pfsense from sending the ping even..
What are you rules on your server interface?
-
@johnpoz
So counting from top to bottom, the first 11 rules (pfB_Top_v4 to pfb_TOR_v4) - all 11 have the same setting with block to WAN interface only (only WAN is highlighted in interface box).
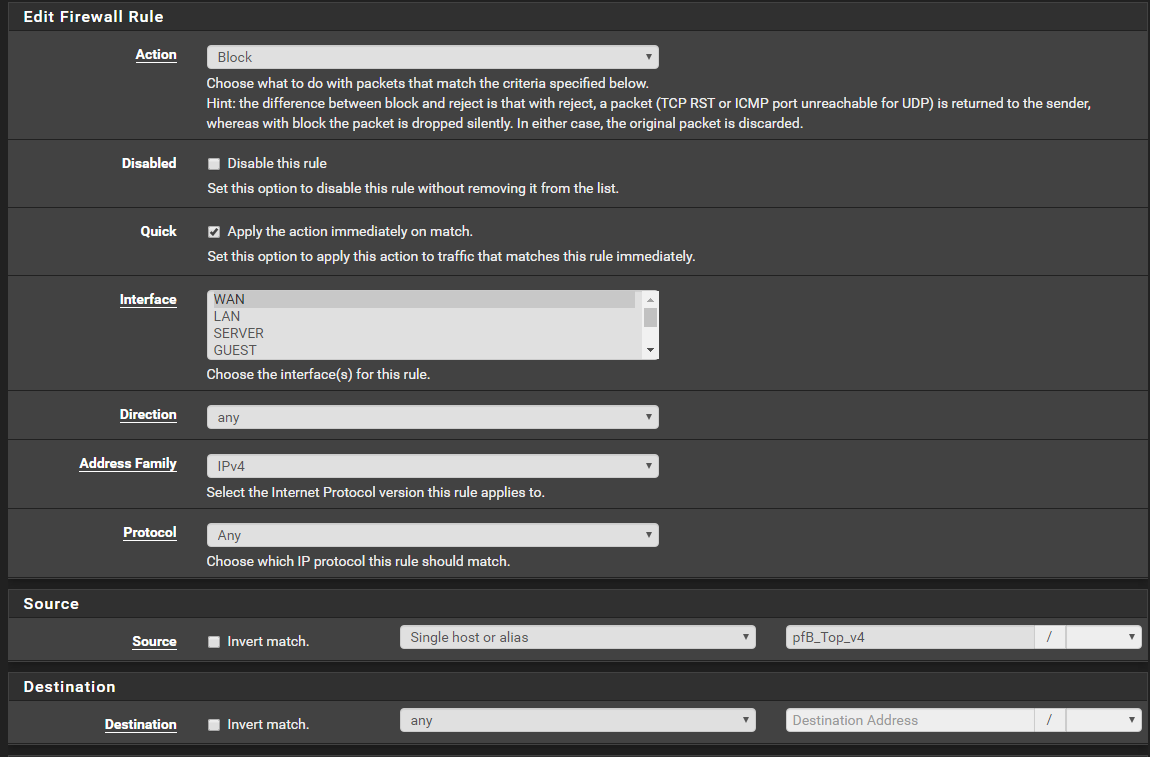
-
Ok well your server interface rules would not allow ping.. So that explains why pfsense would not answer ping.
Set a rule to allow ping to pfsense server address.
And possible dns is not listening on on 70.1Set your ping rule, and try to ping from server again to 70.1
-
@johnpoz
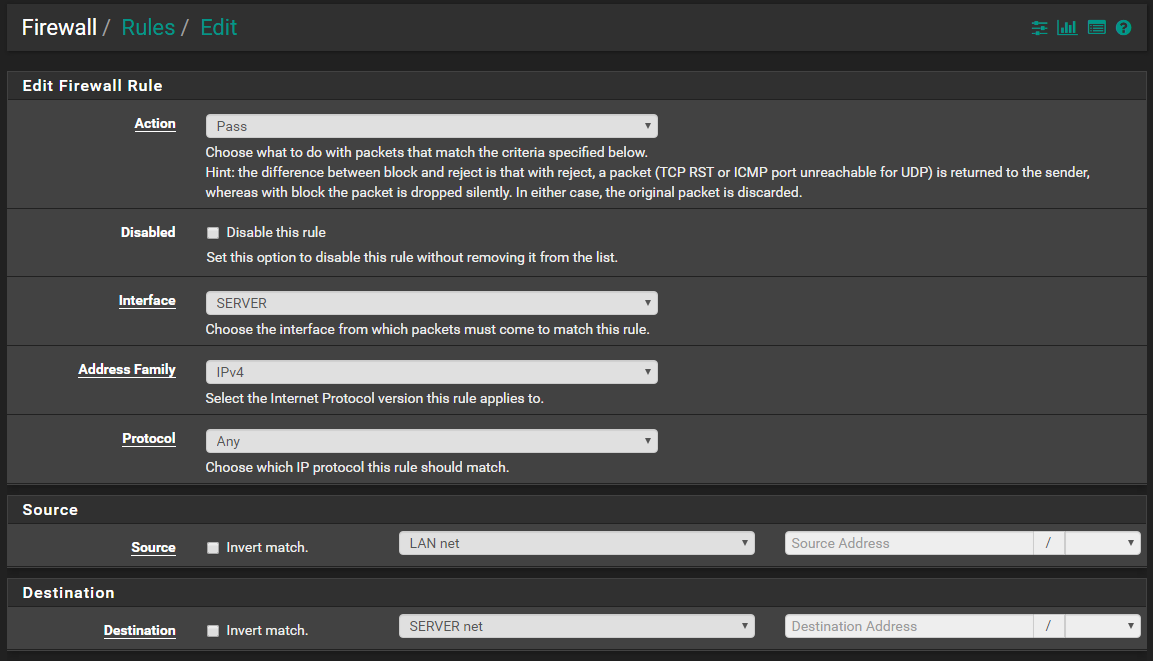
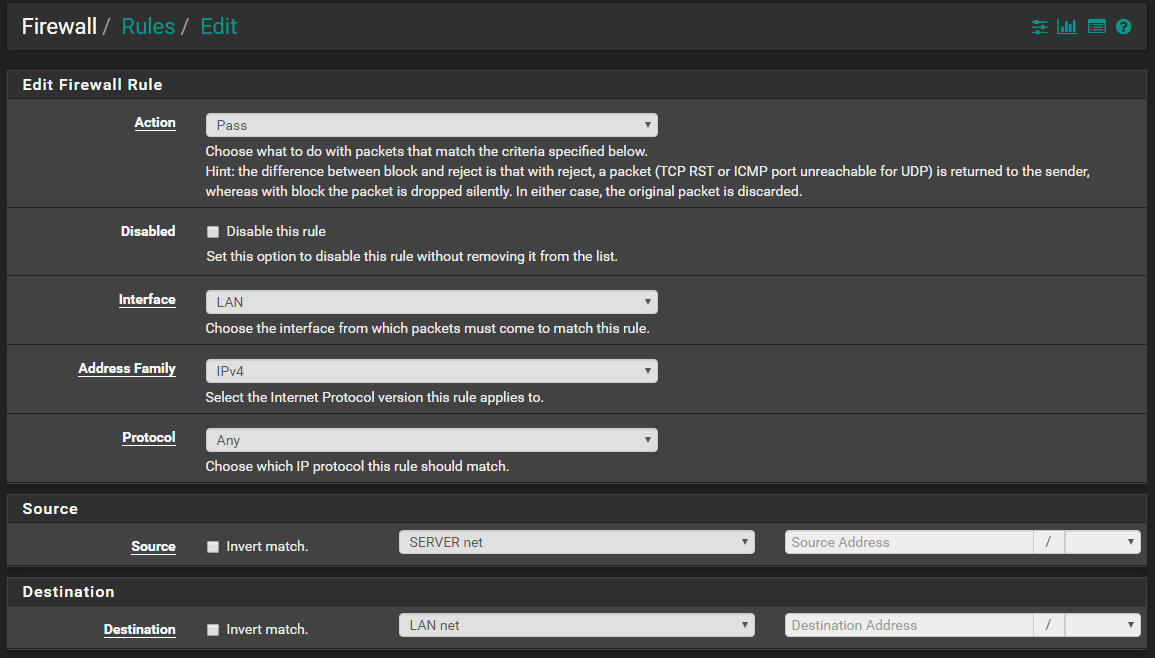
Is this the correct way to set up this rule?
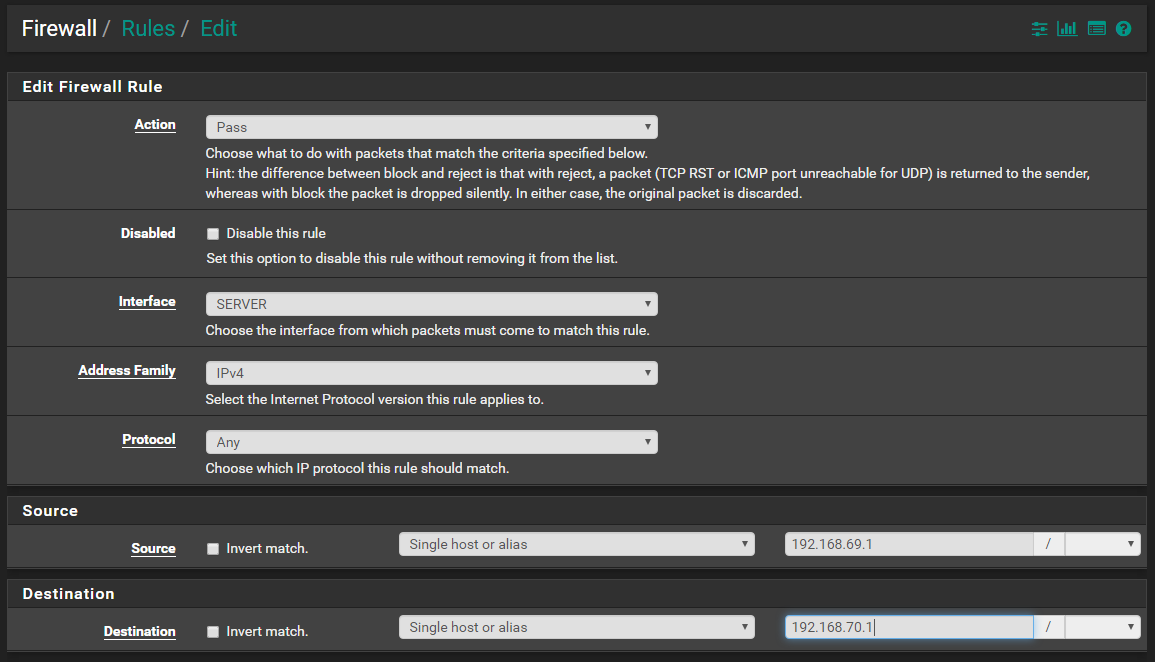
-
No!
On your server interface allow ping to the server address.
example
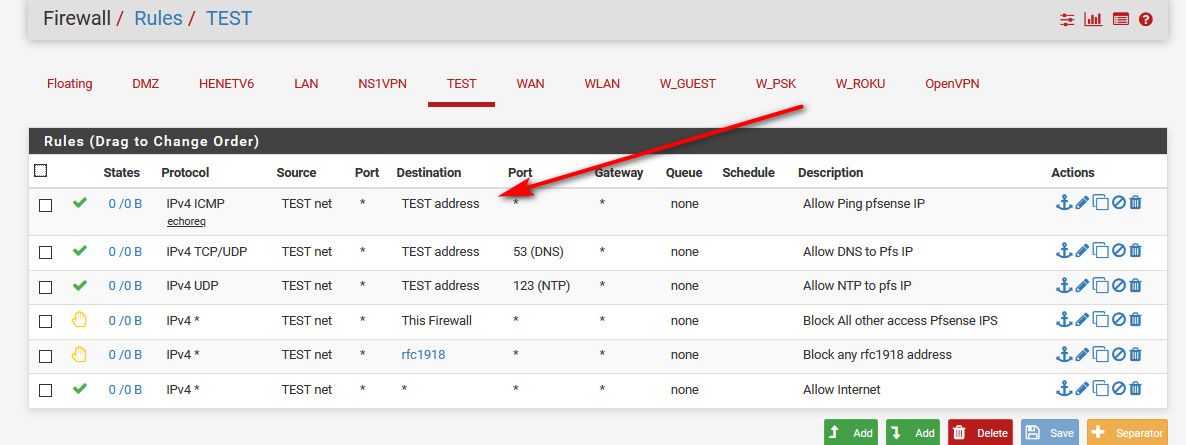
You want to allow your server to ping pfsense server IP 70.1 - lets get that working atleast!
-
@johnpoz
Ping resulted in 100% packet loss
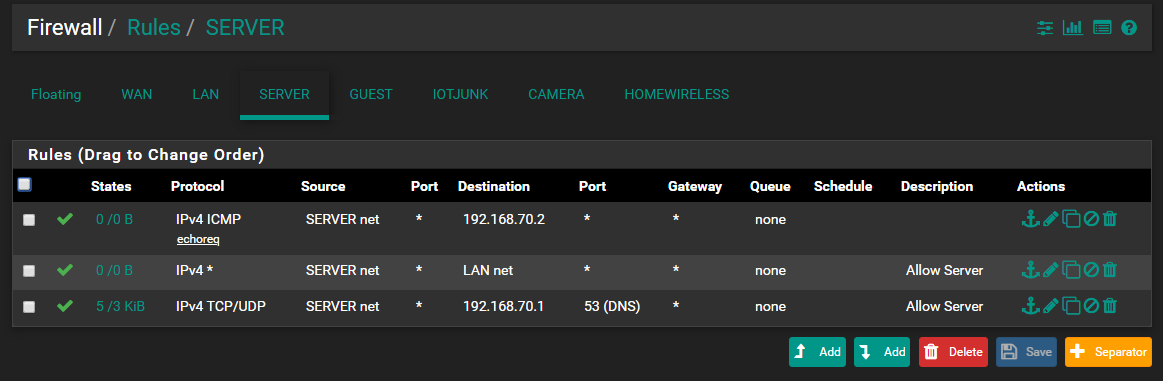
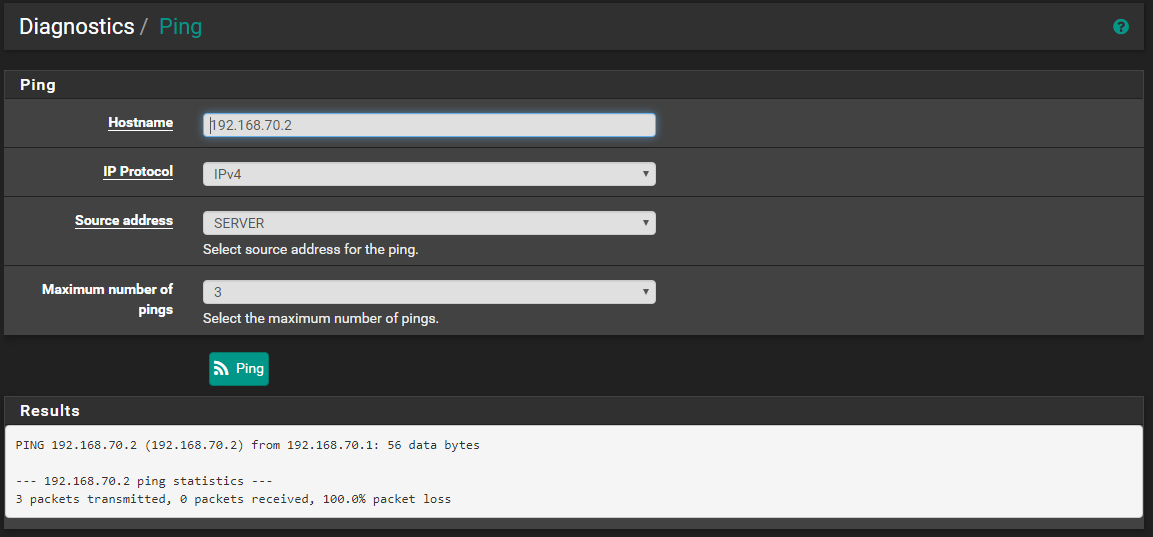
-
OH my GAWD!! dude... how is the dest 70.2 that is not pfsense IP address!!
Please set a rule on your server interface to allow PING to pfsense address server address.. And ping from your server..
-
@johnpoz
Sorry! Dumb mistake! Fixed it. I pinged from the NAS and resulted in packet loss
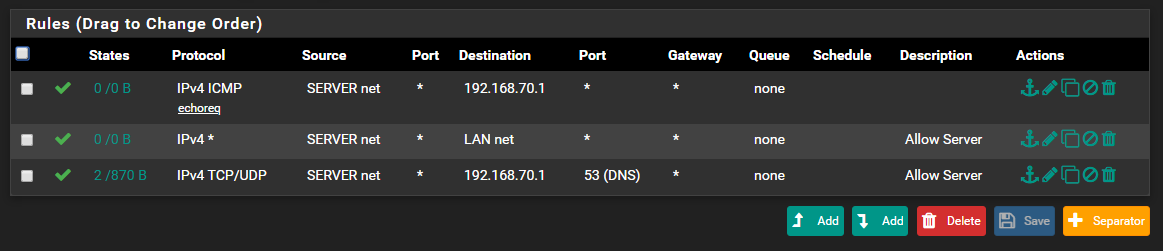
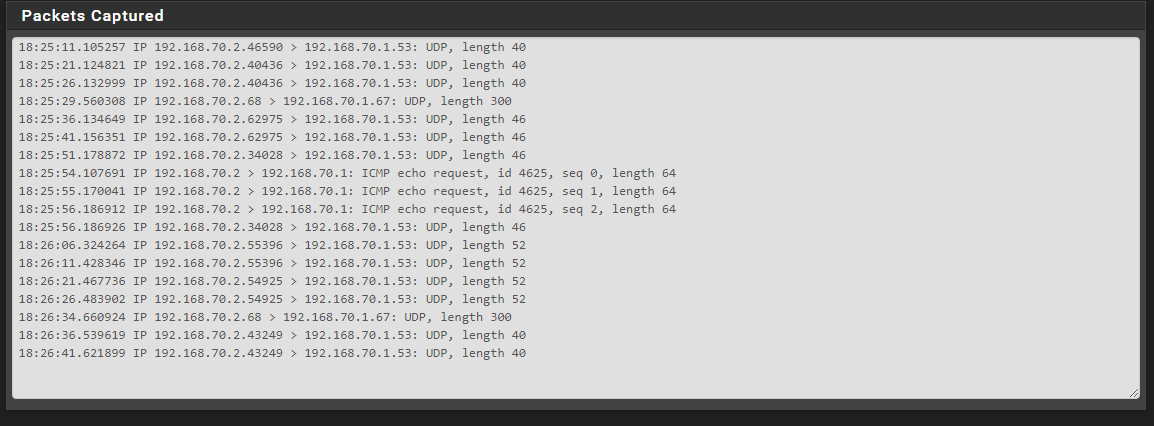
-
Well there is something major wrong... You sure pfsense IP is actually 192.168.70.1?
Can you use a different interface? You don't have any vlans setup or anything like that?
Why was there no answer to the dhcp you show there on port 67? You can arp, but not doing any sort of traffic... Makes no sense at all..
-
@johnpoz
The vlans are all on the LAN side (192.168.69.1) with switch.
The SERVER side has nothing, just a straight direct connection to NAS. -
Well makes no sense at all... Do you have another interface you can use? Another cable.. Post a ifconfig output on pfsense. If it was a bad cable - you would think you wouldn't see the traffic too pfense, and you would see traffic out even if didn't get to the client when you sniff when you pinged.
-
-
dude... How do you have 192.168.70.1 on igb2, and you also have it on igb1.70??
Pfsense shouldn't even let you do that - because the interfaces overlap!!
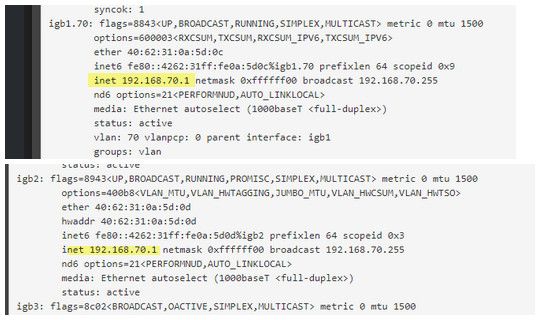
Yeah that is not going to work ;)
-
@johnpoz
igb1.70 is a vlan right? That was deleted sometime ago and doesn't exist currently? Here's all of the vlans as of now: -
But the interface is still there via your ifconfig - so yeah that not going to work ;)
I would check in your xml - forwhatever reason its still there.. So yeah big issue!
-
@johnpoz
Nice! How do I get rid of it cleanly? This doesn't actually show up on my GUI. I have routine XML backups so doing it through XML shouldn't be a problem. -
I would look in your xml to see if its stuck in their somehow.. Then you could remove it from the xml and then reload.. Then do a reboot to validate it goes away.
You could remove it from cli command - but if its stuck in some xml, then on a reboot it could get put back.
I thought I was going nuts - cuz it sure didn't make sense. But now seeing you have 2 interfaces with the same IP makes sense that it was sending traffic out the other interface - or trying ;) So yeah our symptoms make sense for this sort of issue.
-
@johnpoz
Oh so I can just go through xml and delete all lines related to igb1.70? Just to be clear on the correct way:- Delete igb.70 from xml
- Restore new xml
- Reboot and check xml again
-
Yeah must be something left in the xml I would think... Or maybe the interface just didn't get delete.. But I have to assume you have rebooted at some point in troubleshooting this.
So I take it something must be messed up in the xml.
So validate its not in there in some messed up way.. If it is, remove it and then restore it. And then either delete the interface with cli, or reboot and make sure that igb1.70 interface is not there.