pfSense / Unbound / DOH support for ESNI?
-
Hi,
I've got Unbound set up as the resolver on my local network. It's set up to forward using DOH / TLS.
I tested for encrypted SNI (ESNI) using CloudFlare's tool (https://www.cloudflare.com/ssl/encrypted-sni/), and I see that ESNI is not working.
I can get ESNI working in Firefox with the same DNS provider by setting configuring DOH in the browser settings and then setting network.security.esni.enabled=true. If I do that ESNI shows up as working in CloudFlare's tool, so I know it could work.
I checked the docs and Googled to see if there is an Unbound server directive to enable ESNI. I couldn't find anything. Can Unbound's DNS / DOH forwarder support ESNI?
Thanks!
-
Unbound does not do anything with DoH. It only does DNS over TLS.
DoH is between the browser and the DoH server.
-
First: I'll say that you should do what you are comfortable doing for any reason you want. It's not my intention to tell you what to do or why. I will however point out that DoH or DoT does not obscure your browsing history from anyone, just makes it a little harder to do.
Yes, you are hiding your DNS queries/responses but all of your traffic is still out in the open. Every host you connect to, unencrypted or encrypted, can be scraped up and associated with other information about you. By hiding your DNS traffic you take away the easiest method but if your ISP wants to collect, aggregate and sell your browsing history they can do so relatively trivially.
Who do you trust? Your ISP? Cloudflare? Google? There is BIG money in surveillance capitalism. Just because a company is not selling their logs now doesn't mean they won't do so in the future, with or without notifying you. You would have to wade through the privacy/terms of use agreements and see what they reserve the right to do whenever they want.
IMHO the best practice is to use unbound as your resolver. If you really must, route that traffic through a VPN tunnel. If you are committed to hiding your browsing you would need to route everything through a VPN tunnel (and trust that VPN provider).
As I said, you do what you want. Not my place to say one way is better than another. Just do so knowing what is going on, what you are hiding and what isn't hidden by DoH or DoT. Money is a big motivator and few companies are able to resist the lure of that easy money.
Edited to add: TOR isn't a perfect solution either. Being a know cesspool of nasty business there are many compromised exit nodes. Like is often true, a few bad actors make it so the rest of us can't have nice things.
-
@jimp That confuses me a bit. The Netgate blog itself says pfSense supports DOH (https://www.netgate.com/blog/dns-over-tls-with-pfsense.html). The attached screenshot of the setting in pfSense's admin seems to do exactly that -- configuring DOH forwarding. In practice tests as doing so when I set it. With that set, all my queries test as being DOH secured as viewed by external servers.
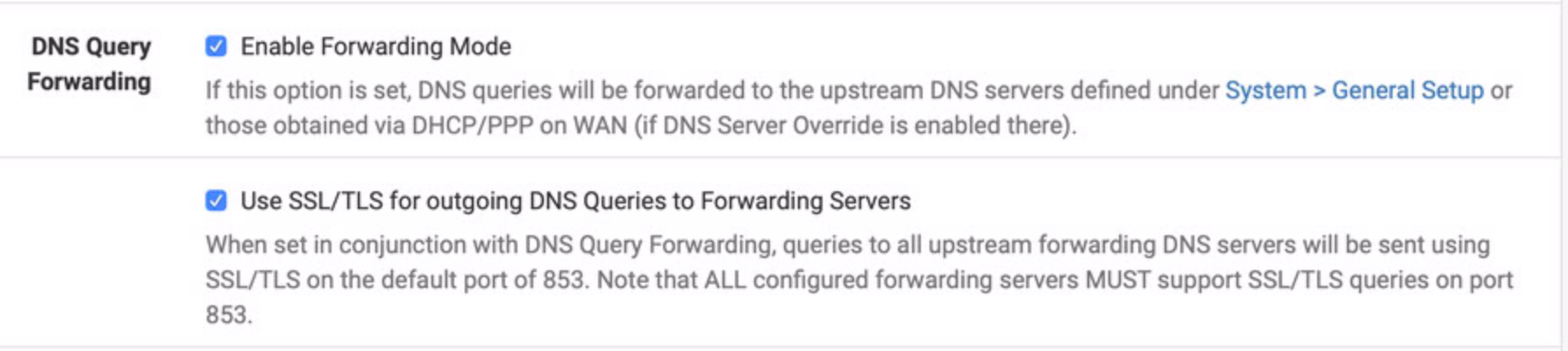
-
That is DoT not DoH. Notice the port. 853 is DoT, DoH would be on port 443.
-
DoT is DNS over TLS is encrypted DNS on port 853 (It's still a DNS request, but wrapped in TLS)
DoH is DNS over HTTPS is encrypted DNS on port 443 (which appears like an HTTPS request)
Completely different protocols.
-
-
I'm not sure that's a factor for DoT but I'd have to check. It would be a factor for DoH but that's still up to the DoH client. That's why it worked when you enabled DoH+ESNI in your browser, because your browser was doing it.
SNI matters for DoH since it's based on HTTPS and SNI is a concept for HTTPS servers.
If you do a packet capture of a DoT request, you probably wouldn't even see an SNI exchange.