(SOLVED)pfSense 2.5.0 and 2.4.5 confusion
-
What vulnerabilities are you concerned about, specifically?
Don't spread FUD!
-
https://forum.netgate.com/topic/149493/12-1/5
-
@akuma1x That's fair, my concerns are coming from the standpoint of if the OS running my network's firewall in anyway has a code bug/exploit etc. It should be patched but pfSense hasn't been patched for a long while now. Even though the underlying OS has security problems being discovered and patched.
Is my thinking flawed in this regard? Should only the network facing program code get patched and all other security advisories don't matter in the context of pfSense?
As you said about only pfsense software being involved. In a sense protecting the underlying OS. Maybe this is why I've been confused I've been thinking that any code in the OS can in be accessed/exploited through the gui. Does the gui create a buffer so to speak?
it would be awesome if Netgate could create a video explaining pfSense from a security point of view. I think I've been thinking about this all wrong.
Thank you Jeff.
-
If there was some critical vulnerability discovered we would release an update to patch that, 2.4.4p4 etc.
Vulnerabilities discovered in FreeBSD so not necessarily apply to pfSense that is only a portion of that code.
We include out own patches to the base code including backports from newer versions where appropriate.As far as I know there no critical vulnerabilities in 2.4.4p3. 2.4.5 will hopefully reach release "soon" and includes numerous for non-critical issues as well as re-basing to 11.3-stable.
If you want to help get that out sooner run a test instance if you can. Hammer on it and find any issues.2.5 will not based on 12.0-rel when it is released as others have said.
Steve
-
@stephenw10 Thank you for the reply. That really helps clear up my confusion around the pfSense releases support issue.
But I still don't understand how security issues are found, if the FreeBSD release pfSense 2.4.4 bases on is eol. Does Netgate test the code for security issues independently of the core FreeBSD devs well past the eol dates? Or do users/pentesters just bring bugs to your attention.
Does backporting mean for instance you would backport this patch
https://www.freebsd.org/security/advisories/FreeBSD-SA-20:02.ipsec.asc
from FreeBSD 12 or wait until 2.5 comes out?I do hope 2.4.5 releases sometime soon in the meantime I'll see about running a 2.4.5 snapshot.
UPDATE:
got a 2.4.5 snapshot installed in a vm. I'm routing through it right now.
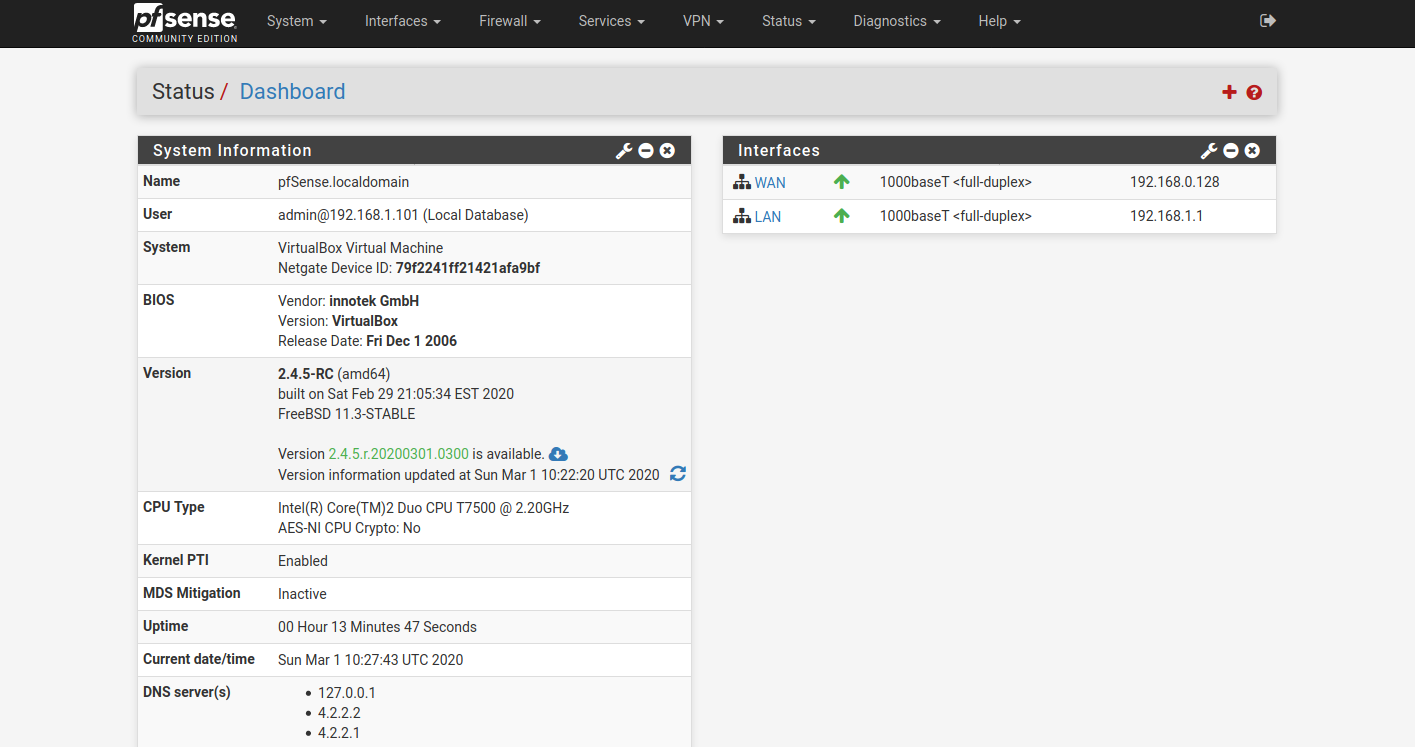
-
Assessing FreeBSD SAs is not something I personally usually do but in that particular case it looks like only 12.0 is affected so pfSense 2.4.x (11.x) would not be. There would be no reason to backport that.
Steve
-
@stephenw10 You're saying some security advisories don't apply to certain versions of FreeBSD at all? Meaning just because ipsec has a new SA affecting 12.X. That doesn't mean the code for ipsec in 11.X has the same issue?
I think I understand it and see why I've been thinking pfSense has had unpatched code all this time. But taking into account what you said. I see why I'm incorrect in thinking that.
I apologize but I really didn't know that until now.... I've learned some valuable things from this discussion so thank you and everyone else very much.
-
Indeed in that particular example it looks like something that was introduced in FreeBSD 12 and does not apply to FreeBSD 11.x.
But even if it did it may not necessarily apply to pfSense.Steve
-
@tman904 said in (SOLVED)pfSense 2.5.0 and 2.4.5 confusion:
You're saying some security advisories don't apply to certain versions of FreeBSD at all? Meaning just because ipsec has a new SA affecting 12.X. That doesn't mean the code for ipsec in 11.X has the same issue?
Read the item you linked.
Affects: FreeBSD 12.0 only
Corrected: 2020-01-28 18:56:46 UTC (releng/12.0, 12.0-RELEASE-p13)If any version of FreeBSD 11.x was affected, it would be listed in the
Affectssection. -
Thank you, I'll keep that in mind for future. I understand why I had confusion and the replies have helped clear it up for me.
Again thank you Jim and everyone that helped.