adding link to my shop
-
OK I finally go the link between the two nano beams.
I run them through the ig2 interface on the router. I can ping the dishes from both sides, I can dhcp an IP from the router, from the router in the shop. so that part is working.
However I cannot ping anything outside the local network from the shop. I looked at my shop_link interface and the IPV4 gateway is set to none. I went to add a gateway, but my router gateway didn't show up.
It seems that I may need to add a gateway for the shop_link interface?
thanks,
david -
no IPv4 Upstream gateway must be none
you have to check firewall rules for that interface
out of the box only LAN is open and can go everywhere if you have a new interface like OPT you need to set the firewall rules yourself first
you can ping your own vlan network because the traffic is not passing through pfsense yet -
I can ping from my lan to the shop_link. I can ping all the nano beam dishes and the router in the shop, all 10.10.1.0/24 ip addresses.
In the shop I can ping the nano beam dishes, but I cannot ping anything else.
The only firewall rules for the shop_link are:
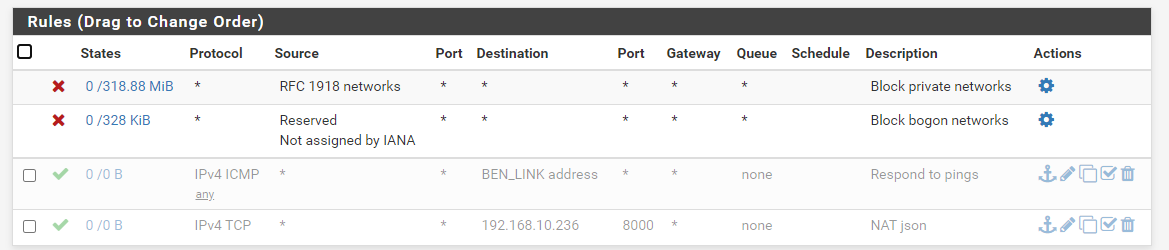
For my gateway interface I just see the port forwarding rules to get to my LAN services. There is nothing there for the shop_link.
Do I add rules to the shop_link interface or the gateway inteface?
thanks
david -
Well your shop firewall rules block everything.. So why would you think you could ping anything?
Why would you be blocking bogon? And blocking rfc1918 is going to prevent you from going to any of your other networks for sure.
-
the last 2 rules are disabled from what i can see
maybe start with a rule that permit any to any and see if it work
you can adjust it later eventually -
@johnpoz
These settings are just the defaults it gets created with. I didn't change any of them.I don't understand what the RFC 1918 or bogon networks are so I didn't change them.
At my shop I don't need access to my LAN, just to get to the internet.
david
-
Pfsense sure and the hell does not create rfc1918 or bogon block on a new lan interface.. Only if you made pfsense think this was a wan interface would it do that.. Which this is not to be honest.. it would be just a transit network to your other router.. Which you don't have or even need..
I even gave a drawing of how you would set this up..
-
@johnpoz
Interesting. i just added the new interface, named it, put in the static IP (10.10.1.1), setup a dhcp server for it.the block bogon and RFC1918 boxes come pre-checked, so I left them that way.
david
-
well anyway remove this from the interface
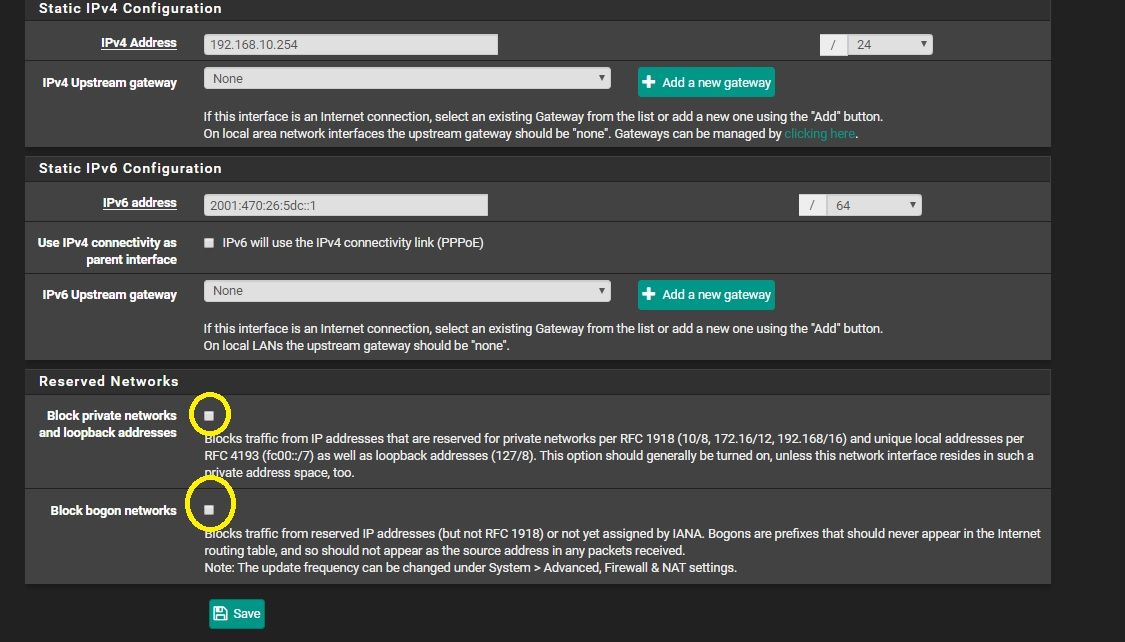
-
Yes, I did that. I can now ping 10.10.1.1
I'll move it over to a VLAN instead of a different subnet. I have VLANs working so maybe the routing is different.
I chose a new subnet because I wanted to use a different interface port. Maybe I can do that with a VLAN?
david
-
I did figure out how to add the dedicated interface to a VLAN, created the VLAN and I can now get to the internet when plugged into the router at the house. Not to get it working on the other end of the nano beams. Need to reconfigure their IP addresses to the VLAN address space.
Not sure why I can't get it working as a 10.10.1.1 subnet, but I do get something now.
thanks,
david -
There is no difference to pfsense of vlan or native just naked on an interface, vs just tagging and not tagging the traffic leaving.. Or looking for that vlan tag on traffic entering the physical interface the vlan is on.
All routing would be the same.. Its just another interface, tagged or not tagged is the only thing that is different..
-
I'm trying to figure out why I can't get access to the shop_link VLAN from my LAN. I've setup the firewall rules just like my other VLANs. I see a couple differences. The other two VLANs share the same interface on the router, while my shop vlan has its own interface.
The shop interface is also called (wan) in pfsense. I think that is because it is the first interface and they seem to be hard coded (?) as wan lan opt1 opt2 opt3 seen here: <had to remove becauase the xml in a code block got flagged as spam>
Does this matter? I have a rule on my LAN interface that should allow me access, at least it works on the other VLANs.
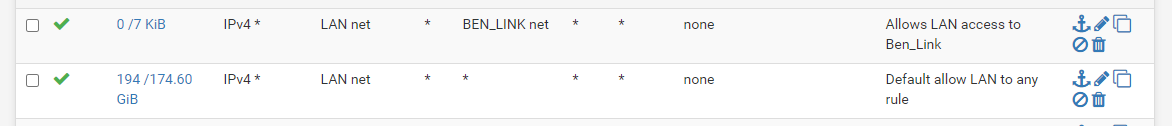
I tried looking in the Firewall rules, filtering on the destination IP to see if I could find the rule blocking my ping tests, but when I ping 192.168.30.116 it never shows up in the firewall log. So it sounded to me like it never got out of the LAN interface. If I ping the router 192.168.1.1 it does show up in the firewall log, but no other destination IP shows in the firewall log.
EDIT: OK I figure out the logging issue, I didn't have the allow rule set to log. When I set to log I do see that the ICMP packet is passed, but I still get 100% packet loss, so it seems the return response isn't getting back.
I can access all the antennas from the shop just fine, but would also like to access them from the house.
Ideas on how to further debug my issue?
thanks,
davidPS. I'm getting a nice steady 27Mbps up and down speed at the shop. It is wonderful!!!
-
Why would you shop network interface be called wan would be you named it that, or you used the previous wan interface that pfsense had set..
You don't need the rule to allow access on your lan, if you already have a any any rule..
How about you actually draw up how you set this up.. And we can work through what you might not have right. It really just comes down to how I drew it.. Fill in the details on that drawing..
What network are you using on this shop network? Your wireless devices - did you setup gateway on them (pointing to pfsense IP in your shop vlan), if you didn't then no you wouldn't be able to talk to them from different network, ie your lan.
If your on a vlan, pfsense would be tagging the output - your AP or devices downstream might not understand the tag.. Do you have a switch between your wireless device that connects to your shop wireless devices.. Did you setup vlans on it?
-
Sure thing. Here is my attempt at using paint to show what I have setup.
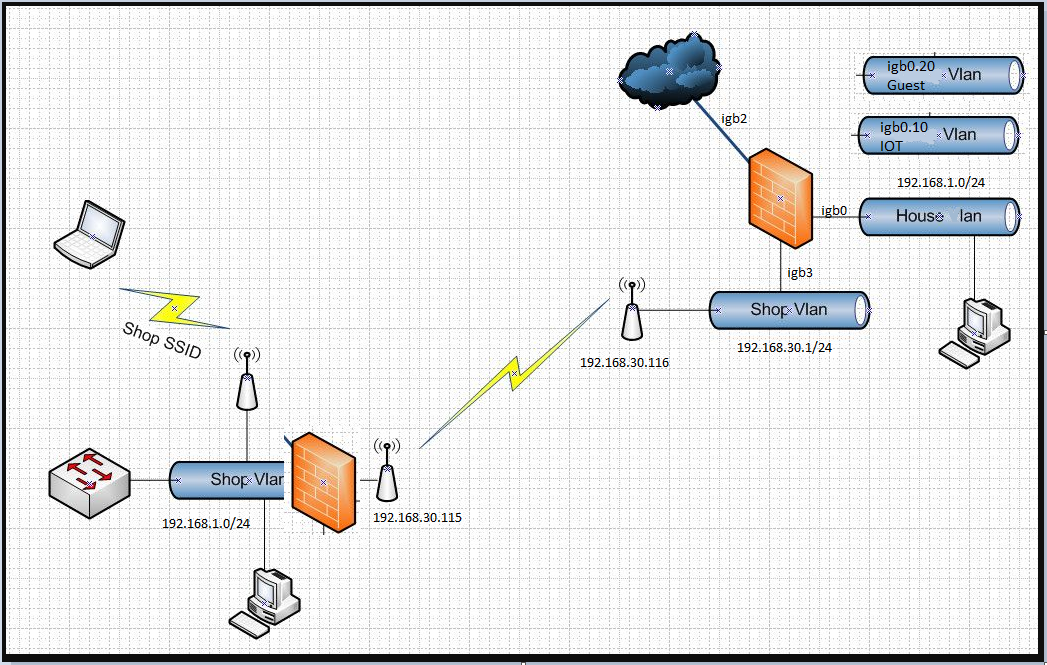
I left the firewall in the shop the way it was because I already have the LAN and VLANs setup and didn't want to deal with that. I also have the shop firewall setup to fail over to the T1 line if the link from my house goes down.
Yes, igb3 was my original WAN a few years ago. When I switched providers I just setup a new WAN and setup WAN failover from igb2 to igb3 during the overlap period. When the other provider went away I just removed the igb3 interface. So I reused it when I hooked up the shop. I haven't found where I can remove the wan label, and don't know if it even matters.
I truly appreciate your patience and willingness to help me.
thanks,
david -
Are you actually using a VLAN to the shop? If you're on a separate interface, you don't need to and it just adds complexity. You only need to use VLANs, when you want to separate networks.
-
^ exactly if this shop network is the only thing on igb3, then there is no reason for a "vlan" its just a native, untagged network now... There is no reason to set up a vlan in pfsense for this.
So you shop network is 192.168.30/24.. This shouldn't be a vlan unless your devices downstream or there is a switch between pfsense and your wifi device that understands vlans and can strip them because I don't you have vlan info setup on your switches and or devices downstream.
I also have the shop firewall setup to fail over to the T1 line if the link from my house goes down.
So your using 192.168.1 behind this firewall? And you also use that network in your house??? Yeah that not ideal to be sure!!!
If that is the case then you should be using transit between your 2 firewalls (both pfsense?) and not natting between these networks, etc. etc. Routes would be setup.. And to your shop firewall connection to house is primary wan, and T1 is backup wan, etc..
the easiest way to make sure you can get to your wifi devices that your using as transit bridge between house and shop would be to source nat traffic to them from one of the locations that is not their default route, if you can not setup routing on the devices. This way you can get to them from either house or shop if one side is down, etc.
-
Yes I do have VLANs in the shop (Guest), and an IOT one, similar to my home.
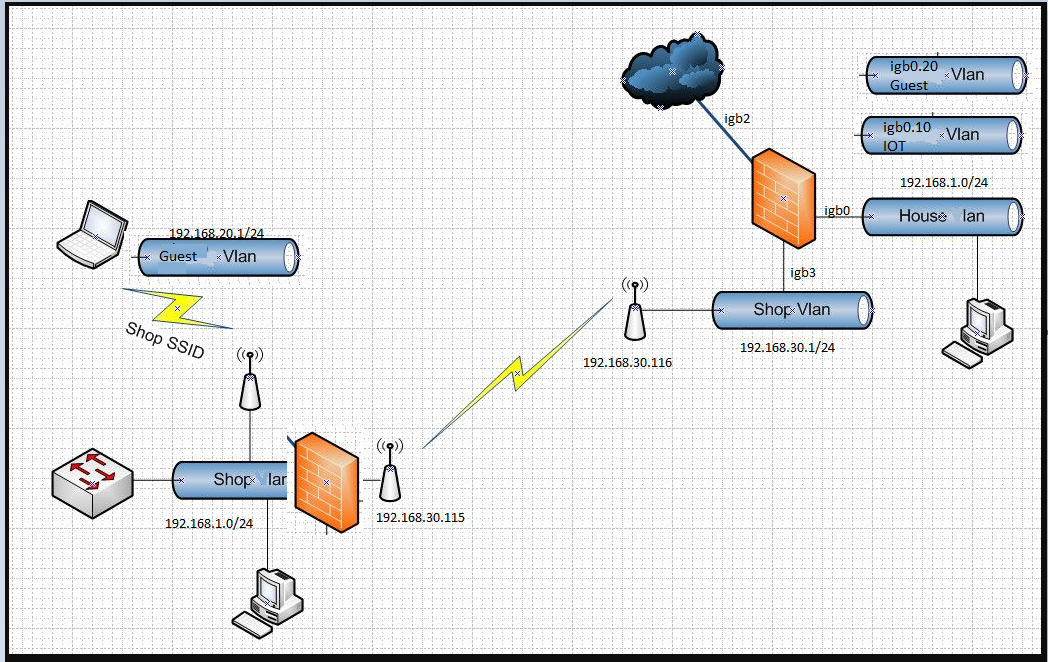
Yes I am using 192.168.1.0 behind the shop router and at the house. This was my original concern.
The primary LAN is not a vlan so I remove the V on that in the picture. The router/firewall in the shop is a Netgear router running Tomato.
I originally setup the link between the house and the shop as a subnet 10.10.1.0/24, and I could get to the nano beams, but couldn't get the shop to route to the internet. When I changed it to a VLAN I could get routing to the internet, but lost routing to the nano-beams.
John, I have no idea what your last paragraph is saying. " source nat traffic to them from one of the locations that is not their default route, if you can not setup routing on the devices.", but like the conclusion.
thanks again,
david -
So your wifi devices 30.115 and 30.116 devices what do they have set for their gateway? Do they have one.. While I have to assume your tomato is natting, which means you wouldn't be able to get to stuff in the shop because its firewalled and you would have to port forward to get to stuff behind your shop firewall.
So while you would be able to get to the devices from shop network because to the wifi devices you would be coming from shop firewalls IP in the 192.168.30 network... From your house side.. They wouldn't know how to talk to some other network, etc..
Your current design with a firewall in shop complicates the setup.. But can be configured to do whatever you want to do, not sure about tomato and its limited feature set... But would assume you can disable nat on specific interfaces?
-
The shop router DHCPs and an IP from the home router, it happened to get 192.168.30.3. I can easily make that as static IP if it makes things easier.
This is what is set as the gateway for the shop devices.
My home devices get the gateway assigned to the igb2 interface, which is my static IP address.
I don't need access to the shop devices from the home, but I would like to get access to the nano-beams. I can see that my home firewall passes the requests to the 192.168.30.0 vlan, but I get no response back. Ping just says no response.
I'd love to be able to remove the double NAT if possible.
thanks
david