IPSec mobile CARP
-
The IPsec tab rule wouldn't be relevant, WAN would be the rules the client hits. But that's not it because you see entries in the client log.
Looking at the message in the log, it's not matching your mobile IPsec config. You can see that it's matching
bypasslaninstead which means that it didn't match the Phase 1 settings. Most likely your IDs or something along those lines is not matching.Go back a bit more in the IPsec log (increase the number of lines it shows, or dump the whole log from ssh with
clog /var/log/ipsec.log.If your IPsec config is using a certificate, the certificate may not include the CARP VIP in its SANs.
-
I just looked at the ipsec logs, I don't understand exactly what I'm looking at, there's a lot of information.
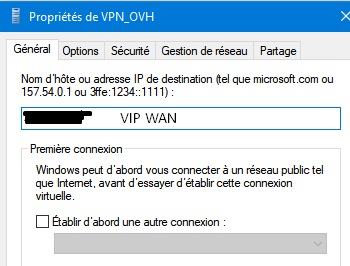
Could you tell me how the configuration of P1 should be with Carp VIP...
My certificate says in SAN: "PfsenseMASTER_OVH.lgdd.local and my VIP"
The same configuration but with the WAN of the pfsense 1 "so no VIP" works perfectly.
So I don't understand why it doesn't work with the VIP.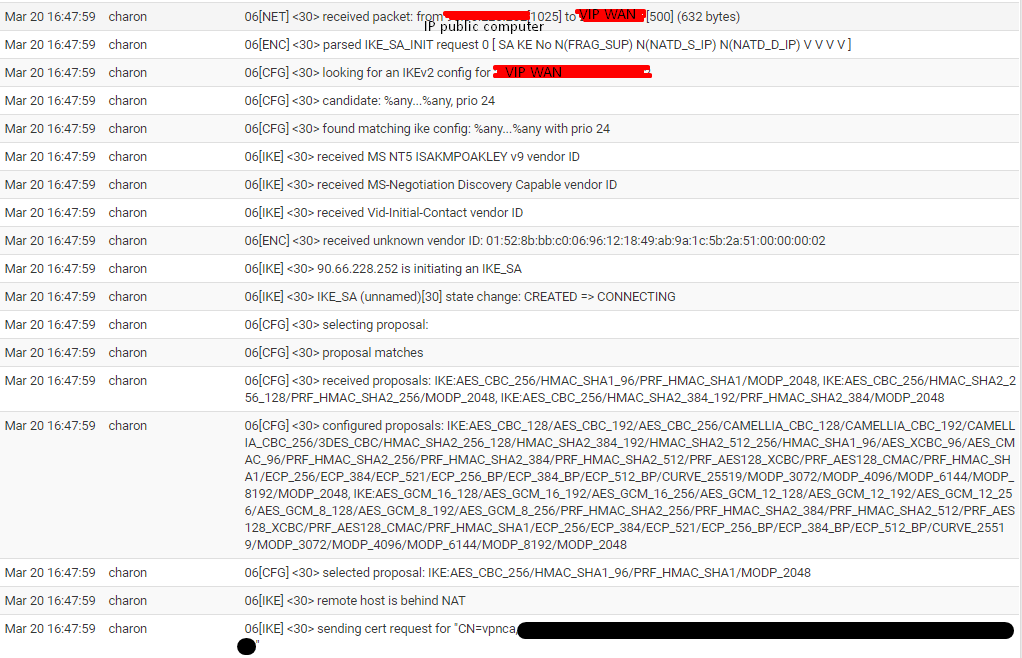
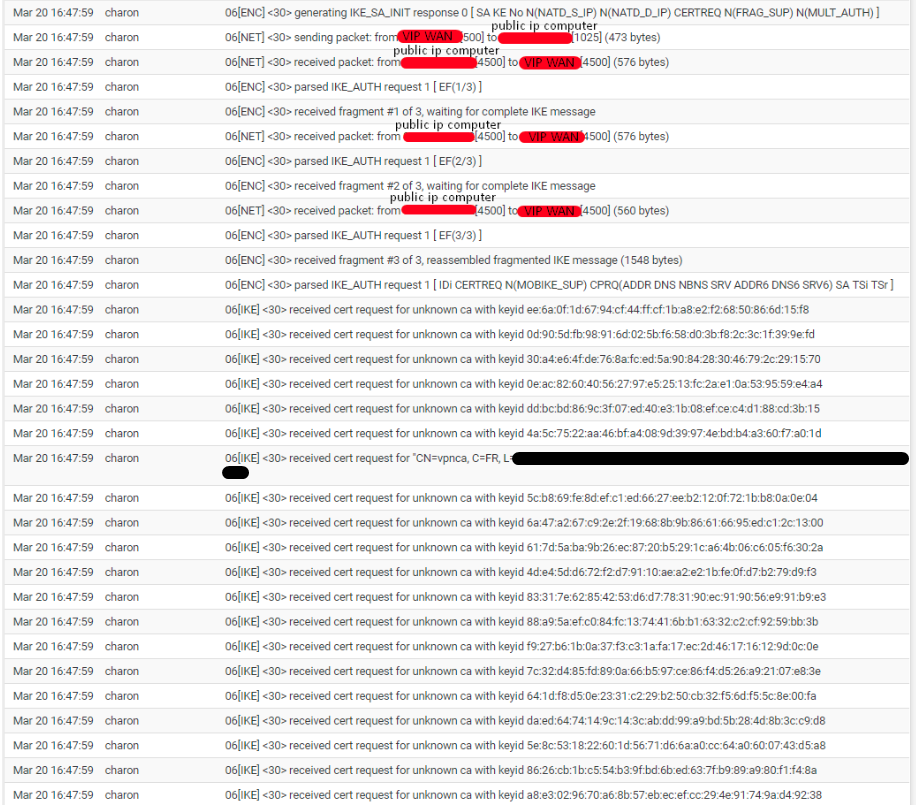
-
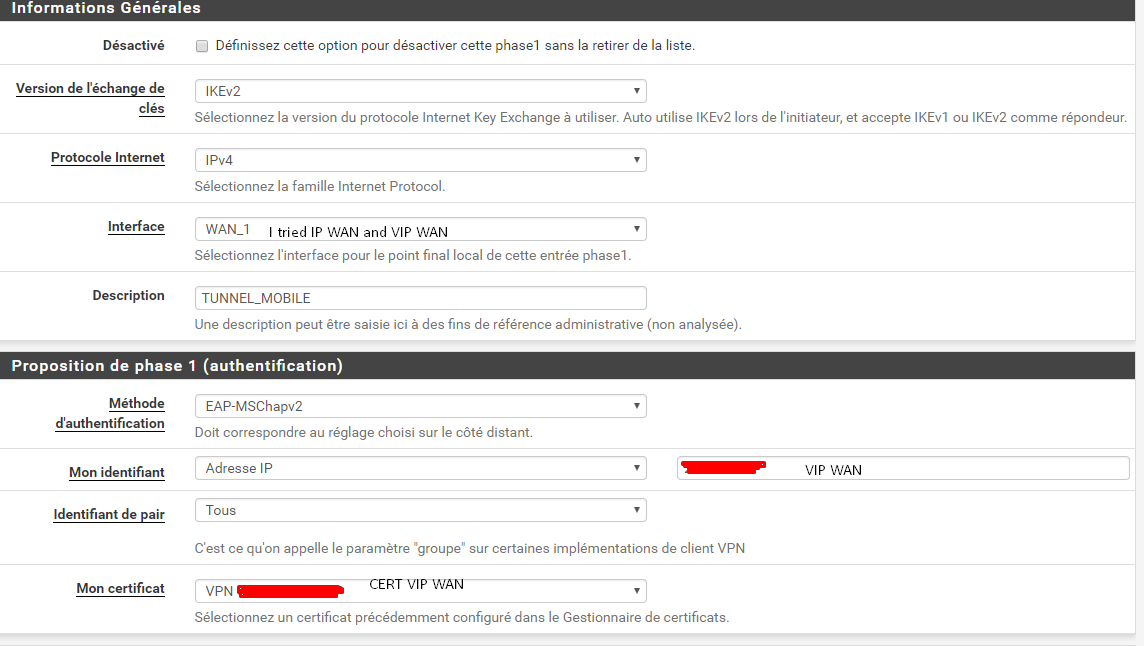
What is the value of "My Identifier" in the Phase 1 authentication proposal on the server config?
If you look at the configuration in
/var/etc/ipsec/ipsec.conf, what does it show forleftid?Normally that would be the hostname of the server, and the client would be connecting to the hostname, which would also match a SAN in the server certificate. And to use a VIP you'd point the hostname to the VIP instead of the interface address. If you use a VIP directly, it should be the VIP in the ID (set to IP Address), in the SAN, etc.
-
/var/etc/ipsec/ipsec.conf
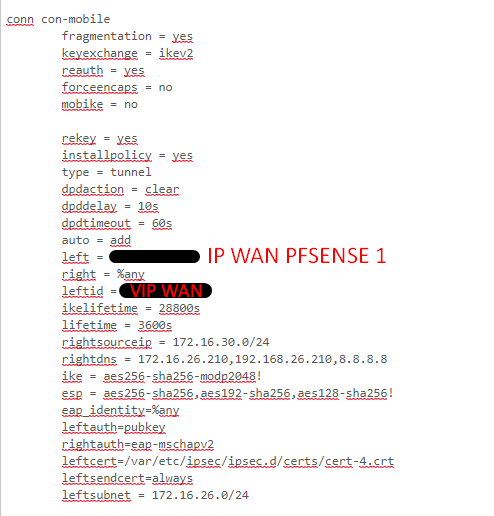
Certificate
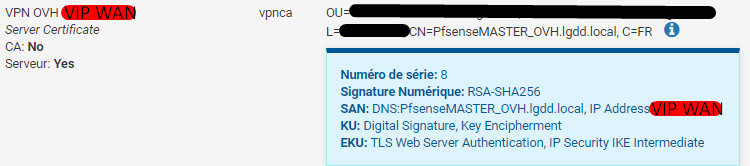
I use this powershell command to create the tunnel as well as other commands but this is the main :
Add-VpnConnection -Name "VPN_OVH" -ServerAddress "WAN VIP" ` -TunnelType IKEv2 -AuthenticationMethod EAP -EncryptionLevel "Required"
-
leftandleftidshould match in your case. Are they really different? Is the VIP selected in the Interface option for the VPN?It would help to see screenshots of the mobile IPsec P1 settings
-
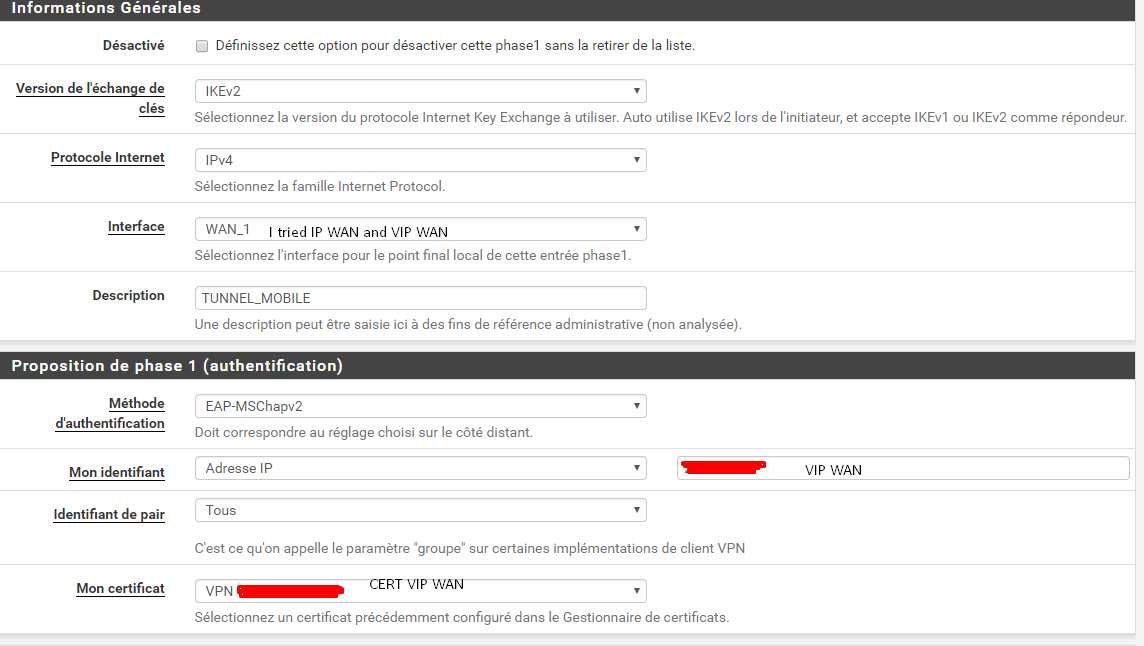
@jimp You have the screen in the very first publication but I give it to you here.
I tried to put the VIP but also my simple interface, in both cases it doesn't work.
-
I meant at it was exactly when you captured the ipsec.conf above.
It should be set to the VIP in the interface and ID. Set it that way. Save, apply. Check ipsec.conf again. Try to connect again and see if the logs change.
-
I checked the configuration file; it's changing fine.
I try to connect and send you the logs.
-
It's good it's working.
That's weird, 'cause I've tried this setup.
It seemed to make the most sense to me.Then I did an "f-route" in my cd to reset my routes. Maybe that helped a little?
Thanks a lot, I'm left with the 192.168.26.0/24 network access problem which is the LAN of another pfsense which is connected to the pfsense with LAN 172.16.26.0/24 through a normal ipsec tunnel.
I do have two P2 one in 192.168.26.0/24 and one in 172.16.26.0/24.
The pfsense which is connected in a mobile ipsec tunnel does receive packets going to 192.168.26.0/24 but apparently doesn't know how to route them to the right destination.My client workstation has the right routes:
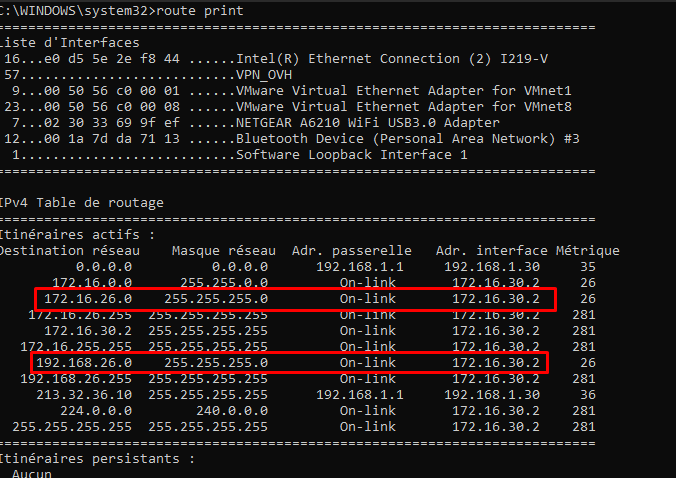
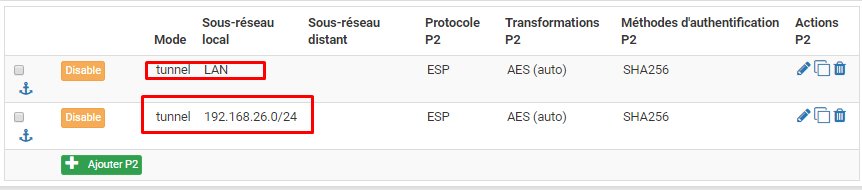
-
You will probably be better off starting a fresh thread for that since it's not related to the original topic here and can easily get lost in the other conversation.
-
@jimp Yes, no problem, thanks you
https://forum.netgate.com/topic/151438/ipsec-mobile-to-an-other-network-ipsec
-
Sorry to bother you again.
Small problem when I connect the mobile ipsec tunnel from a "Windows 10" client machine, everything works.
But when I'm on a Windows 7 machine the connection doesn't work.
Here are the logs: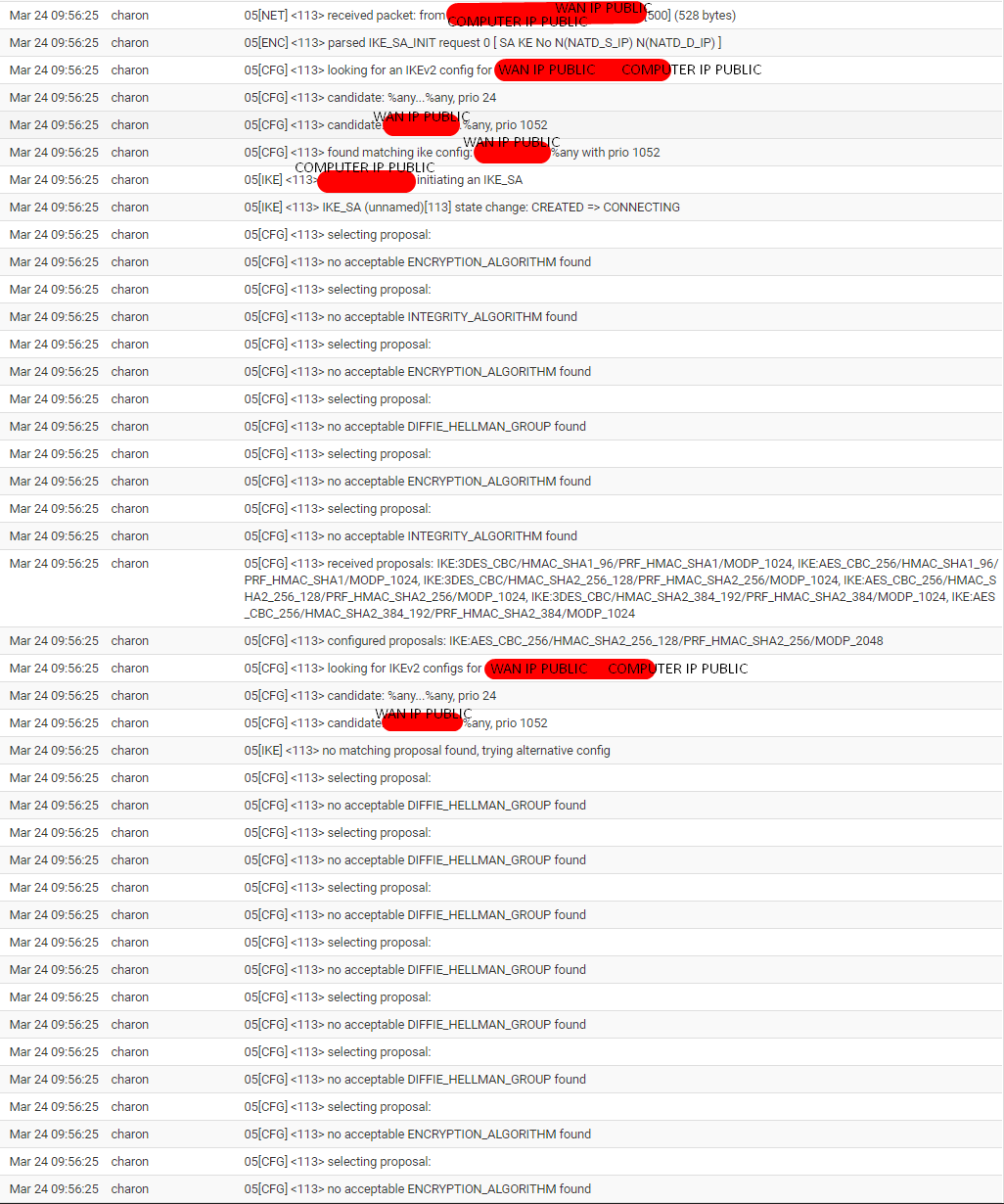
In these logs, what I understand is that it doesn't have the DH group corresponding to the tunnel's DH group, so it doesn't match.
But I did enter this powershell command on the client machine:
Set-Itemproperty -path 'HKLM:\SYSTEM\CurrentControlSet\Services\RasMan\Parameters' -Name 'NegotiateDH2048_AES256' -value '2'.
Maybe she's not good for Windows 7? "It doesn't display any errors when I run it."
PS: Do you have a technique to create VPN powershell tunnels with Windows 7 because the "Add-VpnConnection" command doesn't exist. Even after upgrading powershell 2.0 to 4.0.
Thanks for your help.
-
That is not related to this thread, start a new thread for each of those questions separately.