Increased Memory and CPU Spikes (causing latency/outage) with 2.4.5
-
Firstly, I huge thanks to Netgate and pfSense team and all those testers out there. I appreciate what you do and continue to do. Please don't read the following as a complaint, just feedback and my experience with a hope that someone can help.
Since upgraded to 2.4.5 I noticed a large increase in memory usage. I noticed this because I used to happily run 2.4.4p3 in a 512M Virtual Machine, when booting 2.4.5 the firewall rules failed to load with out of memory errors. Increasing the VM's memory to 1G resolved this quickly enough. I can understand a memory increase requirement from 11.2 to 11.3 so no major issues there.
However the bigger problem is the large increase in CPU requirements. Again, this is a Virtual Machine (KVM / Proxmox 6.1). The VM is given 2 CPUs of an i5-5250U CPU and this has always ticked along at about 5%-10% usage with 2.4.4p3 and previous releases.
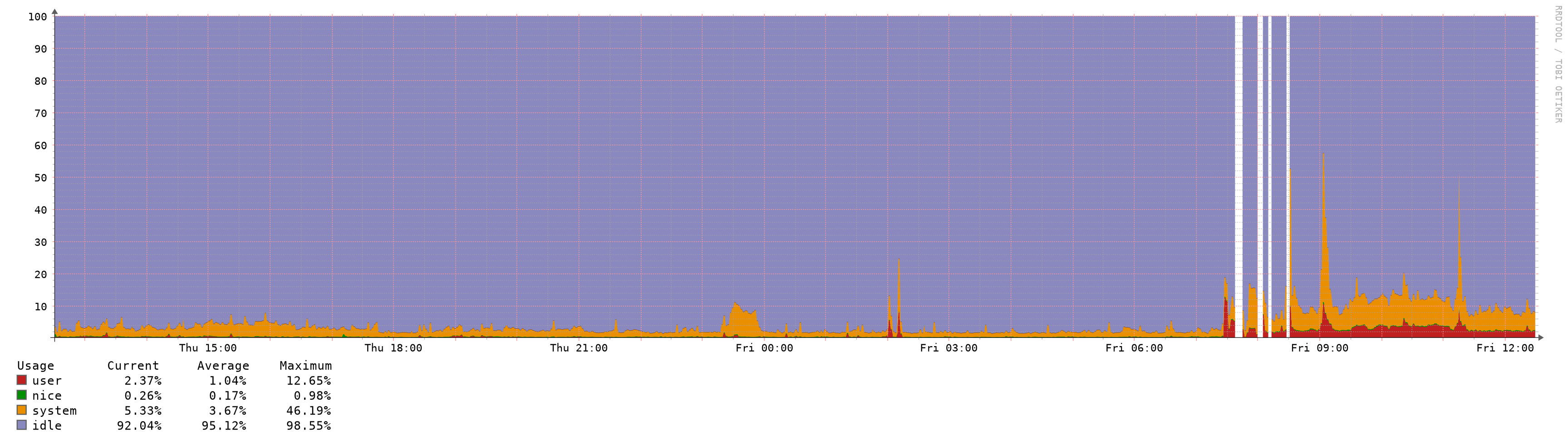
You can see today at about 7am where I upgraded my pfSense instance:
There's a few reboots in there too obviously as I struggled with why pf wouldn't load my rules (the memory problem)
You can see the big spikes though and those happen when I reload one of my OpenVPN clients, just by pressing the little reload icon on the services status widget.
When I do this, pfctl goes up to 100% CPU and just gobbles it for about 4 minutes, though it seems to drop off a few times then come back. But for this 4 minutes, latency goes through the roof. dpinger reports that all gateways are seeing packet loss and latency.
After 4 minutes, it comes right again.The only thing I think that's different about my pfSense from the average user is that I have 4 large ipfire blacklists I load, using the Aliases->URL feature.
Does anyone else see similar? Even in normal usage (where ping times are fine and performance is good) the CPU usage is much higher than it used to be as you can see on my librenms graph.
This is standard, expected? Does anyone else see the big latency/cpu spikes/dropped/delayed packets when reloading services that cause pfctl to reload?
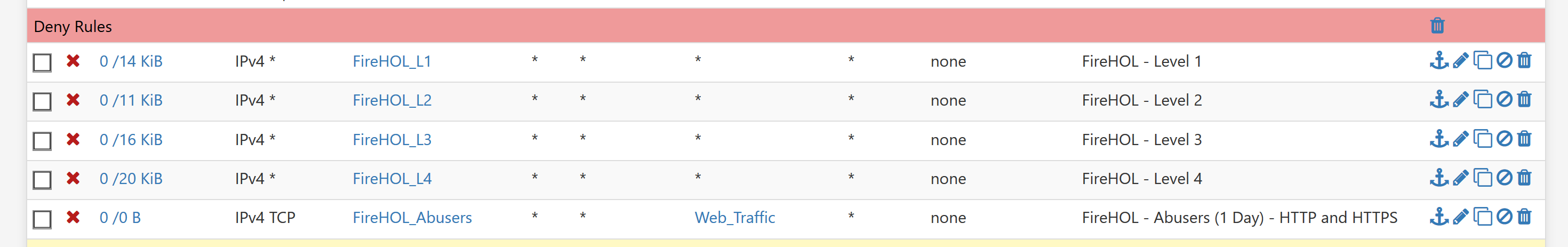
Here's the rules I have on my WAN interface (a pppoe interface)
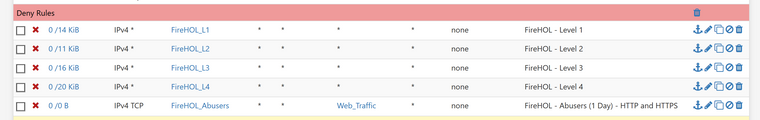
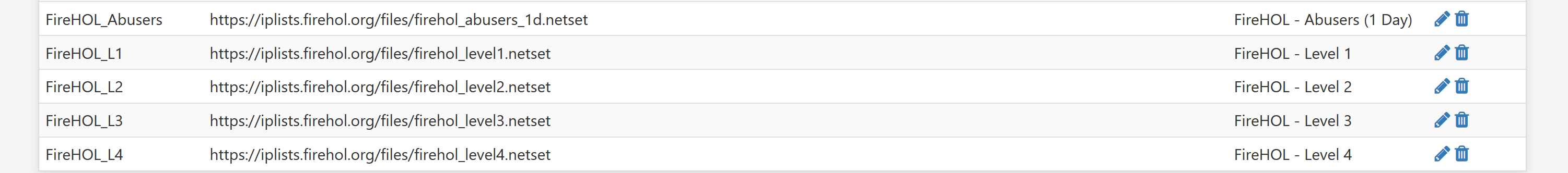
Here's the aliases I am using:

There are 18k entries in the L3 list for example
{12:39}~ ➭ cat firehol_level3.netset| wc -l 18290But as mentioned, this all worked perfect with 2.4.4p3. I could make any changes I wanted and the CPU wouldn't be swamped. It's like pfctl has had a large performance regression.
Anyone else see similar?
Thanks!
Edit to add: I am using vtnet interfaces (virtio ethernet interfaces) not e1000.
Edit2: Hi Abzstrak. -
I haven’t quite figured out what’s going on yet, but I upgraded a 2.4.4-p3 installation that was working fine, and the CPU is absolutely pegged with pfctl using 99% of the CPU nonstop, as well.
I’m running OpenVPN but no blacklists in aliases that large.
-
Are you using KVM and/or virtio interfaces?
-
No. The pfSense instance is on Hyper-V (Windows Server 2019). The interfaces are synthetic NICs with VMQ. Been running this way for at least 4 or 5 months on 2.4.4 builds without ever seeing this kind of CPU usage.
For what it’s worth, I killed the OpenVPN processes along with everything except “bare essentials” like dhcpd and unbound. Pfctl is still running away with all the CPU. The only way I can get it to stop is to roll back to my 2.4.4-p3 snapshot.
-
Interesting. Must be something to do with virtualisation then. Mine settles down after a while, does yours not? I take it a simple reboot doesn't fix the CPU problem?
-
I rebooted it twice so far. It hangs booting up from the point that it initializes the queues onward. Every step of the bootup after that takes far longer than it used to with 2.4.4-p3. The entire bootup process is over 2 minutes. With 2.4.4-p3, it’s about 40 seconds.
And nope, it never settles down. I let it sit untouched for over 30 minutes at one point and pfctl was still churning away at 99%.
-
@xpxp2002 I'm tried upgrading this afternoon and saw the same thing. pfctl - 100%. I'm also using Hyper-V on Server 2019 and had to revert back to a snapshot. Been using pfSense under Hyper-V for years and this is the first time I've had to revert an upgrade.
-
@swinn Perhaps there is something about these virtualized instances that is a problem, as @muppet suggested. Looking through the release notes, I don’t see anything specifically calling out virtualization that seems like it would cause this. Unless simply going to FreeBSD 11 is the issue.
I’ve also run pfSense on Server 2016 for years without issues prior to this. Ran into an issue with Server 2019 and receive segment coalescing causing weird packet drop issues when I first went to 2019, but once I disabled RSC the issue went away. But this is the first time a pfSense upgrade didn’t go smoothly for me either.
-
We haven't had a big FreeBSD jump though, 11.2p10 to 11.3
I can't find any release notes either that say something major/odd has changed with Virtualization in 11.3
-
I’ve been using the snapshot to test individual settings and packages that seem like possible culprits. As I mentioned before, the bootup hangs on the first “configuring firewall...” so I’ve tried removing settings and packages that I expect would be initialized when the filter rule load is occurring, then performed the upgrade.
So far, I’ve ruled out queues/limiters, pfBlocker-NG-devel, and Service Watchdog.
-
The only packages I have installed are:
- Avahi
- OpenVPN-Export
Oh and I have fq_codel configured.
-
@muppet I also have both of those. I’m out of time for testing but either one of those could be the culprit.
My first thought goes to Avahi trying to come up on an interface where it isn’t supported, but it could also be the OVPN export package struggling with the new version of OVPN.
-
Maybe avahi could cause problems, that I could understand.
OpenVPN export isn't even called until you visit that page. -
I upgrade six (6) pfsense production server at the same time from 2.4.4_p3, and I had problem with the conectivity. The ping time is very high above 7.000ms.
I tried upgrade my pfsense server at home from 2.4.4_p3, but in this case I did a snapshot on vmware, and the problem is same. The ping time is very high and the navigation have a lot of problems.
I restored the snapshot, and all return to normally
At all server I have installed this packages:
Open-VM-Tools
openvpn-client-export
squid
snort
zabbix-agent4I tried reinstall all packages, but the problem persist
-
Same troubles after upgrade from 2.4.4 to 2.4.5 on Hyper-V Windows Server 2019, 100% CPU usage (by pfctl process), long boot, and pfSense works with spikes and hangs.
It seems that 2.4.5 not compatible with Hyper-V Windows Server 2019.
Maybe it related:
https://forum.netgate.com/topic/149595/2-4-5-a-20200110-1421-and-earlier-high-cpu-usage-from-pfctl/8 -
I'm having the same problem. I'm running 2.4.4.-p3 on Server 2016 with Hyper-V. I tried upgrading my 2nd CARP node to 2.4.5 yesterday, but it pegged the CPU and never became stable. I reverted that snapshot, shut it down and tried to upgrade my 1st CARP node, but the same problem. I've reverted both nodes to the snapshots.
pfSense on Hyper-V has been rock solid up until now and all previous upgrades have been flawless.
If I have time, I'll try installing a 2.4.5 VM from scratch to see if the problem occurs there too.
-
I have made clean reinstall system with catching config from updated system, first time boot was fast, then all packagers was restored (installed), after that system stuck at boot and lags after.
Then i have found a source of problem — pfBlockerNG! When it's disabled, all works good, after enabling pfBlockerNG system lags totally. -
@Gektor This is interesting. I had pfBlockerNG-devel installed on 2.4.4-p3. One of my earlier tests was to roll back to 2.4.4-p3, uninstall that package, then upgrade; and my system was still slow. Did you simply disable it, or uninstall the package?
I will try this later today when I have an outage window.
-
Mine is pfBlockerNG version 2.1.4_21, with this setting all works good:
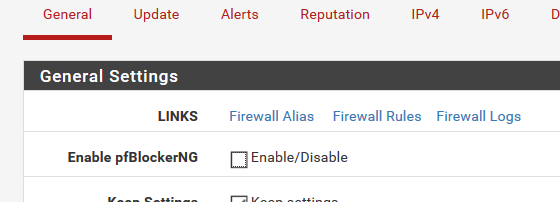
Then i have disable all GeoIP lists, but enable DNSBL, and enable pfBlockerNG, and for now there is no problems with pfSense 2.4.5 on Hyper-V. System makes "crazy" when GeoIP lists is enabled in pfBlockerNG.
Have make post, maybe it will be helpful:
https://forum.netgate.com/topic/151726/pfblockerng-2-1-4_21-totally-lag-system-after-pfsense-upgrade-from-2-4-4-to-2-4-5 -
@Gektor I deleted all the installed packages:
Open-VM-Tools
openvpn-client-export
squid
snort
zabbix-agent4and I disabled OpenVPN links unpriority; and the system conectivity was restored